Multi-antenna non-trusted relay system based on limit feedback and transmission method thereof
A technology of a relay system and a transmission method, which is applied to a multi-antenna untrusted relay system based on limited feedback and its transmission field, can solve problems such as the inability to obtain complete CSI and the like
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
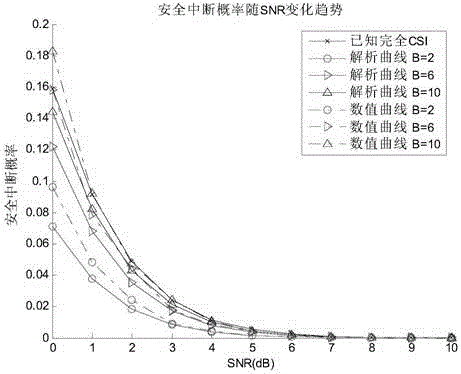
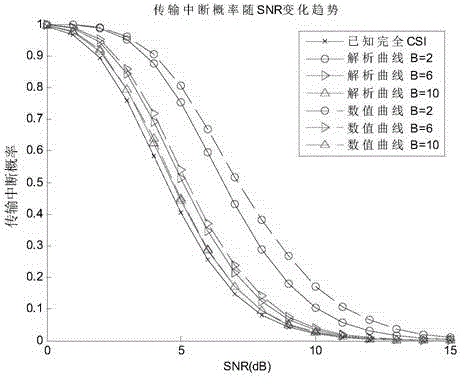
[0032] like figure 1 As shown, the structure of the communication system includes a sending signal source S node, an untrusted relay R node and a legitimate receiving D node. The numbers of antennas of S node, R node and D node are M, 1, M respectively, and R node is an amplify and forward (AF) untrusted relay. The system uses limited feedback technology to obtain the channel state information CSI of the S-R channel, and estimates the channel state information CSI of the R-D channel through the training signal. There is no training estimation error and there is channel reciprocity.
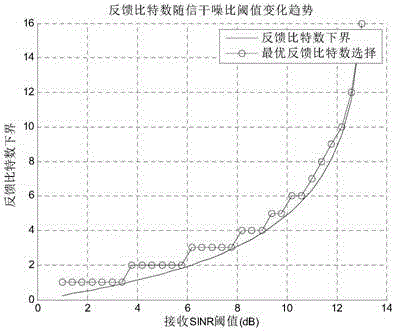
[0033] The embodiment of the invention discloses a transmission method for self-adaptive selection of the number of feedback bits, and a complete communication process is completed within two time slots. In the first time slot, the S node sends the signal to be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com