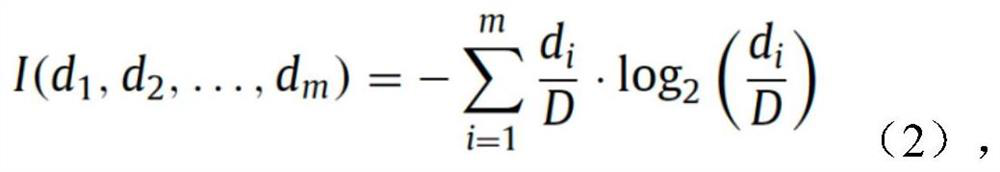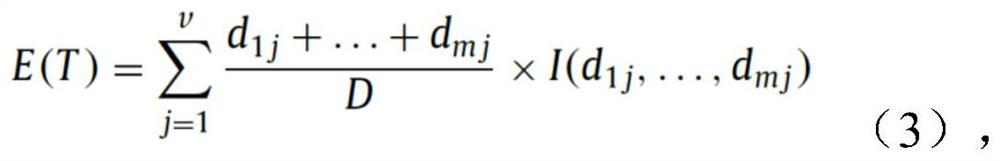A network-oriented intrusion data detection method
A data detection and data technology, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve the problems of difficult classification of data sets, low classification efficiency, etc., to eliminate irrelevant features, reduce dimensionality, and improve classification efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
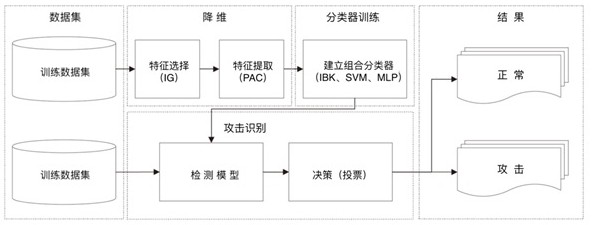
[0046] The working principle and technical solutions of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation.
[0047] Dimensionality reduction technology, as a means to improve computing performance, can be used as a preprocessing step in machine learning algorithms to eliminate irrelevant features and retain the most relevant features. In practice, there are two ways to re-determine the number of attributes in a dataset. The first approach is feature selection, which retrieves a subset of the original features without modifying data attributes. Feature selection can be divided into three categories by type: filters, wrappers, and embedding methods. Filter methods select features based on their intrinsic properties, i.e. regardless of classifier performance. In the second feature extraction method new features are created by generating new combinations of original features.
[0048] Such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com