Patents
Literature
44results about How to "Efficient Safety Management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
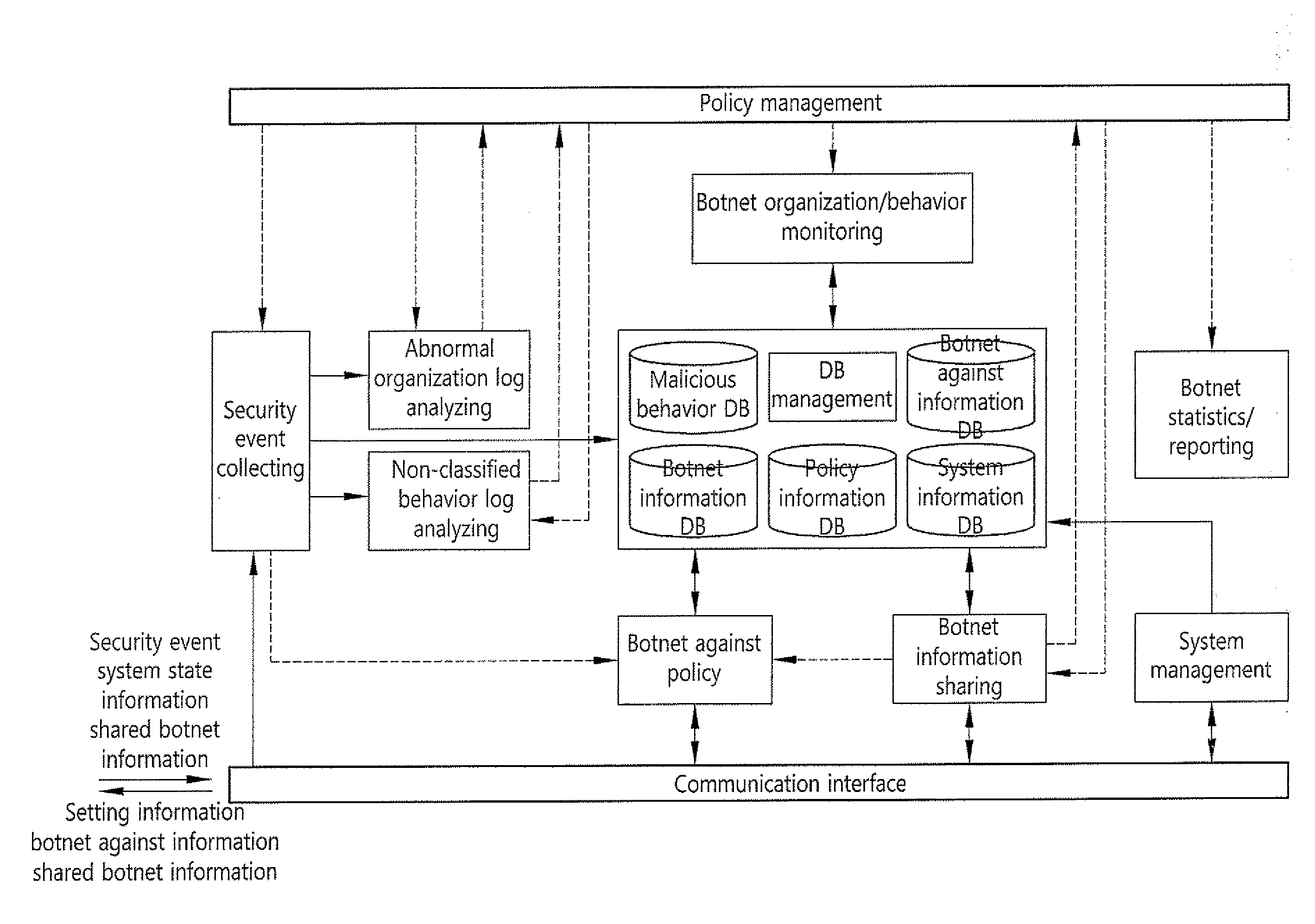
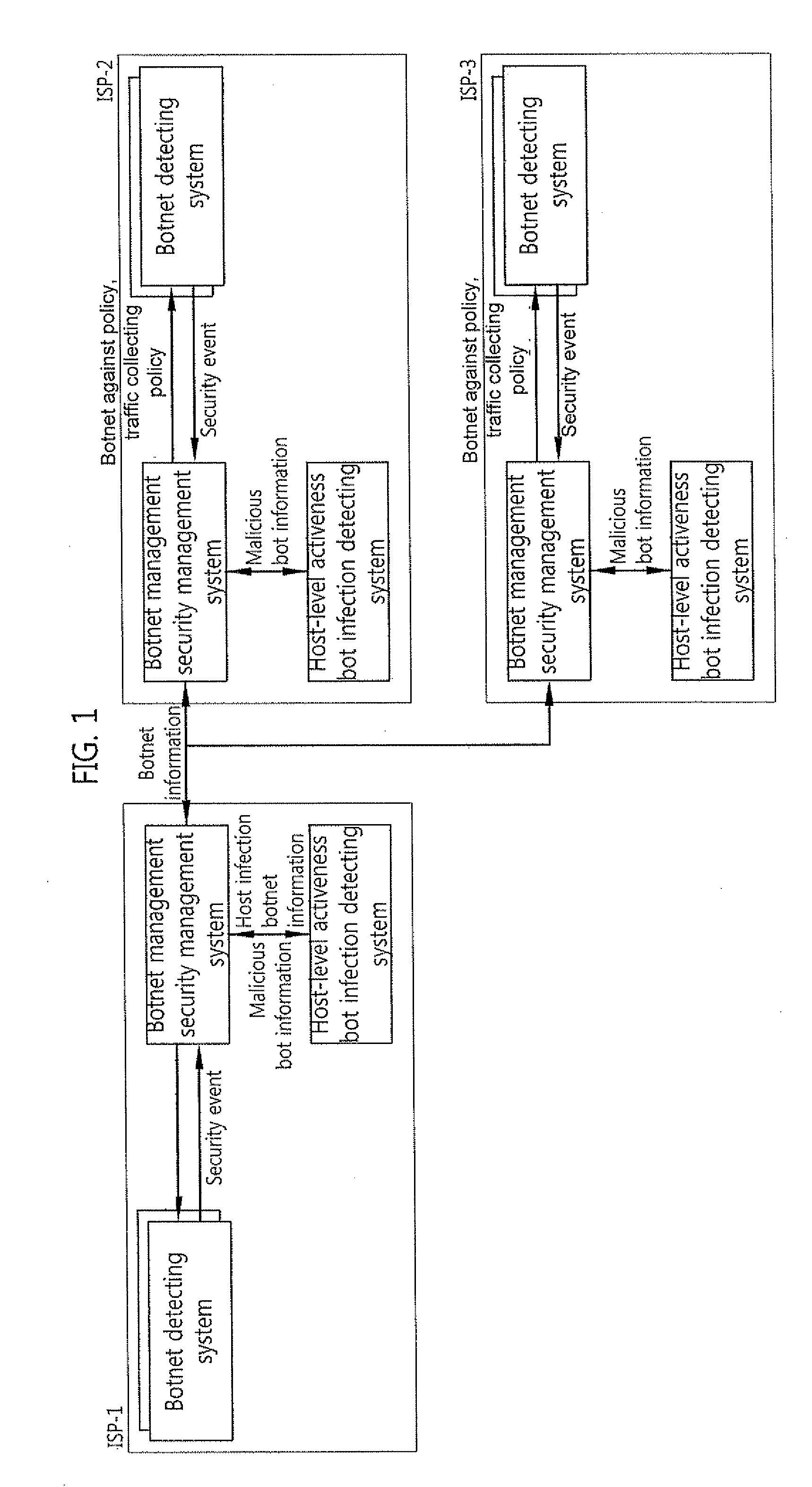
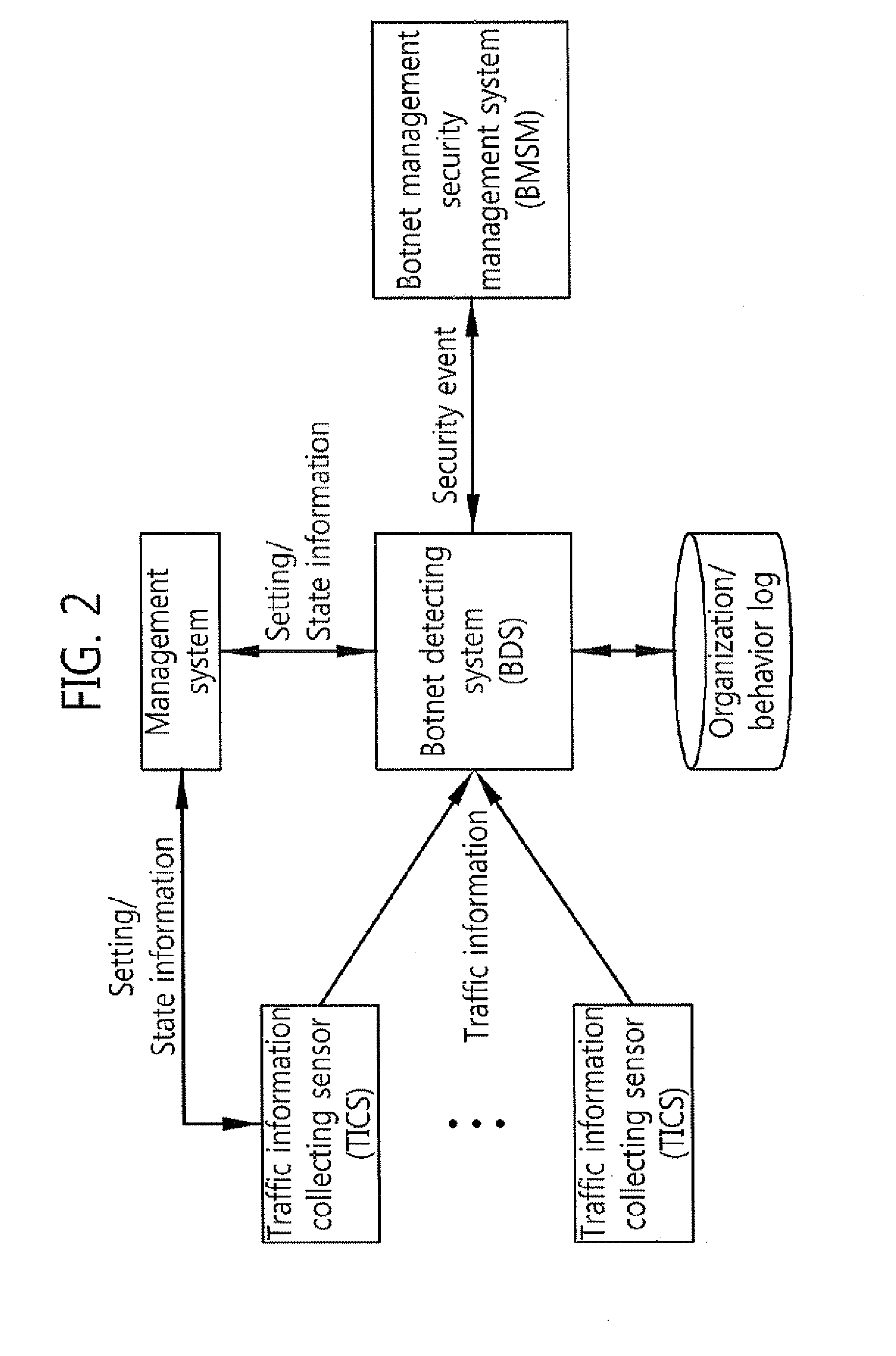
Security system of managing irc and HTTP botnets, and method therefor
InactiveUS20100162350A1Efficient Safety ManagementData taking preventionSpecial data processing applicationsService provisionBotnet
The present invention relates to a security system of managing IRC and HTTP botnets and a method therefor. More specifically, the present invention relates to a system and a method that detects a botnet in an Internet service provider network to store information related to the detected botnet in a database and performs security management of IRC and HTTP botnets, including a botnet management security management (BMSM) system, configured to visualize the information related to the detected botnet and establish an against policy related to the detected botnet. Accordingly, the present invention provides a security system of managing IRC and HTTP botnets that can efficiently performs the security management of IRC and HTTP botnets by using the BMSM system
Owner:KOREA INTERNET & SECURITY AGENCY
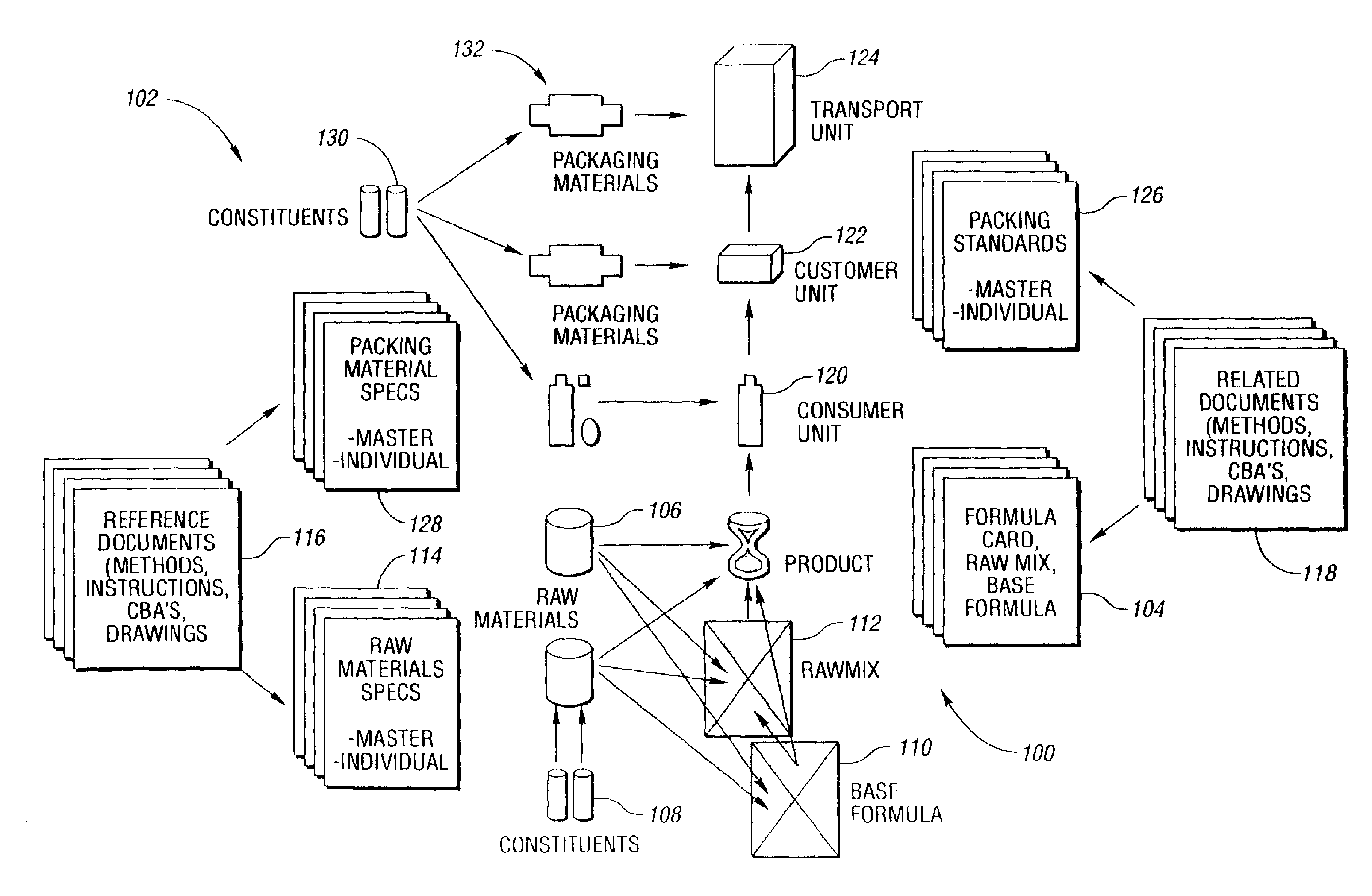
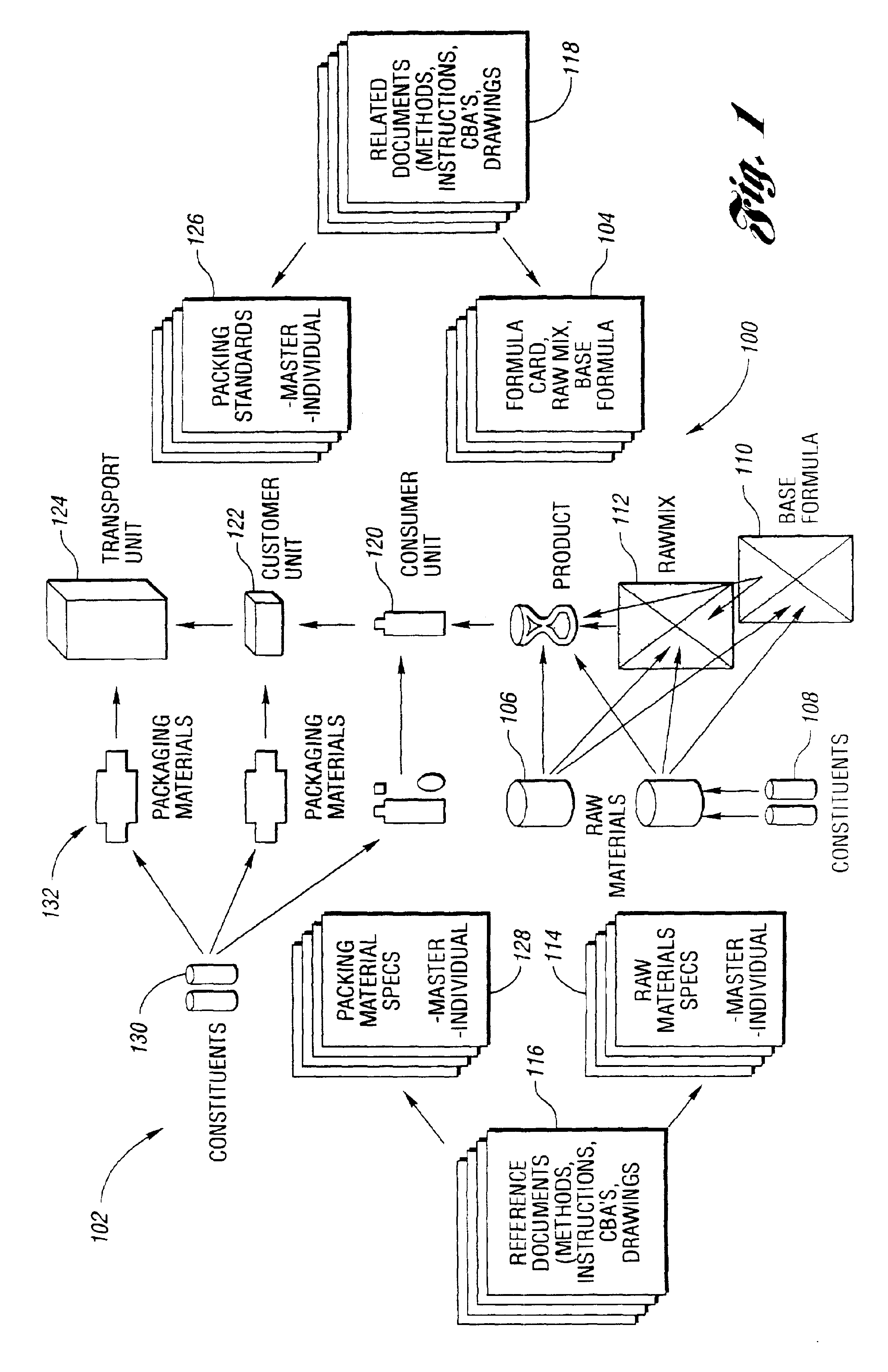
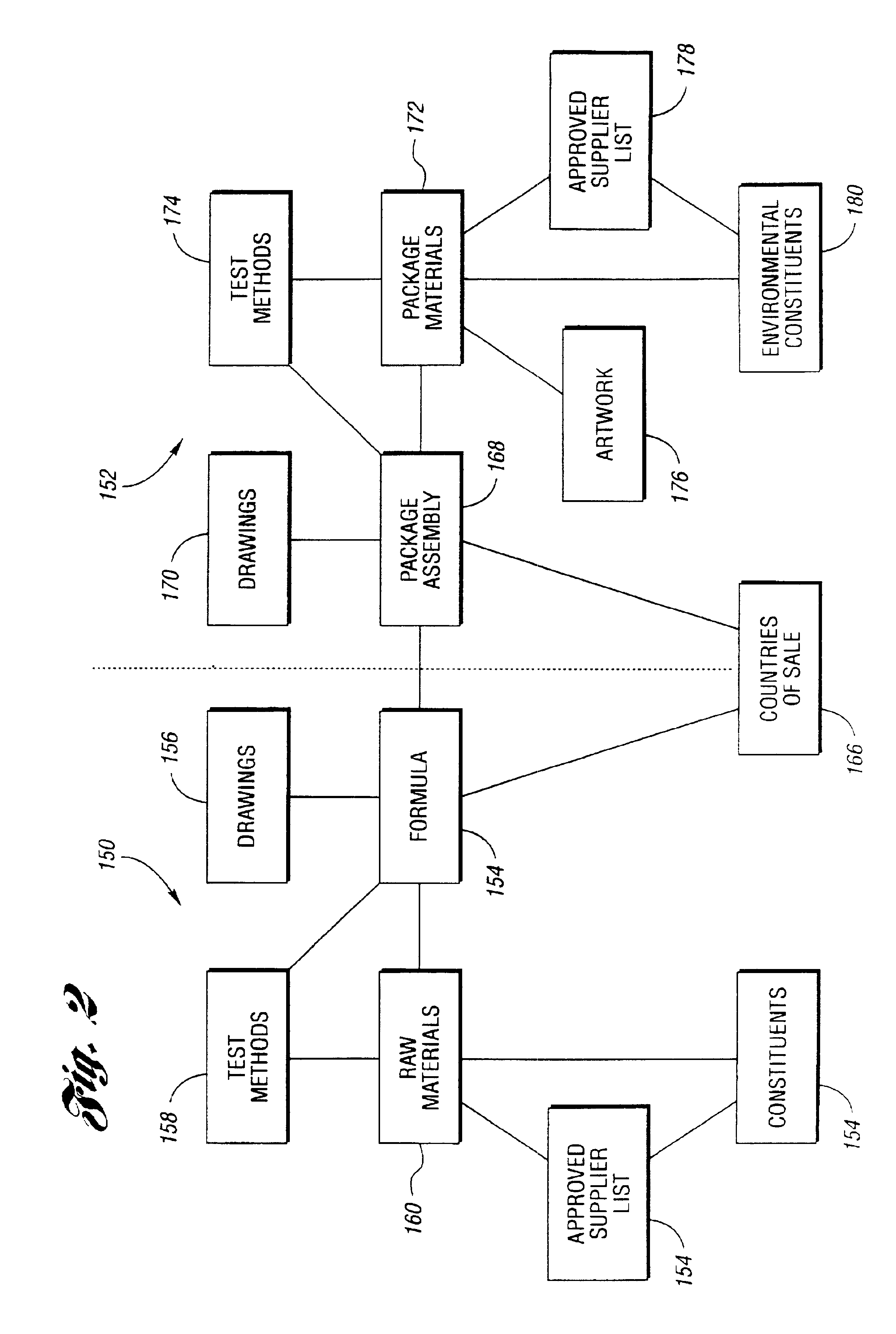
System and method for managing product development
InactiveUS6862585B2Reduce redundant data entryFacilitates electronic review and approvalResourcesSpecial data processing applicationsElectronic communicationProcessing Instruction
A system, method, and computer readable storage medium for managing product development include a relational database containing draft, approved, and archived versions of product, package, materials, process, and artwork technical data for use by product development personnel in providing a structured set of data output for use in a supply chain. In one embodiment, the relational database includes objects having data to describe design requirements of a finished product component such as a formula, material, package, and the like. Text documents may be linked to the relational data structure by reference to provide design requirements not amenable to a structured data format, such as test methods, process instructions, and the like. The system, method, and computer readable storage medium provide for electronic communication and electronic approval of data subsets while tracking changes and archiving previous versions for subsequent access or reference. System validation and ongoing change control provide necessary support for products in regulated industries.
