Electric power security communication network based on quantum key distribution technology
A quantum key distribution, quantum key distribution technology, applied in key distribution, can solve problems such as cracking and tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
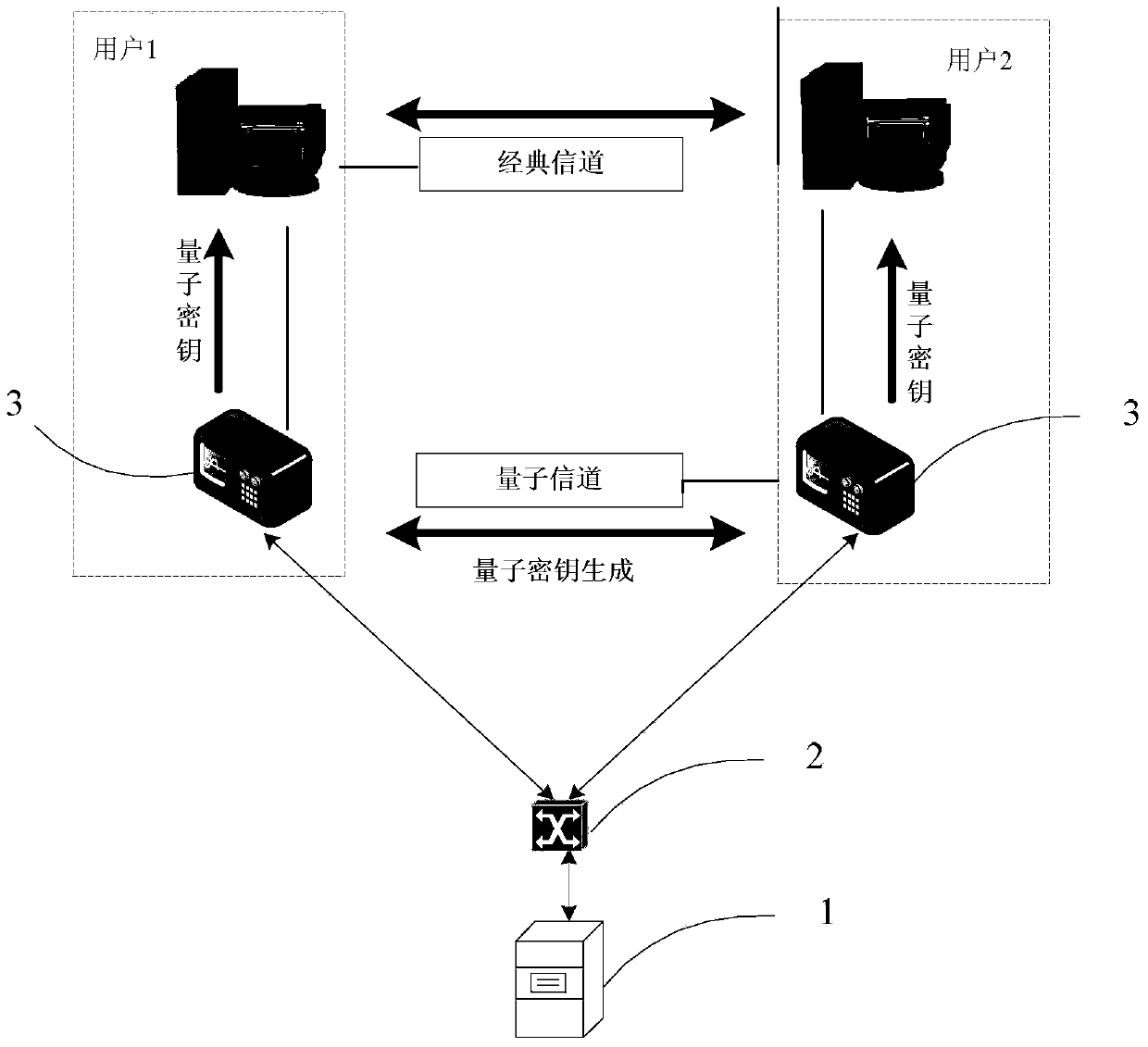
[0044] see figure 2 as shown, figure 2 In , only the principle of mutual communication between any two users in the power security communication network based on quantum key distribution technology is shown, that is, a model combining the QKD system and the power longitudinal encryption authentication device is established. An electric power security communication network based on quantum key distribution technology of the present invention includes a key generation control server 10 , a classical switch 20 , a QKD system 30 and an electric power longitudinal encryption authentication device 40 .
