Data secrete sharing system and method based on core network
A core network and secret sharing technology, applied in the field of data secret sharing system based on core network, can solve the problem that the fingerprint feature of the entry node is easy to be discovered by the adversary, and it is easy to cause the adversary's suspicion, so as to improve the efficiency of covert communication, increase the difficulty, The effect of improving concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
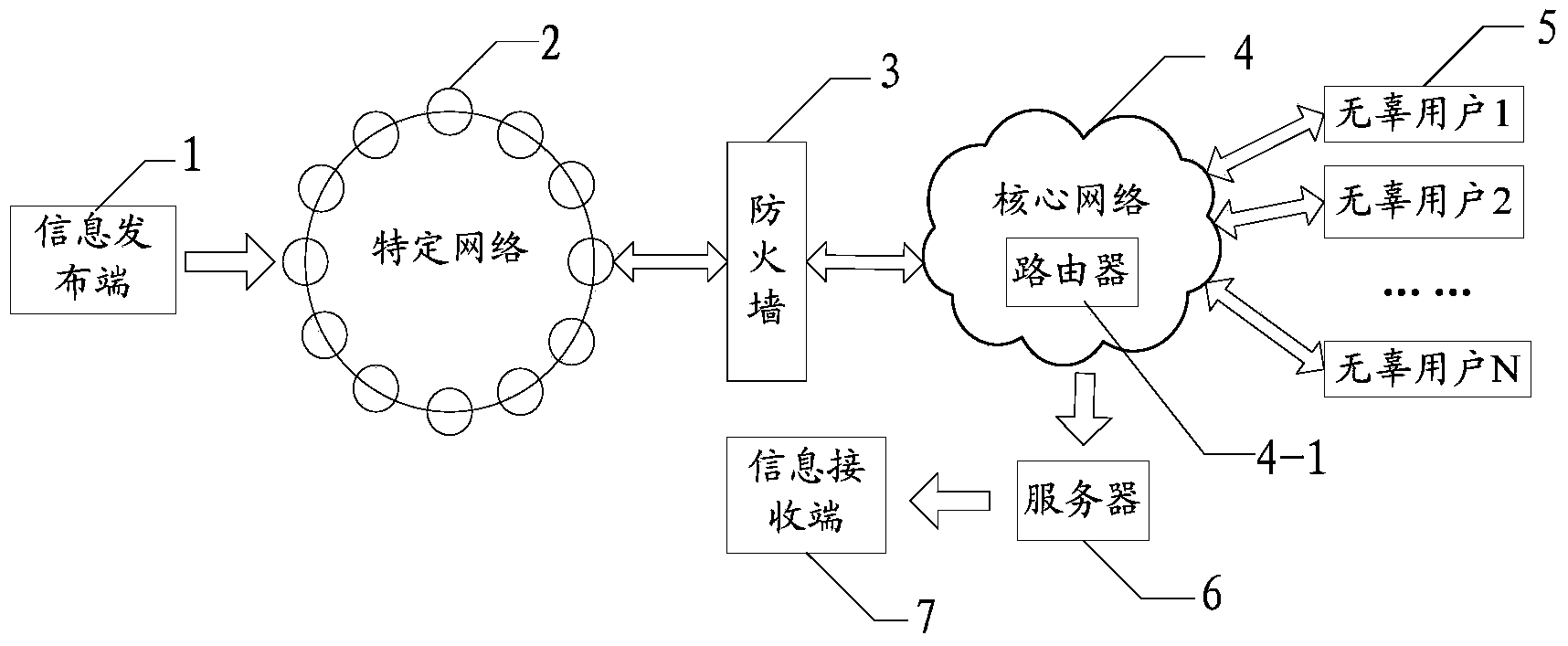
[0053] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0054] Traditional covert communication methods are all end-to-end communication methods. Generally, covert channels are placed in other bunker channels. Unlike traditional covert communication, which requires both parties to participate in a covert handshake, the core idea of the present invention is to use end-to-end covert channels , moving to the end-to-intermediate (information publishing end and forwarding router) communication method, that is, in the covert handshake process, with the help of the forwarding router in the core network, only the information publishing end and the forwarding router need to participate, and the information receiving end does not need to participate. While this method improves th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com