Efficient terminal alarm processing method
A processing method and terminal technology, applied in the field of IT operation and maintenance, can solve problems such as system crash, inability to achieve different alarms and different devices without affecting each other, and inability to efficiently and stably handle alarm events, so as to reduce daily workload and provide reliable data basis. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
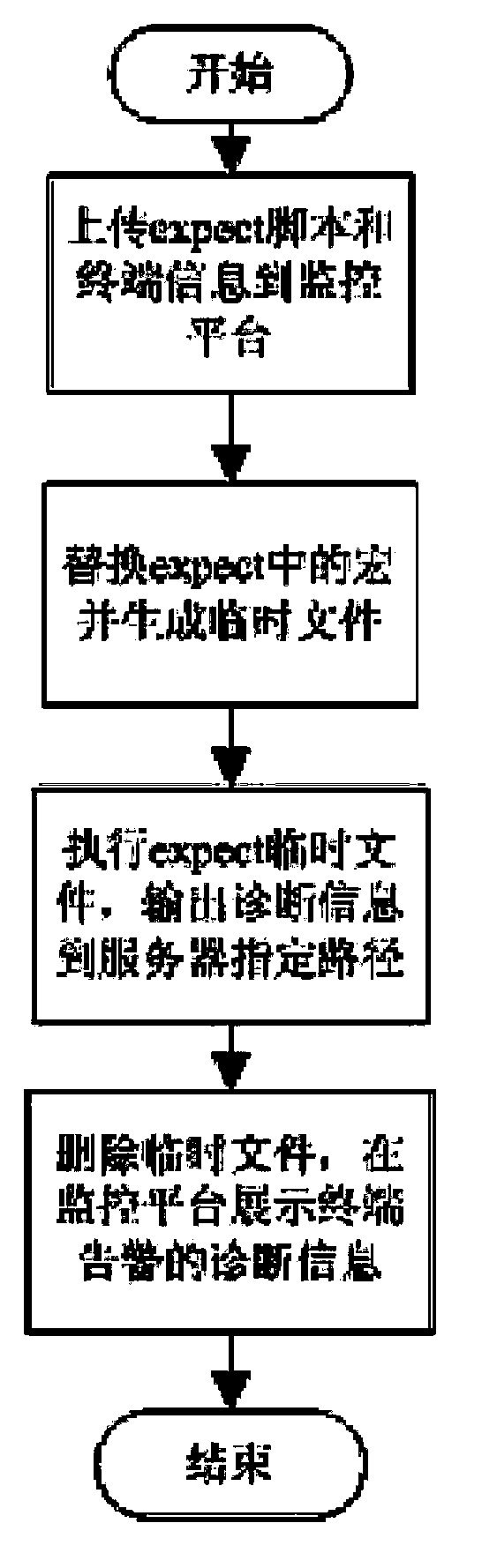
Image
Examples
Embodiment 1
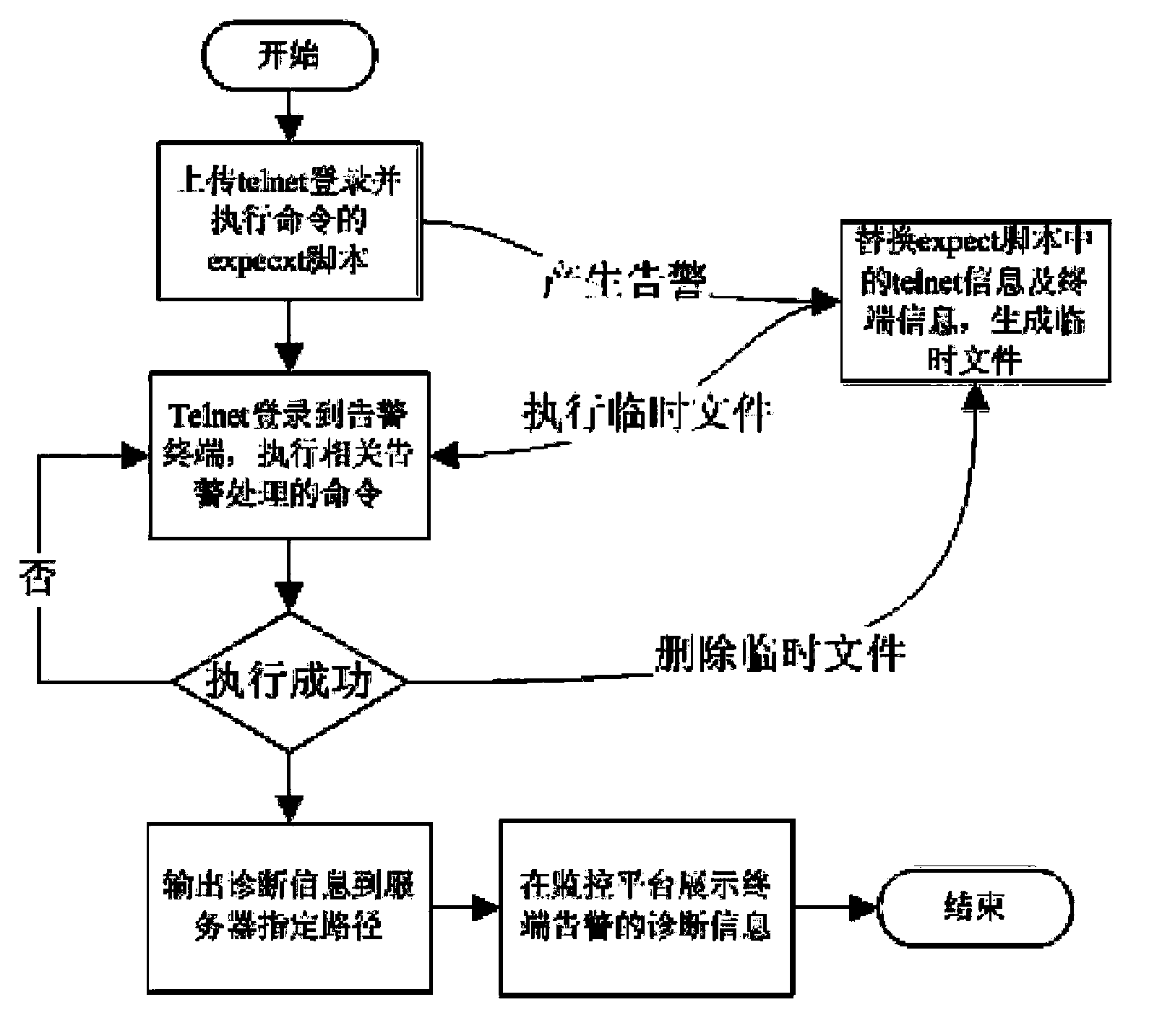
[0016] Embodiment one: if figure 1 and figure 2 As shown, this example uses telnet to obtain the load information of the alarm terminal as the alarm processing scheme. The specific steps of using the method of the present invention are as follows: 1) Install the expect script environment in the server, upload the telnet remote login in the monitoring system and execute the command to obtain the load The expect script file, the telnet login user name in the file, telnet login password, telnet general terminator, telnet privileged mode password, telnet privileged mode terminator, telnet login user prompt, telnet login password prompt, telnet privileged password prompt 2) When an alarm occurs, the monitoring system replaces the macro value in the expect file with the terminal telnet information and device IP in the database, generates and executes the temporary file, and telnet remotely Log in to the terminal device, execute the command to obtain the load, and output the return...
