Mobile intelligent terminal safety detection method based on boundary detection
A mobile smart terminal, security detection technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as poor platform compatibility, low efficiency, and unintuitiveness, and achieve good compatibility and high efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings.
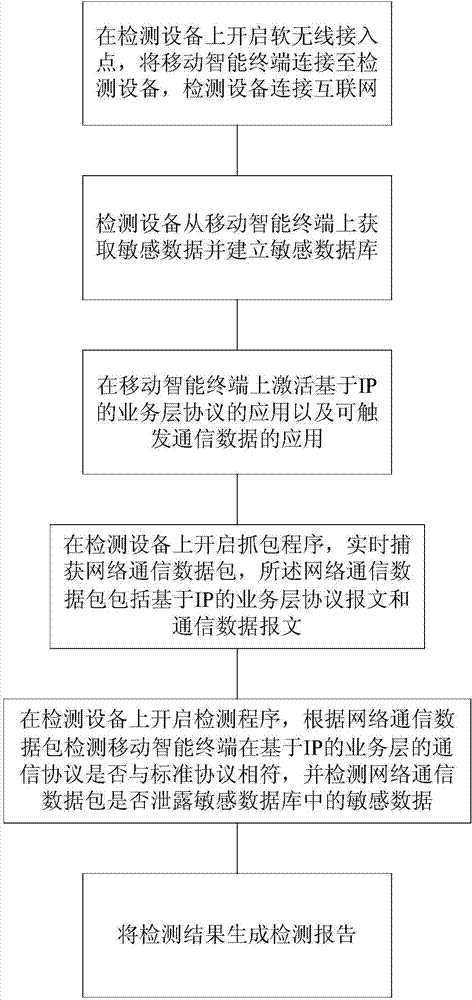
[0036] Such as figure 1 As shown, a mobile intelligent terminal security detection method based on boundary detection includes the following steps:
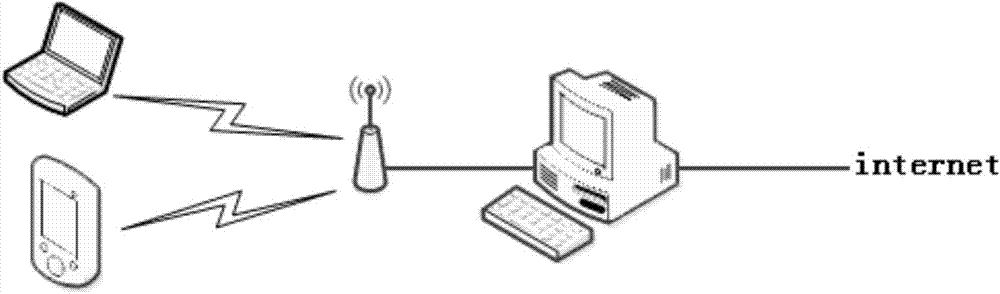
[0037] (1) Turn on the soft wireless access point on the detection device, connect the mobile smart terminal to the detection device, and connect the detection device to the Internet such as figure 2 As shown in , the detection device is a PC running the Linux platform and the detection tool has been installed.
[0038] The soft wireless access point is an open wireless access point established by switching the wireless network card to AP / Master mode through Hostapd and modifying the configuration file.
[0039] (2) The detection equipment obtains sensitive data from mobile smart terminals and establishes a sensitive database.
[0040] (3) Activate the application of IP-based business layer protocol and the applicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com