Gate control all-in-one machine adopting multi-verification to obtain complete open password
A technology for unlocking passwords and multiple verifications, applied in instruments, time registers, and individual input/output registers, etc., to solve the problems of access control password theft, forgetting, and misunderstanding, and achieving simple and extensive implementation. applied effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
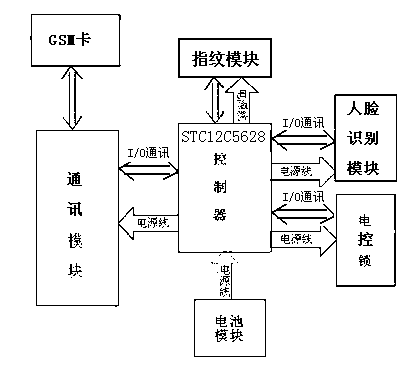
[0012] As shown in the figure, an access control all-in-one machine that adopts multiple verifications to obtain a complete unlock password includes an electronically controlled lock, a communication module, a controller, a battery module, a verification module, and a password terminal. The electronically controlled lock passes through the controller I / O The port is connected to its data, the communication module is connected to its data through the Uart port of the controller, the verification module is connected to its data through the controller I / O port, and the battery module is connected to the controller, communication module, verification module and electric lock wire and provide them with electricity.
[0013] The communication module, controller, battery module and verification module are packaged in a box body, and the box body is installed on a wall 60 cm away from the electric control lock.
[0014] The verification module includes a fingerprint module and a face ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com