Owner:THE PROCTER & GAMBLE COMPANY
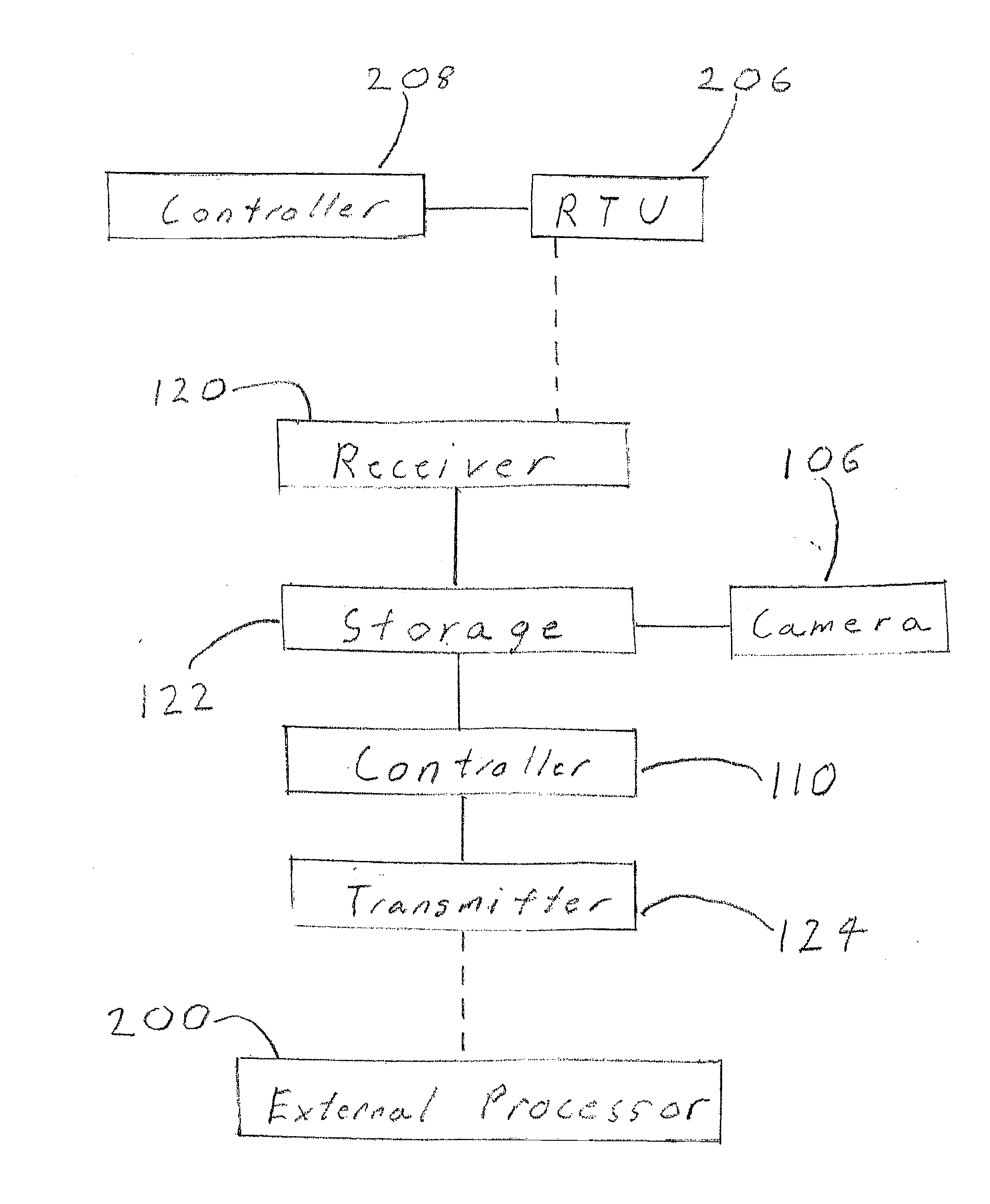
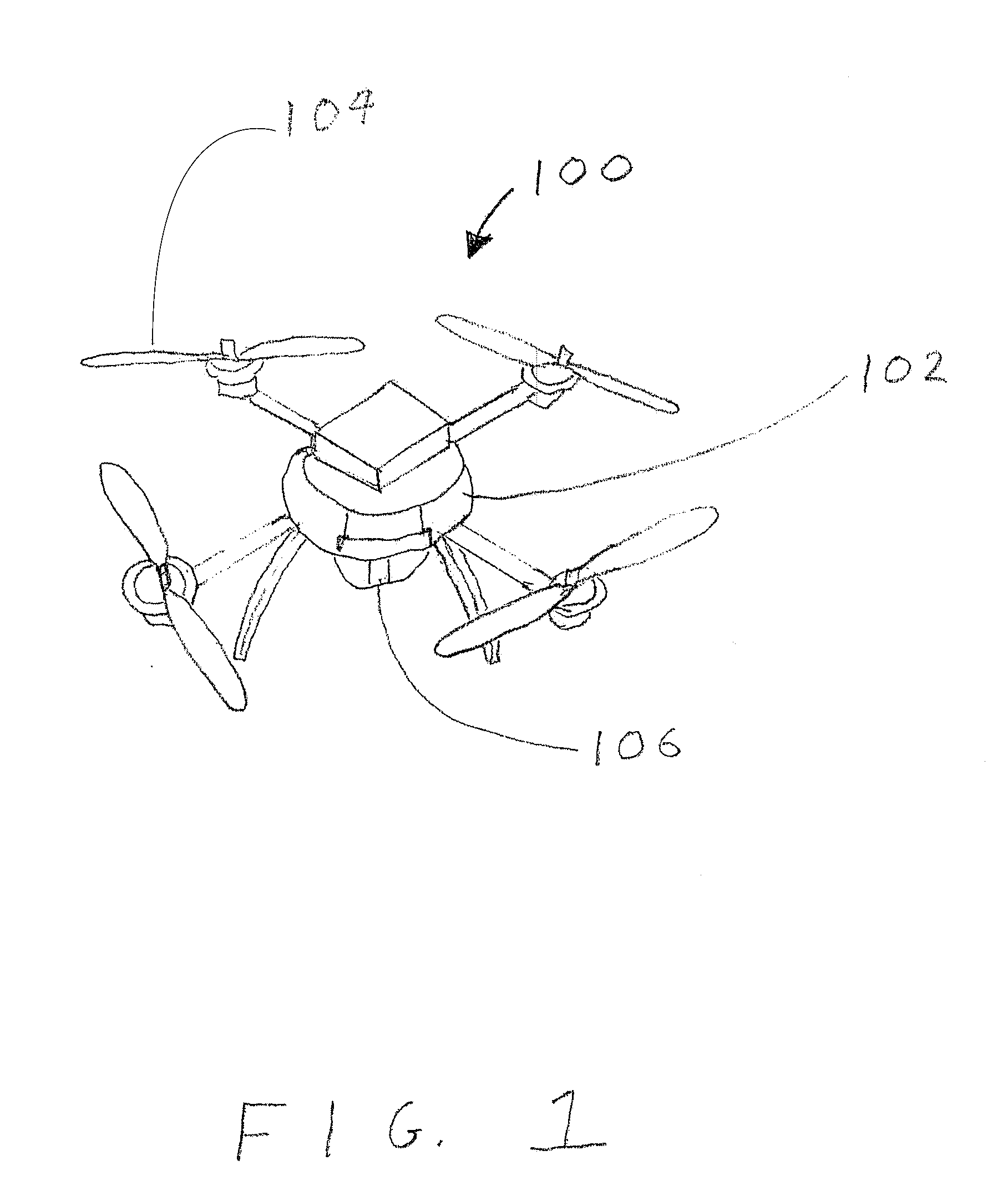
Systems, Methods and Devices for Collecting Data at Remote Oil and Natural Gas Sites
InactiveUS20160144959A1Efficient Safety ManagementAvoid collisionAircraft componentsSamplingParticulatesFeedback control
Systems, methods and devices are provided for collecting operational data at remote oil and natural gas sites, such as wells, and or processing and refinery plants. One such system comprises a remote transmitter and / or controller at the site and an unmanned aerial vehicle (UAV), such as a drone aircraft, configured for aerial dispatch to the remote site and wireless connection to the remote transmitter for subsequent relay or upload of data to an external processor. The UAV may include still or video cameras for collecting images around the well site that can be uploaded and transmitted to the external processor. The system may also include logic-based applications allowing for feedback control of the well site to change operational parameters based on the received data. The system may also include a variety of sophisticated sensor devices on the UAV or located at the remote site to collect additional operational data, such as airborne particulate and / or toxic gas concentrations, audio files of pumps or other equipment and levels and properties of produced water and other fluids.
Owner:OIL & GAS IT LLC
Data transmission method, system and apparatus in internet of things
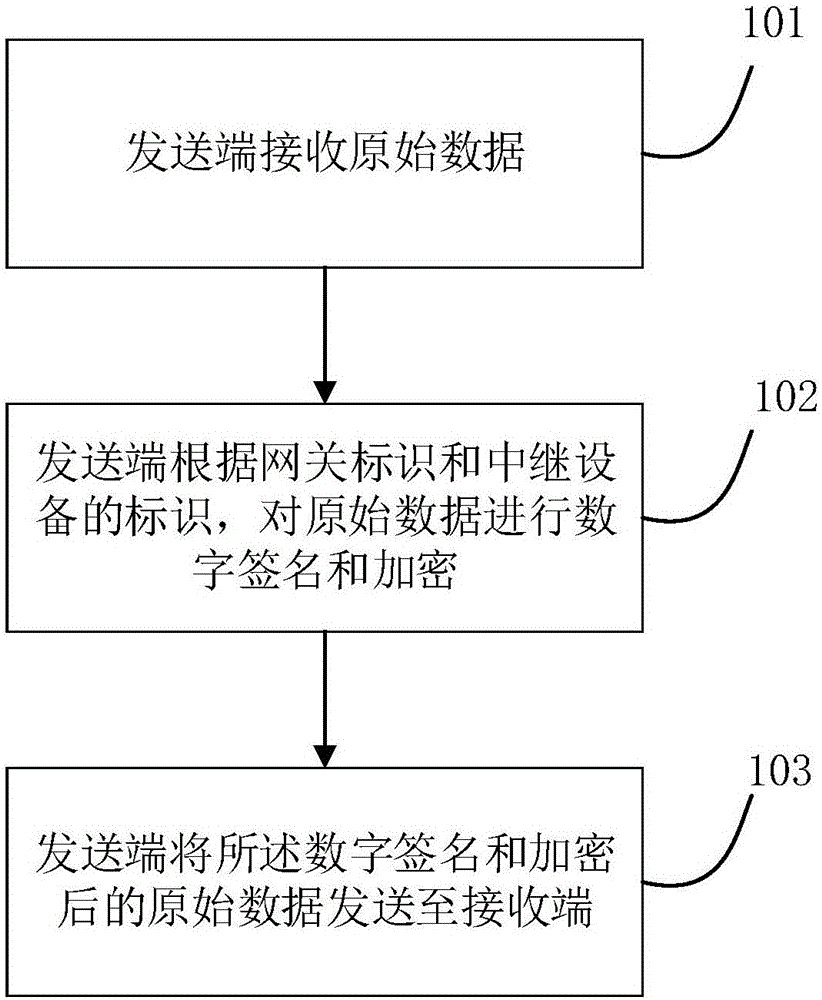
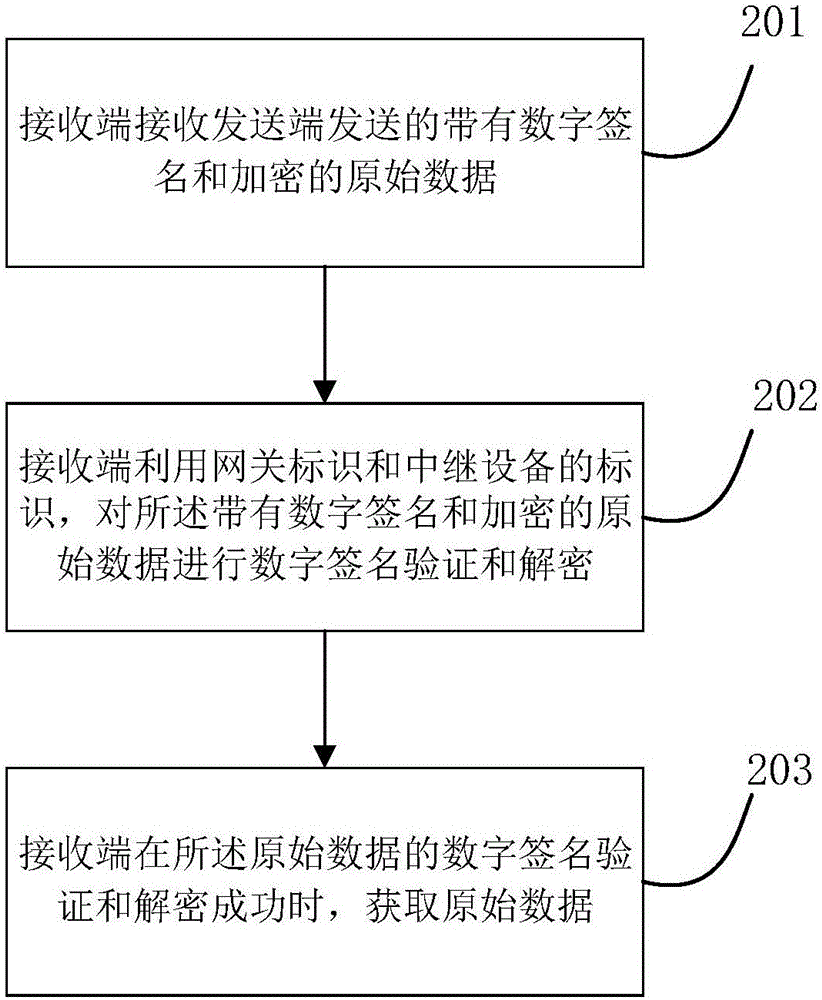
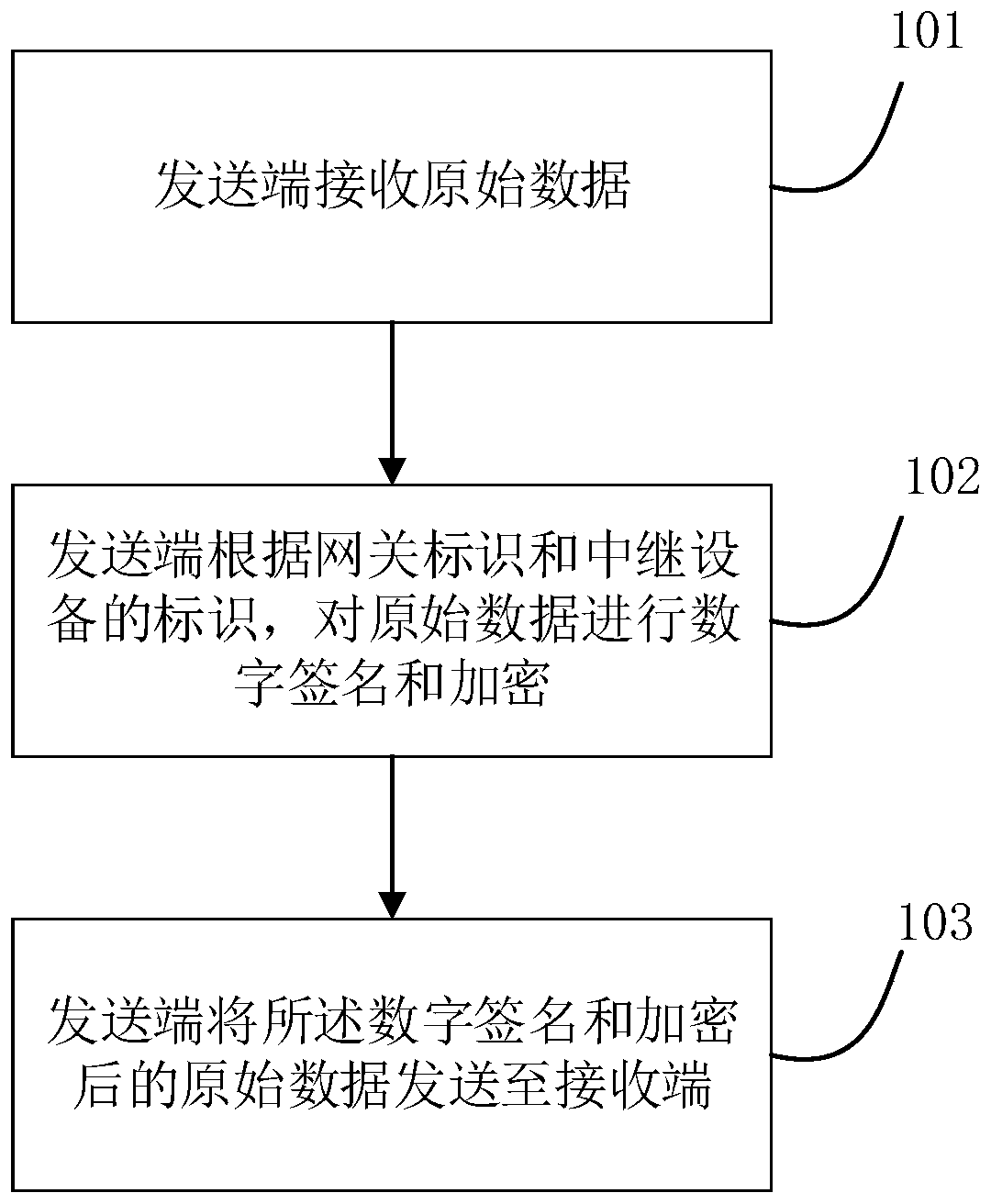
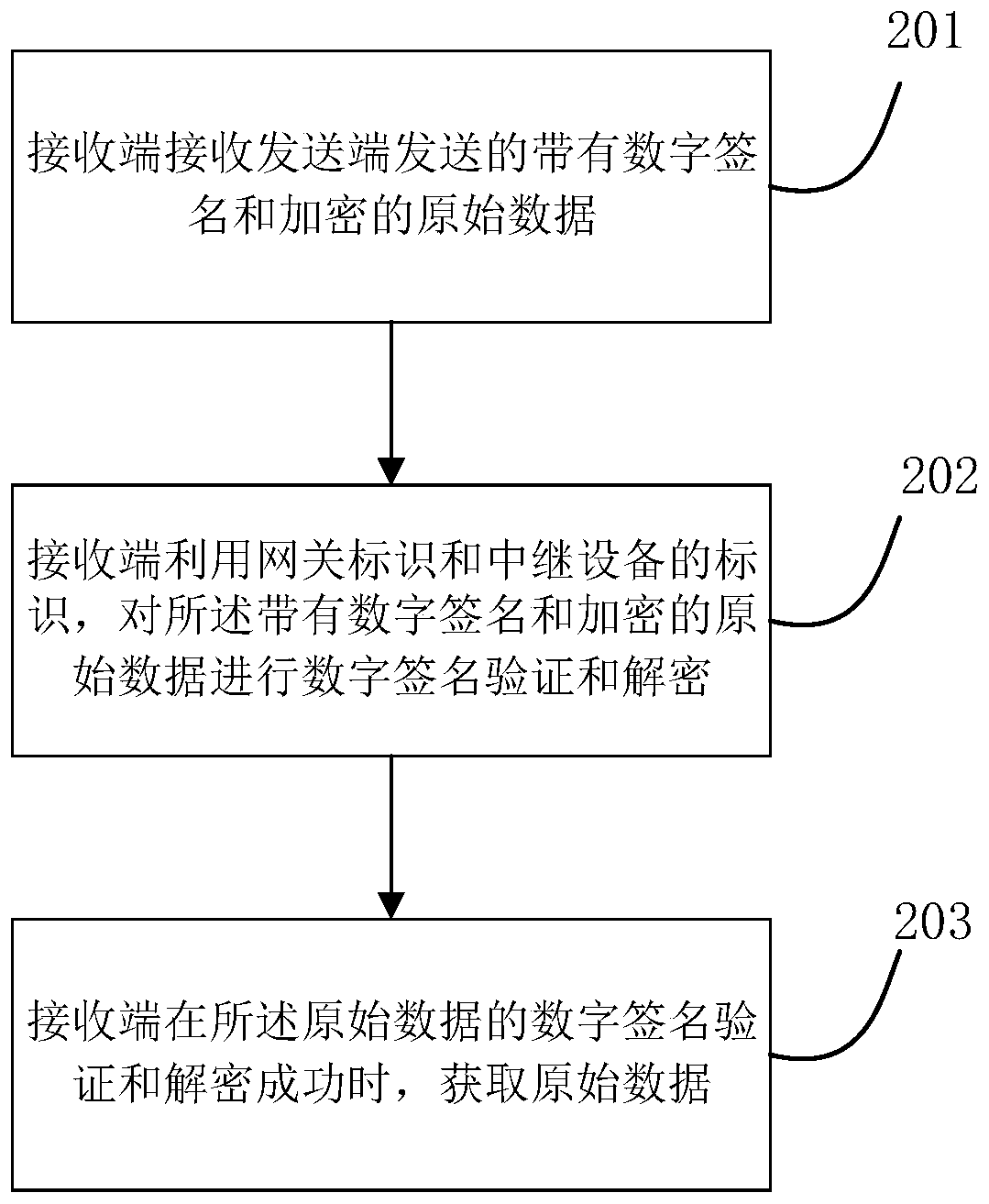
ActiveCN106375390AEfficient data transferEnsure communication securityTransmissionOriginal dataDigital signature
The present invention relates to a data transmission method in an internet of things. Data is transmitted between terminals in an internet of things environment; a transmit end sends original data to network data transmission devices; the network data transmission devices sequentially add a digital signature to each piece of data; and the final network data transmission device verifies all digital signatures of the received data, determines that the data is from the transmit end through a set path, and then sends the original data to a receive end. The present invention further provides a data transmission system in the internet of things and a data transmission apparatus in the internet of things. The data is singed when passing each hardware device in transmission, a later receiving device can verify the signature, so that multiple nodes on one communication chain are managed safely and effectively, the whole communication chain is ensured to communicate safely, and a non-credit person is prevented from intruding and controlling the device.
