Methods of judging and blocking outlets
A network, judgment and processing technology, applied in electrical components, transmission systems, etc., can solve problems such as data outflow, computer poisoning, computer system failure, etc., and achieve the effect of rigorous and effective methods, ensuring confidentiality, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The specific embodiments adopted by the present invention will be further described by the following embodiments and attached drawings.
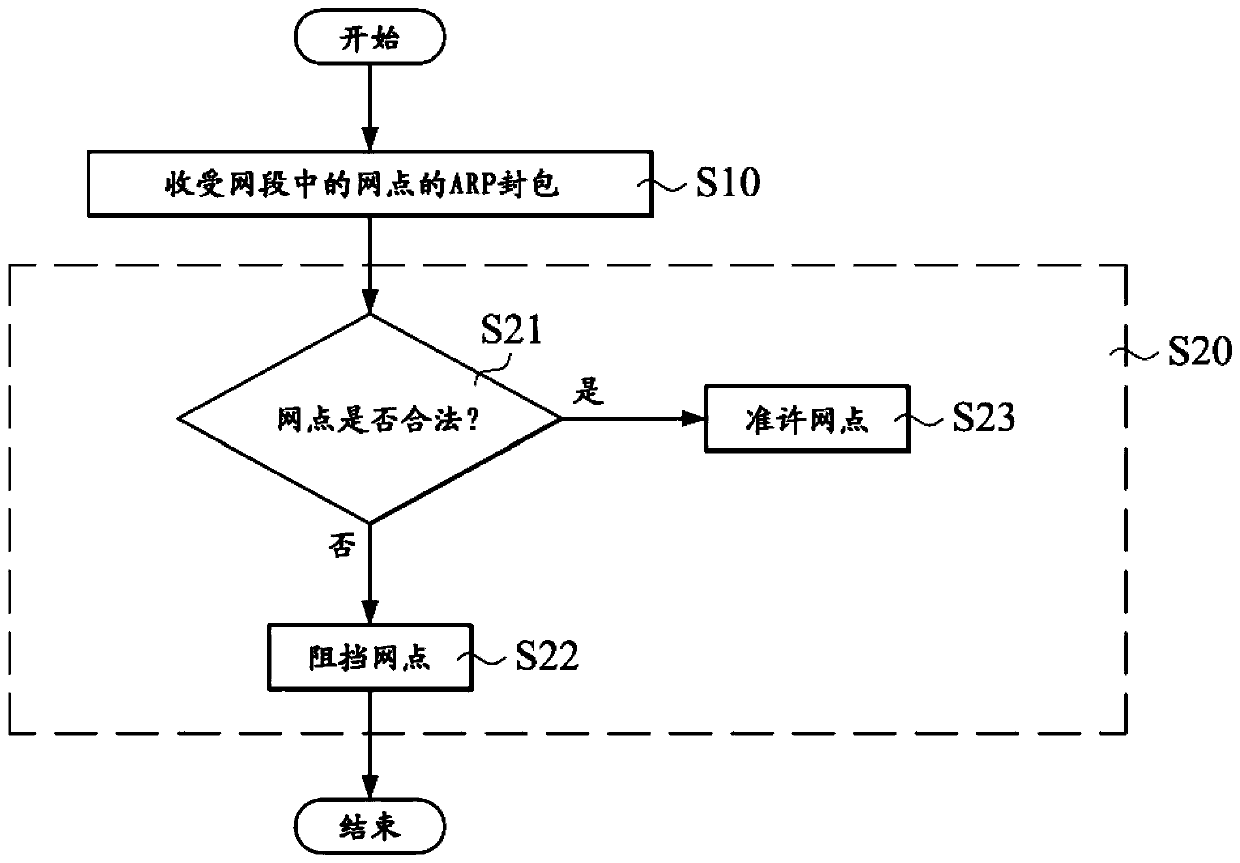
[0032] The invention provides a method for judging and blocking a network point, which is to judge whether the corresponding network point is a legitimate network point in a network segment according to an ARP (Address Resolution Protocol) packet, and decide whether to block the network point according to whether it is legal or not. Please refer to the following Figure 1 to Figure 3 The method of judging and blocking network points in the first embodiment of the present invention is described as follows.
[0033] Such as figure 1 As shown, it is a flow chart showing the method for judging and blocking network points according to the first embodiment of the present invention. The method for judging and blocking an outlet according to the first embodiment of the present invention mainly includes a packet receiving step and a packet j...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com