Network security detection method and system
A network security and detection method technology, applied in the field of network security detection methods and systems, can solve the problem of unable to identify network attacks and intrusions, virus detection can not solve network attacks, network behavior audit problems, and can not simultaneously realize the analysis of network security status, User behavior recording, attack monitoring and other issues to improve security
Active Publication Date: 2014-05-14
BEIJING TOPSEC SOFTWARE +3
View PDF4 Cites 42 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Virus detection cannot solve the problem of network attack and network behavior audit
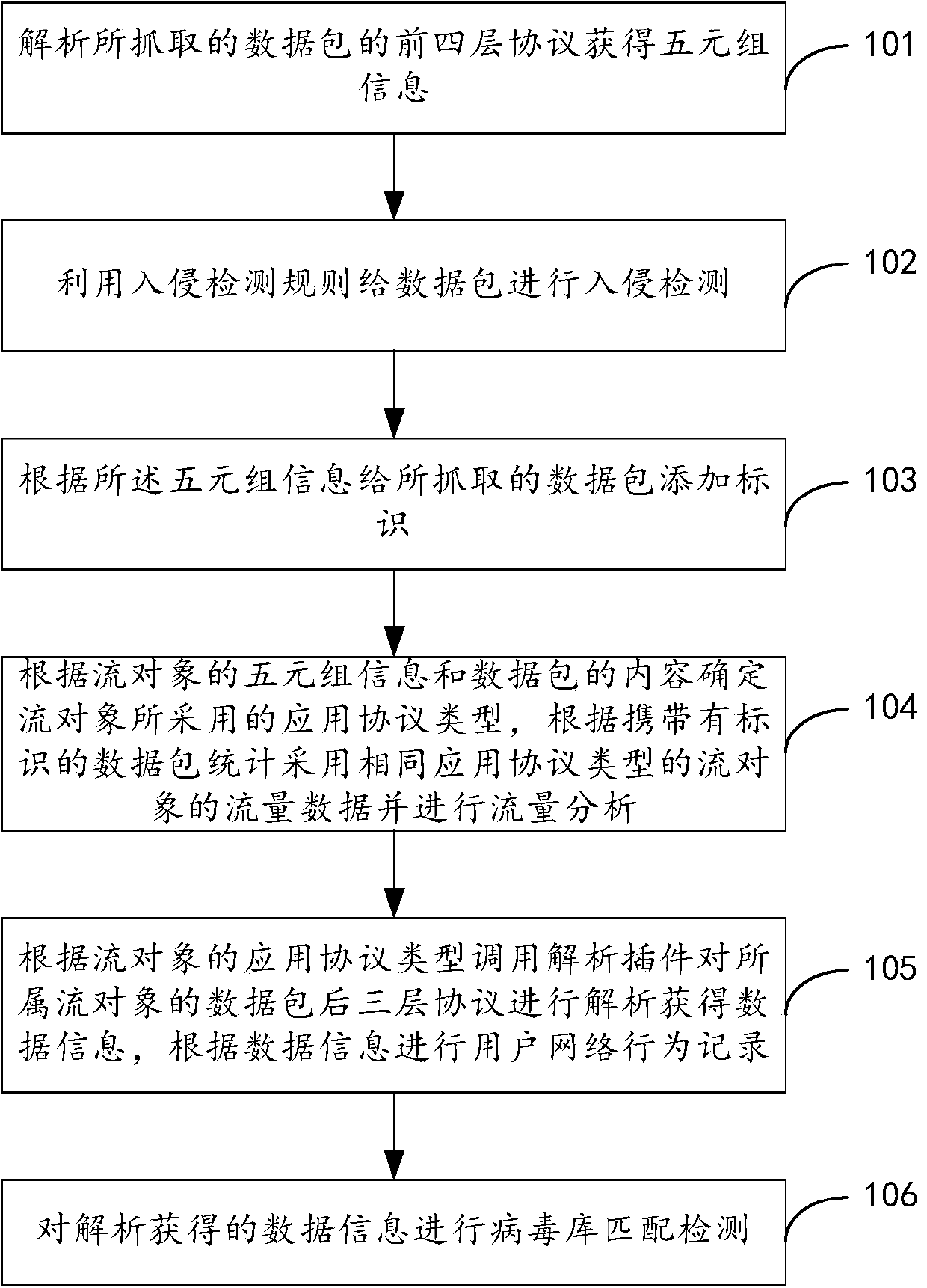
[0007] For most network devices, such as switches, routers, etc., only one data monitoring interface is configured for network security monitoring, and only one of the above methods can be used for security detection of network access. The above-mentioned technologies for network access security detection are different. There are advantages and disadvantages. Simply relying on a network security detection technology cannot identify all kinds of network attacks and intrusions, and cannot simultaneously realize the functions of network security status analysis, user behavior recording, attack monitoring and unknown malicious code identification.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 2
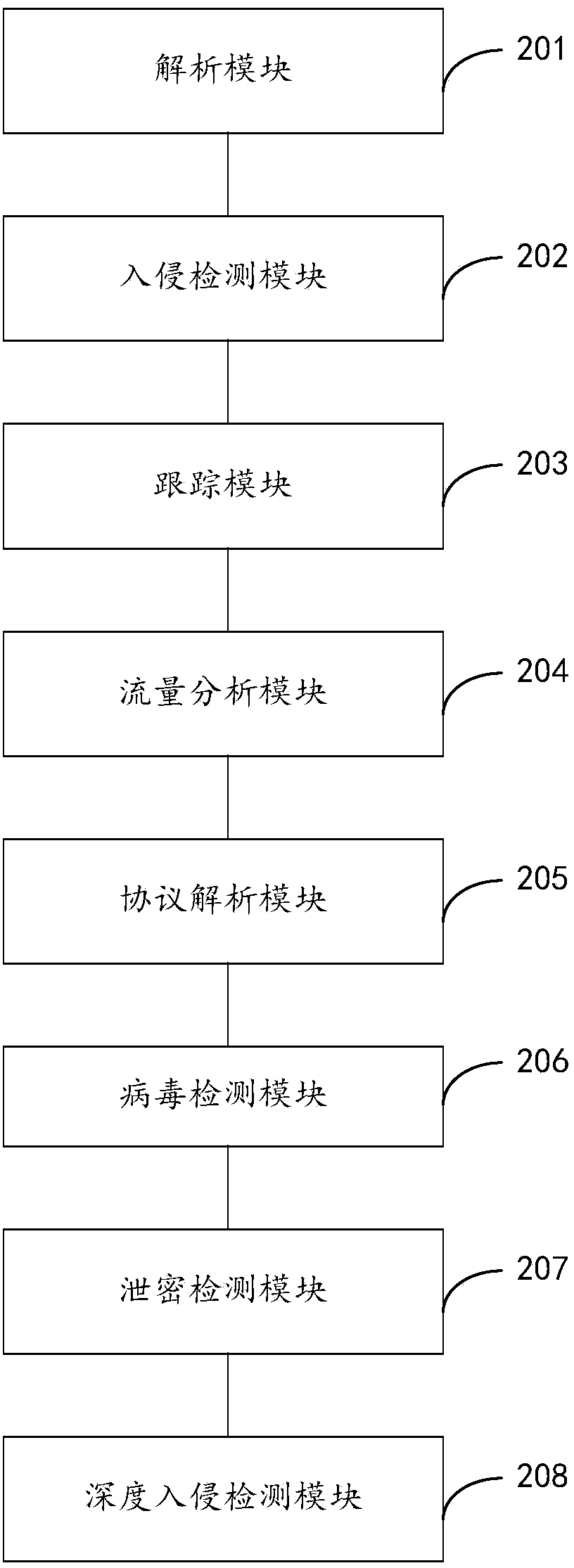
[0068] figure 2 It is a schematic structural diagram of Embodiment 1 of a network security detection system according to the present invention, and it is a system corresponding to the method described in Embodiment 1. The system includes:
[0069] The parsing module 201 is configured to parse the first four-layer protocol of the captured data packet to obtain quintuple information.