Owner:北京爱接力科技发展有限公司
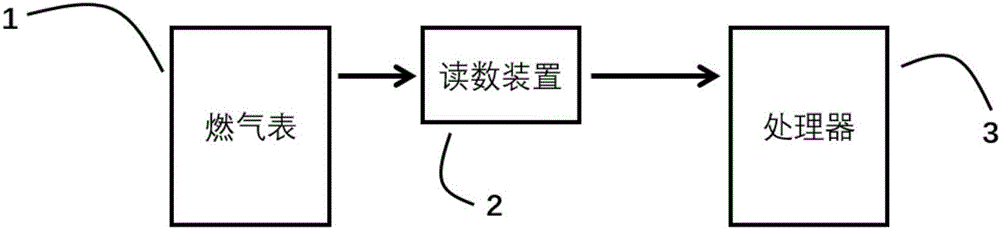
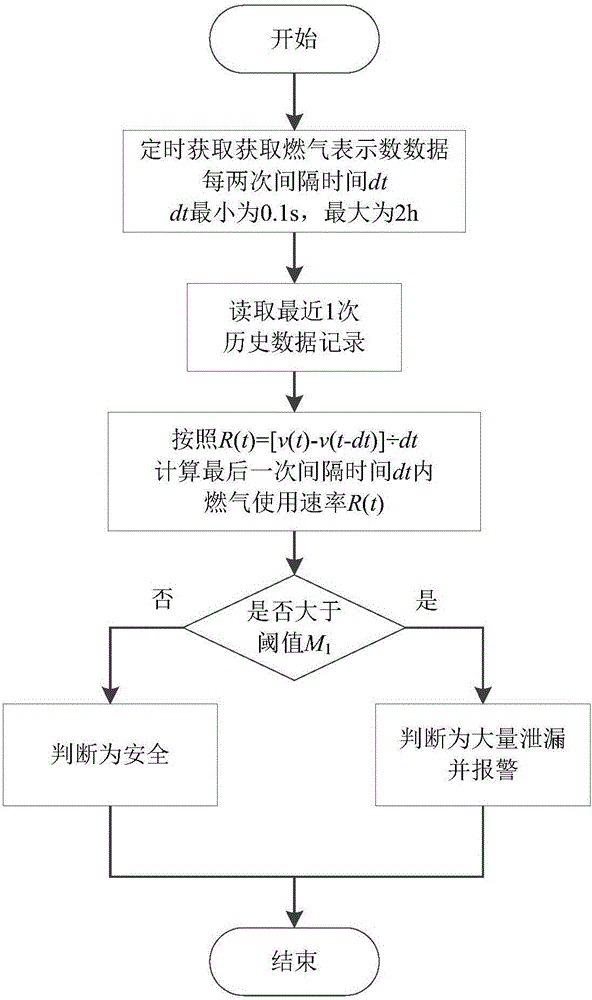
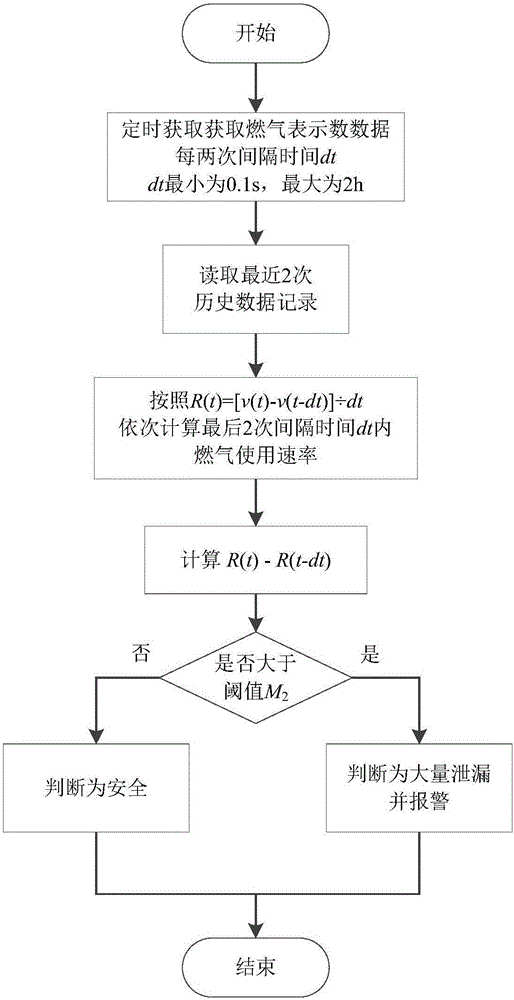
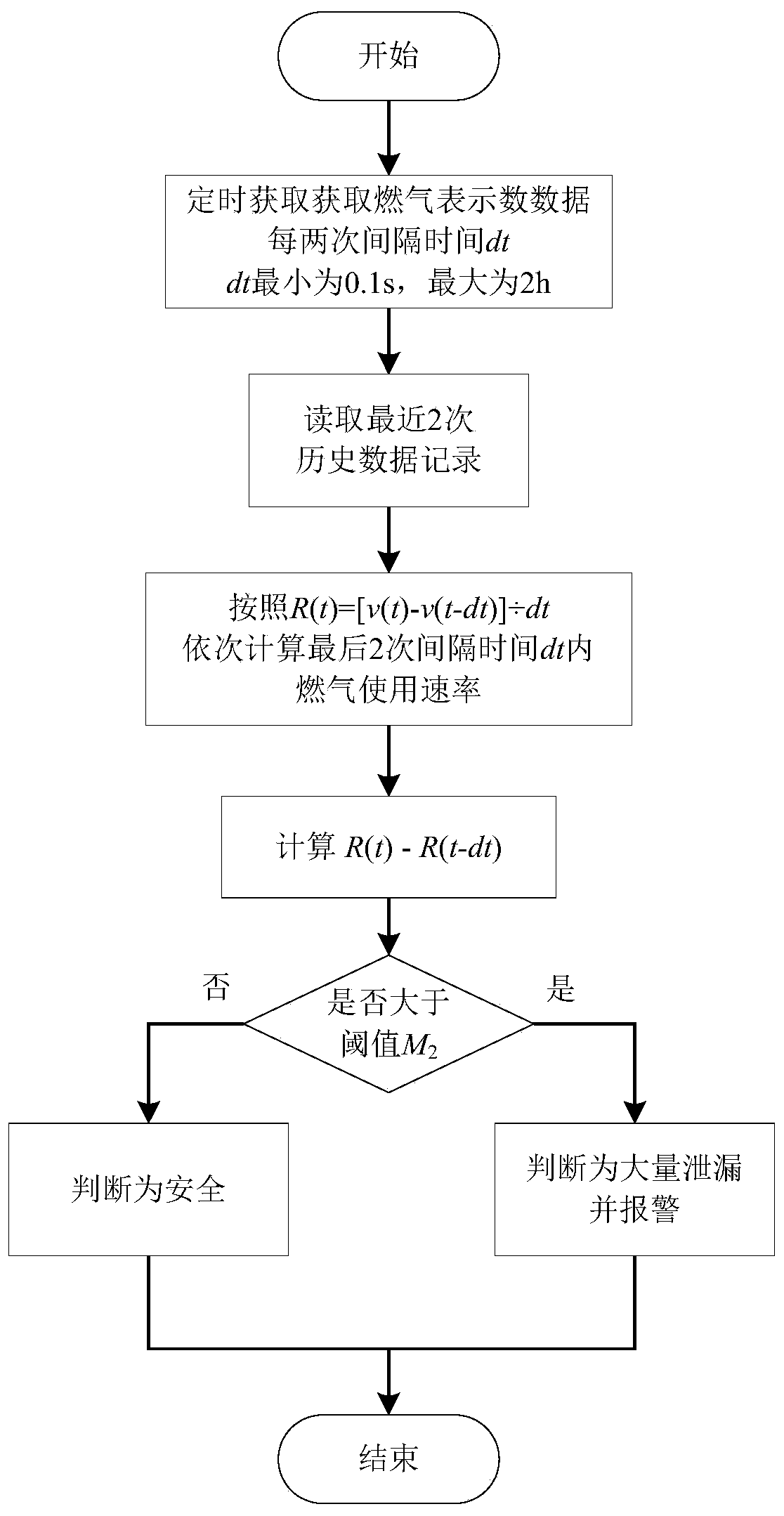
Civil gas safety monitoring method
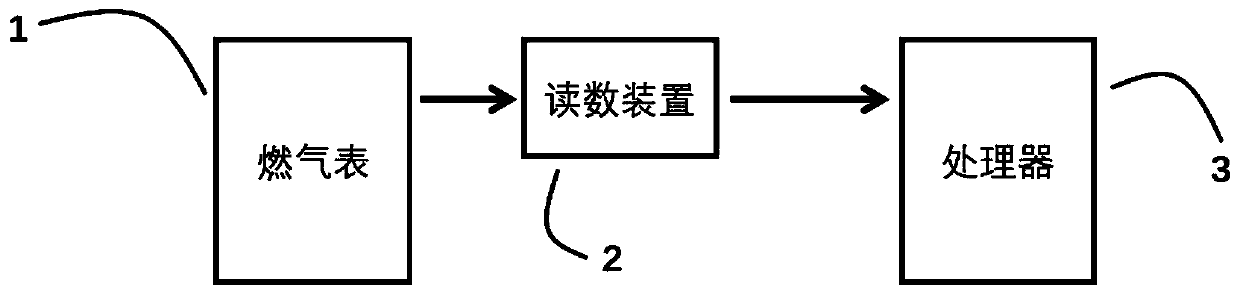
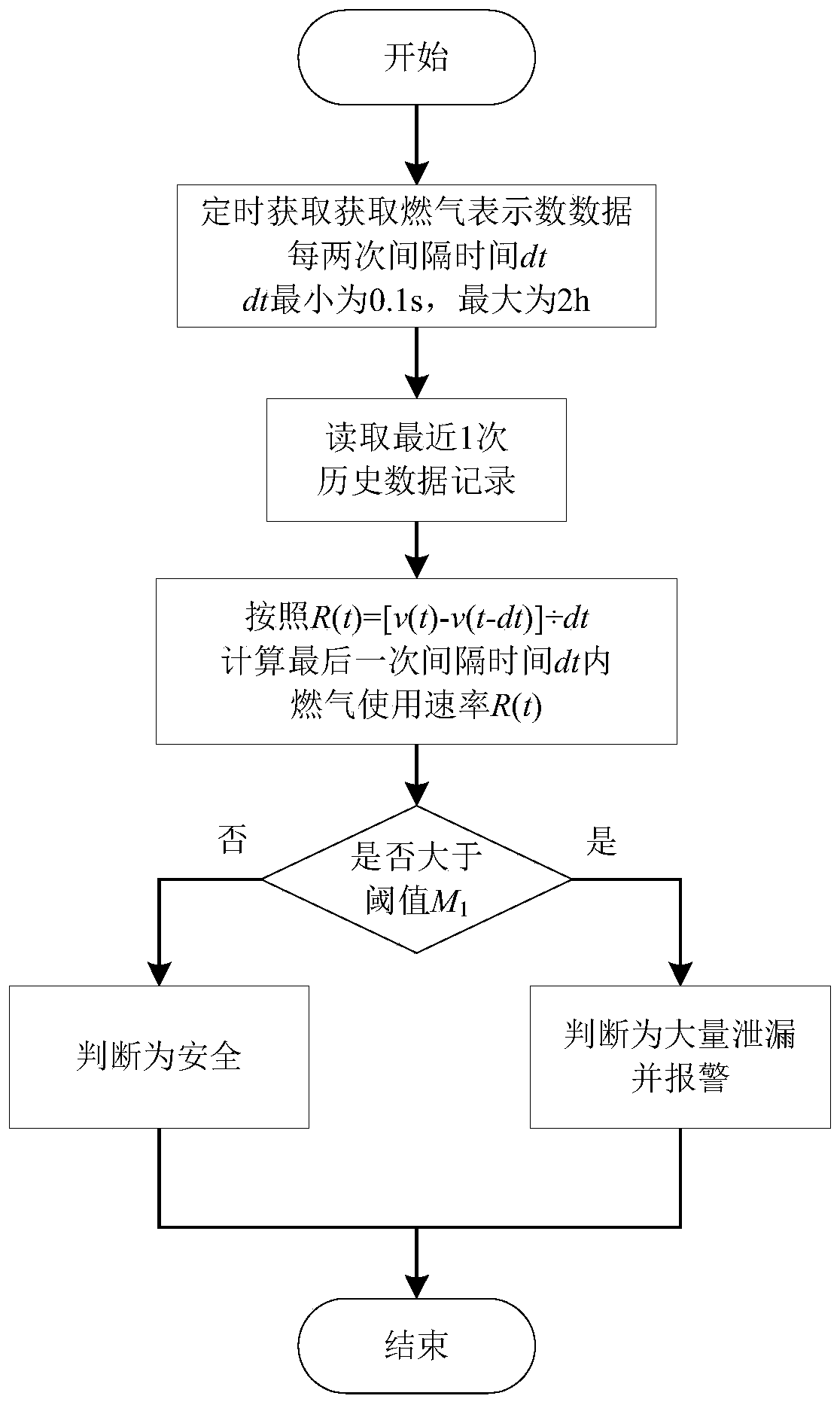
ActiveCN106527327AReal-time acquisitionUpload in real timeProgramme controlComputer controlGas meterSecure state
The invention provides a civil gas safety monitoring method, and relates to a method for judging the pipeline safety state through gas meter reading data. According to the method, different thresholds are set according to the flow data calibrated in advance within the unit time before installation of the system or in preliminary installation or according to the sum of the upper limit of the nominal values of gas consumption of all the gas utilization equipment behind the gas meter within the unit time and according to different situations; concretely, the gas meter acquires the reading data in real time and transmits the reading data to a processor, and the processor judges whether the pipeline behind the gas meter has large amount of leakage or small amount of leakages through the change law of the historical data and the preset thresholds and alarms if the judgment result is yes. The safety of the civil gas system can be guaranteed so that the safety decision and the user service can be provided for the gas company and the method has wide adaptability and flexible expansibility.
Owner:TSINGHUA UNIV +1
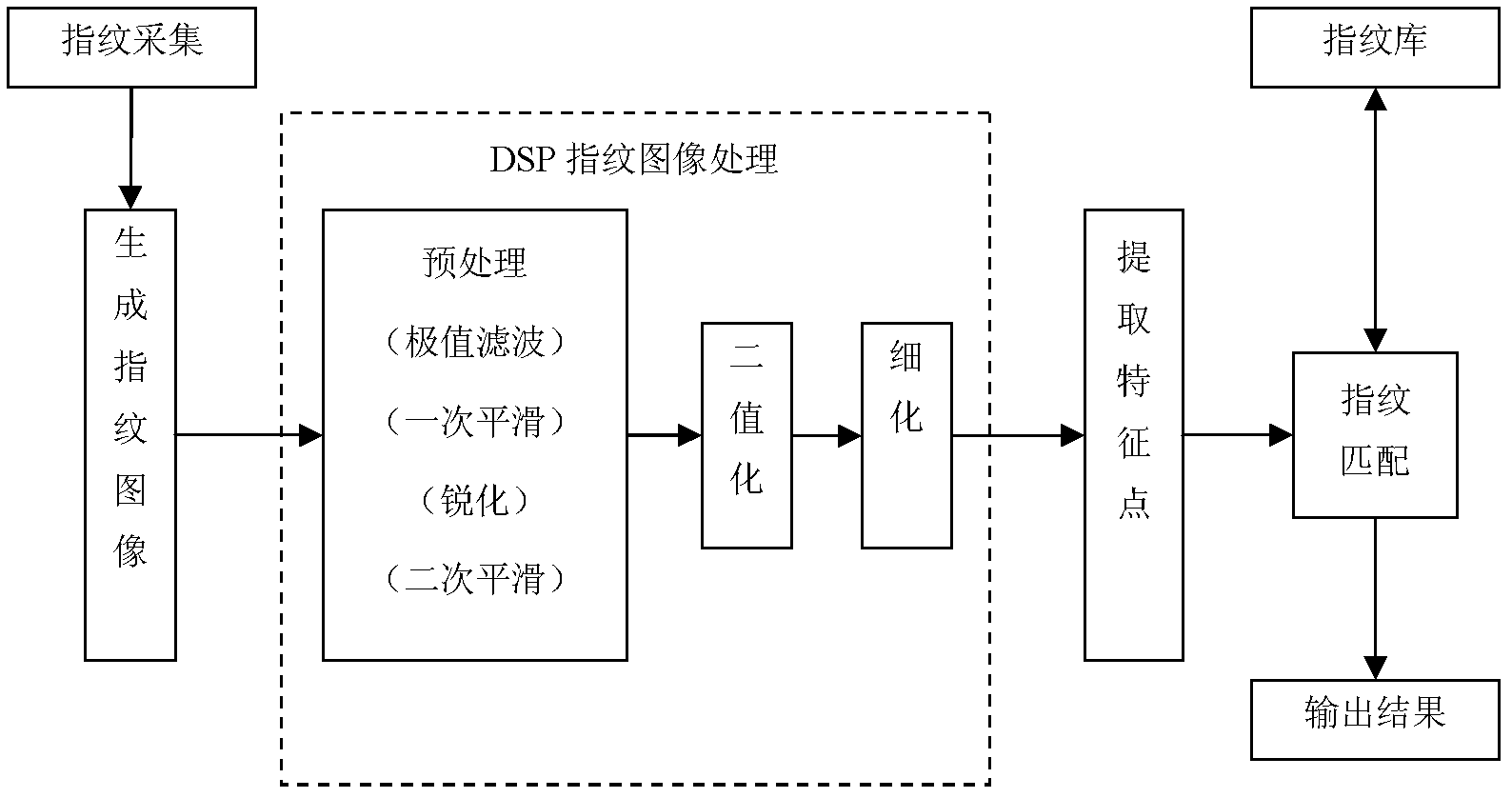
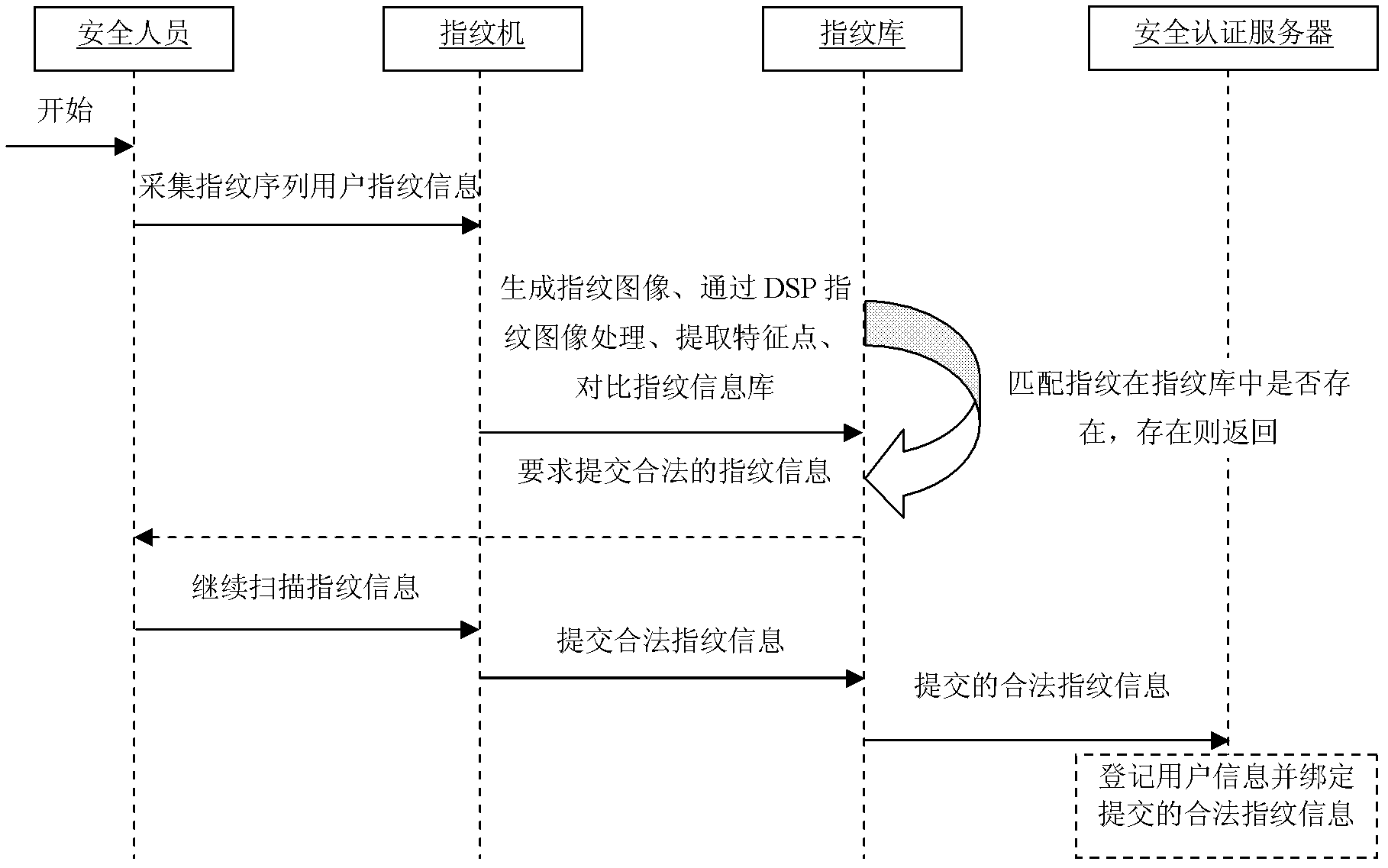
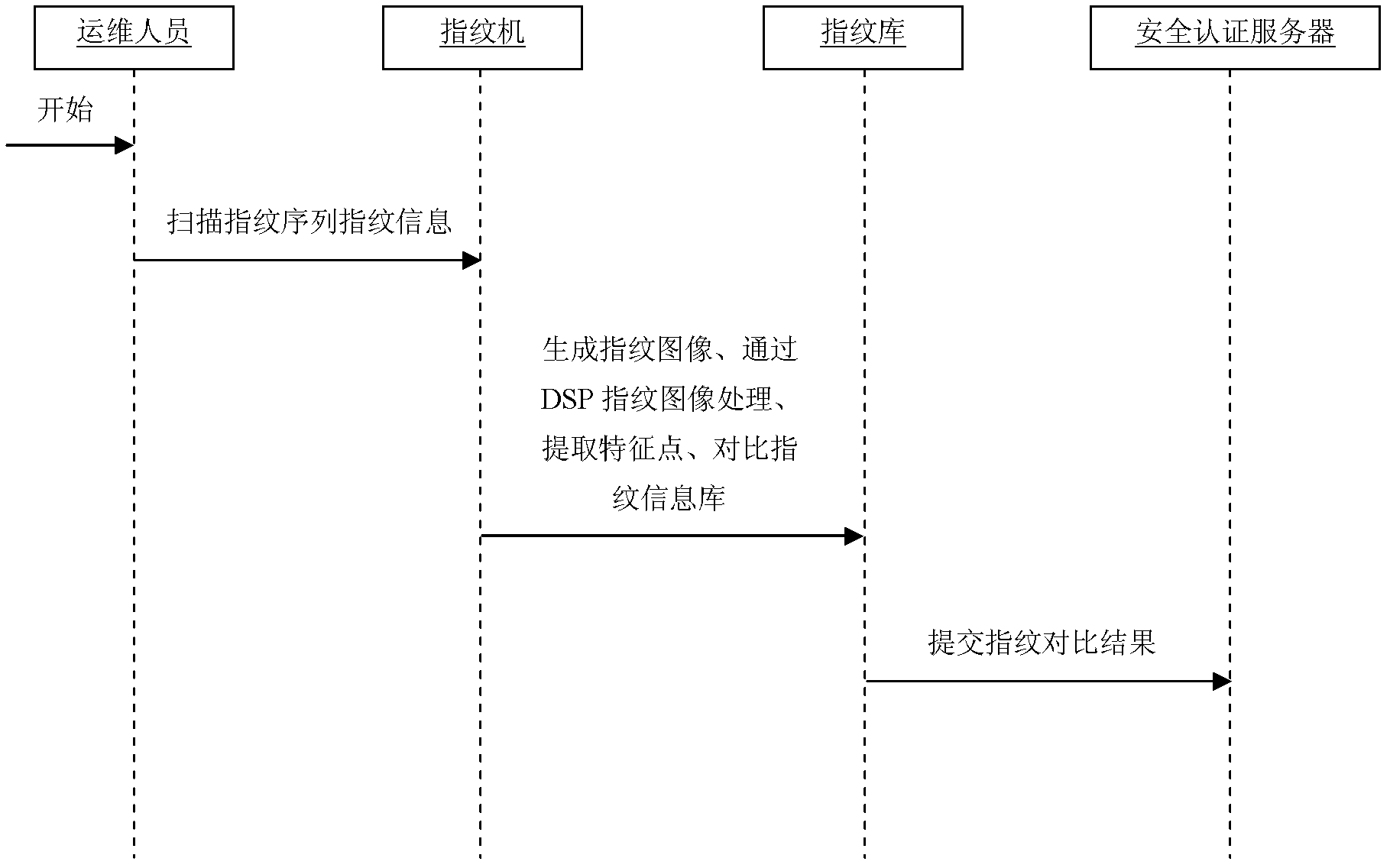
Operation and maintenance safety management method based on fingerprint identification
InactiveCN103186735AReduce security risksGuaranteed confidentialityCharacter and pattern recognitionDigital data authenticationFingerprintManagement system
The invention discloses an operation and maintenance safety management method based on fingerprint identification. The method comprises the steps as follows: 1) collecting and registering fingerprint information to a fingerprint information library; 2) registering user information and binding the fingerprint information on a safety certification server; 3) scanning the fingerprint information on a fingerprint identification machine by a user required to log in an operation and maintenance management system; 4) comparing the scanned fingerprint information with fingerprints in the fingerprint information library one by one for identification; 5) sending a fingerprint information comparison result to the safety certification server; and 6) when the comparison result is passed, allowing the user to enter the operation and maintenance management system, and when the comparison result is not passed, refusing admission to the operation and maintenance management system. According to the method, the safety of the operation and maintenance service is improved through the advanced, unique and stable biological identification technology.
Owner:勤智数码科技股份有限公司
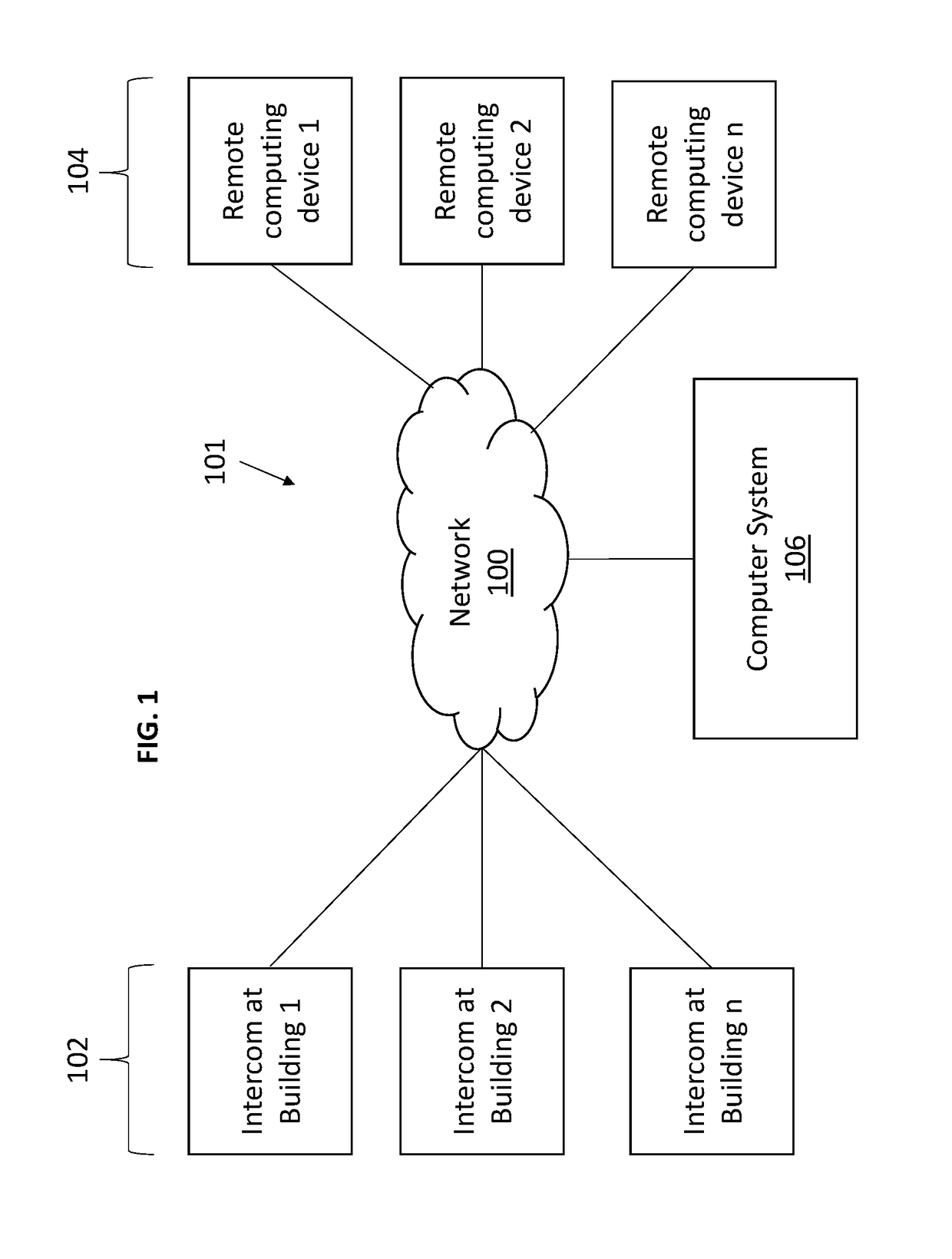
Door entry systems and methods
ActiveUS9800737B2Efficient Safety ManagementInterconnection involving common lineSpecial service for subscribersThird partyMobile device
Owner:DROPBY INC
Status flags in a system of electronic pyrotechnic devices such as electronic detonators
InactiveUS20050190525A1Efficient Safety ManagementReliably successful firing sequenceMake-and-break ignitionIncandescent ignitionEngineeringCapacitor
An electronic blasting system in which each detonator is provided with status flags or the like to convey the status of various states or conditions of the detonator such as detection on the system bus, firing capacitor charging, calibration of the detonator's circuitry, and events such as the successful receipt of a fire command.