[0045] The key generation control server 10 is connected to the QKD system 30 through the classical switch 20, each user terminal includes a power vertical encryption authentication device 40, and each power vertical encryption authentication device 40 deploys a QKD system 30. The QKD system 30 is connected with the corresponding power longitudinal encryption authentication devic...
Embodiment 2
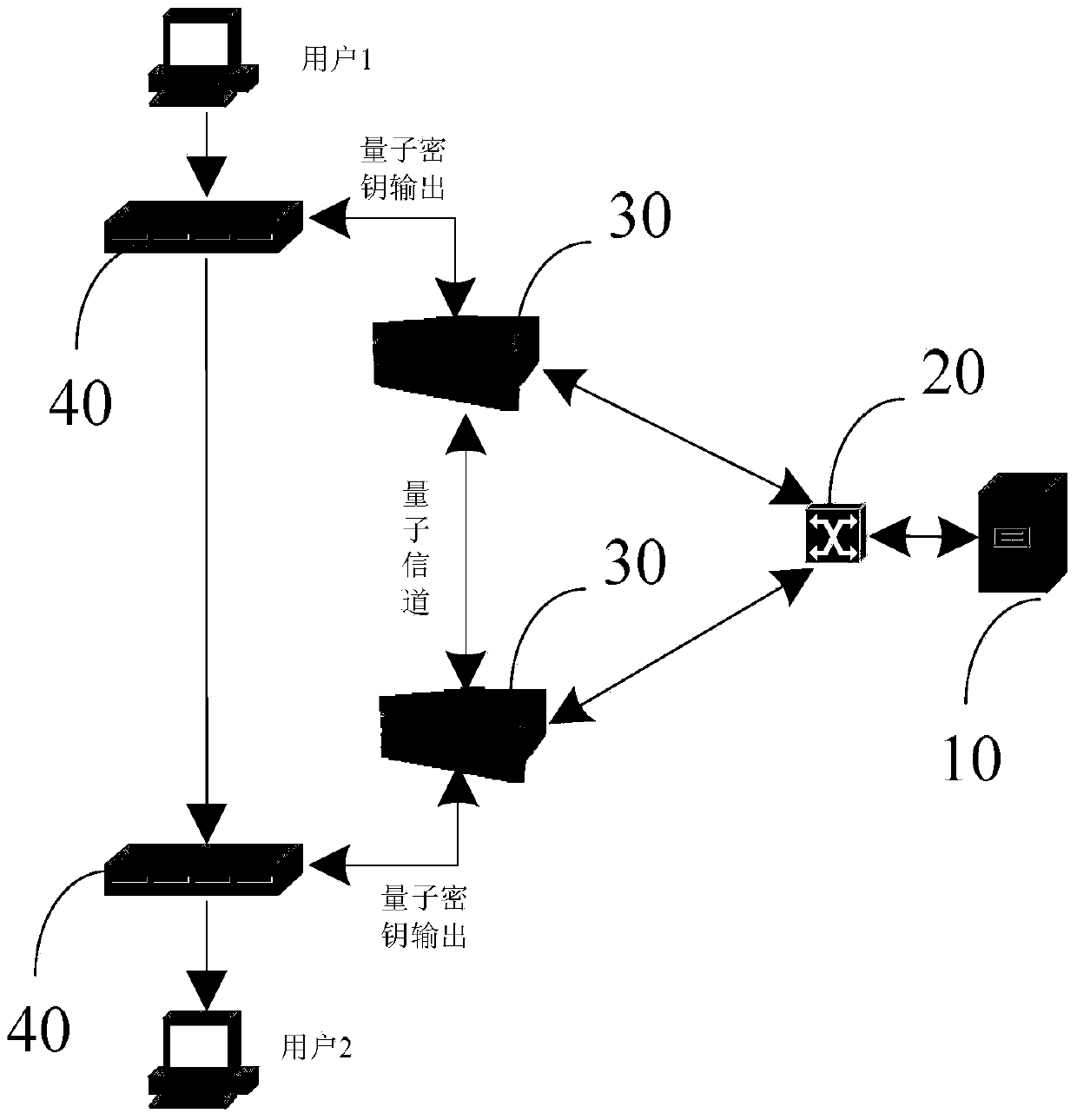
[0048] like image 3 As shown in Fig. 1 , the model of the combination of QKD system and power longitudinal encryption and authentication device is given in the multi-user application scenario of power system. In fact, power communication networks exist with multiple users at the same time. Taking provincial-level power communication networks as an example, existing power communication networks usually have provincial power dispatching centers, city management centers under the jurisdiction of the province, and city subordinates. each factory station. Each plant has multiple power users. In order to realize the communication between any two users, in this embodiment, on the basis of the model of the power security communication network based on the quantum key distribution technology in the first embodiment, an all-pass optical quantum switch is used, and the specific structure as described below.
