Configuration, generation method and device of cloud environment audit log and/or security event
A security event and cloud environment technology, applied to the configuration and generation of audit logs and/or security events in the cloud environment, can solve problems such as the inability to effectively and timely discover and correct security problems, and the inability to continuously monitor the security of information assets, to achieve The effect of enhancing trust, improving confidence and trust, and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] This embodiment describes how to configure audit logs and / or security events in a multi-tenant cloud environment, specifically:
[0068] The cloud tenant configures the audit logs and / or security events of the cloud tenant that the cloud computing service provider (CSP) needs to provide in the Service Level Agreement (Service Level Agreement, SLA for short).
[0069] In addition to cloud tenants, other entities that need to be configured can also configure related requirements in SlA.
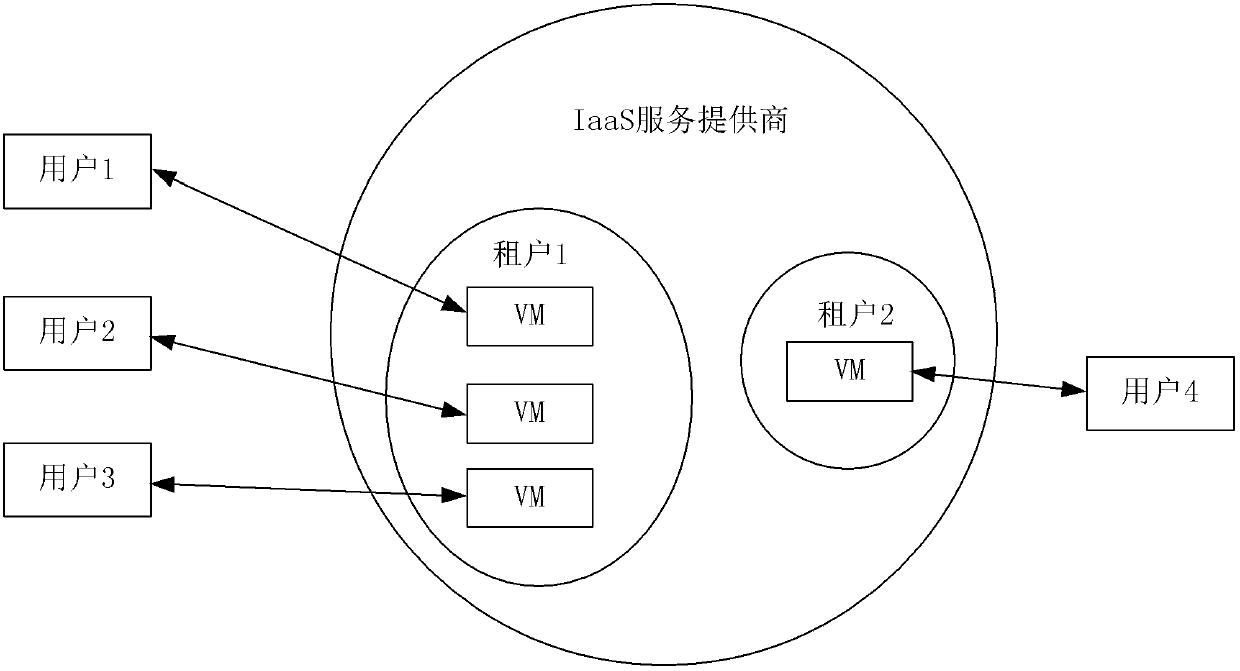
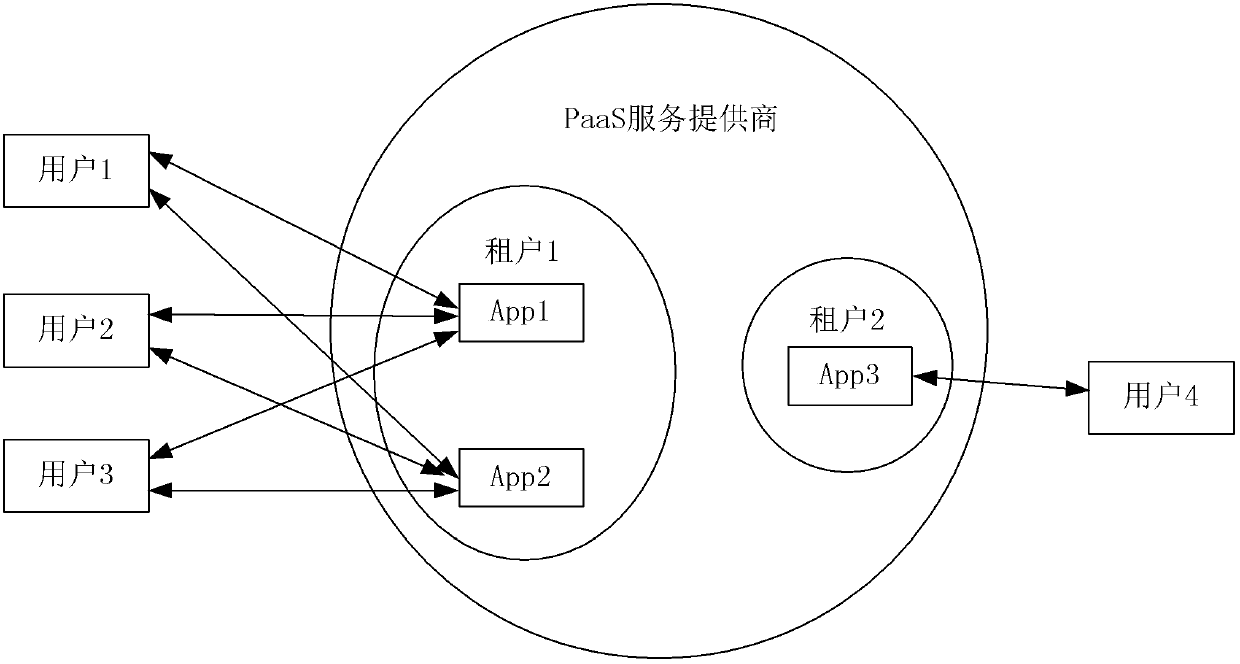
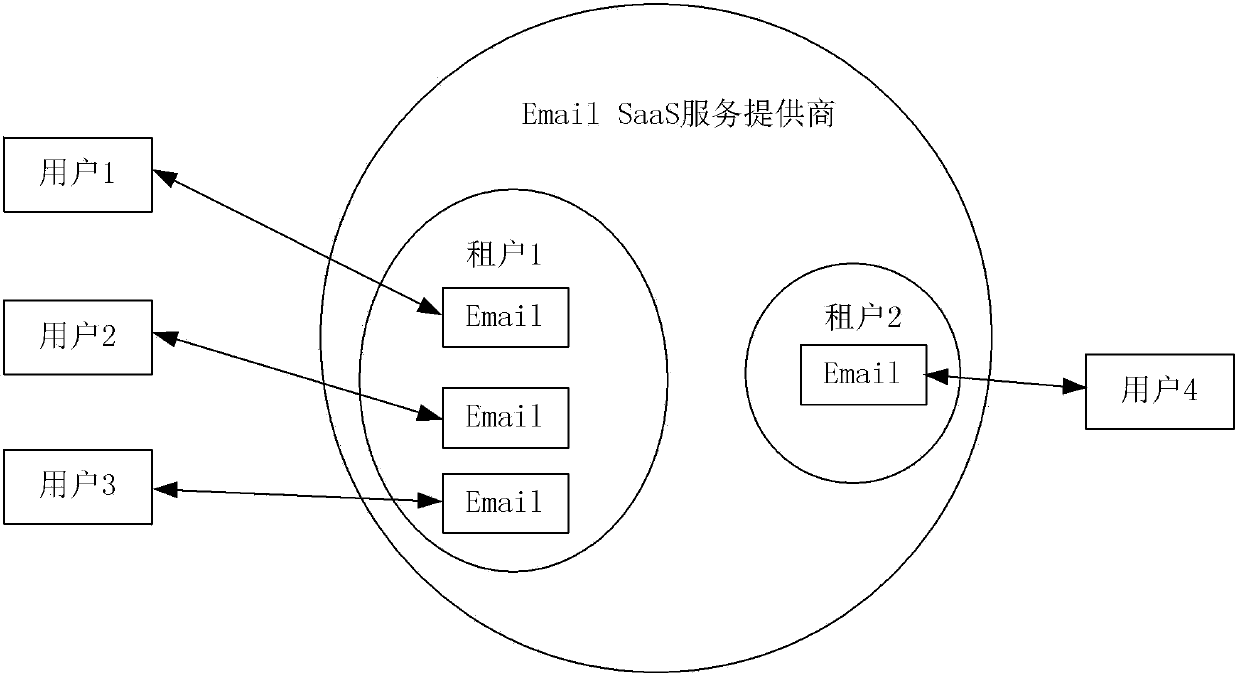
[0070] Tenants' information assets in the cloud are of different types. Figure 4 Some types of information assets are listed in , including: user name, group name, virtual machine, file, folder, directory, IP address, application, database, data table, data record, data object, email address, inbox, sent folders, contacts, audit logs, security events.
[0071] The aforementioned audit logs include one or more of the following: operating system audit logs, database audit logs, applicat...
Embodiment 2
[0081] This embodiment illustrates a method for generating audit logs and / or security events in a multi-tenant cloud environment.