Owner:SPECIAL DEVICES
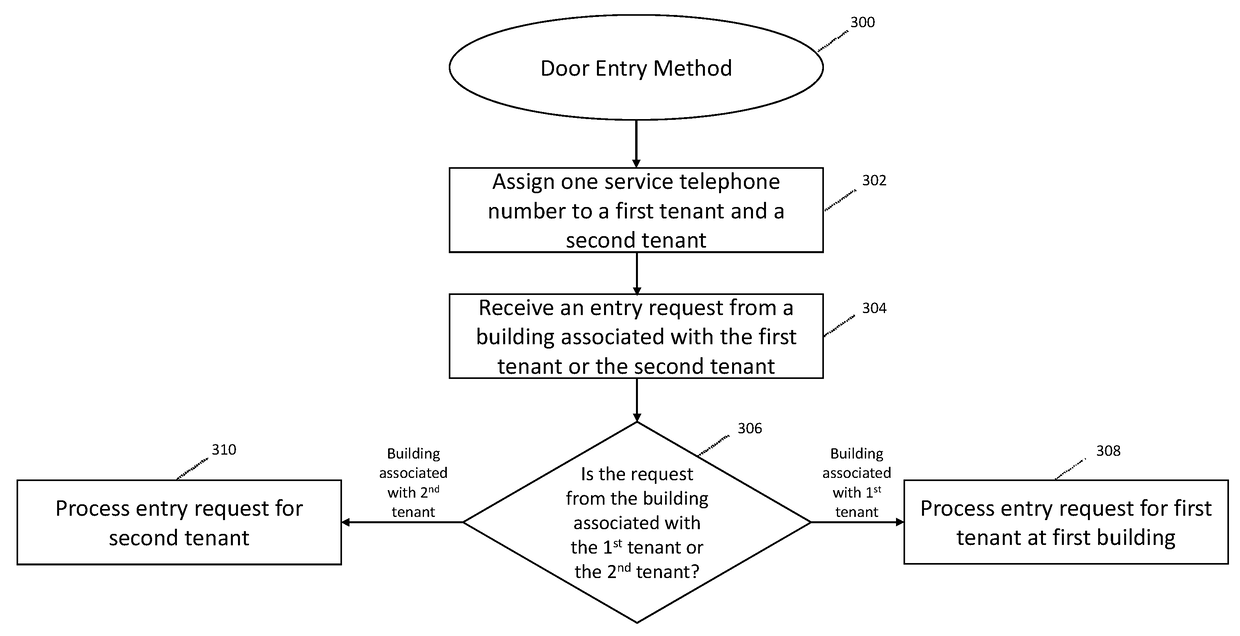
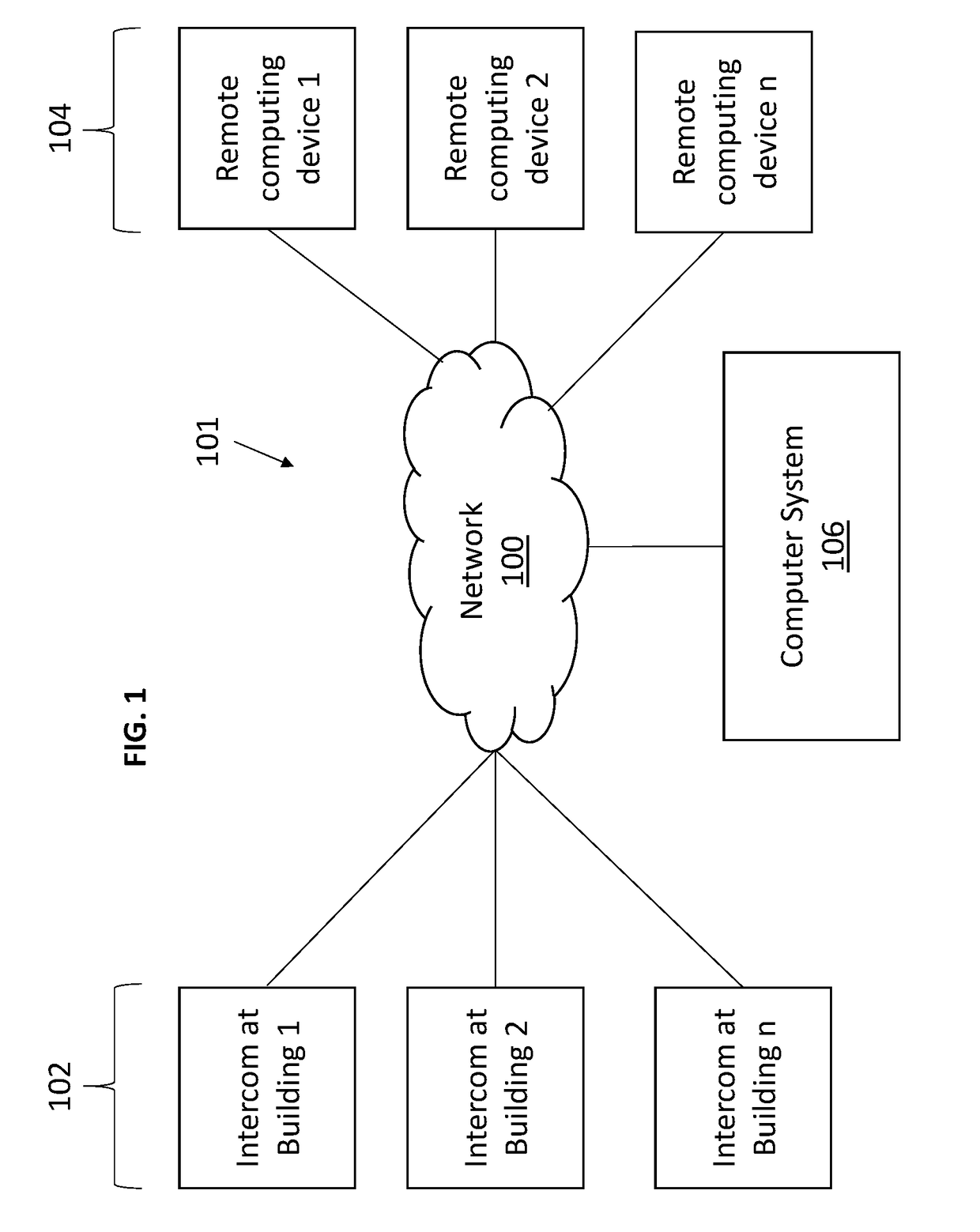
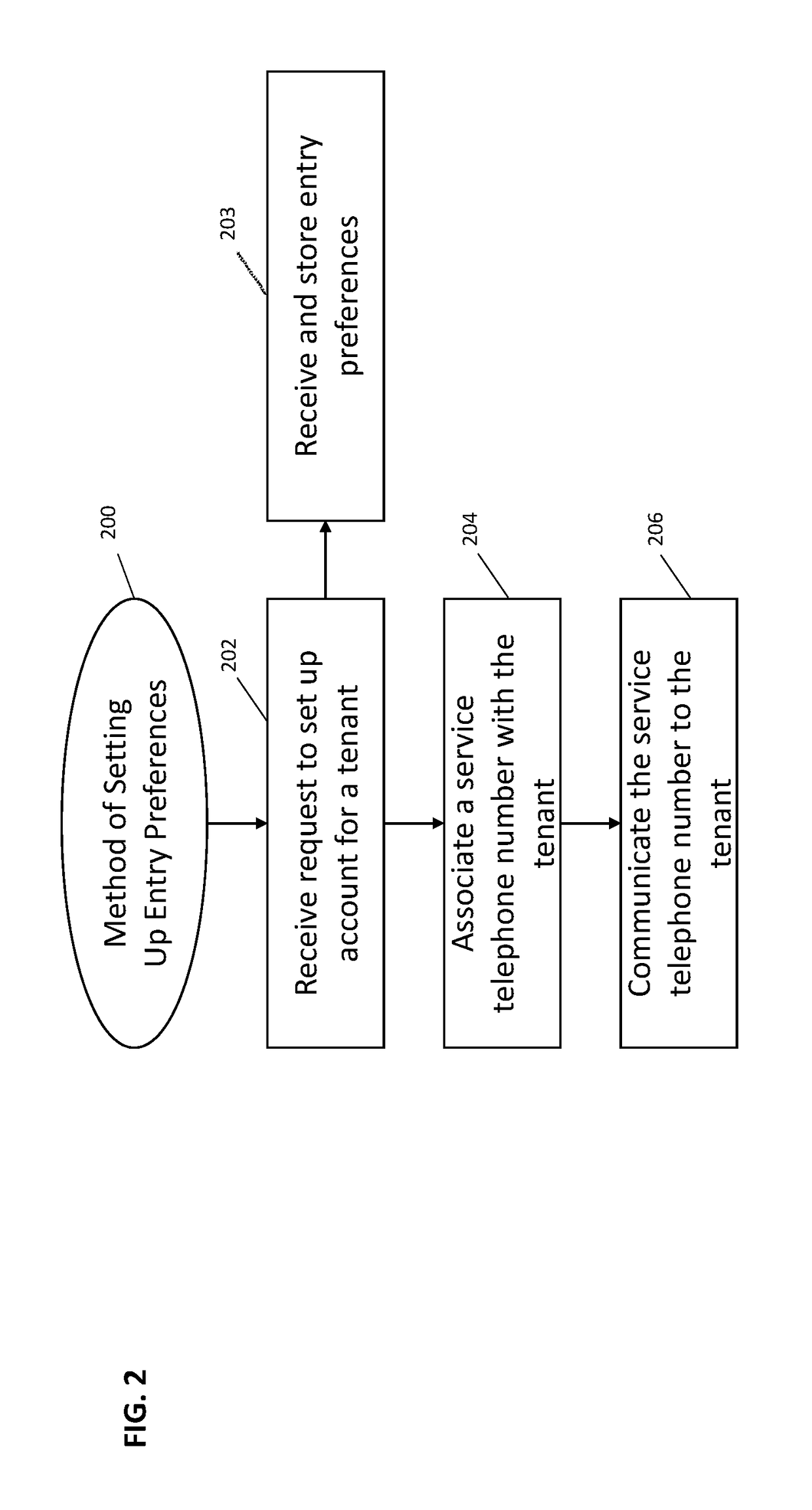
Door entry systems and methods
ActiveUS20170214801A1Efficient Safety ManagementSpecial service for subscribersInterconnection involving common lineThird partyMobile device
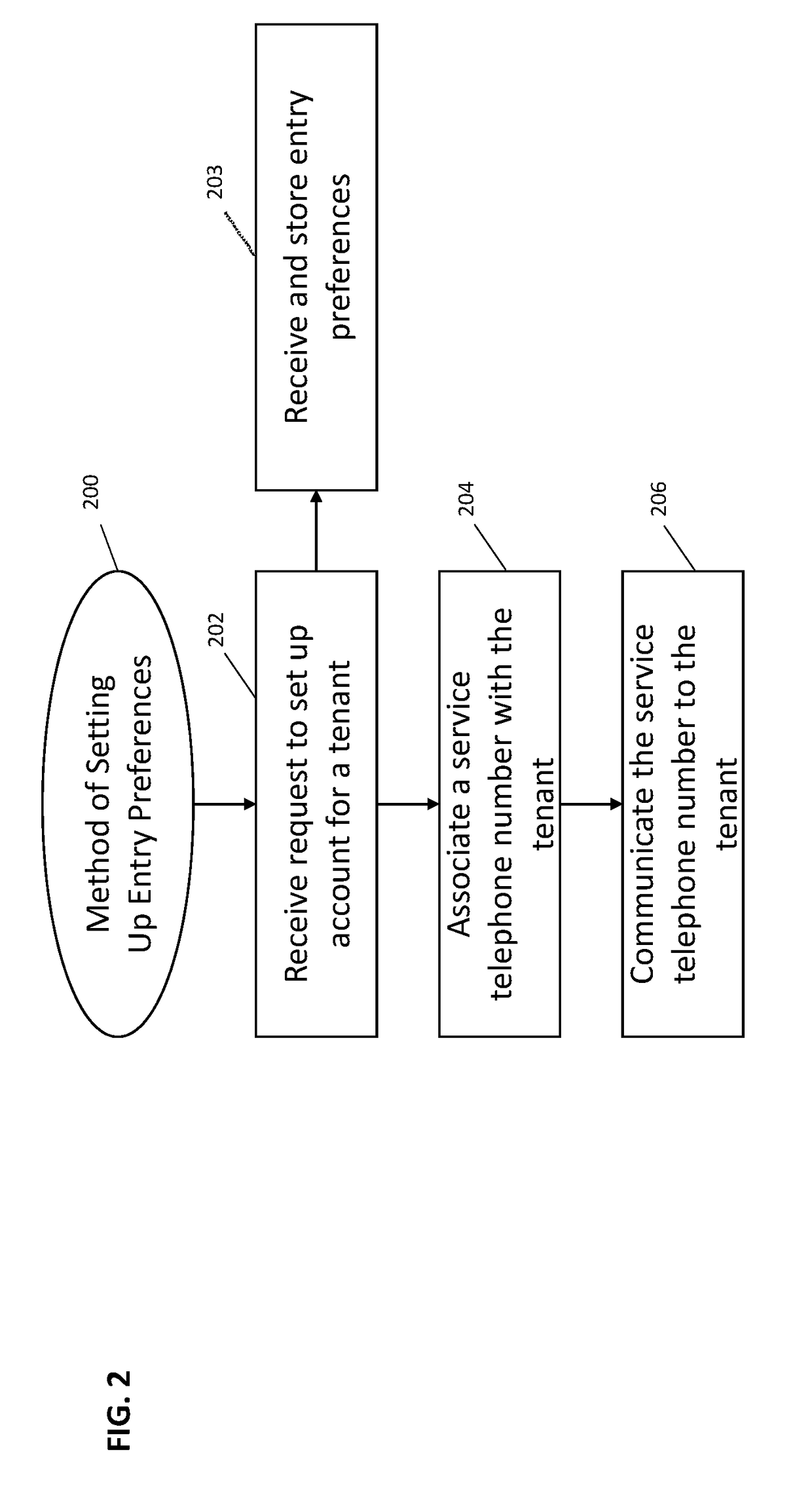
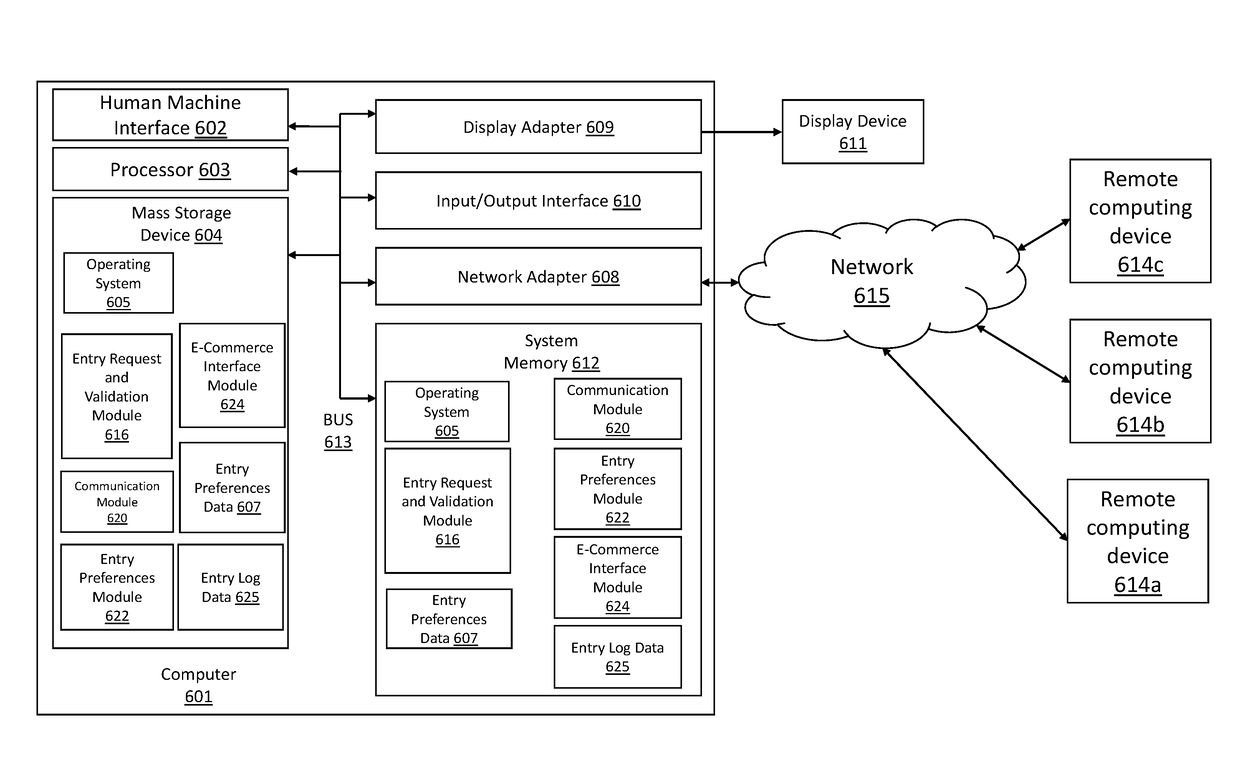
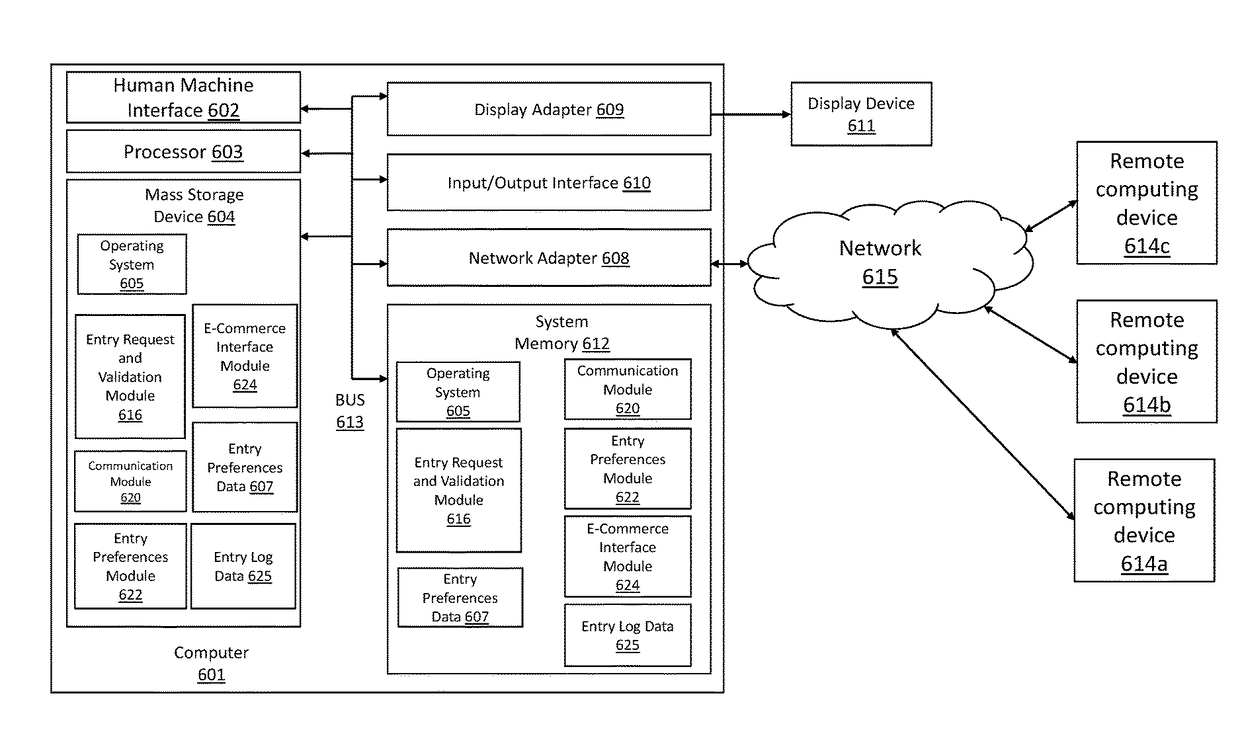
Various implementations include systems and methods for unlocking a door to a building on behalf of a tenant of the building that addresses the shortcomings of legacy telephone entry systems and allows for more efficient and safer management of building entry requests from third parties. In some implementations, the system taps into the legacy telephone entry systems to communicate with third parties seeking entry into the building. In some implementations, the system communicates with third party computing devices (e.g., stationary or mobile devices) to process entry requests. And, in some implementations, the system communicates entry preferences (or parameters) associated with a tenant with a door lock system to allow for entry during certain time windows or under certain conditions.
Owner:DROPBY INC
Door entry systems and methods
InactiveUS20170214802A1Efficient Safety ManagementInterconnection involving common lineSubstation equipmentThird partyMobile device
Various implementations include systems and methods for unlocking a door to a building on behalf of a tenant of the building that addresses the shortcomings of legacy telephone entry systems and allows for more efficient and safer management of building entry requests from third parties. In some implementations, the system taps into the legacy telephone entry systems to communicate with third parties seeking entry into the building. In some implementations, the system communicates with third party computing devices (e.g., stationary or mobile devices) to process entry requests. And, in some implementations, the system communicates entry preferences (or parameters) associated with a tenant with a door lock system to allow for entry during certain time windows or under certain conditions.
