Two-dimensional code cutting and splicing authentication method and system
A technology of two-dimensional code and two-dimensional code library, applied in the field of two-dimensional code cutting and splicing authentication method system, can solve the problem of single two-dimensional code being applied to a single scene, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
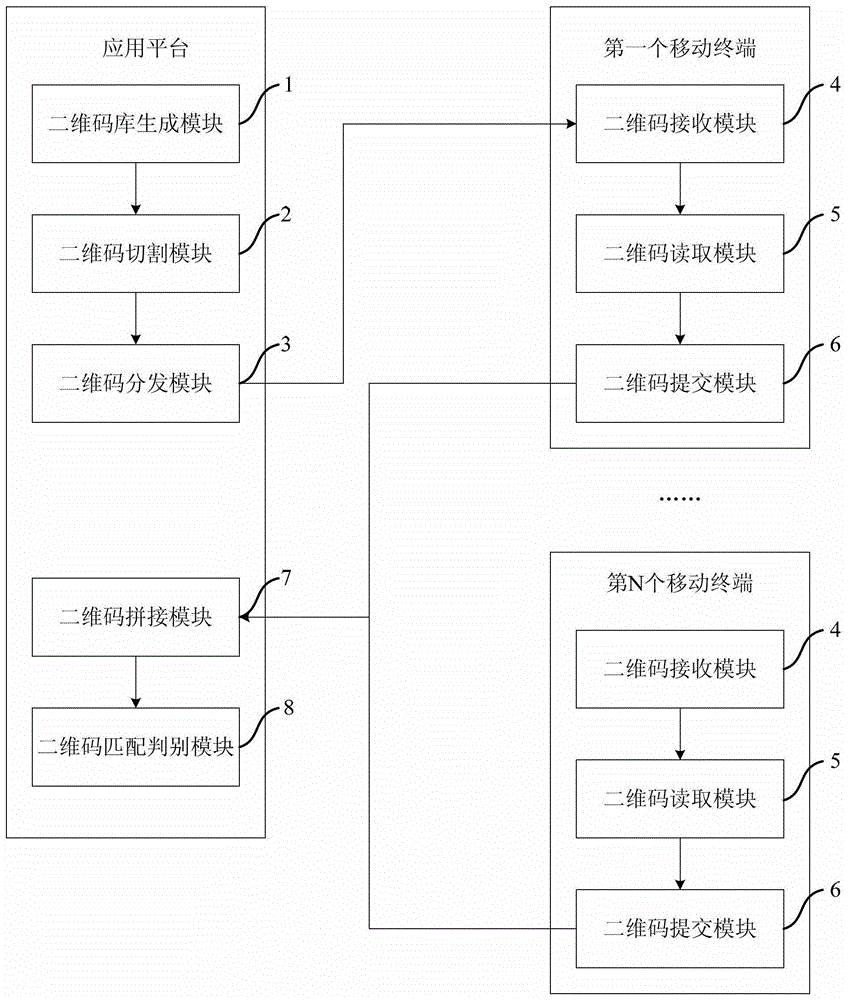
[0045] This embodiment provides a two-dimensional code cutting and splicing authentication system, which is applied to a two-dimensional code authentication system composed of an application platform and at least two mobile terminals. The system is as follows: figure 1 As shown, it includes: an application platform, and at least two mobile terminals, wherein the system includes a two-dimensional code library generation module 1, a two-dimensional code cutting module 2, a two-dimensional code distribution module 3, a two-dimensional code receiving module 4, Two-dimensional code reading module 5 , two-dimensional code submission module 6 , two-dimensional code splicing module 7 , and two-dimensional code matching and judging module 8 .
[0046] The two-dimensional code library generation module 1 is used to form a two-dimensional code library from a plurality of two-dimensional code pictures, and systematically number each two-dimensional code picture in the two-dimensional code ...
