Security inspection device and method for identifying forbidden objects using same
A technology for equipment and articles, applied in the field of detection equipment, can solve the problems of inability to effectively detect explosives, prohibited drugs, labor costs, cumbersome and other problems, and achieve the effects of enhancing applicability, expanding scope and simple operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
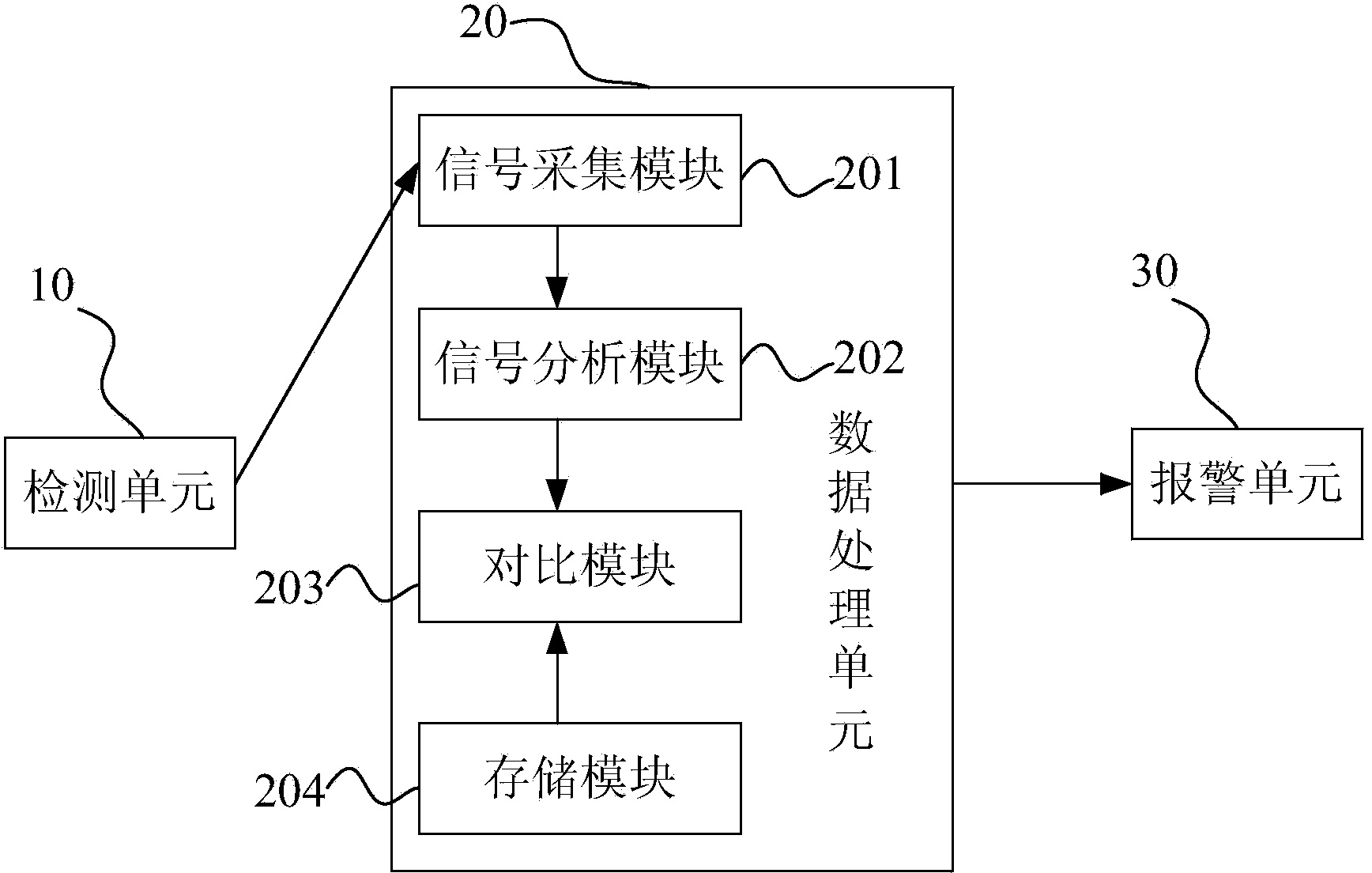
[0024] figure 1 A schematic diagram of the composition of the security inspection equipment provided in this embodiment. Such as figure 1 As shown, in this embodiment, the security inspection equipment for identifying prohibited items includes: a detection unit 10, which is used to detect the items to be inspected; a data processing unit 20, which is used to receive the detection signal sent by the detection unit 10, and Analyzing and processing the detection signal to obtain an analysis result; the alarm unit 30 is configured to activate when the analysis result shows that the item to be inspected is a prohibited item, and alarm to remind relevant security personnel for further inspection.
