Fingerprint identity authentication system and authentication method
An identity authentication and fingerprint technology, which is applied in the identity authentication system and its authentication field using fingerprints, can solve the problems of strict implementation, virtual authority authentication cannot be reliably verified, security policies cannot be guaranteed, etc., so as to achieve ease of use. Strong, mature technology, widely popular effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in further detail below in conjunction with the embodiments and with reference to the accompanying drawings.
[0021] Multi-virtual systems will use a unified identity authentication ID, and unified management of man-machine management, witness management, and fingerprint multi-device management (fingerprint AD domain, fingerprint SSO single sign-on, fingerprint electronic signature, fingerprint VPN, etc.) Ensure that the account and the actual authorized user identity card are integrated and unified, thereby enhancing the security and service performance of virtual machines and physical servers.
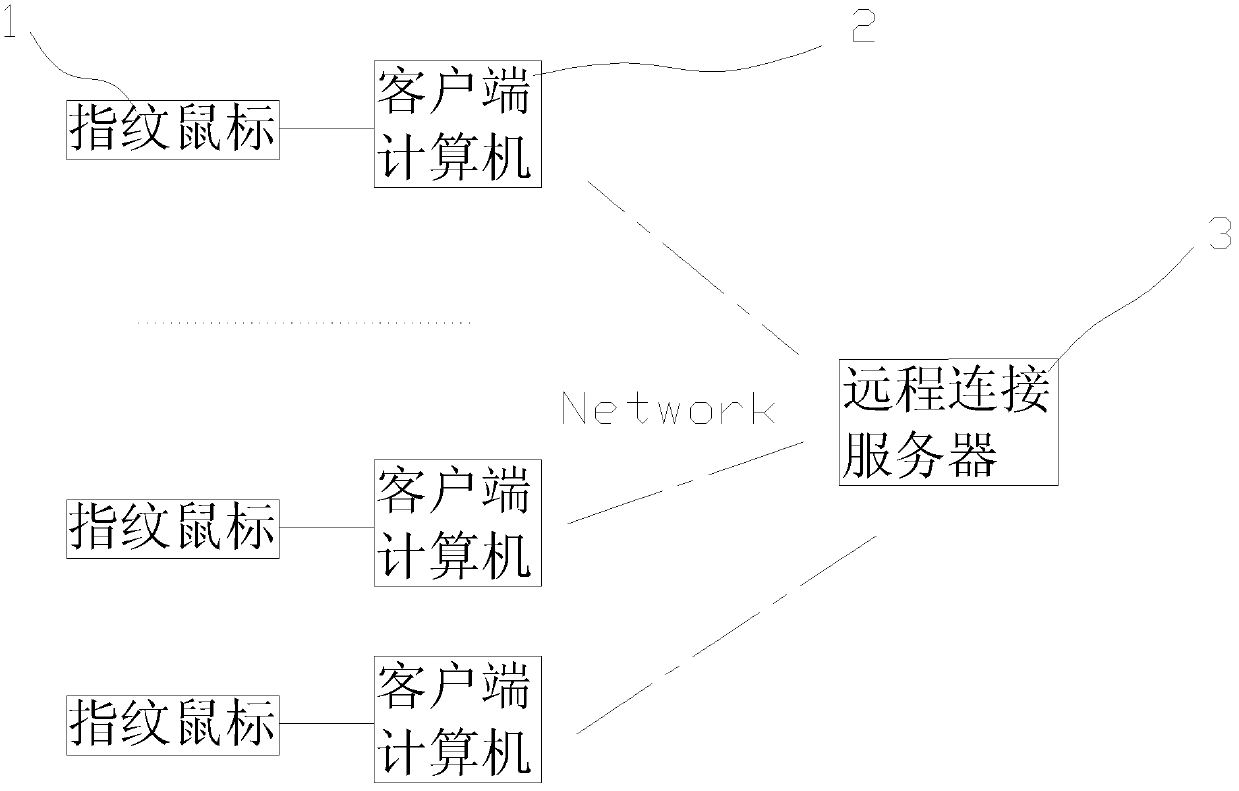
[0022] Such as figure 1 , a fingerprint membership authentication system, including the following components:
[0023] 1. A remote connection server with fingerprint authentication software installed 3
[0024] The installed fingerprint identity authentication software is a SERVICE program responsible for providing fingerprint identit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com