Cloud protective system for improving personal information security in network marketing channel
A technology for information security and online sales, applied in the field of cloud protection systems, can solve problems such as personal information security, damage to the seller's reputation and buyer's privacy, and hidden dangers of personal information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
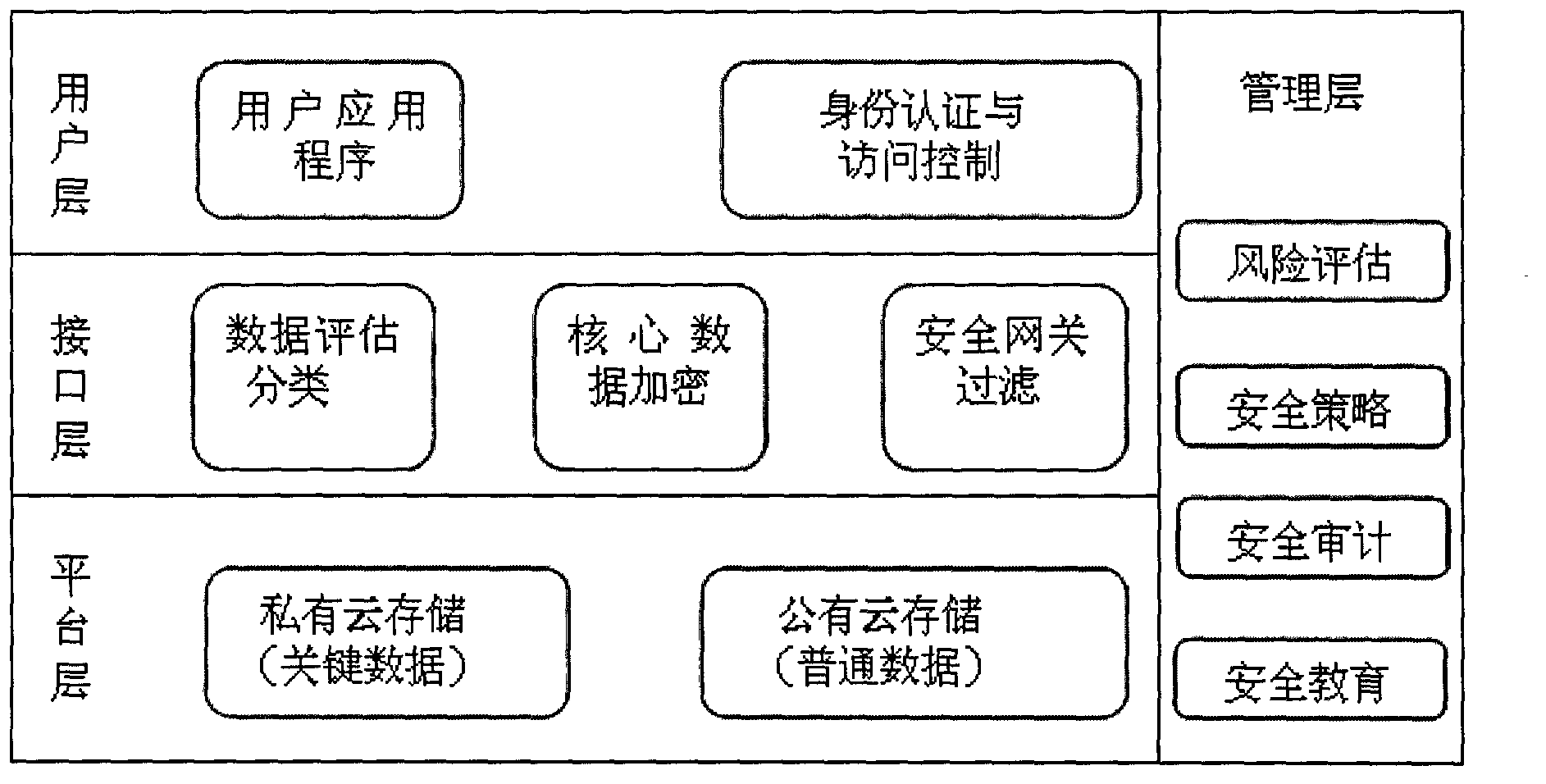
[0047] Such as figure 1 The cloud computing method for personal information security shown in the network sales channel includes a personal information security model and a cloud service provider trust evaluation system. Among them, the personal information security model includes four-layer design: user layer, interface layer, platform layer, management. The user layer is used to complete user identity authentication, the interface layer is used to classify and encrypt complex personal information, the platform layer is used to complete data storage, and the management layer ensures the overall effective work;
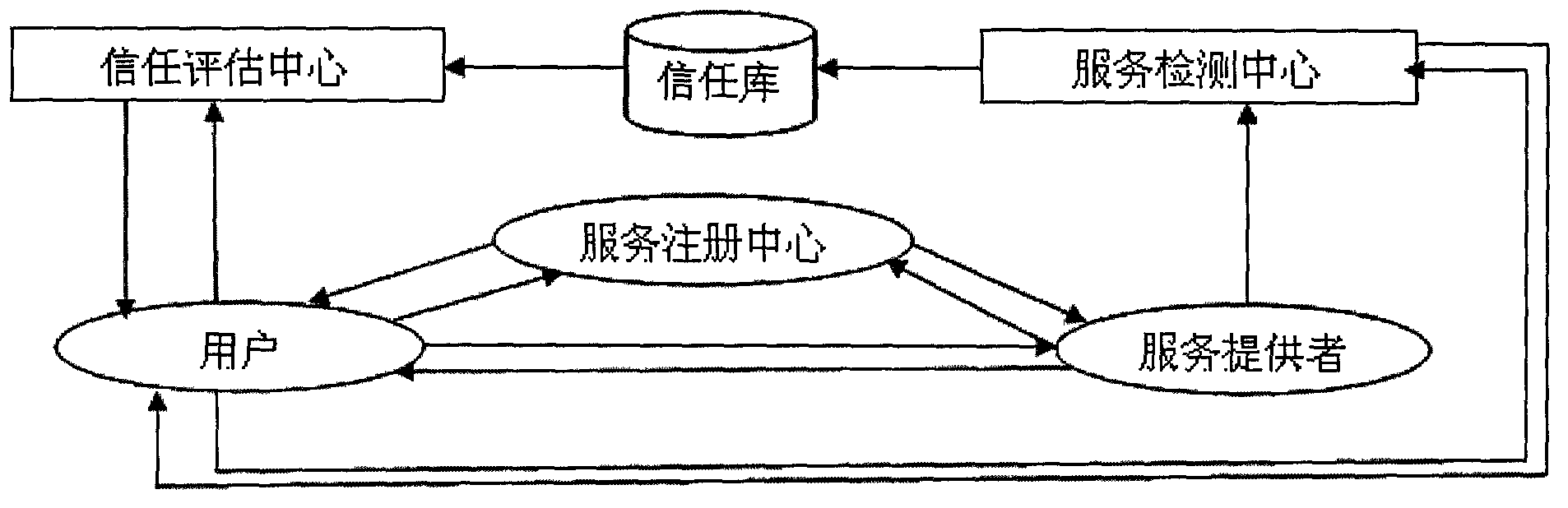
[0048] Such as figure 2 The cloud service provider trust evaluation system shown uses the membership degree theory to establish the behavioral trust evaluation of cloud service providers. The service provider returns the registration result; (3) the user sends a query request to the registration center; (4) the service registration center returns the result to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com