[0082] Take audit logs and security events as examples. The complete life cycle of audit logs and security events includes three stages: audit log generation and security event generation, audit log and security event storage and use (that is, acquisition), and audit log and security event destruction. In a multi-tenant cloud environment, tenants expect the CSP to generate and process tenant audit logs and security events according to their individual requirements. Figure 8It shows that cloud tenants can specify the requirements of each stage of the audit log and security event life cycle by configuring the SLA. The requirements of tenants include several aspects: the scope of audit logs and security events, that is, those audit logs and security events that tenants want to obtain; the content of audit logs and security events, that is, the info...
Embodiment 3
[0097] This embodiment introduces the device that realizes the method of embodiment 2, such as Figure 10 As shown, including the SLA module and the generation module, where:
[0098] The SLA module: configure the audit logs and / or security events of the cloud tenants that the CSP needs to provide in the SLA;
[0099] The generation module: the CSP generates audit logs and / or security events of cloud tenants according to the configuration in the SLA.
[0100] The source of the audit log, the source of the security event, and the scope and content involved in the audit log or security event refer to the description in Embodiment 1, which will not be repeated in this example.
[0101] If the SLA is also configured with: privacy protection information; then the generation module is also used to generate audit logs or security events of other cloud tenants when the cloud tenants need to implement privacy protection information assets in the cloud, Omit or anonymize the informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com