Method for inspecting deep packets based on suffix automaton regular engine structure
A deep packet inspection and automaton technology, applied in the field of network security, can solve the problems of DFA engine space explosion and NFA engine performance degradation, and achieve the effect of shortening response time, solving space waste, and efficient intrusion detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
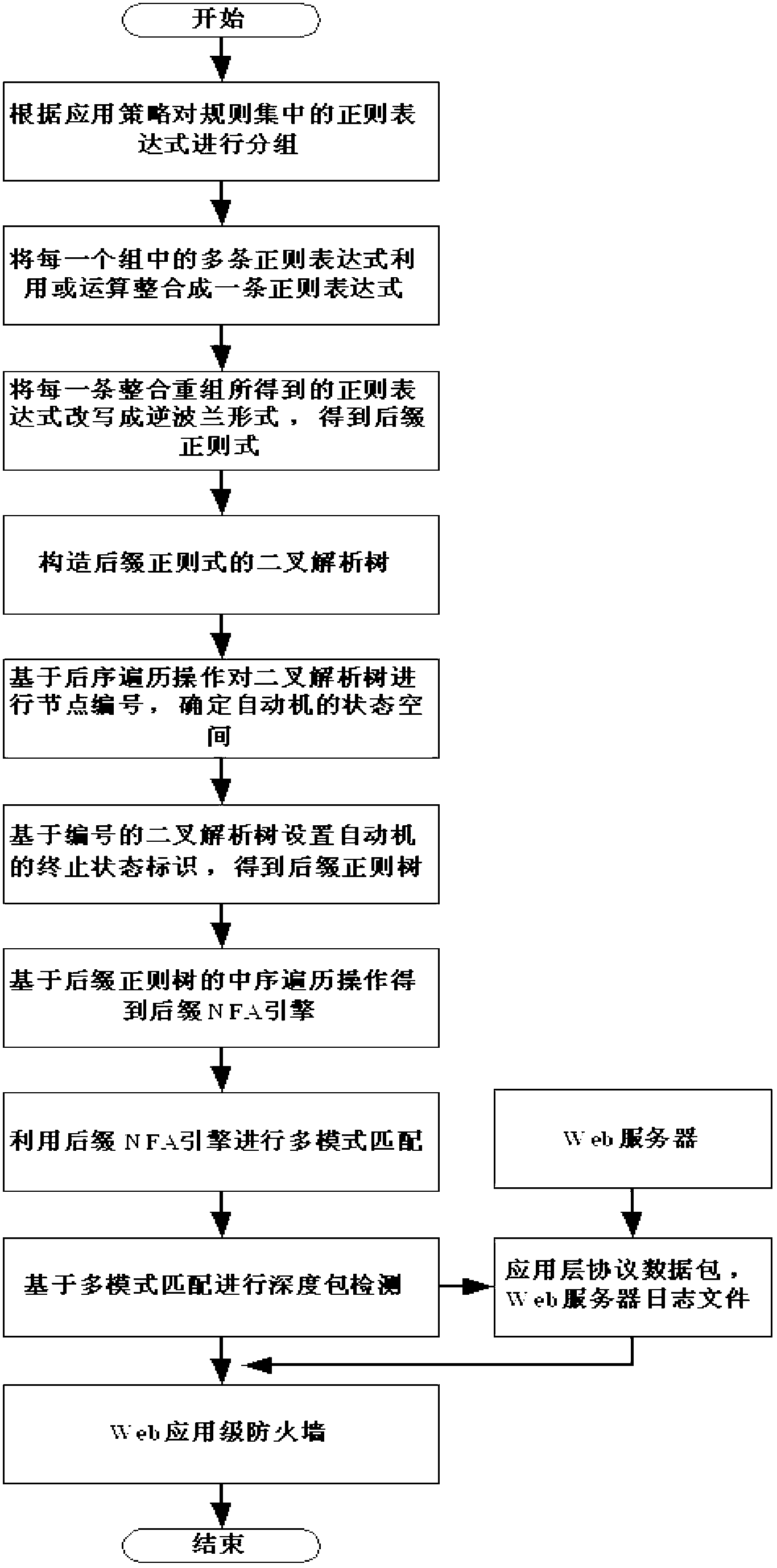
[0084] Embodiment 1: A kind of deep packet inspection method based on the regular engine construction of suffix automata, such as figure 1 shown, including the following steps:
[0085] S1, the intrusion detection system extracts attack features to construct regular expressions;
[0086] S2, constructing a suffix NFA engine and using it for multi-pattern matching;
[0087] S3, obtaining the application layer protocol data packet and the log file of the Web server from the Web server;
[0088] S4, performing deep packet inspection on the above-mentioned protocol data packets and log files and sending the inspection results to the firewall;
[0089] S5. IP source tracing is carried out, and after the attack source is traced, the IP address of the attack source is sent to the firewall for packet filtering.