Owner:DROPBY INC
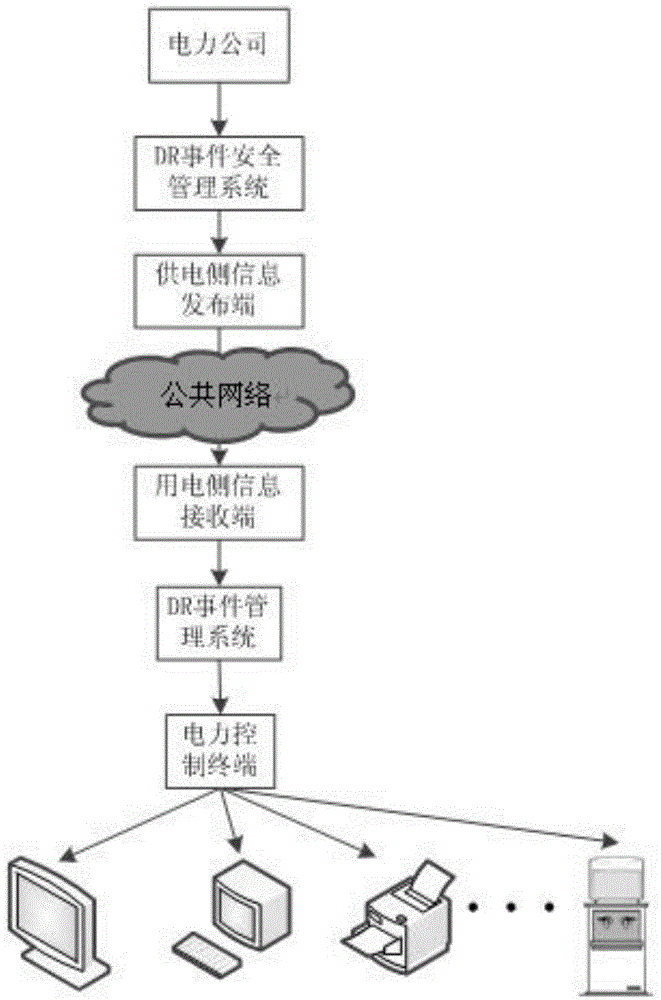
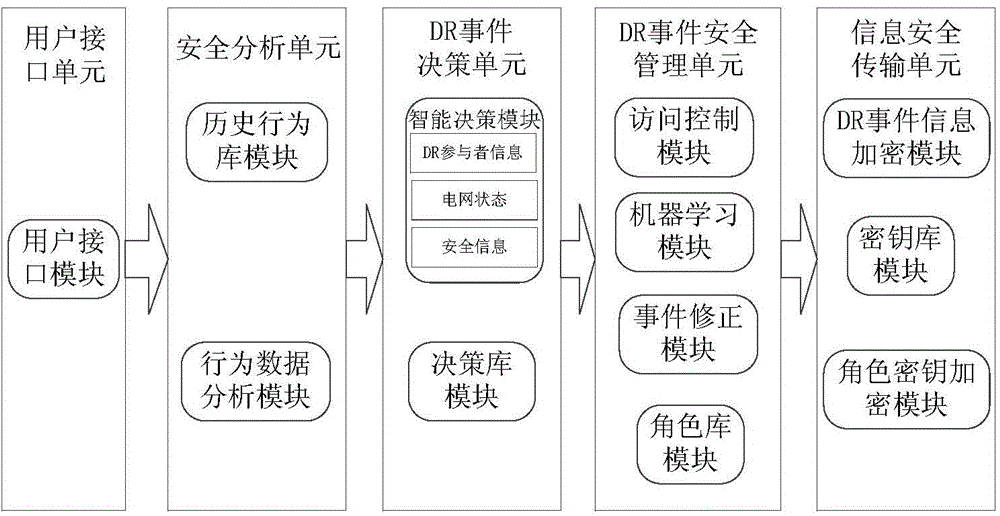
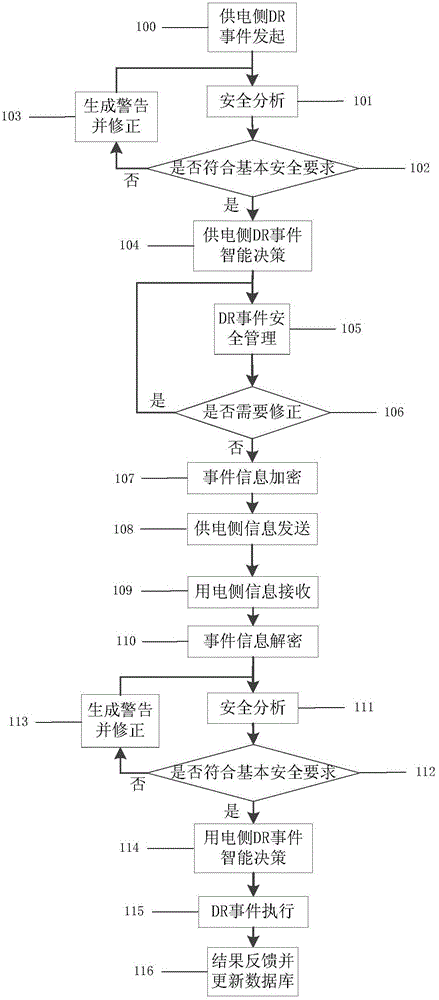
Demand response (DR) event safety management method and system based on role
ActiveCN104378356AEfficient Safety ManagementAvoid security issuesCircuit arrangementsUser identity/authority verificationPower usageSecurity validation
Provided is a demand response (DR) event safety management method and system based on a role. The DR event safety management method based on the role comprises the steps that safety analysis is carried out on a power supply side and a power utilization side, and an analysis result serves a basis of an intelligent decision of a DR event; the DR event serves as a logic user, a support vector machine (SVM) is adopted to carry out safety verification on the role of the DR event, and safety management is carried out on the information of the DR event based on the role; the role information of the DR event is used for encrypting the DR event, so that safe transmission of the information in a public network is guaranteed. A participant of the DR event at the power utilization side encrypts the information of the event, the intelligent decision is made for the DR event at the power utilization side while a safety analysis result of the participant of the DR event at the power utilization side serves as one of reference points, and the intelligent decision is executed; an execution result is fed back, and a historical behavior library is updated.
Owner:SHANGHAI JIAO TONG UNIV +1
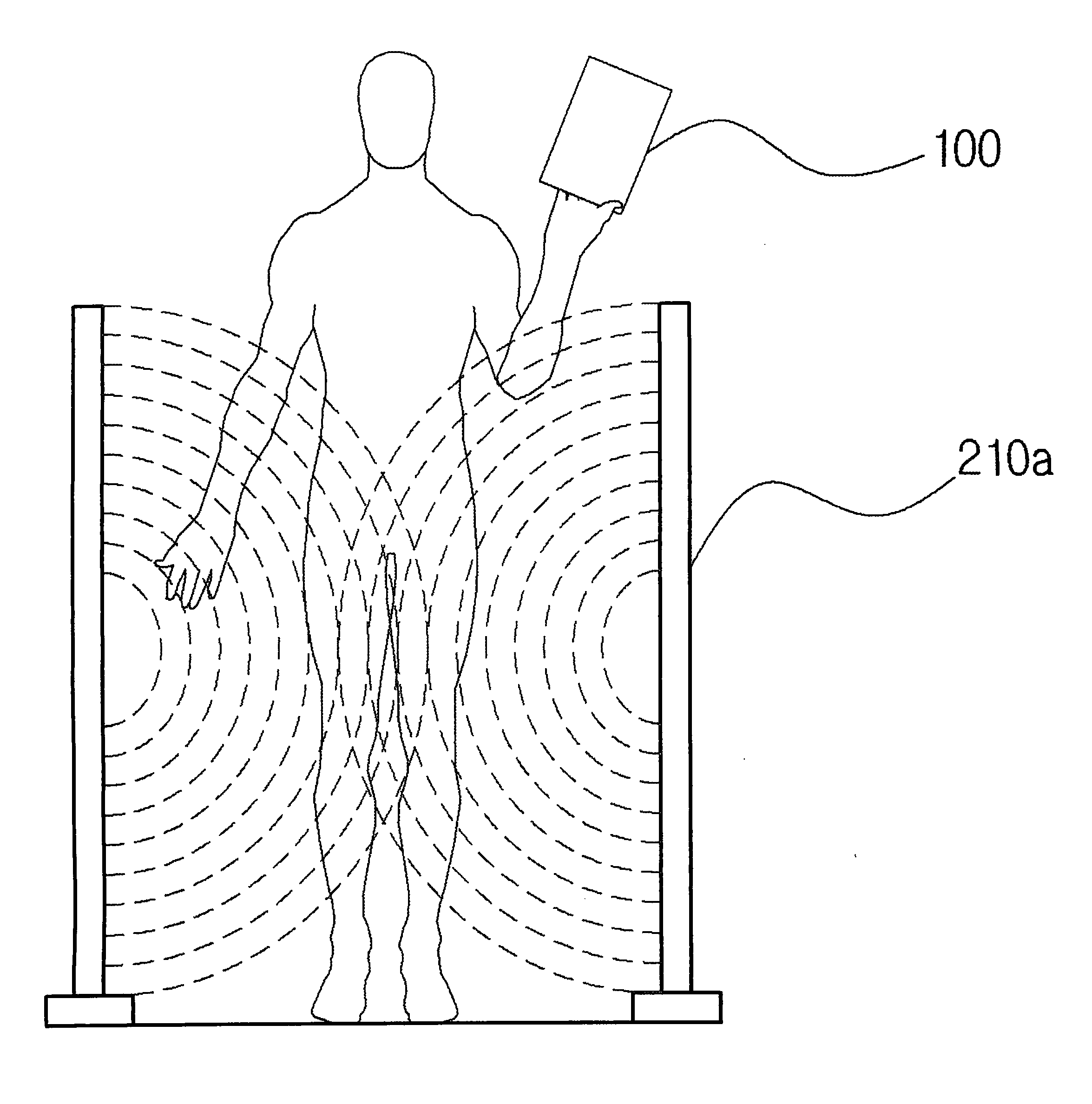
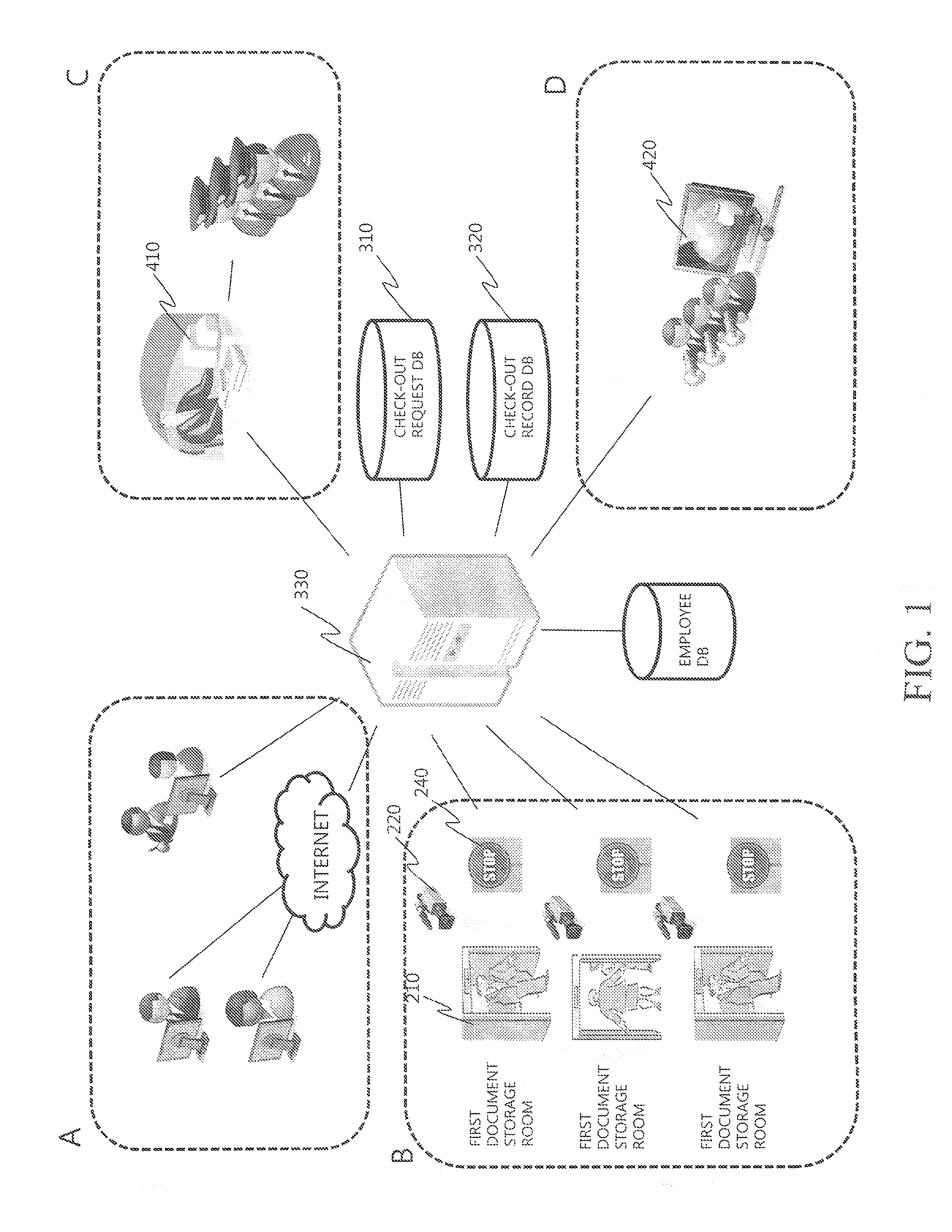
Security document control system and control method thereof
InactiveUS20110309910A1Efficient Safety ManagementAutomate regulationElectric signal transmission systemsDigital data processing detailsAutomatic controlControl system
A security document control system and a control method thereof are disclosed. The system functions to automatically control a series of security operations including sensing security documents, storing all records with respect to check-out of security documents in a database, closing exit gates if illegal removal of security documents is judged, and informing a control center and security guards of the illegal removal of security documents so as to arrest an employee who attempts to illegally remove security documents.
Owner:LEE YOUNG BUM
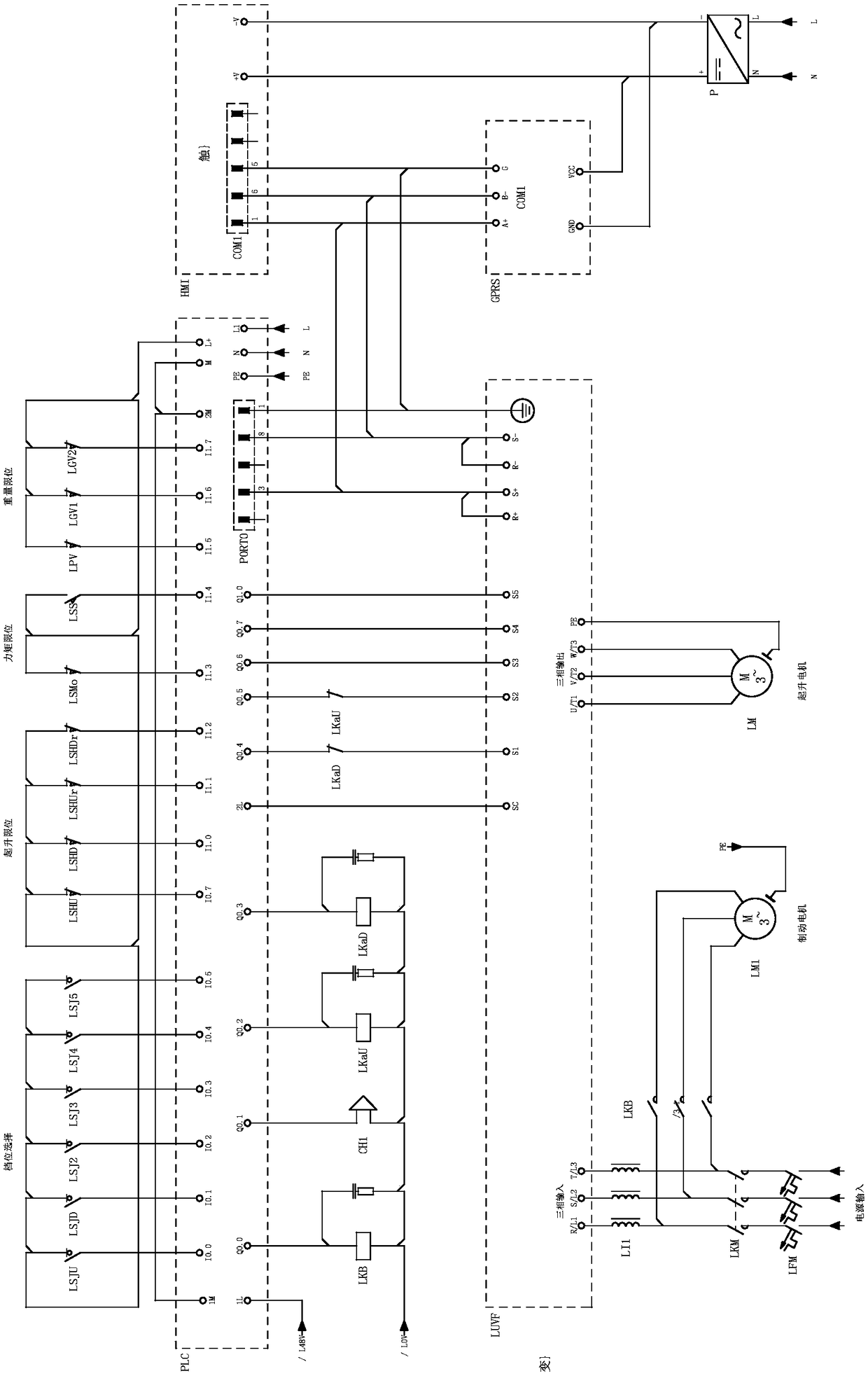
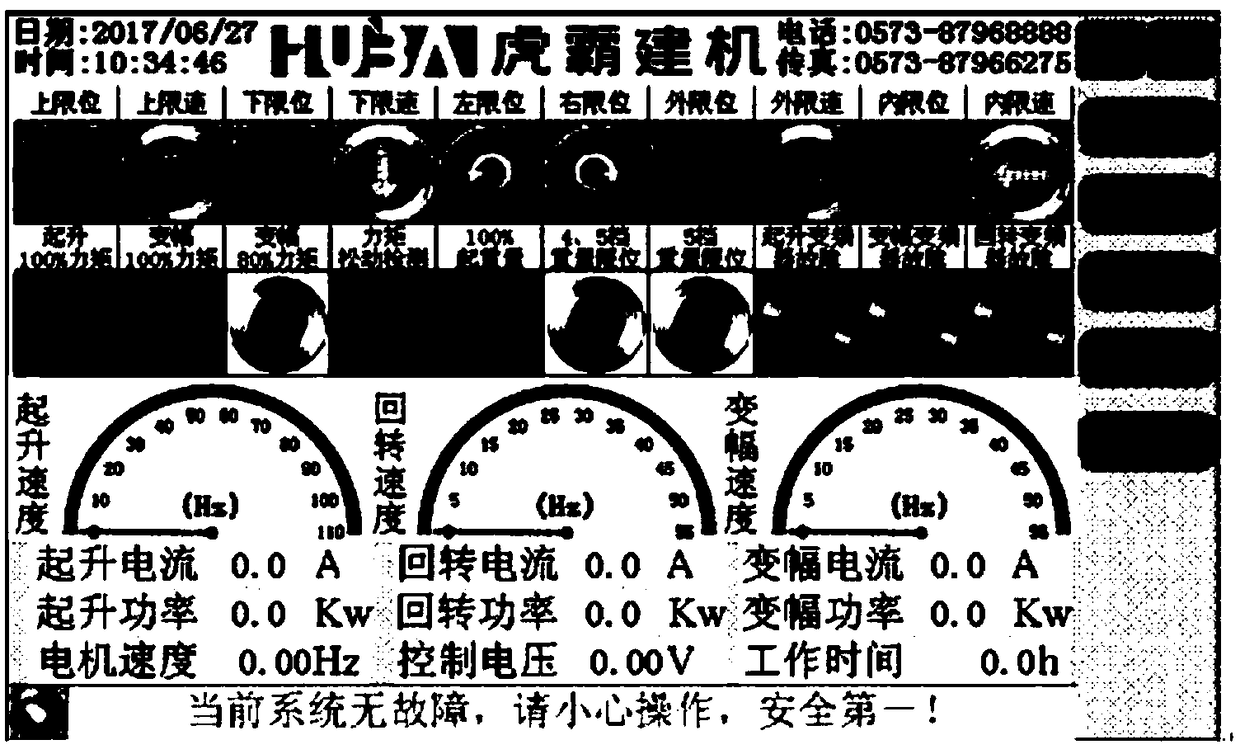
Electric remote fault diagnosis system of tower crane
InactiveCN108249329AUse intelligenceEasy to useLoad-engaging elementsCranesWireless dataAcousto-optics
The invention relates to an electric remote fault diagnosis system of a tower crane. The electric remote fault diagnosis system is characterized by comprising a computer terminal, a mobile phone APP,a cloud server, a wireless data transmitting module, a programmable controller, a touch screen, a frequency converter, an acousto-optic alarming machine, a circuit breaker, a relay, sensors and strokelimiters; the sensors and the stroke limiters are correspondingly installed at all positions of the tower crane; the frequency converter, the programmable controller and the touch screen communicatewith one another by virtue of a 485 bus communication technology; the programmable controller is used for acquiring signals of the frequency converter, the sensors and the stroke limiters and transmitting the signals to the touch screen and the wireless transmitting module; the wireless transmitting module realizes data interaction of the programmable controller and the cloud server and realizes short message control and short message remind functions by virtue of a GPRS wireless communication technology; and the touch screen is used for a driver to implement real-time image-text monitoring and fault diagnosis on the running state of the tower crane in a running process.
Owner:ZHEJIANG HUBA CONSTR MACHINERY
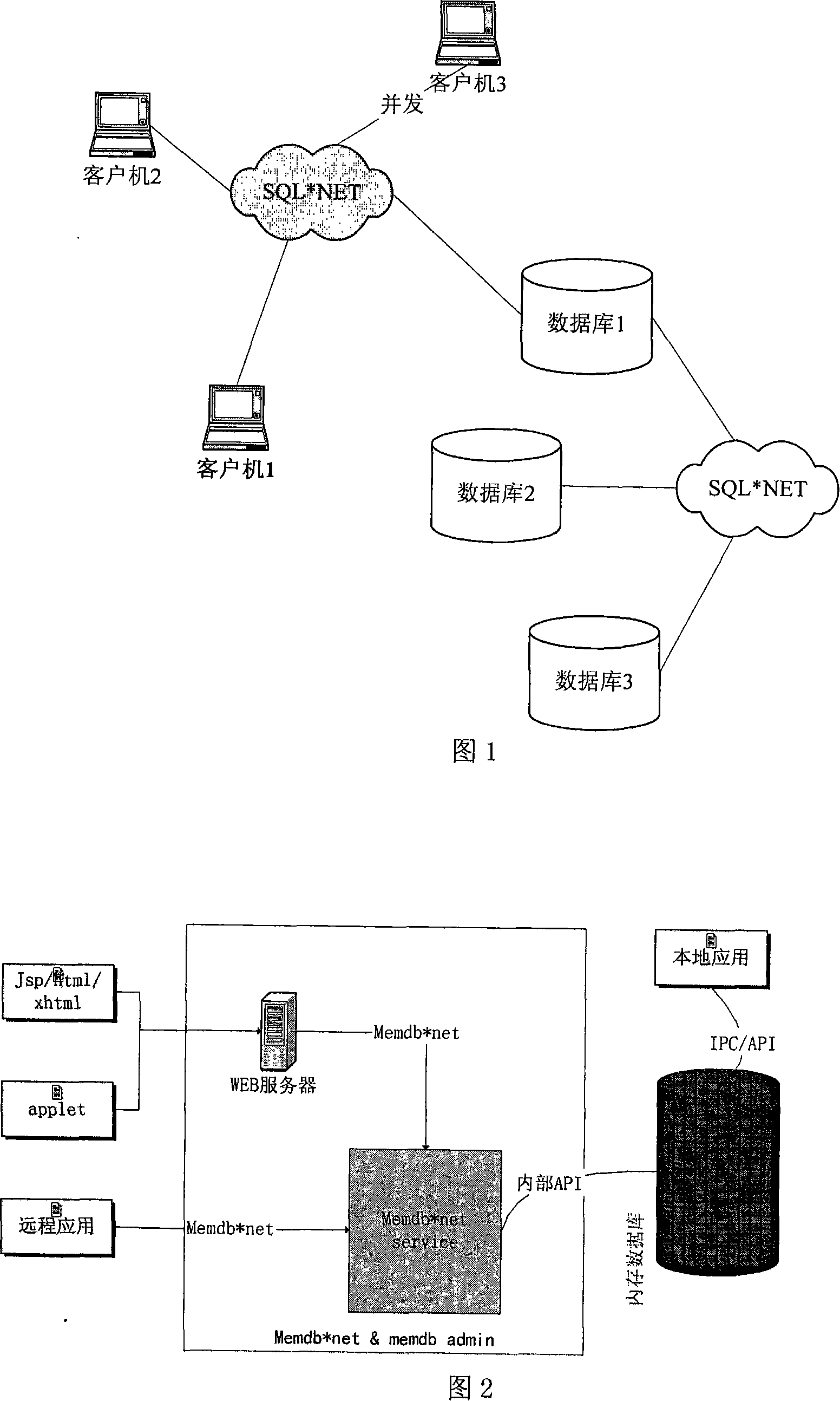
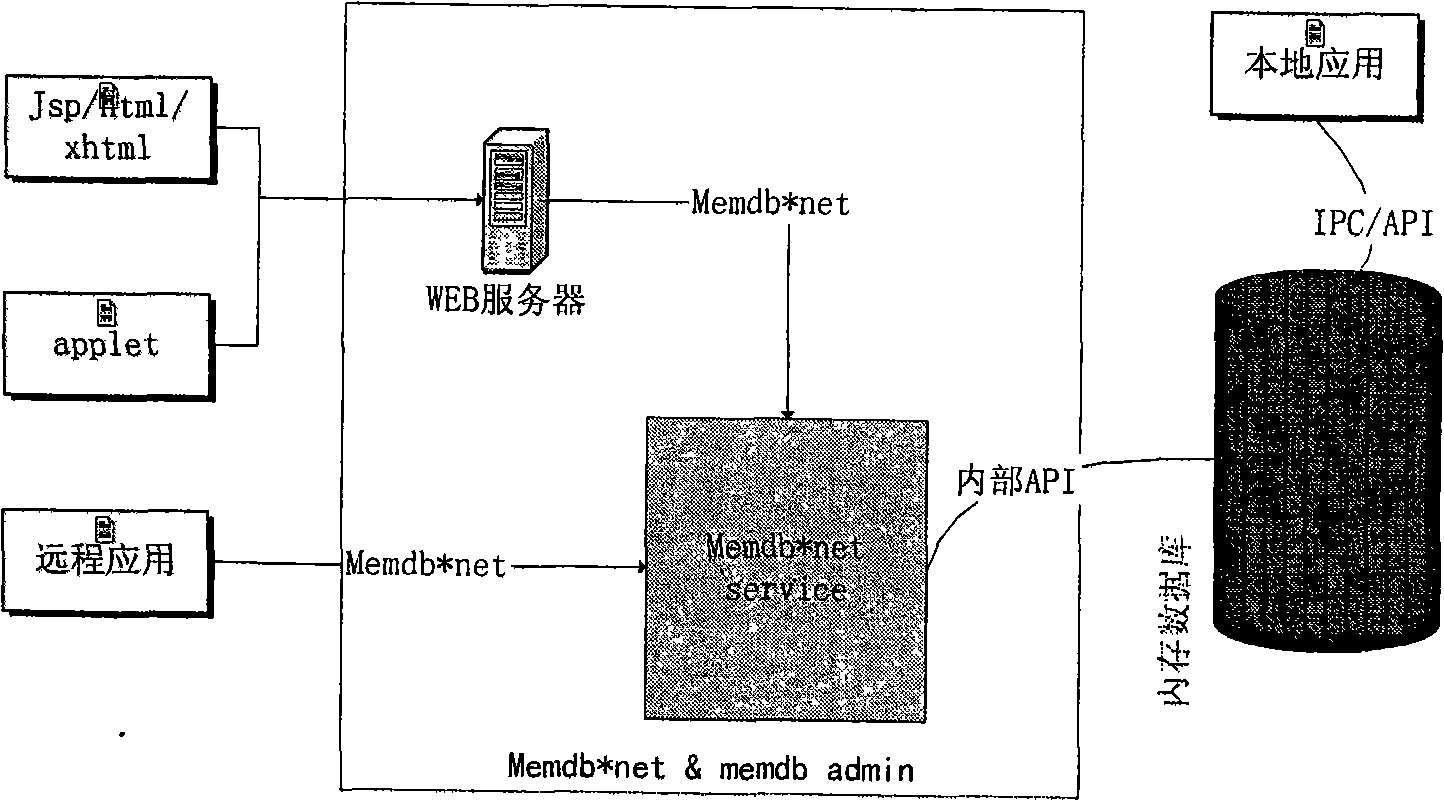
United interface based memory database remote concurrent access and interface management method
InactiveCN101119363AEfficient remote accessLoad balancingTransmissionSpecific program execution arrangementsIn-memory databaseMessage type
The present invention relates to a method based on an in-memory database long distance concurrent access and interface management which adopt the uniform port, which is characterized in that adopting the SOCKET communication means sets a set of complete message type interface, namely, MEMDB*NET protocol, the customer rightly organizes the message used for accessing the stored data according the protocol specifications, thereby having a remote access. Including the steps as follows: the message type network application layer protocol MEMDB*NET based on the TCP / IP organizes the message according to the protocol, and has an indirect communication with the in-memory database through MEMDB*NET SERVICE process, and accesses and manages the in-memory database; the MEMDB*ADMIN provided on the basis manages the in-memory database in the style of WEB interface. The useful effect of the present invention is a balanced load and an efficient management, in addition, increasing the friendliness of the interface, improving the satisfaction of the customer and advancing the stability.
