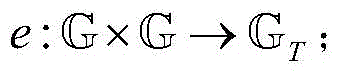An identity-based cross-system proxy re-encryption method
A proxy re-encryption and cross-system technology, applied in transmission systems, public keys for secure communications, electrical components, etc., can solve problems such as differences in ciphertext structure and public keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
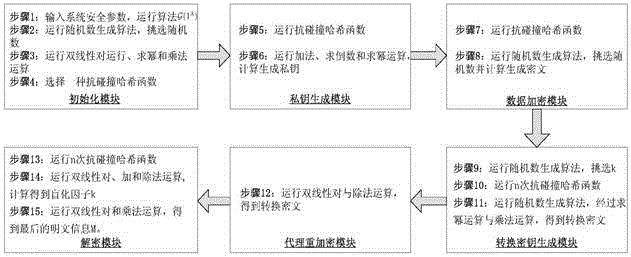
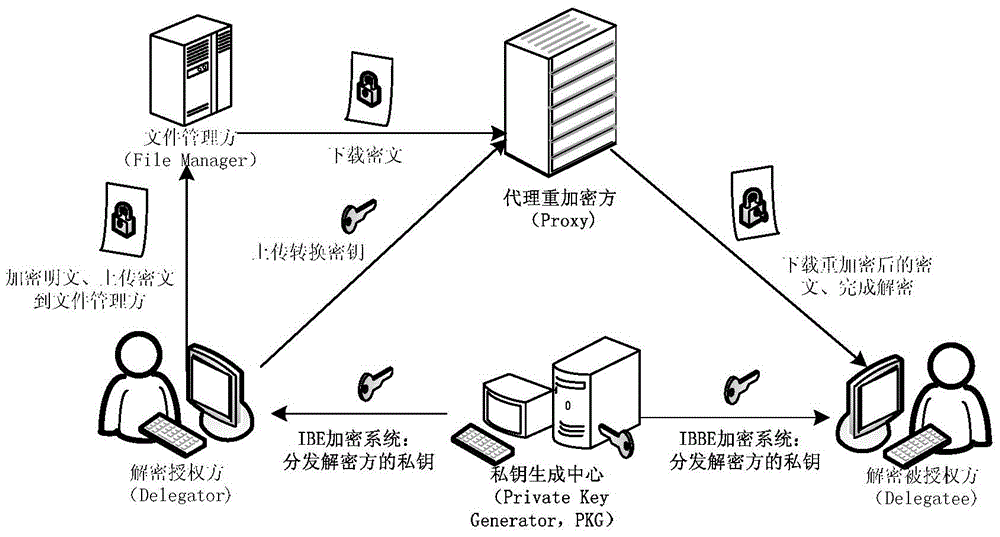
[0104] The present invention is an identity-based cross-system proxy re-encryption method, see figure 1 , 2 As shown, the method is implemented by six modules: an initialization module, a private key generation module, a data encryption module, a conversion key generation module, a proxy re-encryption module, and a decryption module. See the system flow of the entire proxy re-encryption method operation figure 2 , Combined with the flow chart, the specific implementation steps of this method are introduced as follows:
[0105] Module 1: Initialize the module
[0106] The realization of the module function is divided into four steps:
[0107] Step 1: PKG first enters the system safety parameter λ, and runs the algorithm g(1 λ ), output two groups of prime order p And a bilinear mapping operation
[0108] Step 2:
[0109] PKG then runs the random number generation algorithm and randomly selects A generator g in the group, An element h in the group, and An element α in the domai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com