Identity authentication based virtual terminal safety environment protection method and system
A technology of virtual terminal and security environment, applied in the field of protection of virtual terminal security environment, can solve the problems of data not being retained, data leakage, and data protection processing, etc., to prevent data leakage and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
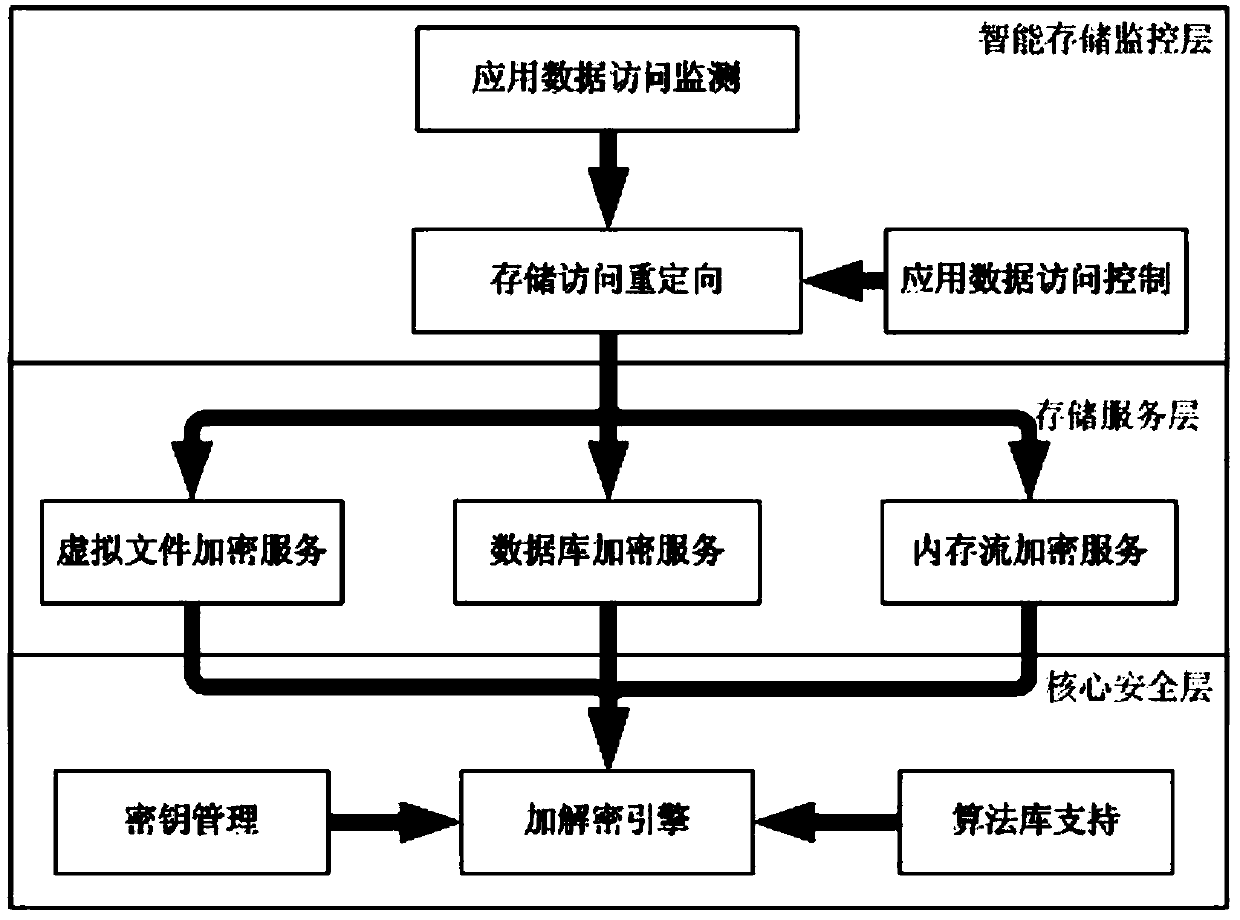
[0076] image 3 It is the overall system frame diagram in the present invention.
[0077] The virtual terminal safety environment protection system based on identity authentication proposed by the present invention is generally divided into three layers: an intelligent storage monitoring layer, a storage service layer, and a core security layer. The intelligent monitoring layer is responsible for monitoring and analyzing the data access behavior of the application program, executing actions according to the configuration rules, and the redirection module transfers I / O access according to the access control rules; the storage service layer is responsible for encrypting or decrypting files or data, and recording files Mapping relationship; the core security layer is the foundation of the entire architecture, providing key management functions, providing encryption and decryption support for the storage service layer, and scheduling different algorithms according to requirements....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com