Owner:ASIAINFO TECH NANJING
Smart dosimeter for coupling of legal dosimeter
InactiveCN108700671AAvoid inconvenienceSafe and reliable workDosimetersOptical detectionCommunication unitNuclear engineering
The purpose of the present invention is to provide a smart dosimeter for coupling of a legal dosimeter, wherein: the structure of the smart dosimeter is such that a legal dosimeter can be attached andcoupled to the smart dosimeter, and the smart dosimeter and the legal dosimeter are used as if they were incorporated into one structure; whether a worker wears the legal dosimeter is detected by a sensor provided in the smart dosimeter; and an instantaneous exposed dose value can be checked in real time so as to assist a worker to more safely perform an operation. The present invention comprises: a motion detection unit for detecting a motion; a legal dosimeter detection unit for checking whether a legal dosimeter is coupled and fixed to a coupling part included in the smart dosimeter; a wearing check unit for checking whether a radiation worker is wearing the legal dosimeter on the basis of motion information detected by the motion detection unit and coupling / fixation information checked by the legal dosimeter detection unit; a G-M detection unit for measuring and detecting the real-time exposed dose of the radiation worker; and a data communication unit for transmitting the exposeddose detected by the G-M detection unit to a management server and receiving warning situation information from the management server.
Owner:LENIVEN
Junction box for solar cell module and method for driving same
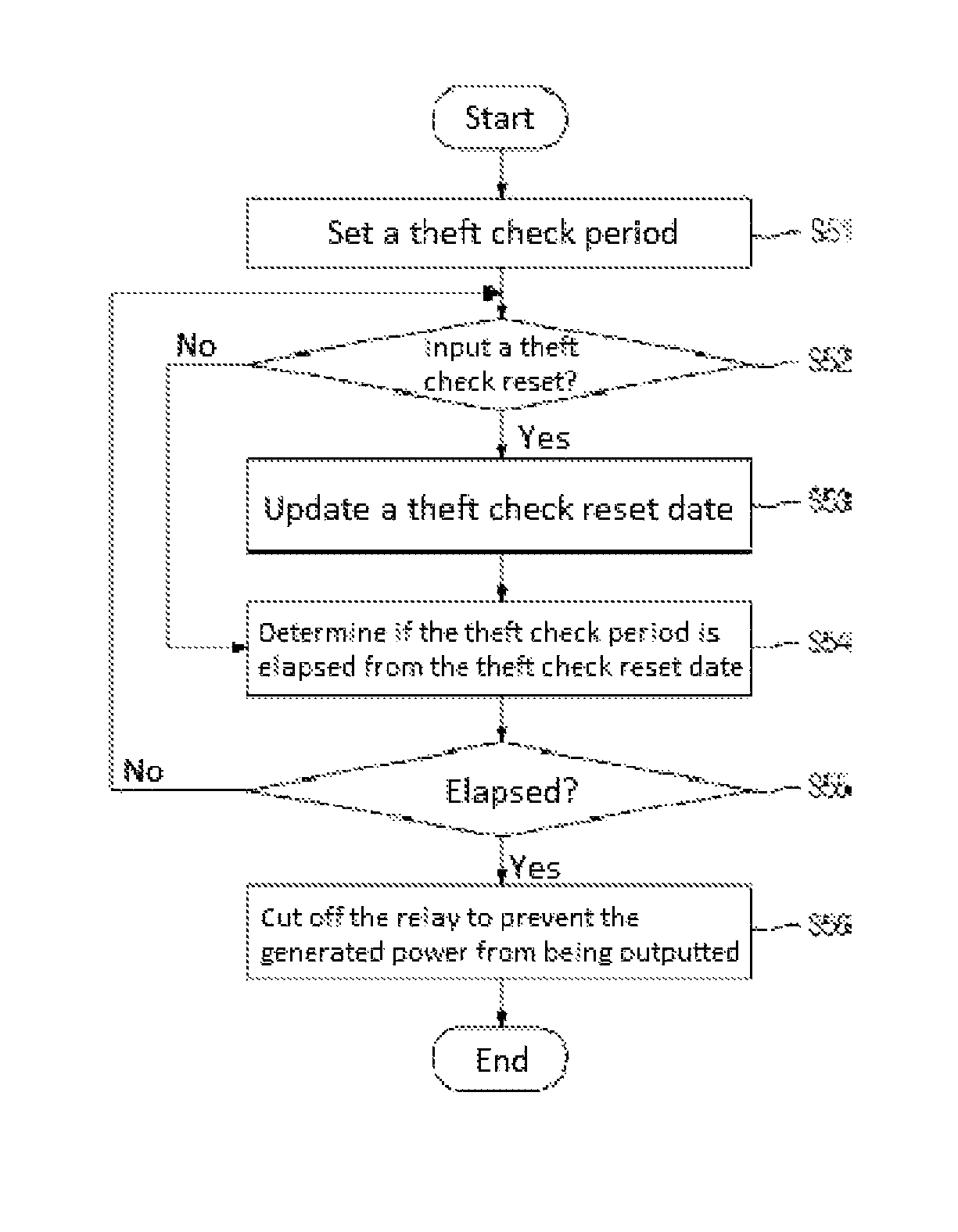
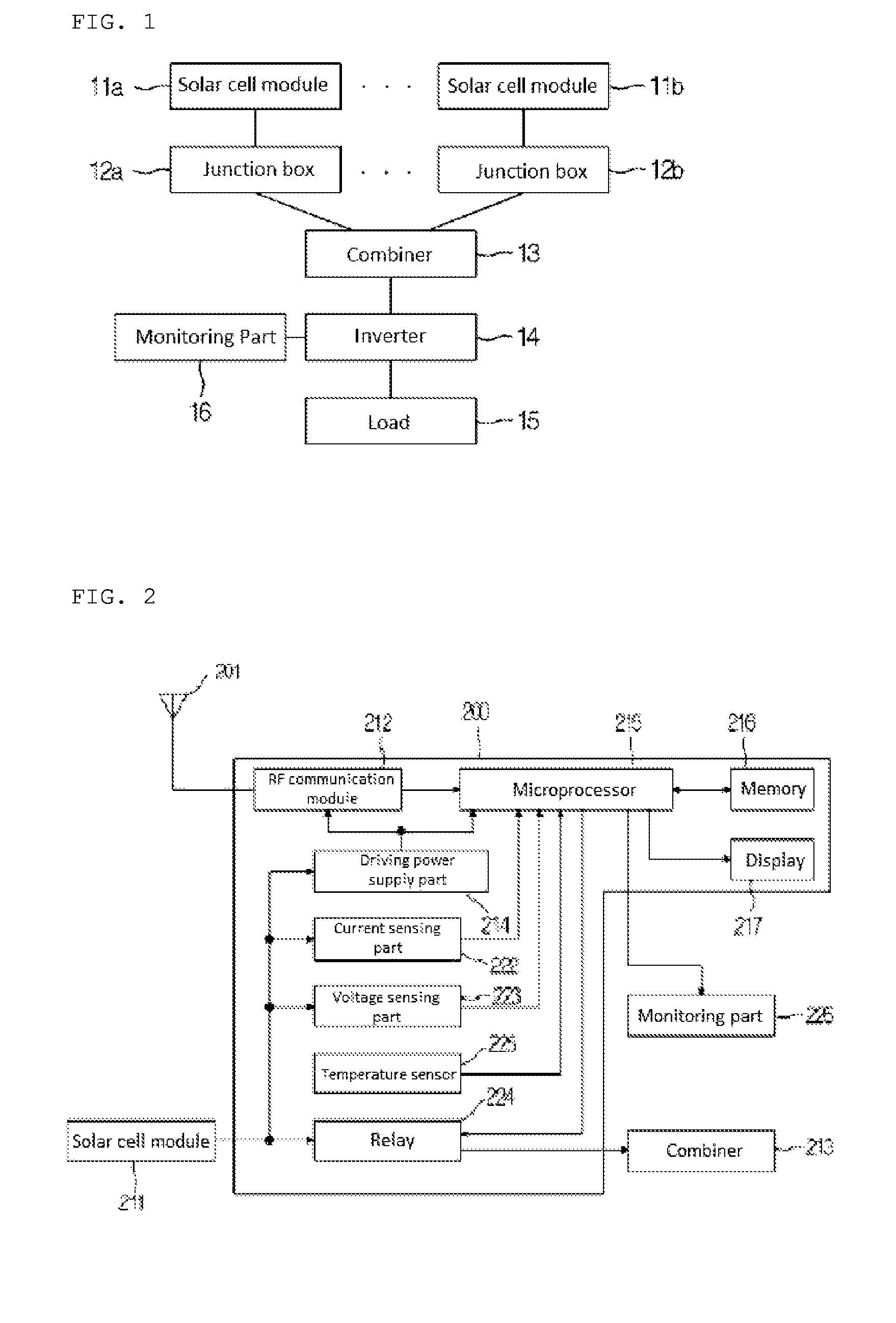
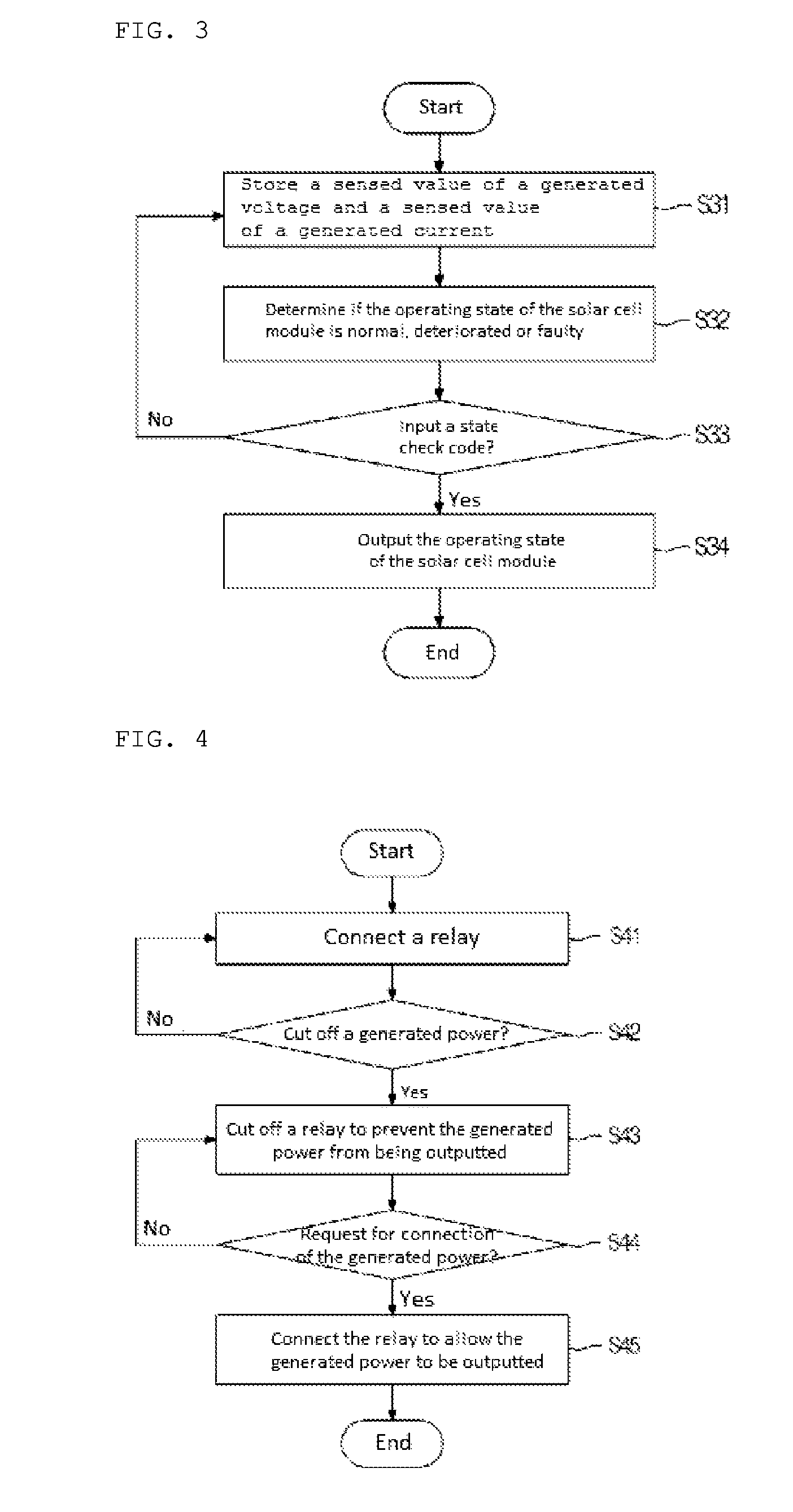
ActiveUS9571032B2Efficient Safety ManagementPrevent theftPhotovoltaic monitoringPower supply testingControl signalElectrical battery
The present invention relates to a junction box for a solar cell module which receives a command of a manager from the outside, controls the solar cell module, displays an operating state of the solar cell module, and implements an anti-theft function, a fire prevention function, etc. of the solar cell module, and a method for driving the same. The junction box for a solar cell module according to the present invention comprises: a relay installed between a solar cell module and a combiner for connecting the solar cell module and the combiner for blocking the connection therebetween according to a control signal transmitted from the outside; an RF communication module for signal-processing a data signal transmitted from the outside and extracting solar cell module information and a command of a manager; and a microprocessor for controlling an operation of the relay so that the relay connects the solar cell module and the combiner or blocks the connection therebetween according to the command of the manager extracted from the RF communication module.
Owner:LETO SOLAR
Highway traffic safety management terminal
InactiveCN103280103AExtended service lifeEffective safety managementArrangements for variable traffic instructionsDriving safetyMagnet
A highway traffic safety management terminal belongs to the technical field of traffic safety management. The highway traffic safety management terminal aims to solve the problems that an existing highway traffic safety management device can not meet installing requirements in a vehicle, is easily damaged, and is unsatisfactory in using effect. The management terminal is composed of an information collecting device and an information receiving device. The information collecting device is used for collecting highway traffic safety information, and the information receiving device is used for receiving the highway traffic safety information. A base is arranged at the bottom of a shell of the information collecting device. A magnet is arranged at the bottom of the base. A central processing unit is arranged inside the shell and respectively connected with a wireless emitter and a temperature sensor through a connecting wire. The temperature sensor is used for detecting temperature of a vehicle body. The information receiving device comprises a wireless receiver and a computer, and the wireless receiver is connected with the computer through the connecting wire. The highway traffic safety management terminal is used for highway traffic safety management.
Owner:哈尔滨智晟天诚科技开发有限公司
Linear engineering labor service supervision system
InactiveCN108648294AProtection of personal rightsSolving Labor Regulation IssuesChecking time patrolsLocation information based serviceInformatizationComputer terminal
The invention discloses a linear engineering labor service supervision system, and relates to the field of construction engineering. The system comprises a mobile terminal connected with a card reader, and a corresponding microcircuit card; the mobile terminal is connected with the server to form a data channel; and the built-in module of the mobile terminal acquires data in the microcircuit cardthrough the card reader, sends a message to the server according to the data, and obtains the feedback of the server. The system effectively solves the labor service supervision problem during linearconstruction engineering construction, realizes real-name system supervision of labor services in the manner of low cost, intelligence and informatization, and also can solve the record problems of attendance, safety education, pre-class education and onsite violations of labor workers. The system can be used to trace back the safety management responsibility problems of certain safety incidents in order to truly ensure the personal rights and interests of the workers.
Owner:THE FIRST COMPARY OF CHINA EIGHTH ENG BUREAU LTD
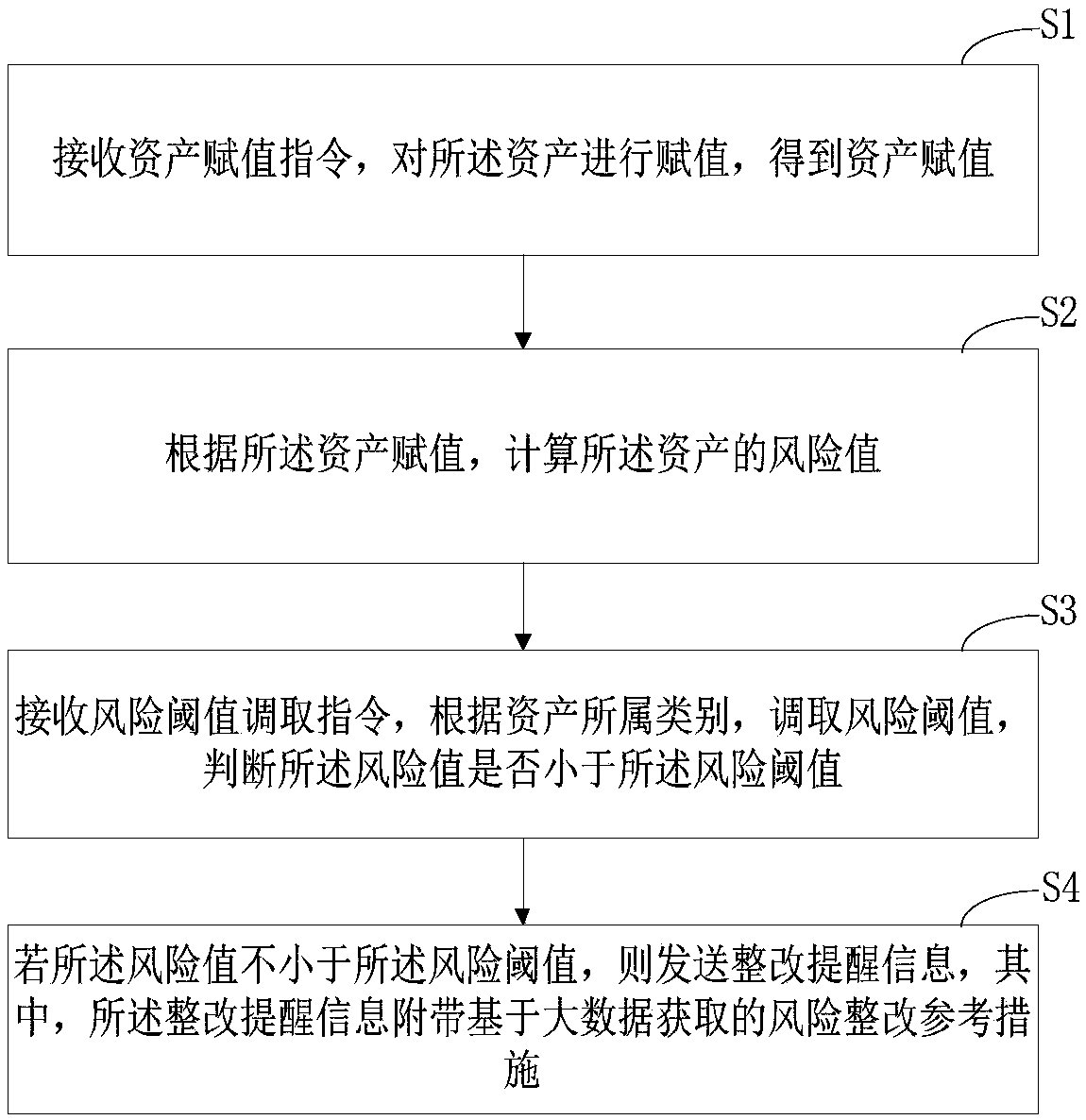
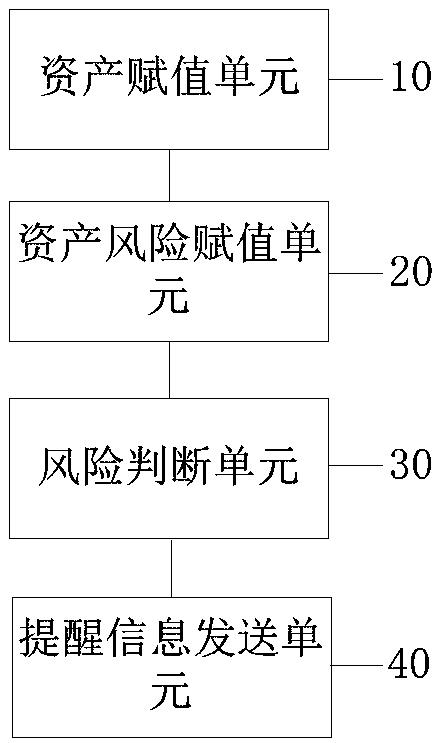
Asset security management method, apparatus and computer device based on big data
The present application discloses an asset security management method, apparatus and computer device based on big data. The method includes: receiving an asset assignment instruction, assigning the asset, and obtaining the asset assignment; Calculating a risk value of the asset according to the asset assignment; Receiving a risk threshold calling instruction, according to a category to which the asset belongs, calling a risk threshold, and judging whether the risk value is less than the risk threshold; If the risk value is not less than the risk threshold, a rectification reminder message is sent, wherein the rectification reminder message is provided with a risk rectification reference measure based on big data acquisition, thereby realizing efficient and high-standard safety management.