[0025] Specifically, such as figure 1 As shown, the above-mentioned data processing unit 20 includes: a signal acquisition module 201, which is used to receive the above-mentioned detection signal; a signal analysis module 202, which is used to analyze the received detection signal and ...
Embodiment 2
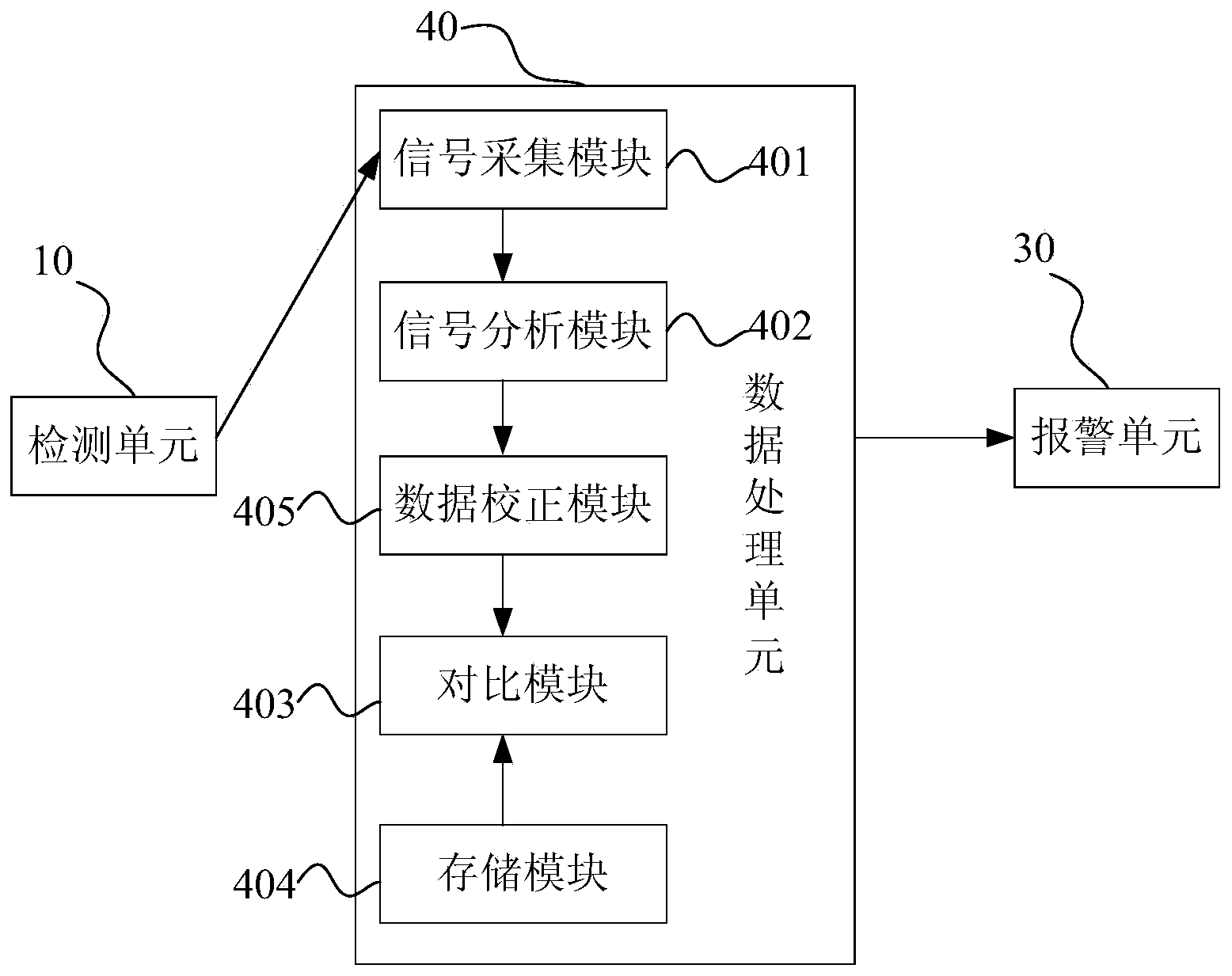
[0032] image 3 A schematic diagram of the composition of the security inspection equipment provided in this embodiment, Figure 4 Then it is a flow chart of the identification method for identifying prohibited items by using the security inspection equipment of this embodiment. Such as image 3 As shown, the difference between the security inspection equipment provided in this embodiment and the first embodiment is that in this embodiment, the data processing unit 40 also includes a data correction module 405, which can be used to output the signal analysis module 402 The characteristic data is corrected according to the calibration standard and then output to the comparison module 403 for comparison.
