Method for performing AAA (Authentication, Authorization and Accounting) authentication during failure of database
A technology of faults and databases, applied in the field of communication, can solve problems such as inability to use, affect, and reduce user experience, and achieve the effects of easy popularization, simple operation steps, and improved user experience quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
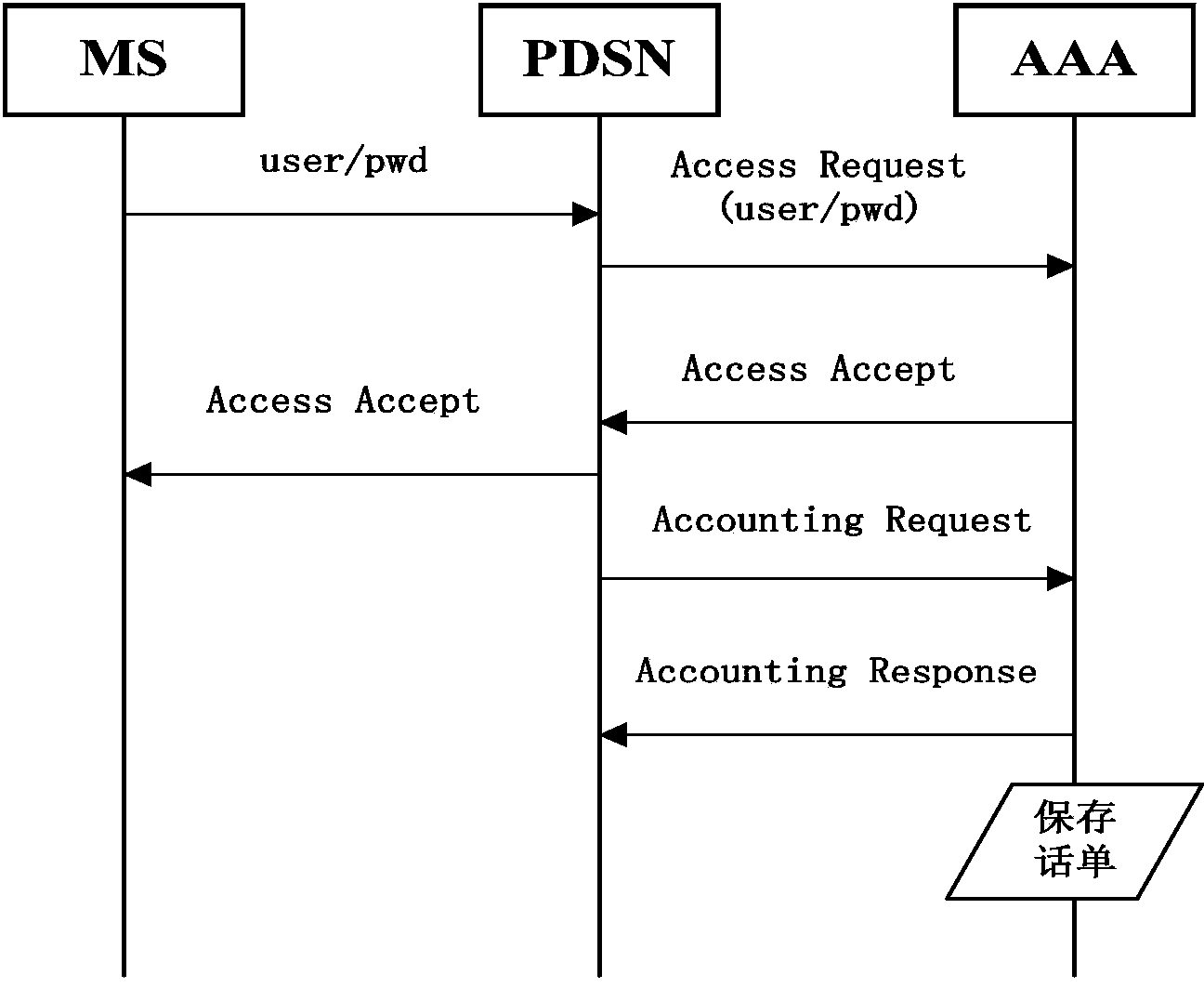
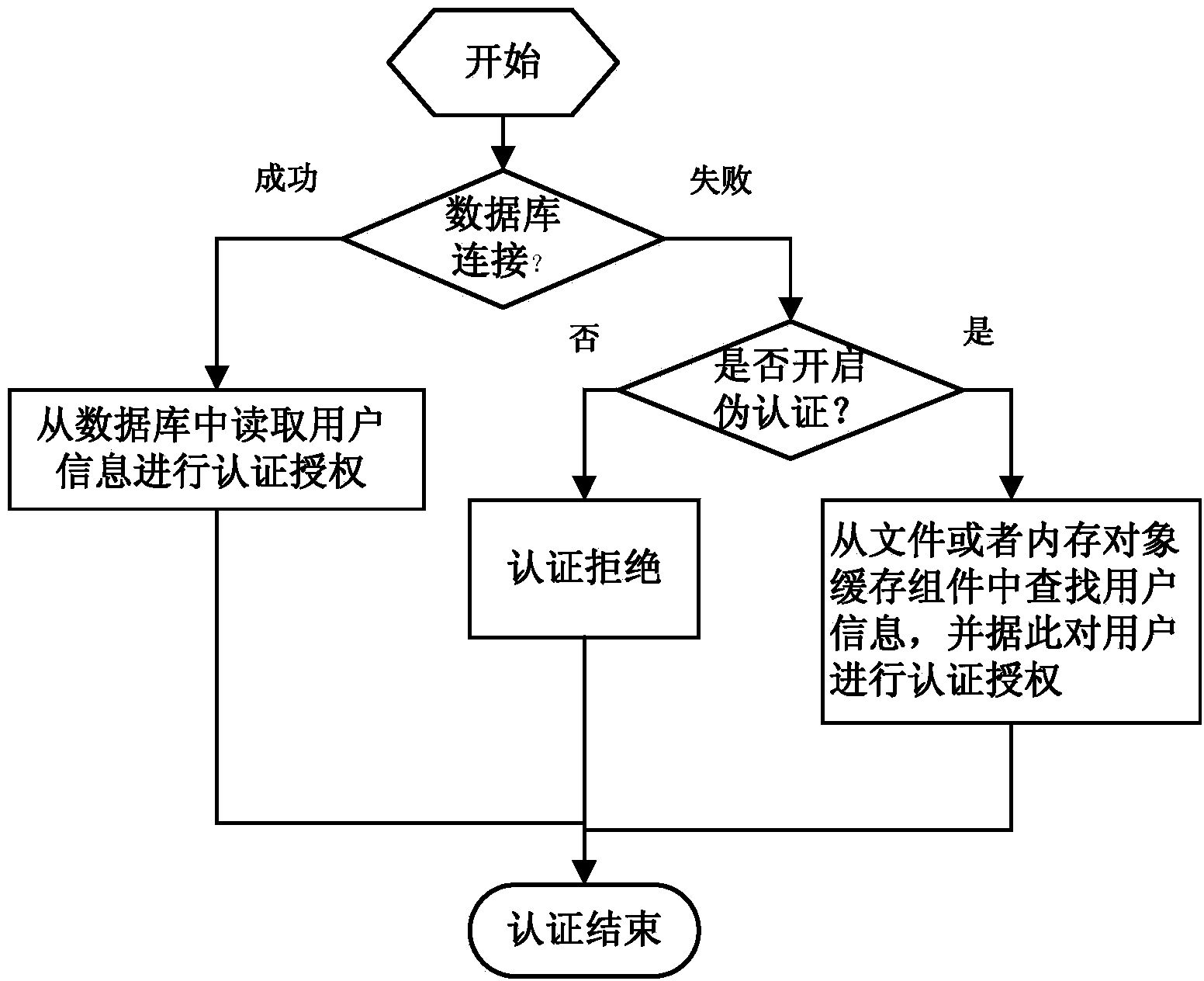
[0021] The method for performing AAA authentication when the database fails in the present invention is a pseudo-authentication method, that is, reading public NAI information and VPN information from files, and then reading IMSI-related information and binding information from the memory object cache component, and the AAA server User authentication and authorization are performed based on this information. Because when the database is working normally, the AAA server has already written the information of the public network access identifier NAI and the virtual private network VPN into the extensible markup language xml file, and also regularly reads the user's International Mobile Subscriber Identity (IMSI) information and user binding information from the datab...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap