Dynamic encryption method of IoT devices based on login serial number
An Internet of Things device and dynamic encryption technology, which is applied in the field of Internet of Things and data security, can solve problems such as low computing power, high requirements for processor computing speed and storage resources, and increase the risk of keys being cracked, and achieve storage resource The effect of low demand for computing power, increasing the difficulty of cracking, and increasing the cost of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
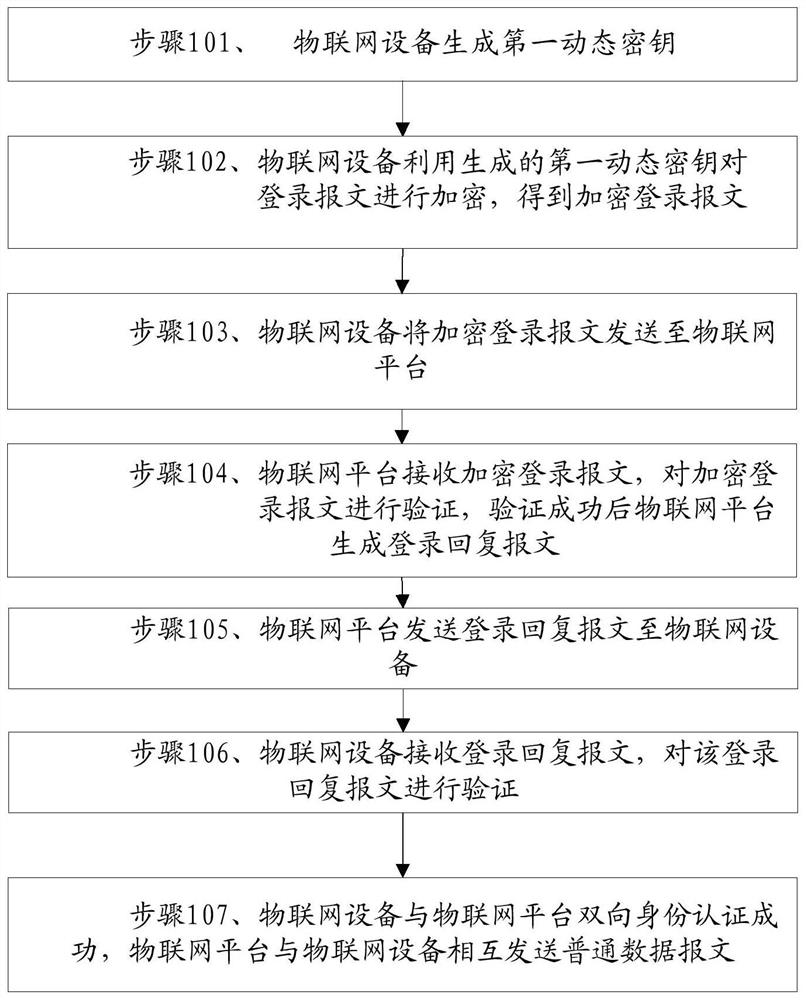
[0059] see figure 1 Shown is a specific embodiment of the method for dynamically encrypting Internet of Things devices based on the login serial number described in this application, and the method includes:
[0060] Step 101, the IoT device generates a first dynamic key:
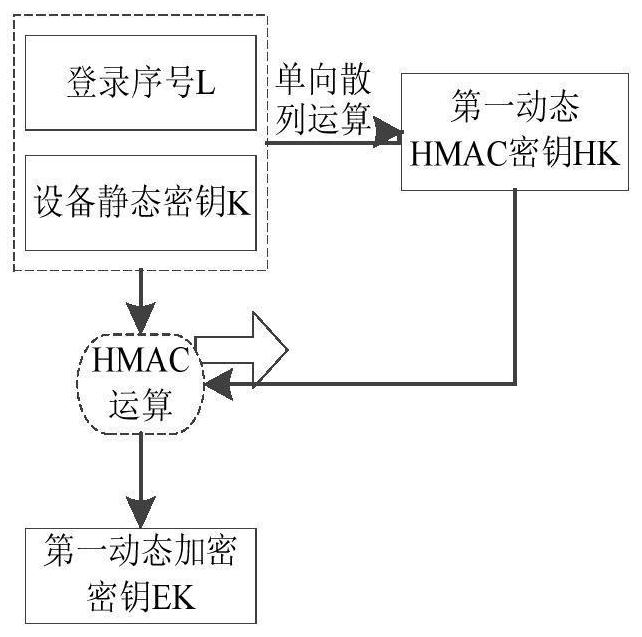
[0061] The IoT device performs a one-way hash operation on the static key K and the login serial number L of the IoT device. The one-way hash operation includes the MD5 one-way hash algorithm and the SHA one-way hash algorithm to obtain the first Dynamic HMAC key HK, the one-way hash algorithm is not limited to MD5 one-way hash algorithm and SHA one-way hash algorithm, and can also include other one-way hash algorithms;
[0062] Utilize the dynamic HMAC key as the key of the HMAC algorithm to perform the HMAC operation on the static key K and the login serial number L of the IoT device, and use the operation result as the first dynamic encryption key EK;
[0063] The first dynamic key includes: the first ...
Embodiment 2
[0084] The present application provides another embodiment of a method for dynamically encrypting an IoT device based on a login serial number, and the method includes:
[0085] Step 201, the IoT device generates a first dynamic key:
[0086] The Internet of Things device performs a one-way hash operation on the static key K and the login sequence number L of the Internet of Things device. The one-way hash operation includes the MD5 one-way hash algorithm and the SHA one-way hash algorithm to obtain the first dynamic HMAC key HK, the one-way hash algorithm is not limited to MD5 one-way hash algorithm and SHA one-way hash algorithm, and can also include other one-way hash algorithms;
[0087] Utilize the dynamic HMAC key as the key of the HMAC algorithm to perform the HMAC operation on the static key K and the login serial number L of the IoT device, and use the operation result as the first dynamic encryption key EK;
[0088] The first dynamic key includes: the first dynamic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com