Embodiment 2
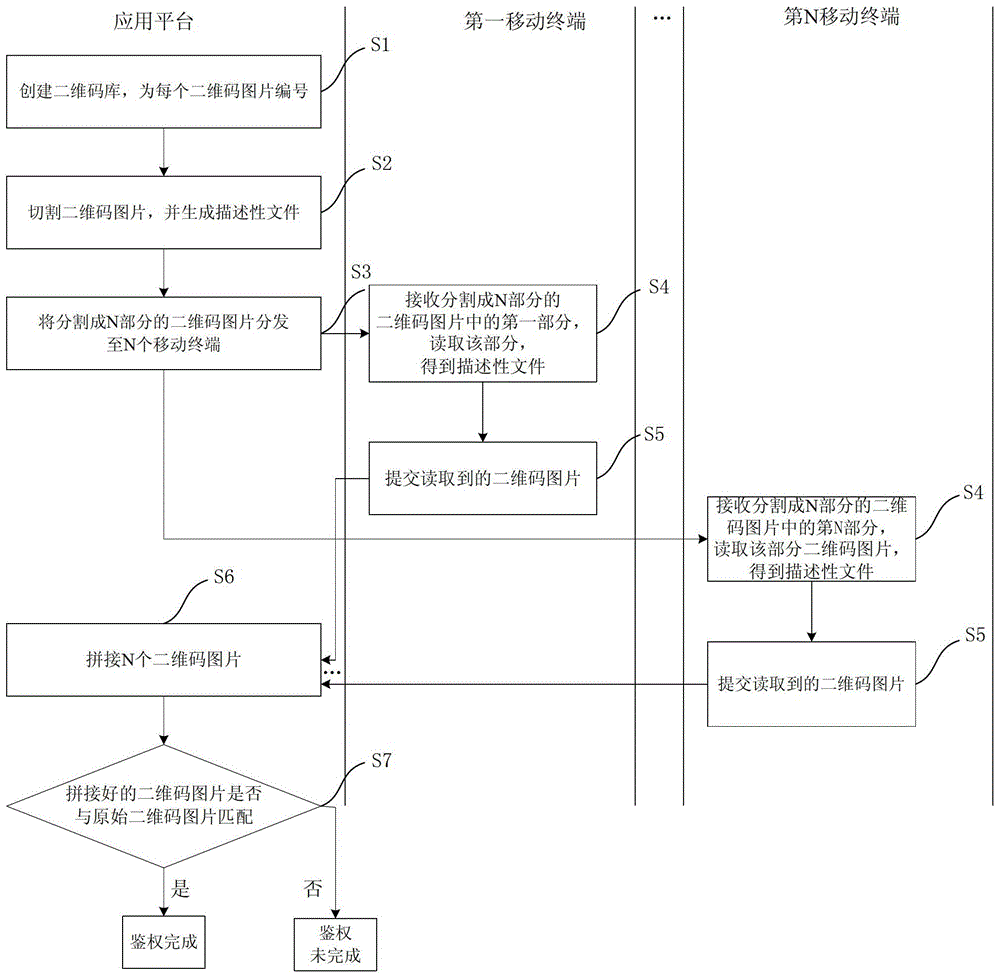
[0056]This embodiment provides a two-dimensional code cutting and splicing authentication method, which is applied to a two-dimensional code authentication system composed of an application platform and at least two mobile terminals. The two-dimensional code cutting and splicing authentication method is as follows: image 3 shown, including:
[0057] S1. Create a two-dimensional code library composed of multiple two-dimensional code pictures, and perform a system number for each two-dimensional code picture in the two-dimensional code library. Wherein, the serial number of each QR code image is unique.
[0058] S2, cutting a two-dimensional code picture in the two-dimensional code library into N parts, and generating a descriptive file for each part; for example, in this embodiment, dividing the two-dimensional code picture into part A and part B, The descriptive documents for Part A include:
[0059] Position Part A description file name
[0060] OX123456789 unique number ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com