Cryptographic algorithm customizing method
A cryptographic algorithm and cryptographic technology, applied in the field of cryptographic algorithm customization, to reduce the value of information, increase the cost of cracking, and reduce the cost of development and difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
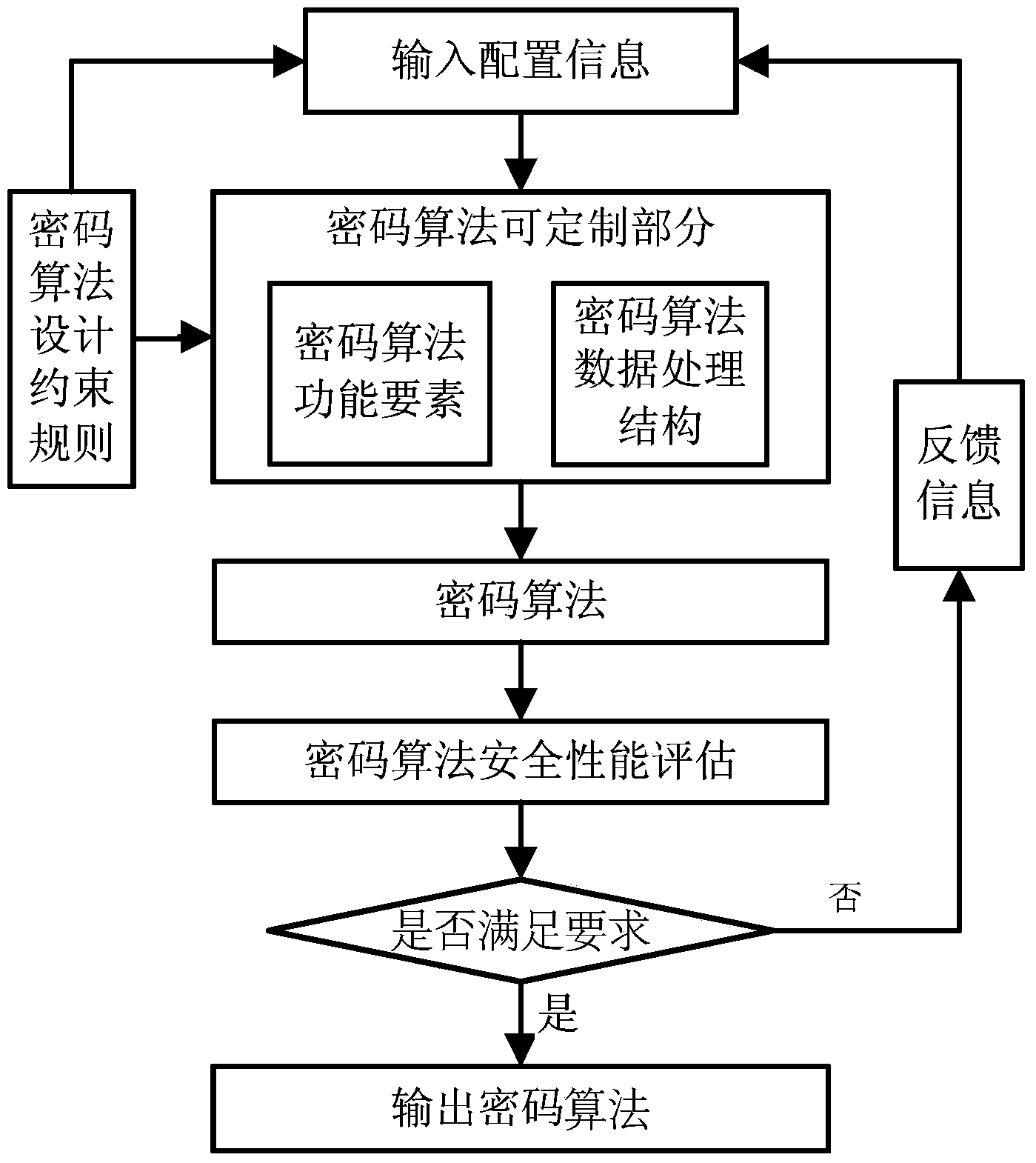
[0053] A specific example of supporting the custom design of the block cipher algorithm is given below. By configuring the functional elements of the cryptographic algorithm and the data processing structure of the cryptographic algorithm, a self-customized Feistel block cipher can be realized.
[0054] Cryptographic algorithm functional elements:
[0055] The functional elements of the cryptographic algorithm in this implementation example include a confusion unit, a diffusion unit, an involution operation unit, a key addition unit, a key expansion unit, and a round function.
[0056] The confusing unit can be composed of one or more sub-functions (such as f 1 , f 2 ,..., f k ) to construct, providing the capability of nonlinear transformation. The sub-function may be one or more SBoxes, or a function composed of SBoxes and algebraic operations. The algebraic operations may include: one or more of addition, subtraction, multiplication, division, shift, AND, OR, NOT, XOR ...
Embodiment 2
[0098] A specific example of supporting the custom design of the hash algorithm is given below. By configuring the functional elements of the cryptographic algorithm and the data processing structure of the cryptographic algorithm, a self-customized hash cryptographic algorithm can be realized.
[0099] Cryptographic algorithm functional elements:
[0100] The functional elements of the cryptographic algorithm in this implementation example include a message filling unit, an expansion unit, and a compression unit.
[0101] The message filling unit is a functional unit that can fill a data string of a certain length with some data at the back of the data string according to a certain filling rule, so that the length of the filled data string is an integer multiple of the message packet length or function. The filling rule can be defined by the user, and the length of the message packet can be defined by the user.
[0102] The expansion unit is a functional unit or function c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com