Cloud control the access control management system and the authentication method
A management system and cloud-based control technology, applied to instruments, time registers, individual input/output registers, etc., can solve the problem of high construction cost, poor convenience, and lack of humanization of access control management systems. problems, to achieve the effect of reducing installation costs, improving aesthetics and saving time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] In the following, the technical means adopted by the present invention to achieve the intended purpose of the invention will be further described in conjunction with the accompanying drawings and preferred embodiments of the present invention.
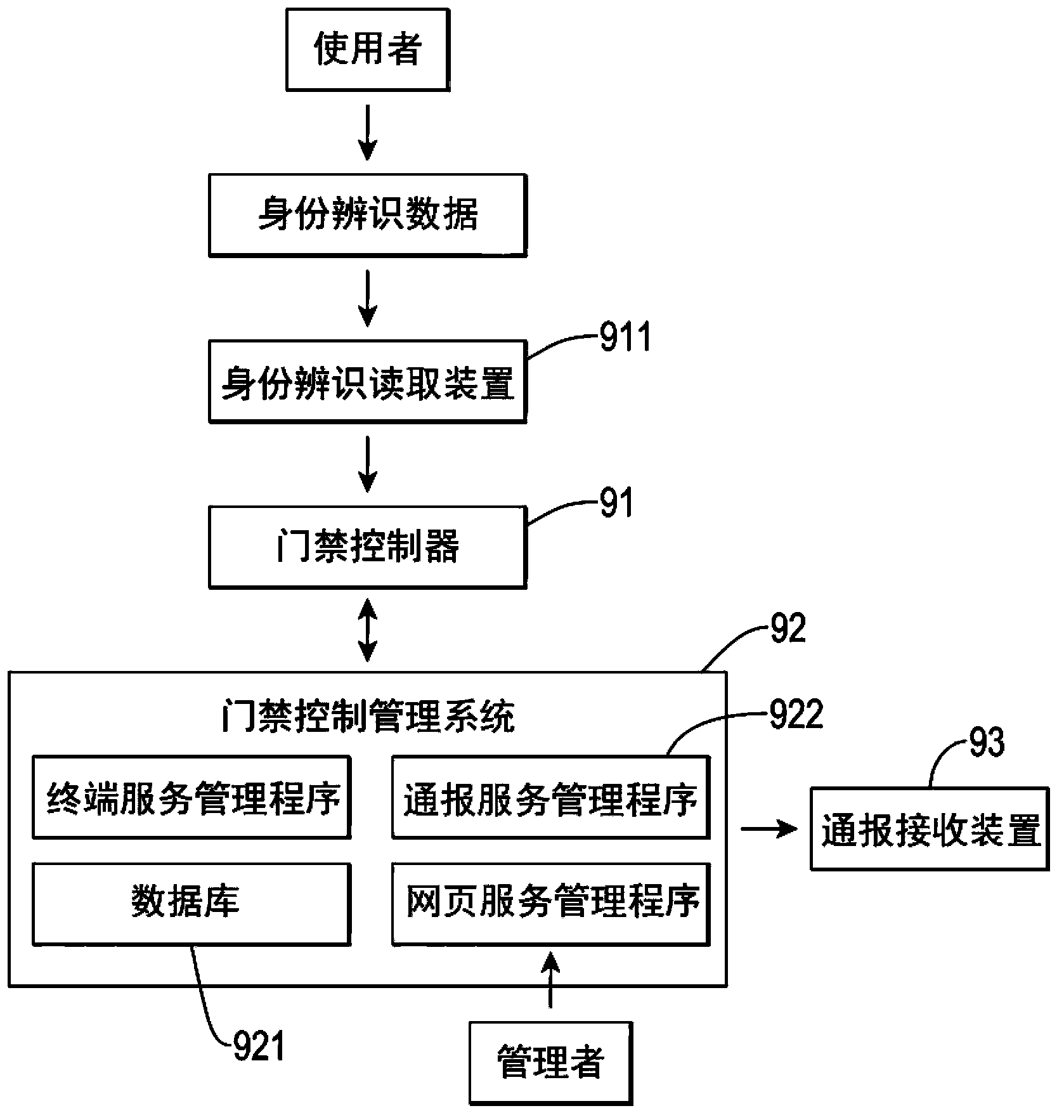
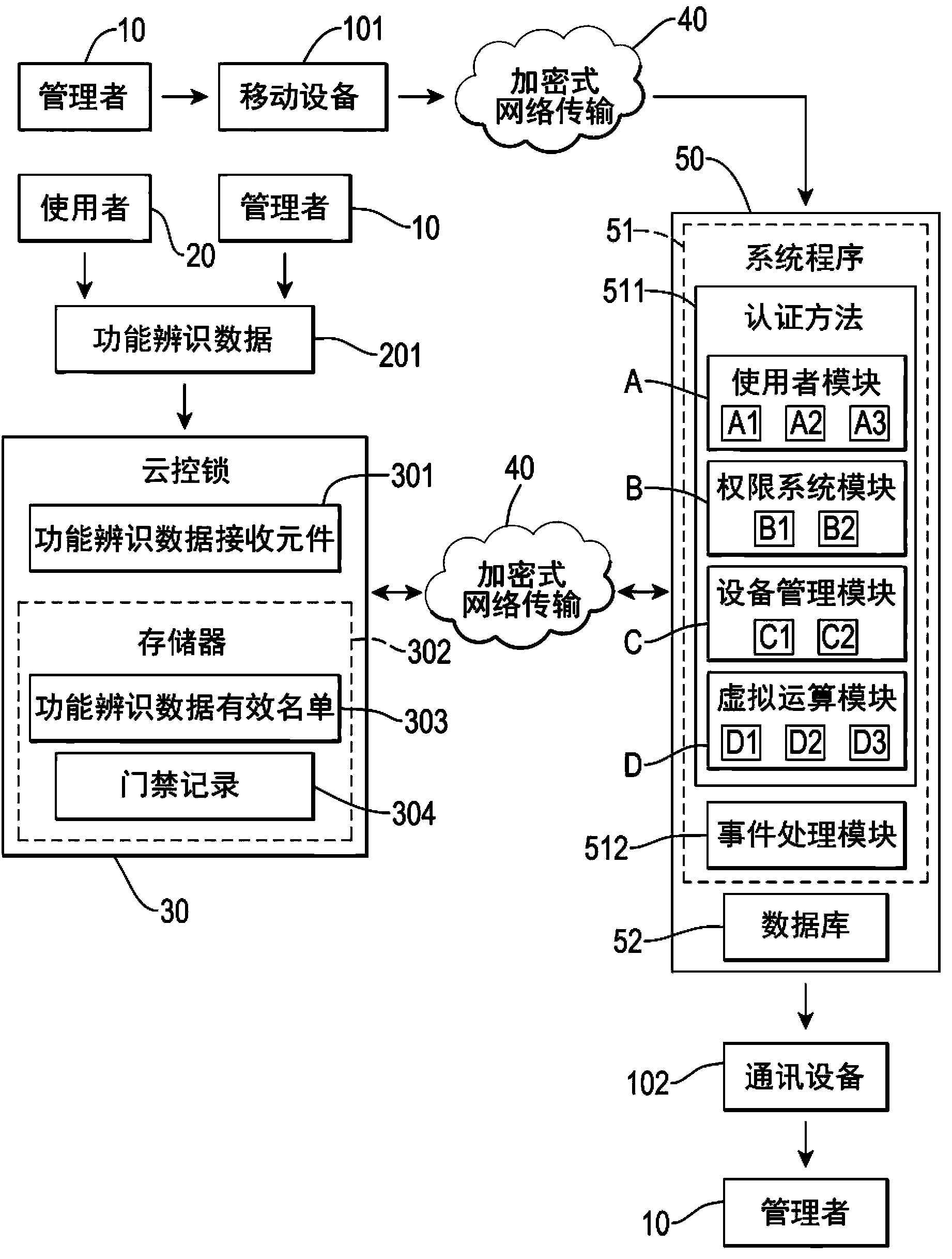
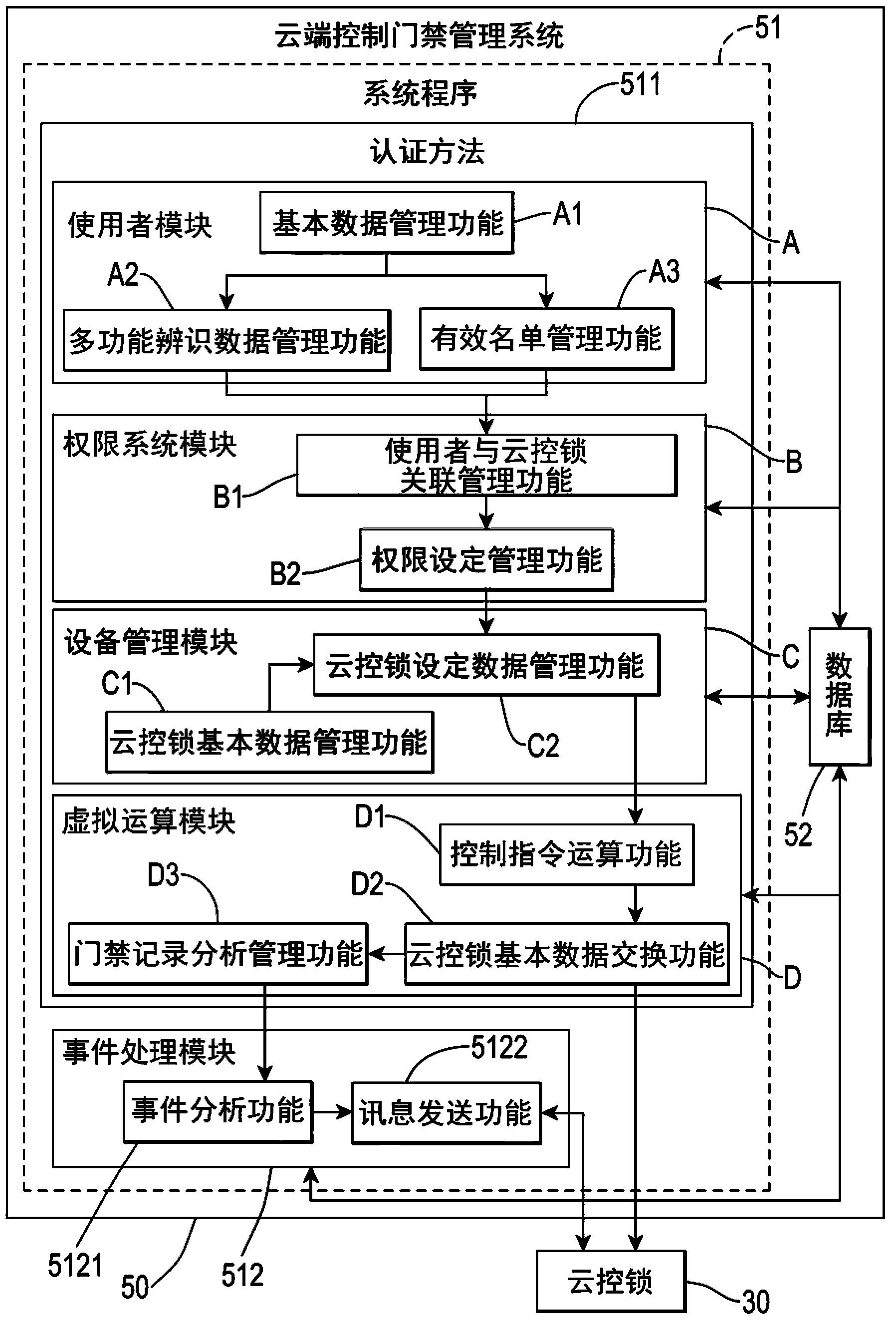
[0061] Please refer to figure 2 , is a circuit block diagram of the present invention, a function identification data 201 is input to a cloud-controlled lock 30 by a manager 10 or a user 20, and the manager 10 is transmitted by a mobile device 101 through an encrypted network 40 and then Control a cloud-controlled access control management system 50, the cloud-controlled access control management system 50 returns a message to the manager 10 through a communication device 102, and the cloud-controlled lock 30 and the cloud-controlled access control management system 50 also transmit 40 to each other through an encrypted network To transmit data, the cloud-controlled lock 30 is an electronic lock controlled by the cloud, especia...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com