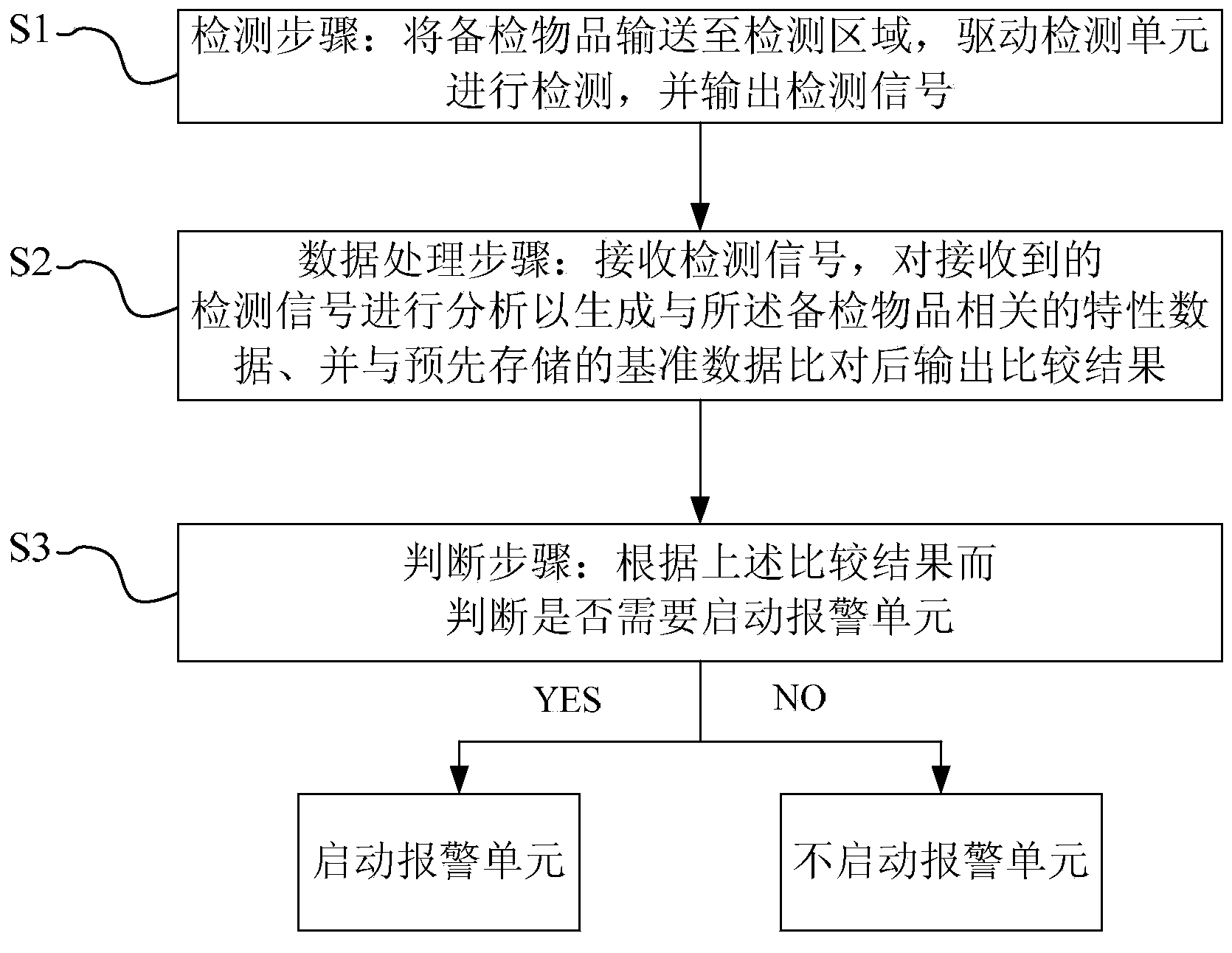
[0033] Correspondingly, as Figure 4 As shown, the data processing step S2' in the identification method in this embodiment adds the operation of "correcting the above characteristic data according to the calibration standard" compared with the data processing step S2 in th...
Embodiment 3
[0036] This embodiment can be obtained by expanding on the basis of Embodiment 1 or 2; and in order to better explain the technical solution, the following takes Embodiment 2 as an example, and specifically describes the solution of this embodiment on the basis of it.
[0037] Figure 5a and 5b are respectively the disassembled schematic diagram and the overall appearance schematic diagram of the security inspection equipment provided in this embodiment, Figures 6a-6c It is the front view, side view and bottom view of the security inspection equipment. Among them, such as Figure 5a As shown, in addition to the components described in Embodiment 1 or Embodiment 2, the security inspection equipment also includes: a moving part 1, which can be composed of a conveying mechanism such as a conveyor belt, and is used to move the items to be inspected to the inspection area for inspection; The rolling part 2 rolls around the moving part 1 at a certain constant speed, and the dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com