Privacy protection display implementation method based on visual passwords
A privacy protection and visual password technology, applied in the field of security display, can solve the problems of high cost, large radiation, and large health damage, and achieve the effect of low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
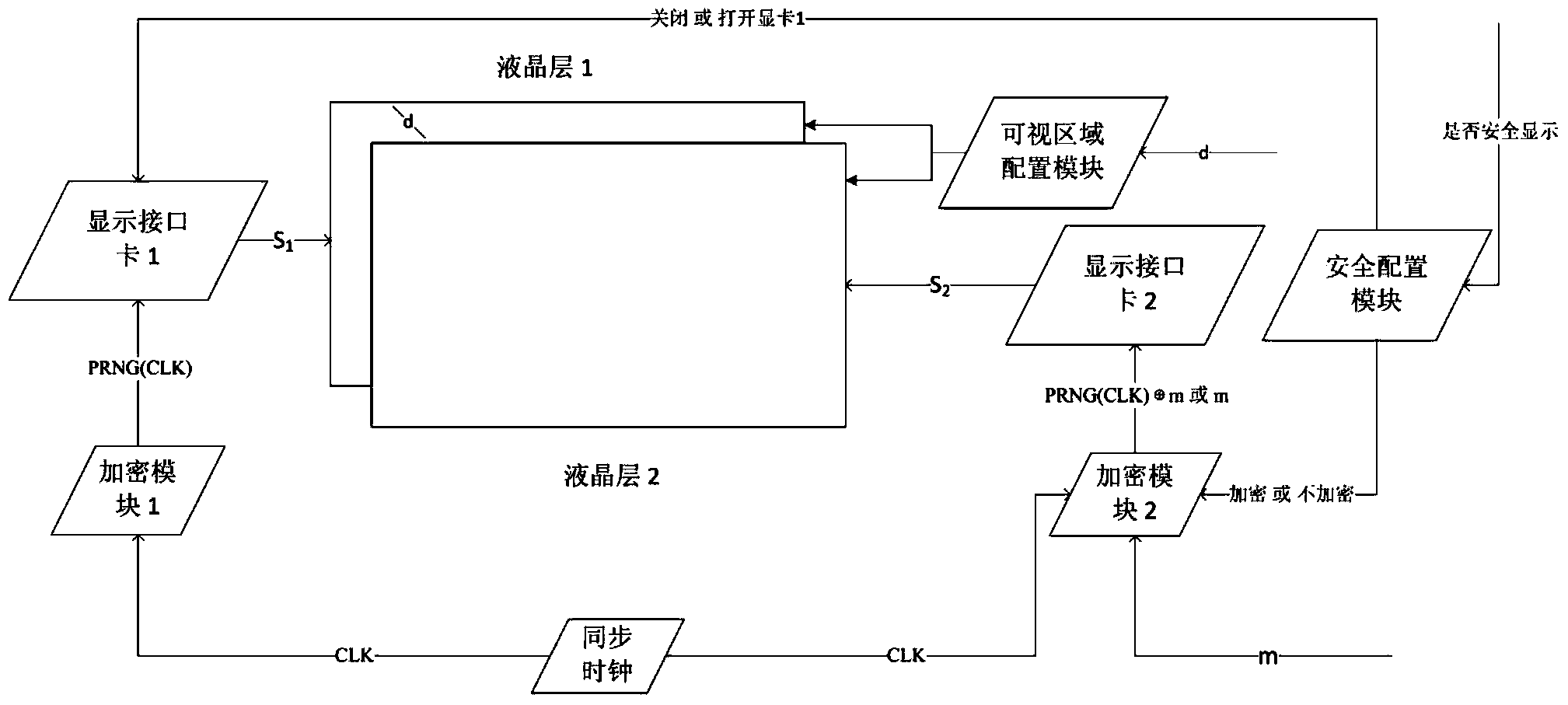
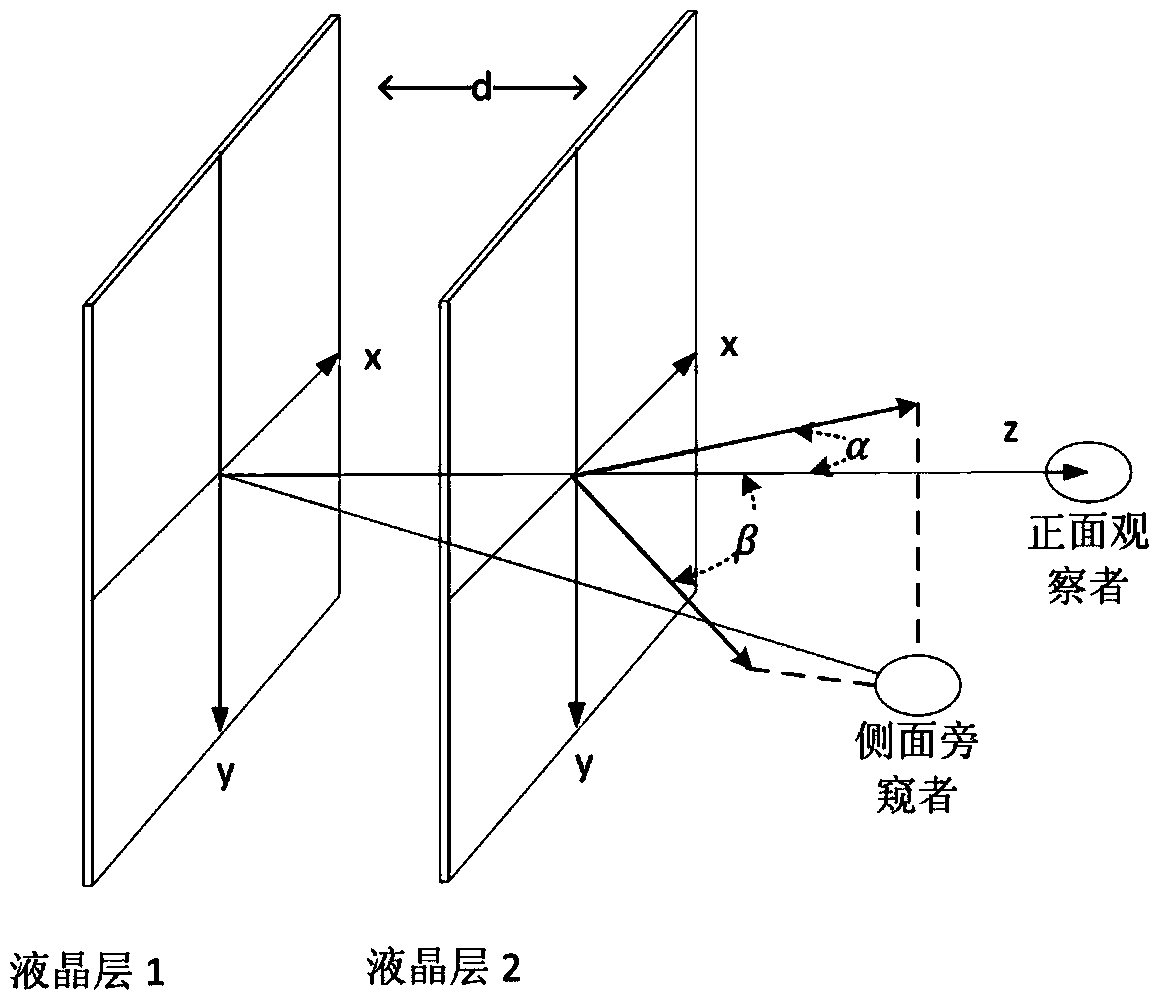
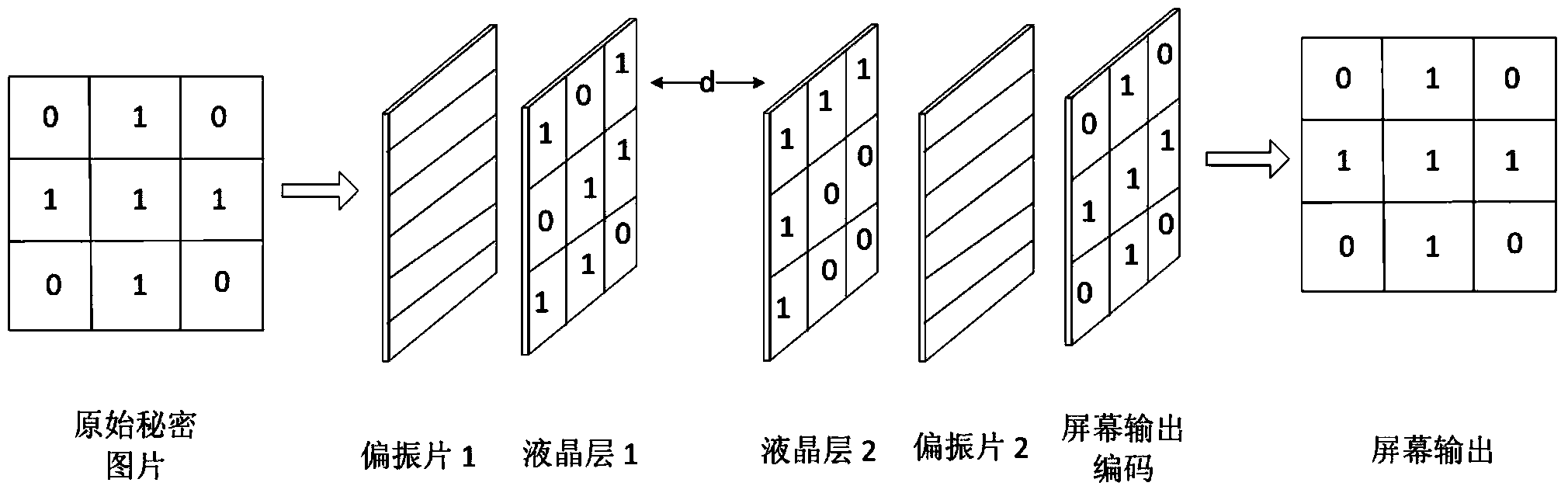
[0043] Example 1: Using the stream cipher algorithm Rabbit as figure 1 The standard RGB screen safety display of the parameter d=2 of PRNG in PRNG, wherein the arrangement of RGB sub-pixel is as follows Figure 5 As shown, the screen size is 1280×1024, and the pixel color is true color 24 bits. Will figure 1 The refresh rate of the screens in the two display interface cards is set to 60Hz. figure 1 In the security configuration module, select the private browsing mode, through figure 1 The middle viewing area configuration module sets the distance between the two liquid crystal layers to be 2 pixels side length. In this working mode figure 1 The specific workflow of each module is as follows:
[0044] (1) A 64-bit random initialization vector IV is preset between encryption module 1 and encryption module 2;
[0045] (2) The synchronous clock module sends a 72-bit clock signal CLK (hour: minute: second: millisecond) to the encryption module 1 and the encryption module 2; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com