Owner:PING AN TECH (SHENZHEN) CO LTD
Efficient safety management system for fuel gas net
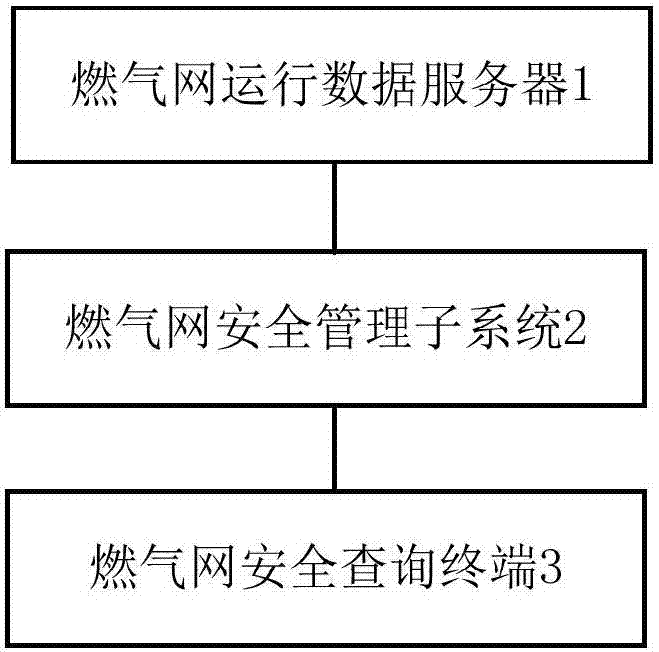
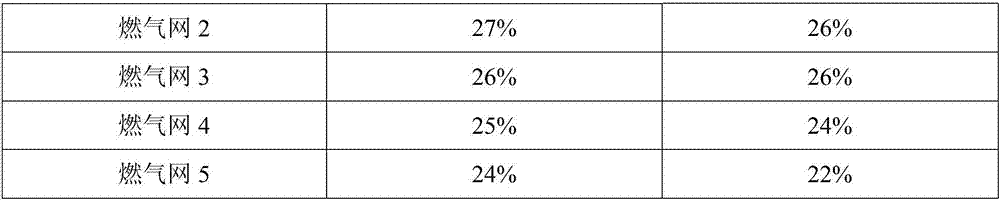
InactiveCN107993015AEfficient Safety ManagementEfficient queryResourcesAutomotive engineeringSafety management systems
The invention provides an efficient safety management system for a fuel gas net. The system comprises a fuel gas net running data server, a fuel gas net safety management subsystem and a fuel gas netsafety query terminal, the fuel gas net running data server and the fuel gas net safety query terminal are connected with the fuel gas net safety management subsystem through an internet separately, and the fuel gas net running data server is used for providing running parameters of the fuel gas net; the fuel gas net safety management subsystem is used for conducting safety management on the fuelgas net according to the running parameters of the fuel gas net, and the fuel gas net safety query terminal is used for querying the safety management condition of the fuel gas net. The efficient safety management system for the fuel gas net has the advantage that efficient safety management and management condition query for the fuel gas net are achieved.
Owner:朱明君
Certificate application management method
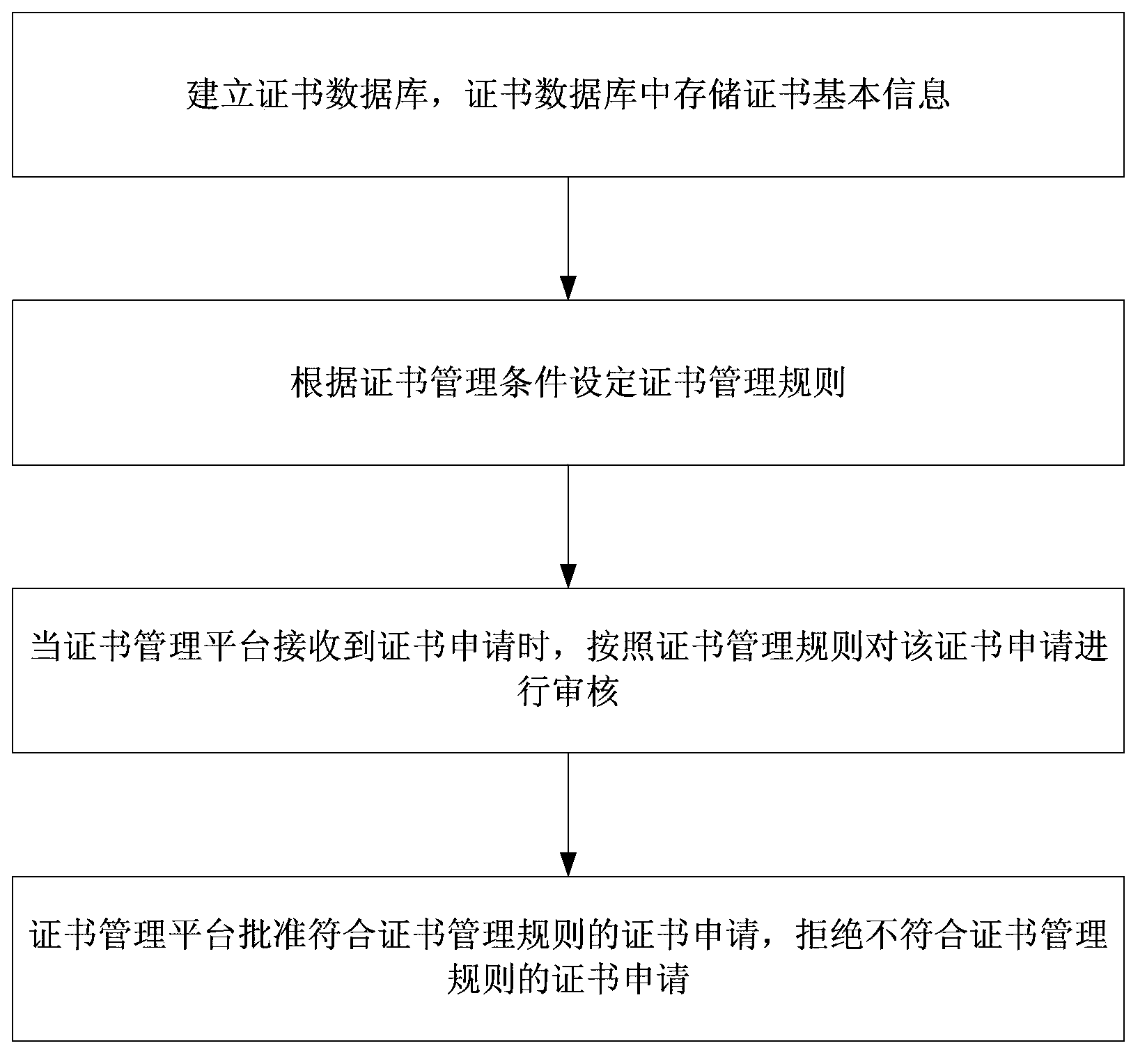
InactiveCN103854102AEffective safety managementEfficient Safety ManagementOffice automationResourcesOperating systemData library
The invention discloses a certificate application management method which includes the following steps: establishing a certificate database in which certificate basic information is stored; setting a certificate management rule according to certificate management conditions; when a certificate management platform receives certificate applications, checking the certificate applications according to the certificate management rule; the certificate management platform approving the certificate applications which comply with the certificate management rule and rejecting certificate applications which do not comply with the certificate management rule. Implementation of the technical scheme has the following beneficial effects: establishing the certificate database in which the certificate basic information is stored; setting the certificate management rule according to the certificate management conditions; when the certificate management platform receives the certificate applications, checking the certificate applications according to the certificate management rule; and the certificate management platform approving the certification applications which comply with the certificate management rule and rejecting the certification applications which do not comply with the certificate management rule so that effective and safe management of the certificates can be realized.
Owner:DALIAN HAMKOO INFORMATION TECH
Computer security management method and device
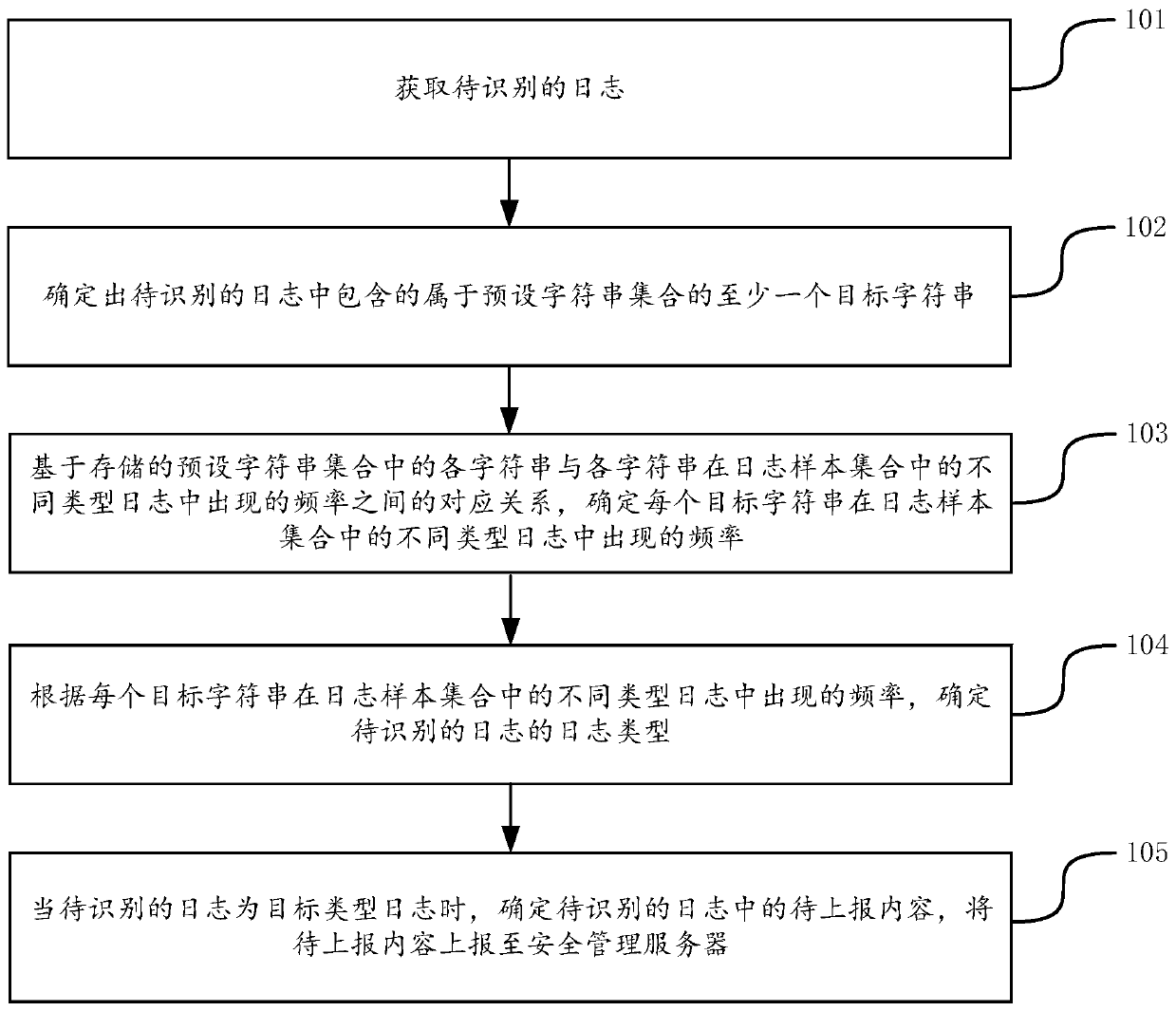
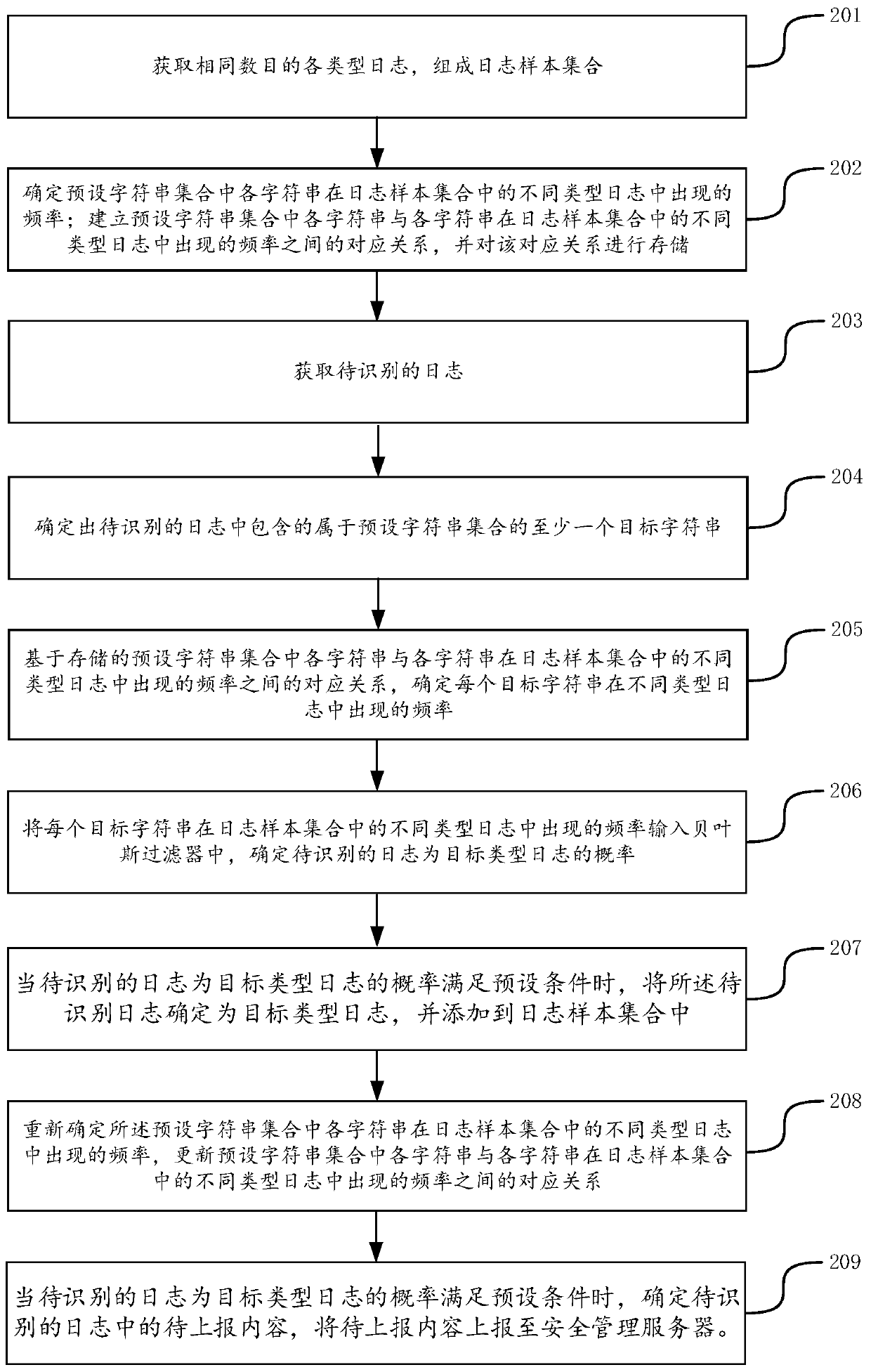
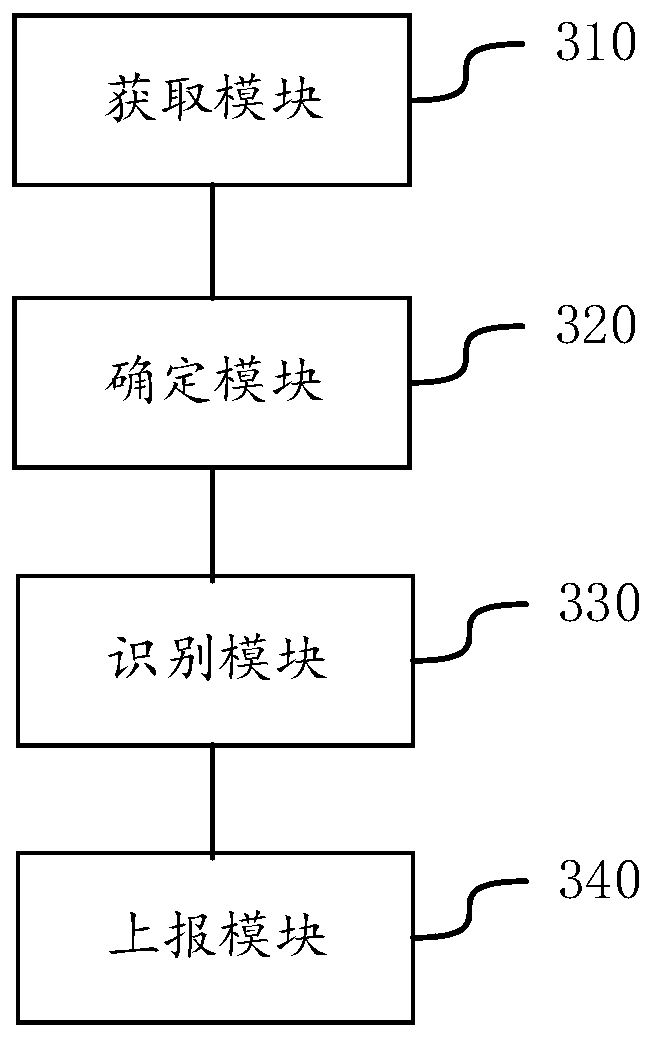
PendingCN110750691AEfficient Safety ManagementNo manual executionPlatform integrity maintainanceOther databases queryingProgramming languageEngineering
The invention discloses a computer security management method and device, and belongs to the technical field of computers. The method comprises the steps of obtaining a to-be-identified log; determining at least one target character string belonging to a preset character string set and contained in the log to be identified; determining the frequency of each target character string appearing in different types of logs in the log sample set based on the corresponding relationship between each character string in the stored preset character string set and the frequency of each character string appearing in different types of logs in the log sample set; determining the log type of the log to be identified according to the occurrence frequency of each target character string in different typesof logs in the log sample set; and when the to-be-identified log is the target type log, determining to-be-reported content in the to-be-identified log, and reporting the to-be-reported content to a security management server. The log identification efficiency in the computer security management process can be improved, so that the computer security management efficiency is improved.
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
Laboratory safety real-time monitoring system
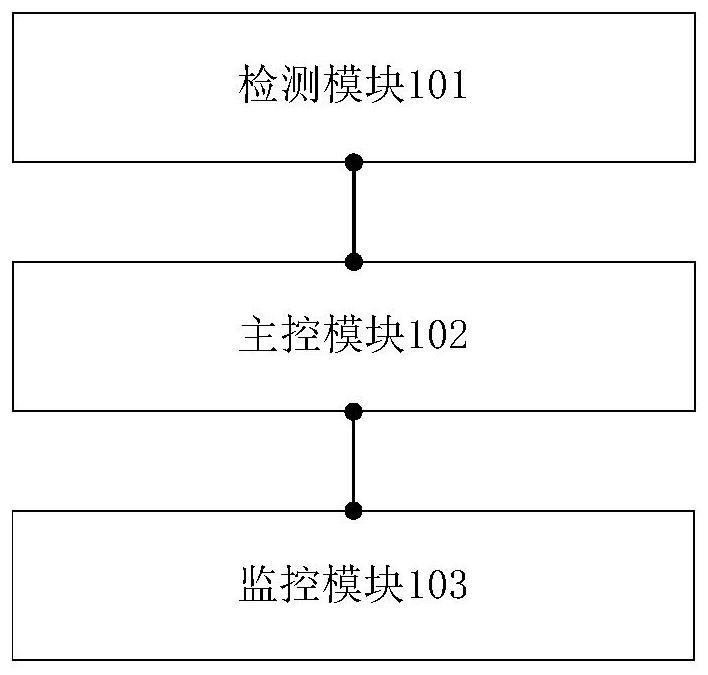
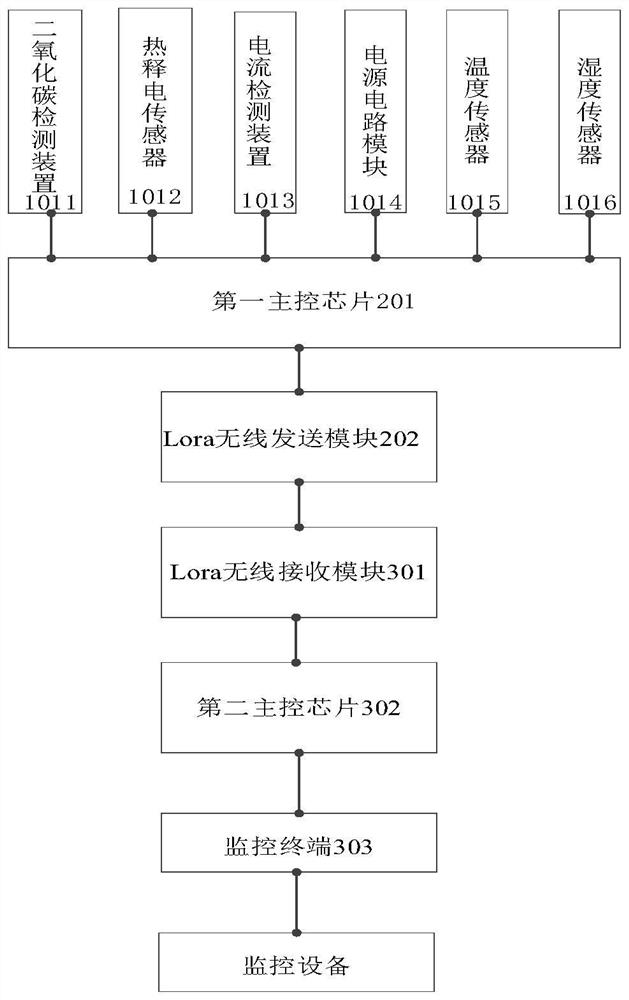
PendingCN113432655AEfficient Safety ManagementLow costMeasurement devicesTransmission systemsReal-time computing
The invention provides a laboratory safety real-time monitoring system which comprises: a detection module, which comprises a plurality of detection devices and is used for collecting safety parameters of preset times according to a preset collection period; a main control module, which is connected with the detection module and used for calculating the average value of the safety parameters and sending the average value of the safety parameters to the monitoring module; and a monitoring module, which is wirelessly connected with the main control module, and is used for displaying an average value of the safety parameters, judging whether the laboratory is abnormal or not according to a comparison result of the average value of the safety parameters and preset threshold values corresponding to the safety parameters, and when the laboratory is abnormal, reminding the management personnel of the safety risk of the laboratory, and taking corresponding measures are in time. The technical problem that an existing laboratory safety monitoring system cannot achieve safety management of the laboratory in time and efficiently is solved, the implementation cost is lower, and the application range is wider.