Embodiment 2
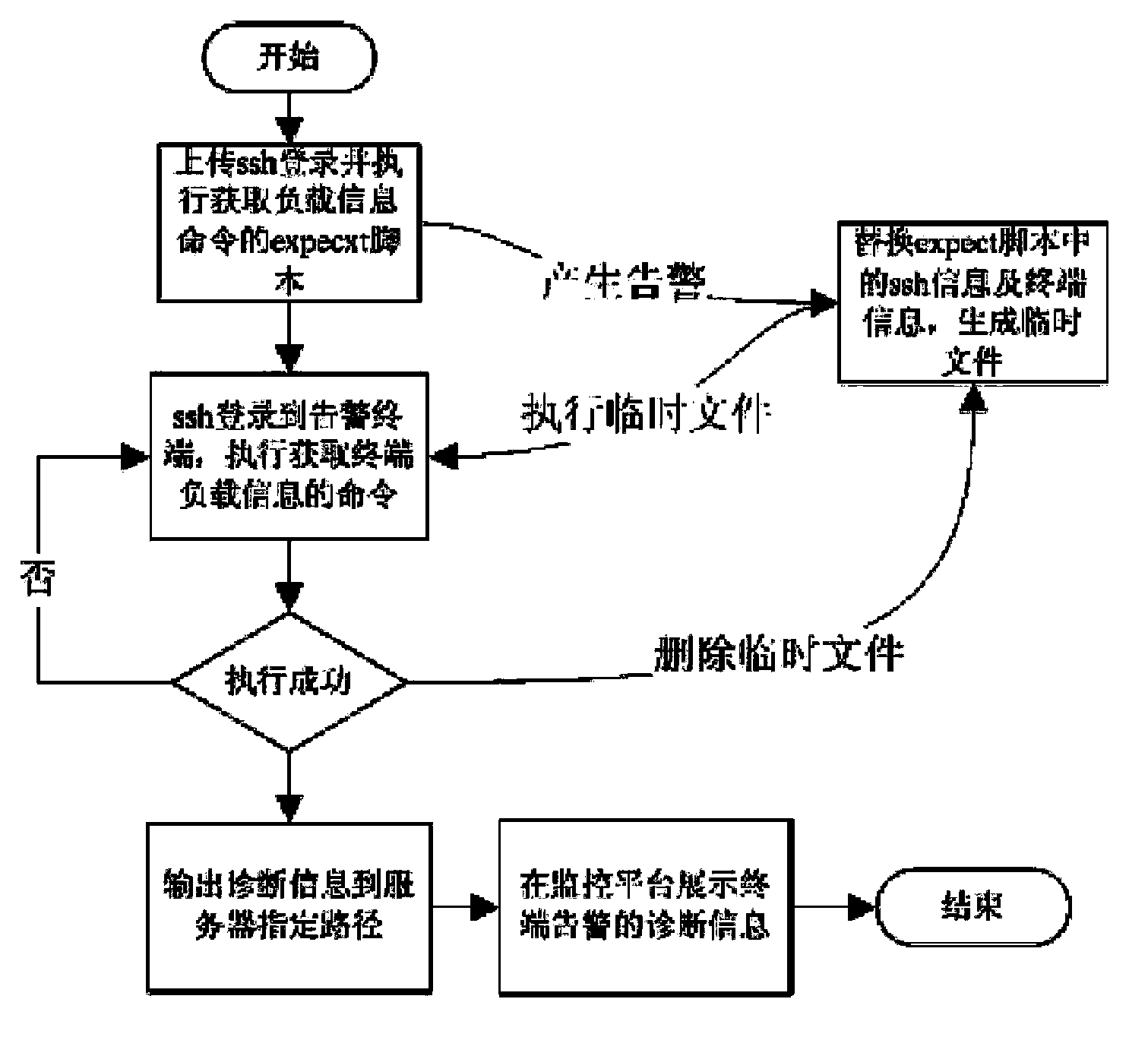
[0017] Embodiment two: if figure 1 and image 3 As shown, this example takes ssh to obtain the load information of the alarm terminal as an example. The specific steps are as follows: 1) Install the expect script environment in the server, upload the ssh remote login in the monitoring system and execute the expect script file to obtain the load command. The ssh login user name, ssh login password, terminal IP, and absolute path of the diagnostic file in the ssh file are replaced by macro values; 2) When an alarm is generated, the monitoring system replaces the macro value in the expect file with the terminal ssh information and device IP in the database, Generate and execute the temporary file, ssh remote login to the terminal device, execute the command to obtain the load, and output the returned result to the specified directory; 3) After the command is executed, the monitoring system deletes the temporary file, and returns the diagnostic information of the returned result a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com