Privacy protection method based on trusted third party attribute fuzzy grouping under cloud environment
A privacy protection and cloud environment technology, applied in the field of data privacy protection based on trusted third parties, can solve problems such as illegal reading of user data, user identity and attribute privacy leakage, cloud privacy data leakage, etc., to prevent malicious parties from attacking , Protect identity privacy, ensure security effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
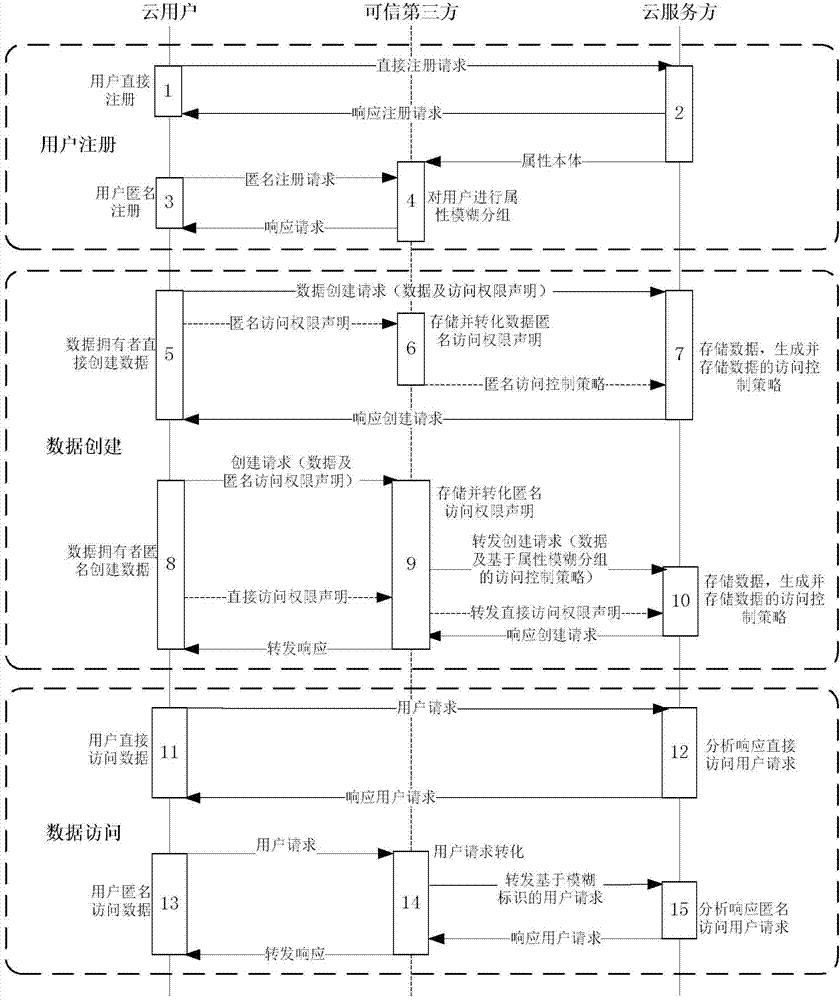
[0025] The specific implementation process of the privacy protection method based on the fuzzy grouping of trusted third-party attributes according to the present invention is as follows: figure 1 shown, including the following steps:
[0026] Step 1: Cloud user registration.
[0027] Cloud user registration can choose direct or anonymous method.
[0028] Step 1.1: Register using the direct method.
[0029] (1) The user submits a direct registration request to the cloud service provider.
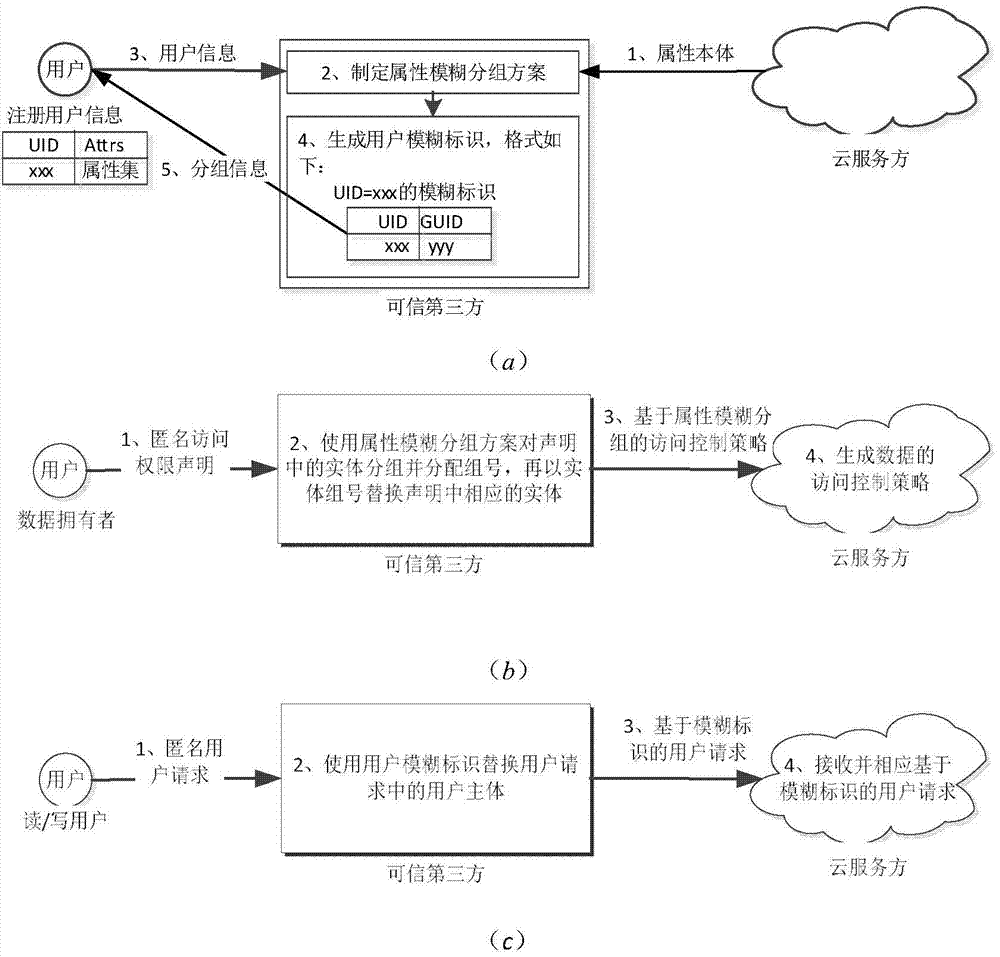
[0030] (2) The cloud responds to the user's registration request. At the same time, the cloud sends the attribute ontology to the trusted third party, and the trusted third party provides an anonymous registration method based on the attribute ontology.
[0031] Step 1.2: Register anonymously.
[0032] (1) The user submits an anonymous registration reque...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com