Asymmetric image encryption and decryption method based on quantum cell neural network system
A neural network and asymmetric technology, applied in the field of information security, can solve problems such as key interception and cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
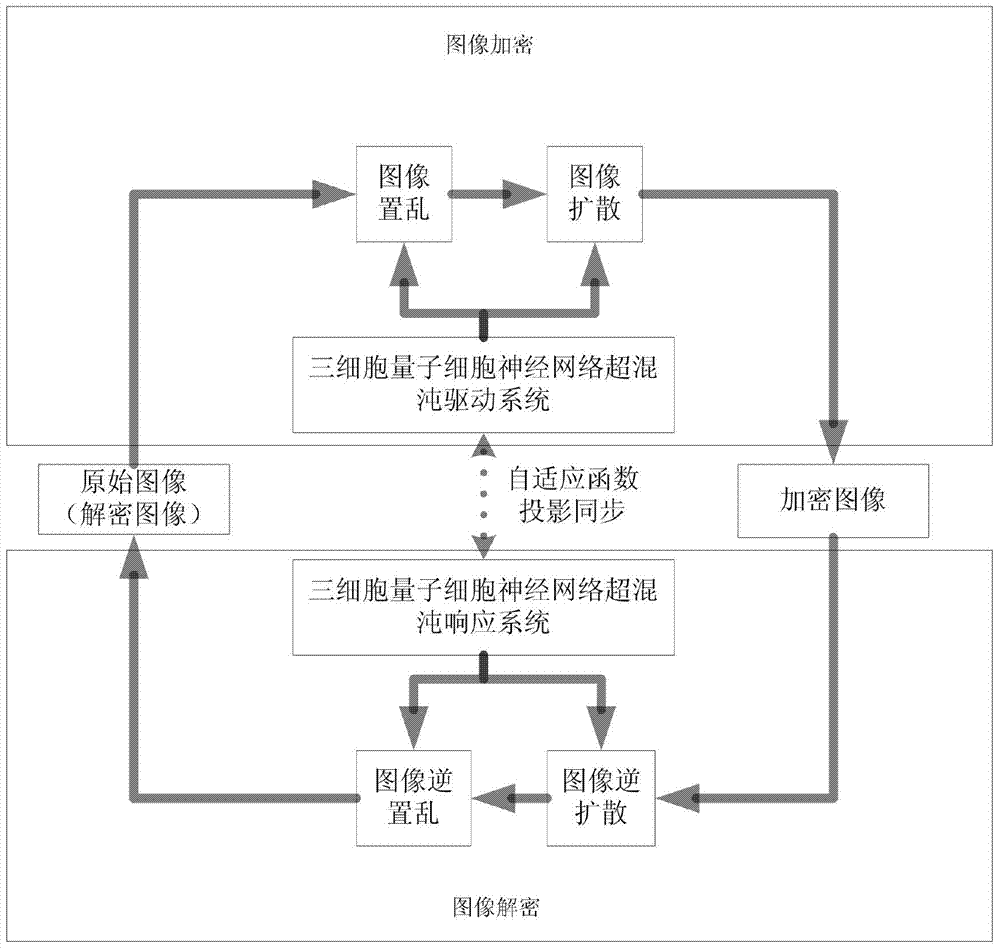
[0048] Specific implementation mode 1. Combination Figure 1 to Figure 3 Description of this embodiment, based on the asymmetric encryption and decryption method of the quantum cellular neural network hyperchaotic system, the encryption process of this method is realized by the following steps:
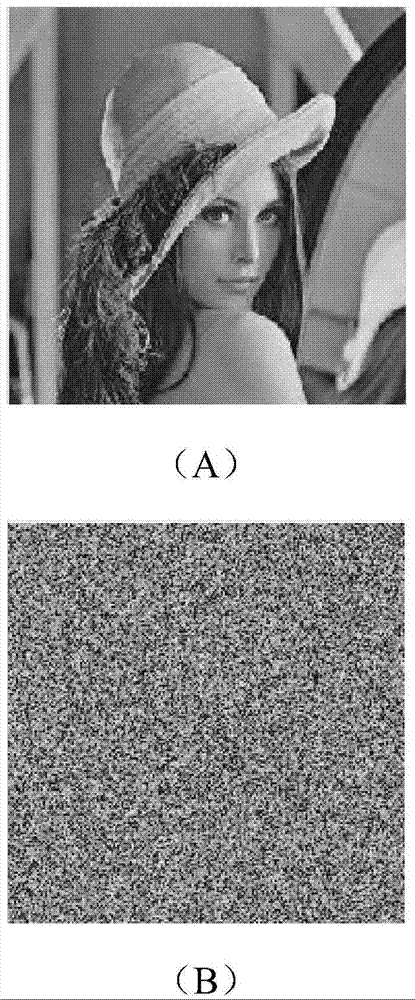
[0049] A1. Select the 256×256 “Lena” image, image 3 A is used as the original plaintext image PI.