[0090] The specific method of constructing the suffix NFA engine described in step S2 includes:
[0091] a. Group regular expressions;
[0092] b. Integrate multiple reg...
Embodiment 2
[0117] Embodiment 2: a kind of deep packet inspection method based on suffix automata regular engine construction, comprises the following steps:
[0118] S1, the intrusion detection system extracts attack features to construct regular expressions;
[0119] S2, constructing a suffix NFA engine and using it for multi-pattern matching;
[0120] S3, obtaining the application layer protocol data packet and the log file of the Web server from the Web server;
[0121] S4, performing deep packet inspection on the above-mentioned protocol data packets and log files, and sending the inspection results to the firewall.
[0122] The specific method of constructing the suffix NFA engine described in step S2 includes:
[0123] a. Group regular expressions;
[0124] b. Integrate multiple regular expressions in each group into one regular expression by OR operation;
[0125] c. Rewrite the integrated regular expression into a reverse Polish form to obtain a suffix regular expression;
...
experiment example
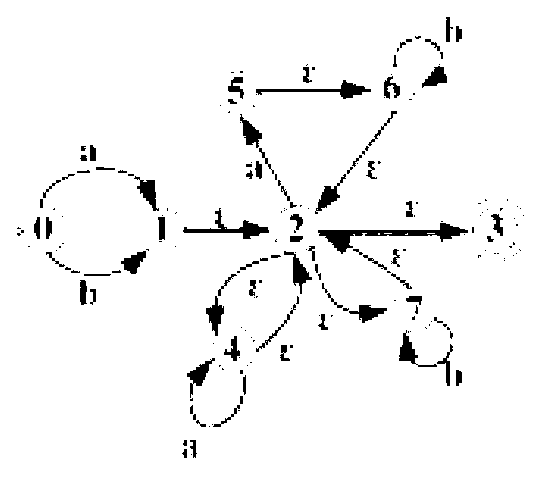
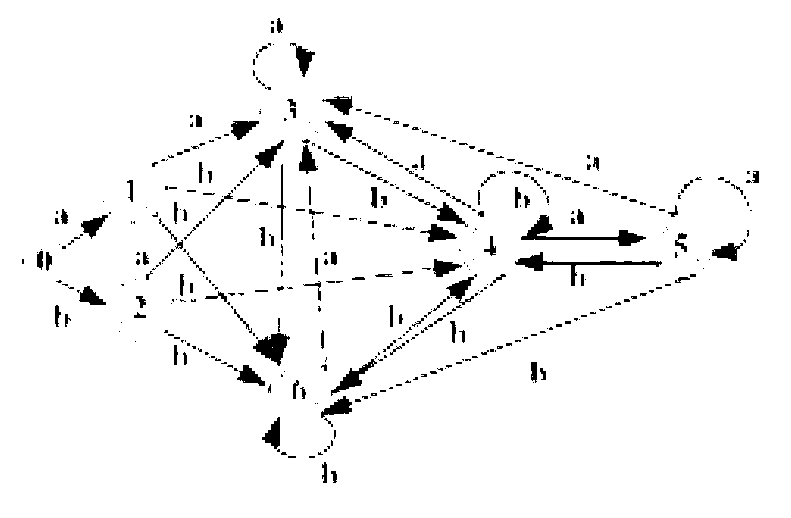
[0150] The number of regular expressions supported by the hardware regular engine is extremely limited, which is not suitable for the current network information system, especially the deep packet inspection application of the cloud computing system. In the current soft engine systems such as Snort, a single DFA matching multiple regular expressions has the problem of space explosion, and the traditional NFA engine has the problem of sharp decline in parallel matching performance. Moreover, there are currently only four theories or methods for constructing regularization engines, and practical systems are basically implemented based on Thompson automata. The NFA engine obtained by the existing automaton construction theory is not the smallest, and a classic example is used to compare and illustrate as follows:
[0151] Adopt the present invention and various existing methods of constructing NFA to realize the NFA construction of the same regular expression r, wherein,
[0152...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com