Owner:GUANGDONG UNIV OF TECH
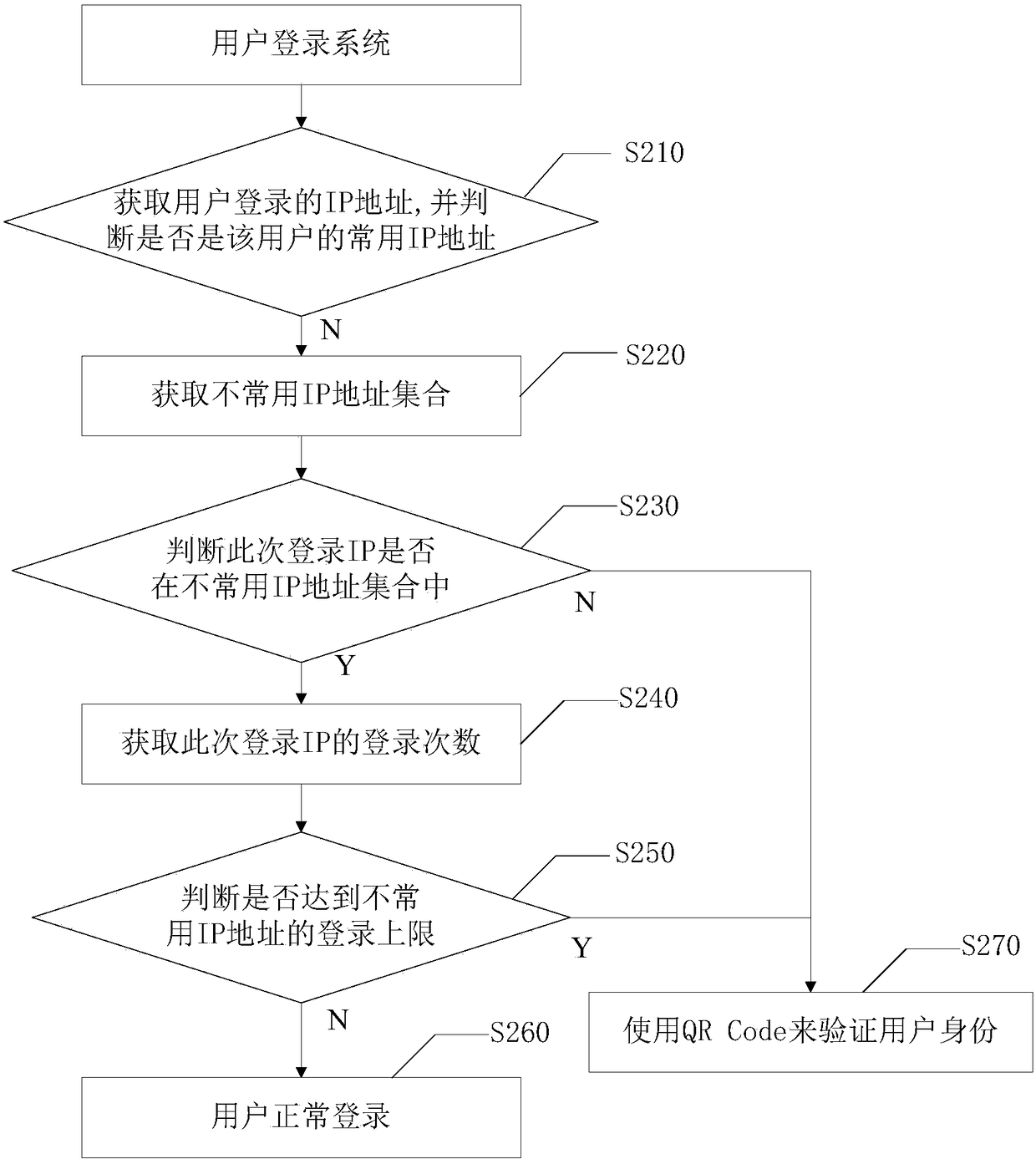
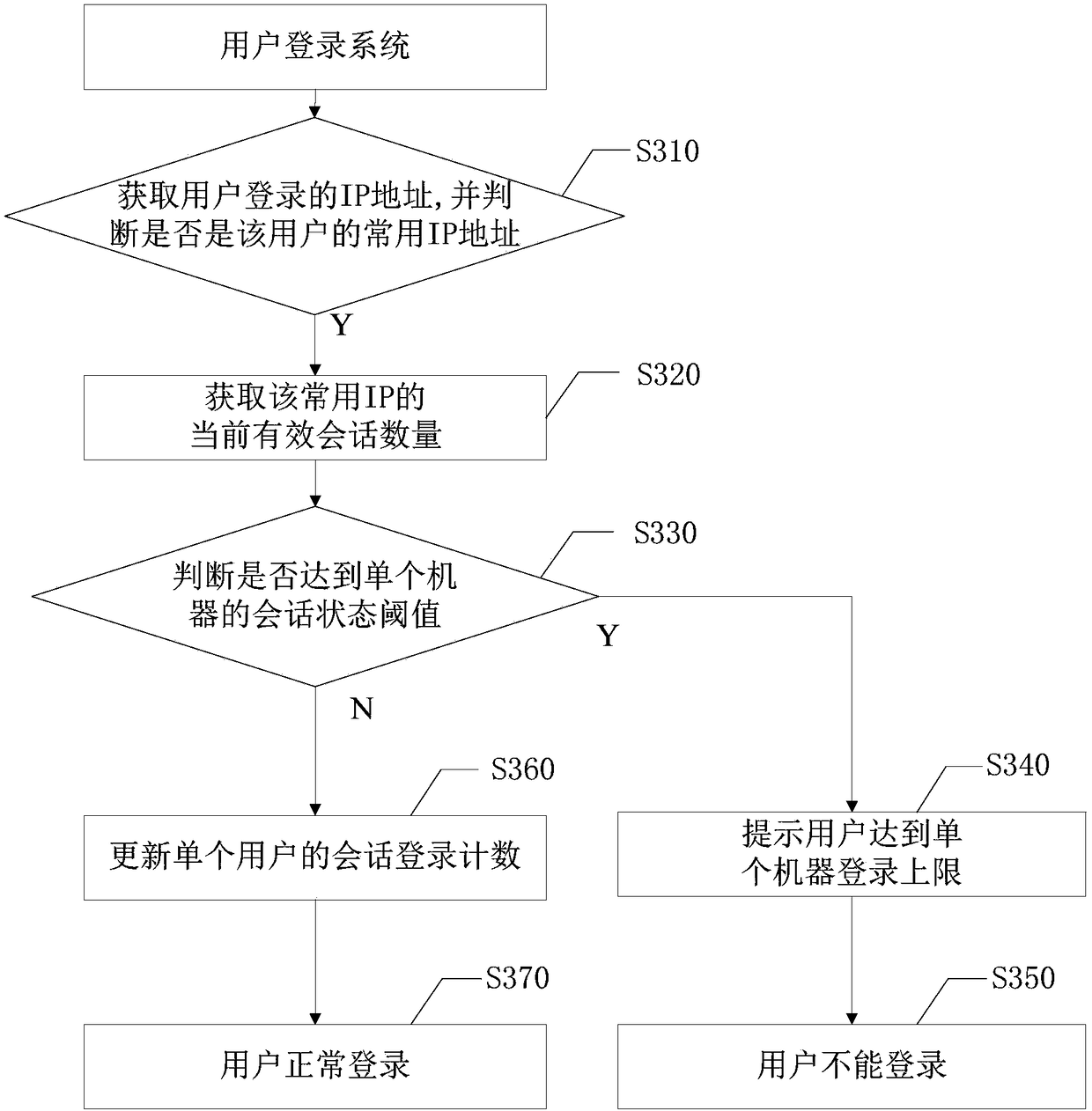
Method and apparatus for managing user login security, electronic device, and computer readable medium
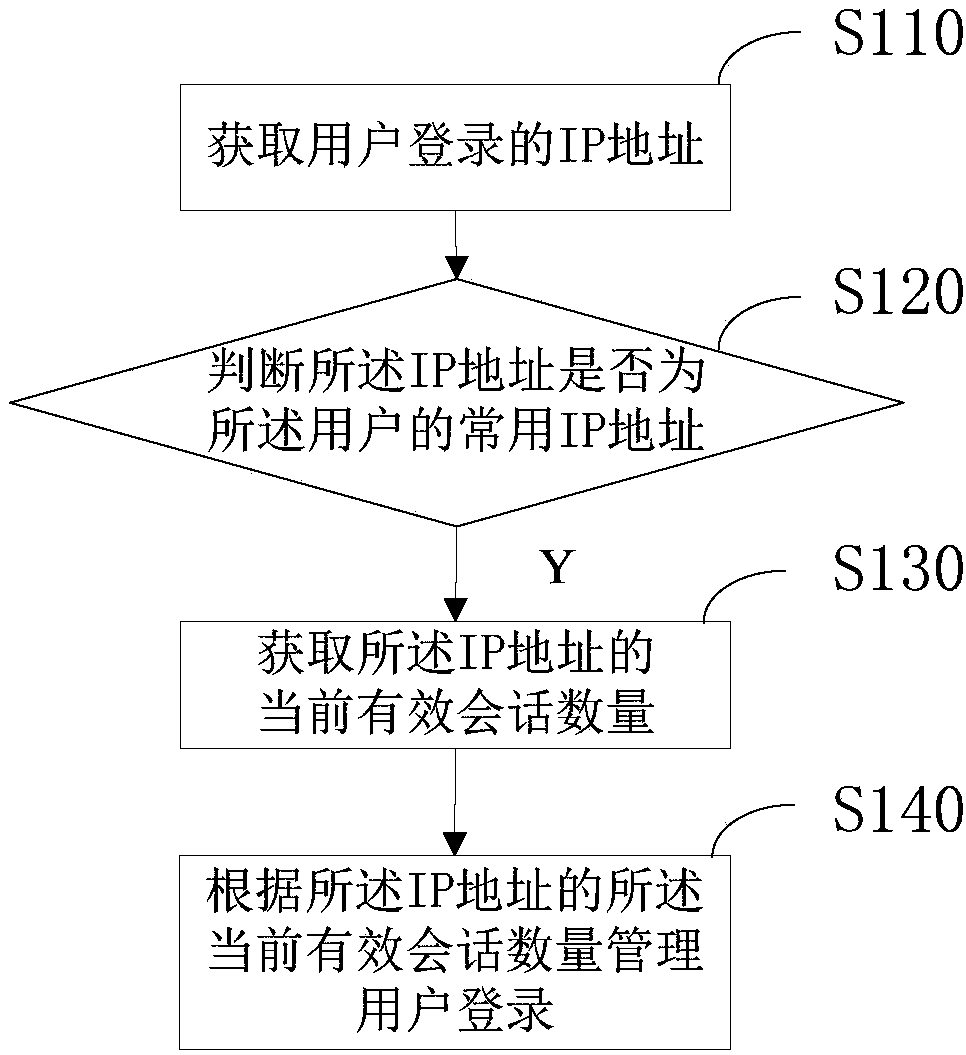
ActiveCN108449367AEfficient Safety ManagementManage login securityTransmissionIp addressComputer science
The invention provides a method and apparatus for managing user login security, an electronic device, and a computer readable medium. The method comprises the following steps: obtaining an IP addressof user login; judging whether the IP address is a common IP address of the user; and if it is judged that the IP address is the common IP address of the user, obtaining the current effective sessionnumber of the IP address; and managing the user login according to the current effective session number of the IP address. By adoption of the method and apparatus for managing user login security, theelectronic device, and the computer readable medium, effective security management can be performed on the session state of user login and the IP address.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
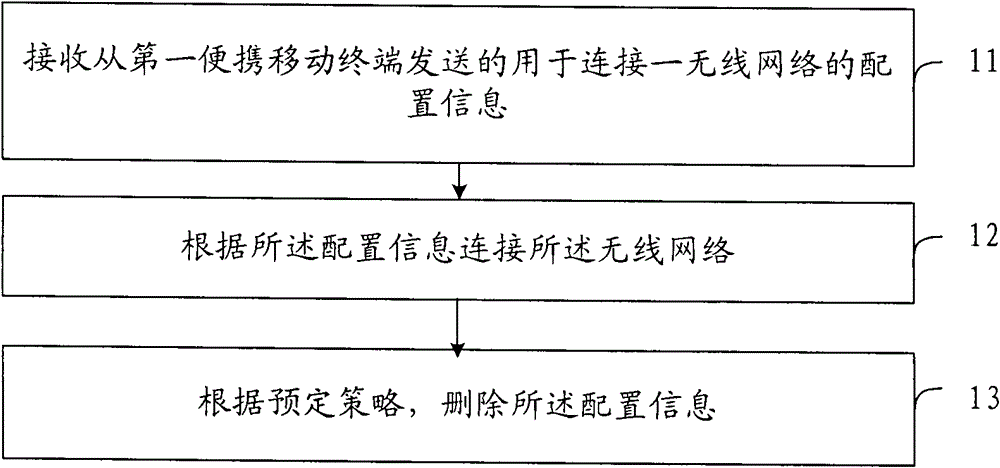
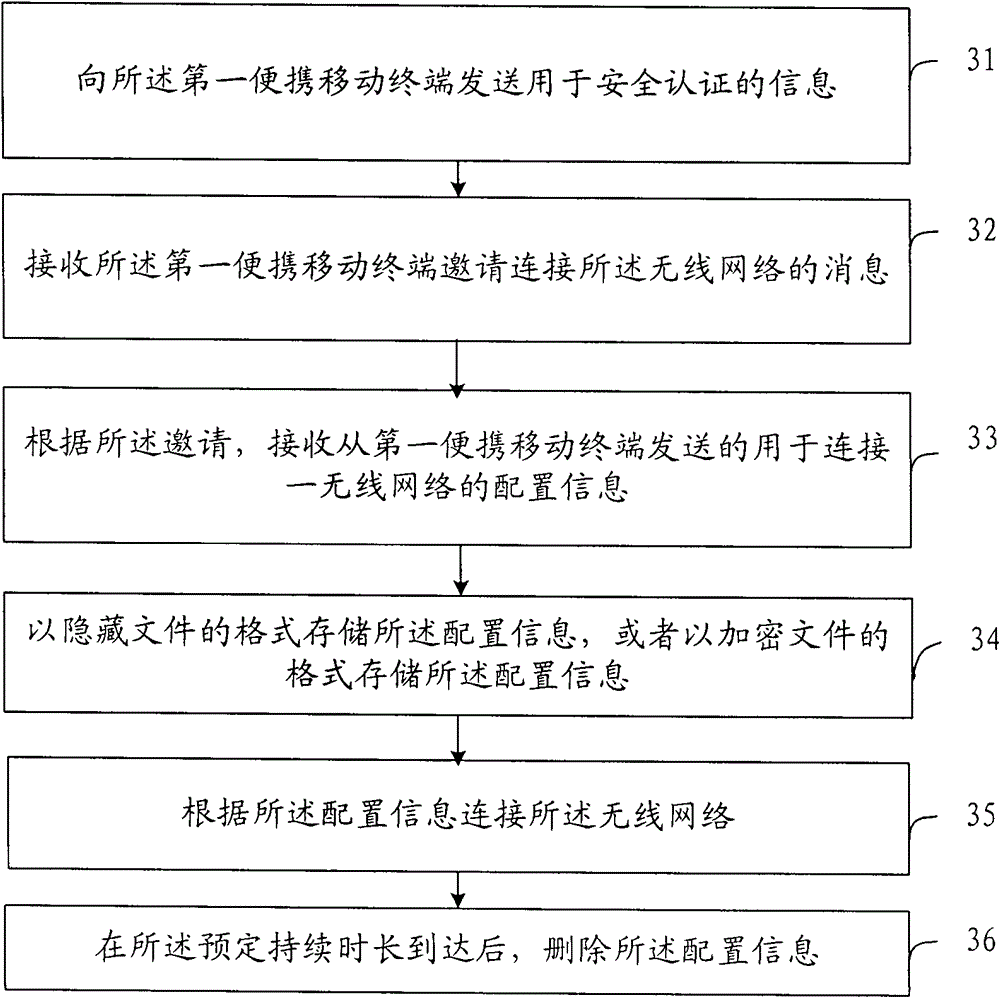
Method for accessing wireless network, portable mobile terminal and wireless network system
ActiveCN102572836BEfficient Safety ManagementReduce resource consumptionConnection managementData switching by path configurationComputer networkNetworked system
The present invention provides a method for accessing a wireless network, a portable mobile terminal and a wireless network system, and relates to the field of wireless networks. It was invented because of the technical problem of high resource consumption of a terminal. The method includes: receiving configuration information for connecting to a wireless network sent from the first portable mobile terminal; connecting to the wireless network according to the configuration information; and deleting the configuration information according to a predetermined strategy. The portable mobile terminal includes: a receiving unit, configured to receive configuration information for connecting to a wireless network sent from the first portable mobile terminal; a connecting unit, configured to connect to the wireless network according to the configuration information; a deleting unit, configured according to a predetermined strategy, Delete the configuration information. The present invention is applied to an application scenario where a mobile terminal as a temporary visitor accesses a wireless network.
Owner:LENOVO (BEIJING) LTD
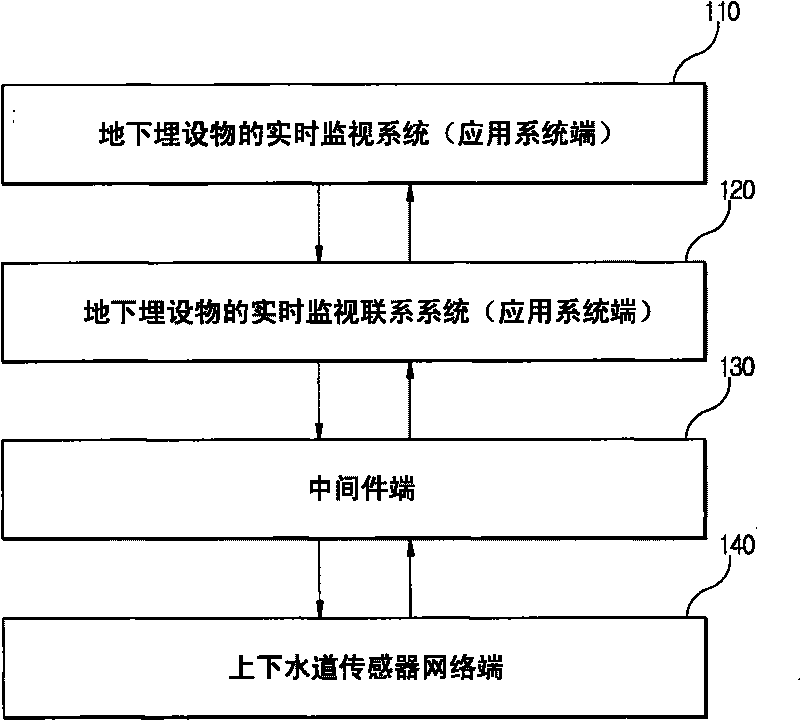
Real time monitoring system adopting GIS for underground installation of ubiquitous base plate
InactiveCN101738959AEffective safety managementAvoid dangerProgramme controlComputer controlGraphical user interfaceInformation system
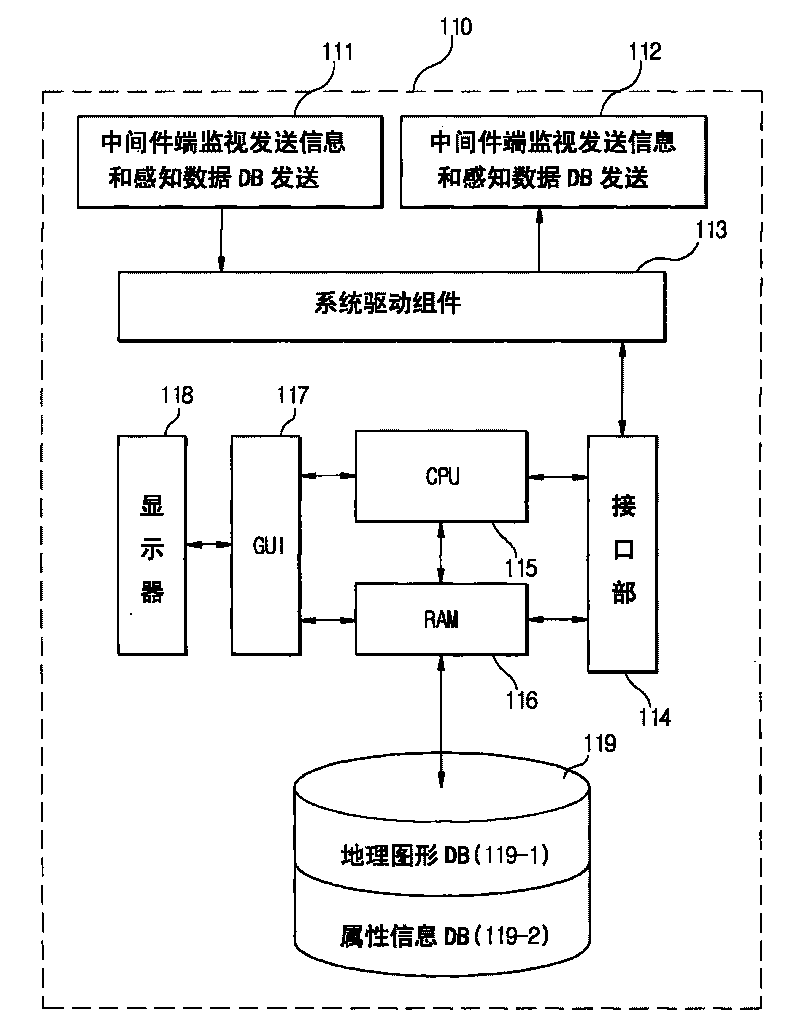
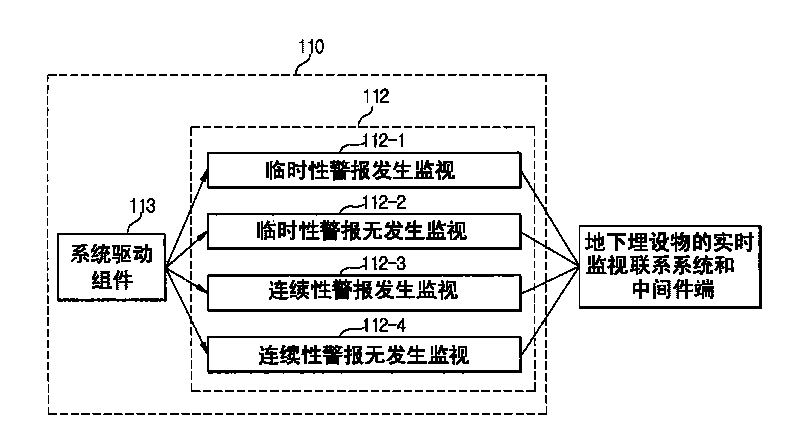
The invention aims at providing a real time monitoring system adopting a GIS (Graphical Information System) for the underground installation of a ubiquitous base plate. The underground installation can be effectively managed by rapidly acquiring the decision information of tubes of water supply pipelines and sewer by an observation and analysis technology for checking information to be input data. The system comprises a sensor, a sending part for sending information API and sensing data DB, a receiving part with a middle ware end receiving the information API and the sensing data DB, a system driving component, geographic graph DB including the graphical information of the underground installation of the water supply pipelines and the sewer and attribute information DB generated by the geographic graph DB, a GUI (Graphical User Interface) which is used for outputting images according to the result of the sensed value obtained through monitoring a setting process by the geographic graph DB and the attribute Information DB, and a central controlling and processing device which is electrically connected with and generally controls the DB, the system driving component and GUI.
Owner:仁荷大学教产学协力团
Portable power management device based on digital signal processing
ActiveCN104753090BRealize managementGuaranteed Security ManagementBatteries circuit arrangementsElectric powerDigital signal processingBattery charge
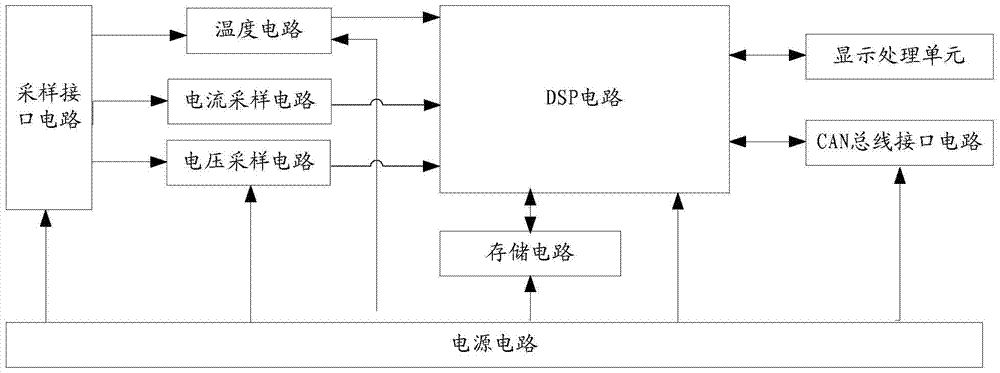
An embodiment of the present invention provides a portable power management device based on digital signal processing. The device mainly includes: a digital signal processing unit, a voltage sampling unit, a sampling interface unit and a display processing unit. The voltage sampling unit performs AD sampling processing on the voltage signal of the portable power supply, obtains the voltage value of the portable power supply, and transmits the voltage value of the portable power supply to Digital signal processing unit; the digital signal processing unit compares the voltage value of the portable power supply transmitted by the voltage sampling unit with the preset voltage threshold range, determines the voltage state information of the portable power supply according to the comparison result, and converts the voltage state information of the portable power supply to And the voltage value is transmitted to the display processing unit. The embodiments of the present invention control the charge and discharge of the battery as a whole through the DSP control chip and related voltage, current, and temperature sampling current, so as to ensure the safe use of portable power sources such as battery packs.
Owner:THE STATE RADIO MONITORING CENT TESTING CENT +1
A method for monitoring the safety of civil gas
ActiveCN106527327BReal-time acquisitionUpload in real timeProgramme controlComputer controlGas meterSecure state
The invention provides a civil gas safety monitoring method, and relates to a method for judging the pipeline safety state through gas meter reading data. According to the method, different thresholds are set according to the flow data calibrated in advance within the unit time before installation of the system or in preliminary installation or according to the sum of the upper limit of the nominal values of gas consumption of all the gas utilization equipment behind the gas meter within the unit time and according to different situations; concretely, the gas meter acquires the reading data in real time and transmits the reading data to a processor, and the processor judges whether the pipeline behind the gas meter has large amount of leakage or small amount of leakages through the change law of the historical data and the preset thresholds and alarms if the judgment result is yes. The safety of the civil gas system can be guaranteed so that the safety decision and the user service can be provided for the gas company and the method has wide adaptability and flexible expansibility.
Owner:TSINGHUA UNIV +1
United interface based memory database remote concurrent access and interface management method
InactiveCN101119363BEfficient remote accessLoad balancingTransmissionSpecific program execution arrangementsIn-memory databaseMessage type
The present invention relates to a method based on an in-memory database long distance concurrent access and interface management which adopt the uniform port, which is characterized in that adopting the SOCKET communication means sets a set of complete message type interface, namely, MEMDB*NET protocol, the customer rightly organizes the message used for accessing the stored data according the protocol specifications, thereby having a remote access. Including the steps as follows: the message type network application layer protocol MEMDB*NET based on the TCP / IP organizes the message according to the protocol, and has an indirect communication with the in-memory database through MEMDB*NET SERVICE process, and accesses and manages the in-memory database; the MEMDB*ADMIN provided on the basis manages the in-memory database in the style of WEB interface. The useful effect of the present invention is a balanced load and an efficient management, in addition, increasing the friendliness of the interface, improving the satisfaction of the customer and advancing the stability.
Owner:ASIAINFO TECH NANJING
A data transmission method, system and device in the internet of things
ActiveCN106375390BEnsure communication securityEfficient Safety ManagementTransmissionCommunications securityOriginal data
The present invention relates to a data transmission method in an internet of things. Data is transmitted between terminals in an internet of things environment; a transmit end sends original data to network data transmission devices; the network data transmission devices sequentially add a digital signature to each piece of data; and the final network data transmission device verifies all digital signatures of the received data, determines that the data is from the transmit end through a set path, and then sends the original data to a receive end. The present invention further provides a data transmission system in the internet of things and a data transmission apparatus in the internet of things. The data is singed when passing each hardware device in transmission, a later receiving device can verify the signature, so that multiple nodes on one communication chain are managed safely and effectively, the whole communication chain is ensured to communicate safely, and a non-credit person is prevented from intruding and controlling the device.
Owner:北京爱接力科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com