[0050] B1, with initial conditions
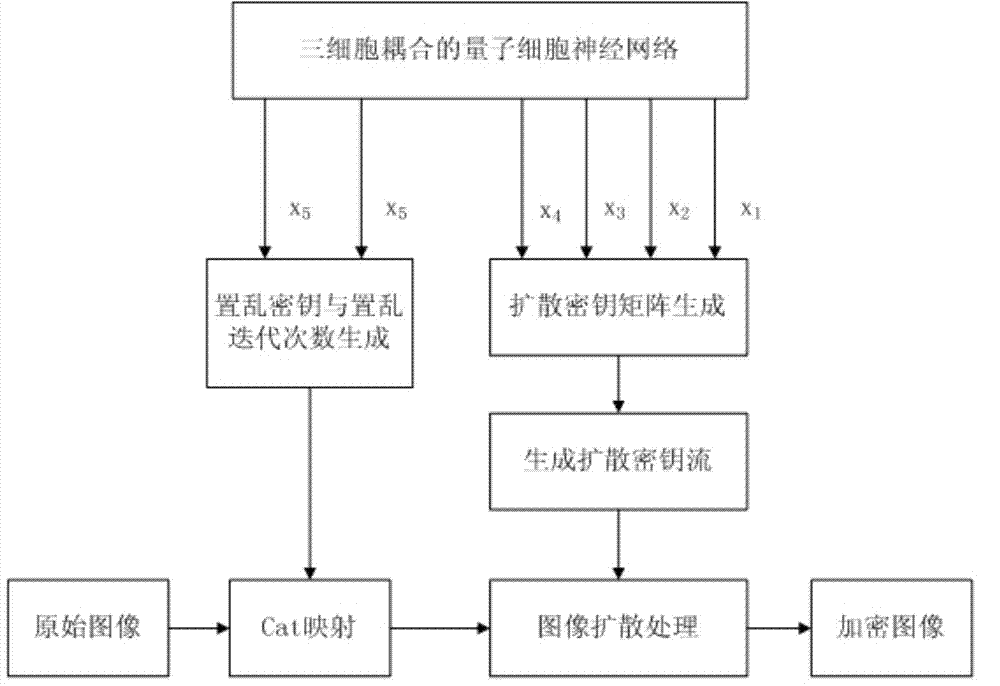
[0051] x 1 (0)=0.1901,x 2 (0)=-184.3,x 3 (0)=0.123,x 4 (0)=-147.32,x 5 (0)=0.113,x 6 (0)=-197.85 and control parameter ω 01 =0.28,ω 02 =0.4,ω 03 =0.28,ω 04 =0.35,ω 05 =0.28,ω 06 =0.25 iterative three-cell quantum cellular neural network drive system, (initial conditions and control parameters can be arbitrarily selected by the encryptor). Get the image scrambling control parameters, the number of iterations and the image diffusion key matrix.
[0052] C1. Use the scrambling control parameters and iteration times obtained in B1 to scra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com