[0049] The power security communication network based on quantum key distri...
Embodiment 3
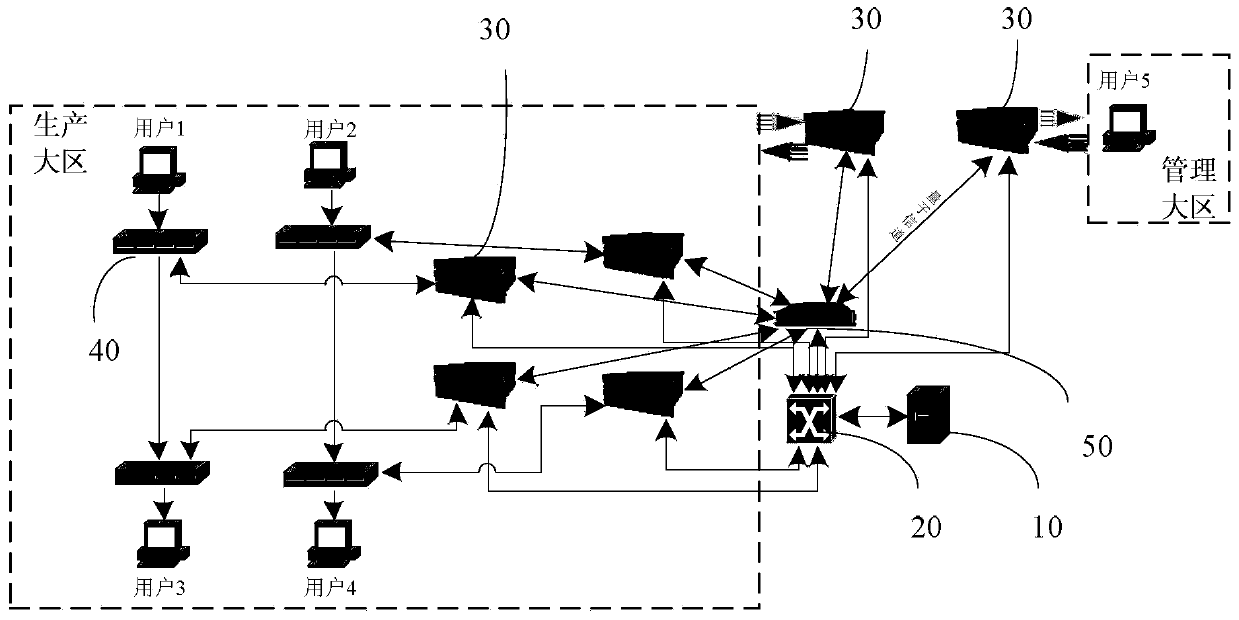
[0058] As mentioned above, in the actual electric power communication network, multiple users exist at the same time. Taking the provincial electric power communication network as an example, the existing electric power communication network usually has a provincial electric power dispatching center. The city management center, each plant station under the city, and each plant station includes multiple power users. Embodiment 2 discusses encrypted data transmission between multiple power users under each plant station. refer to Figure 4 , this embodiment gives an example of the integration of the power communication network and the quantum network under the jurisdiction of the provincial dispatching center. In this embodiment, an implementation based on a quantum centralized control station will be described. For the implementation based on trusted relay, there is no substantial difference in principle from the implementation based on quantum centralized control station. Af...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com