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention provides a network security detection method and system. First four layers of a protocol of a capture data packet are analyzed to obtain quintuple information; an intrusion detection rule is used to carry out intrusion detection to the data packet; the quintuple information is used to add an identifier to the captured data packet; according to quintuple information of a stream object and a content of the data package, an application protocol type applied in the stream object is determined; according to the data packet with the identifier, flow data of the stream object using the same application protocol type is calculated and undergoes flow analysis; according to the application protocol type of the stream object, an analysis plug-in is used to analyze a data packet application layer protocol of the corresponding stream object so as to obtain data information; according to the data information, a user network behavior record is carried out; and the obtained data information obtained by analyzing is detected by matching a virus database. The intrusion detection, the network behavior detection, the abnormal flow analysis and the virus detection are integrated in one system, and only one interface is needed to realize multiple detection methods of the network access.
Description
technical field [0001] The invention relates to the technical field of network security, in particular to a network security detection method and system. Background technique [0002] With the development of Internet technology, in order to prevent malicious network access from destroying, changing, and leaking data in the network system, and to ensure the safe and reliable operation of the network system, it is necessary to perform security detection on network access. Currently commonly used network security detection technologies include intrusion detection technology, network behavior audit technology, abnormal traffic analysis and calculation, and virus detection technology. [0003] The intrusion detection technology collects behavioral characteristics of abnormal network access and establishes a behavioral characteristic database. When a network access matching the behavioral characteristic database is detected, the network access is defined as intrusion access. The ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06
Inventor 张凤羽
Owner BEIJING TOPSEC SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com