Multimode integration core network user traffic application identification method easy to expand
A technology for application identification and user traffic, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as insufficient, achieve the effect of simple processing logic, improve identification processing efficiency, and improve effectiveness and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The specific implementation of the present invention will be described below according to the drawings and embodiments.
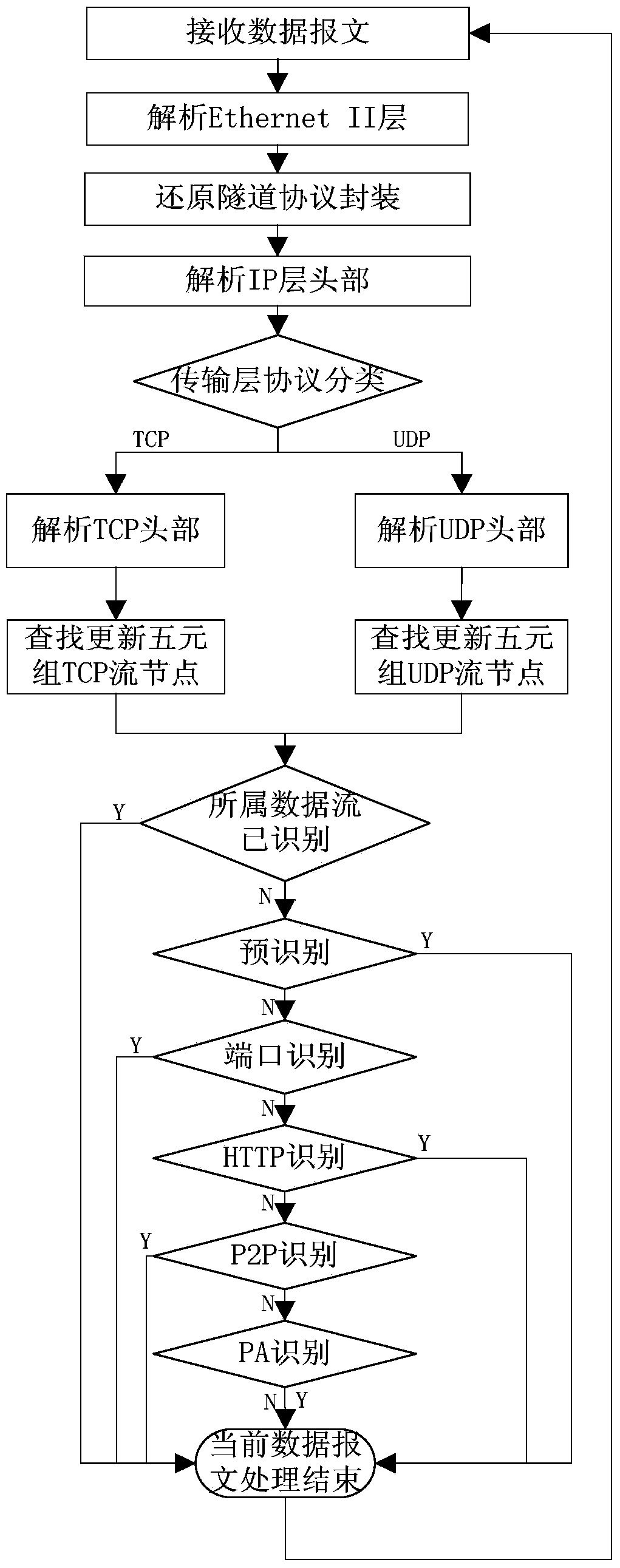
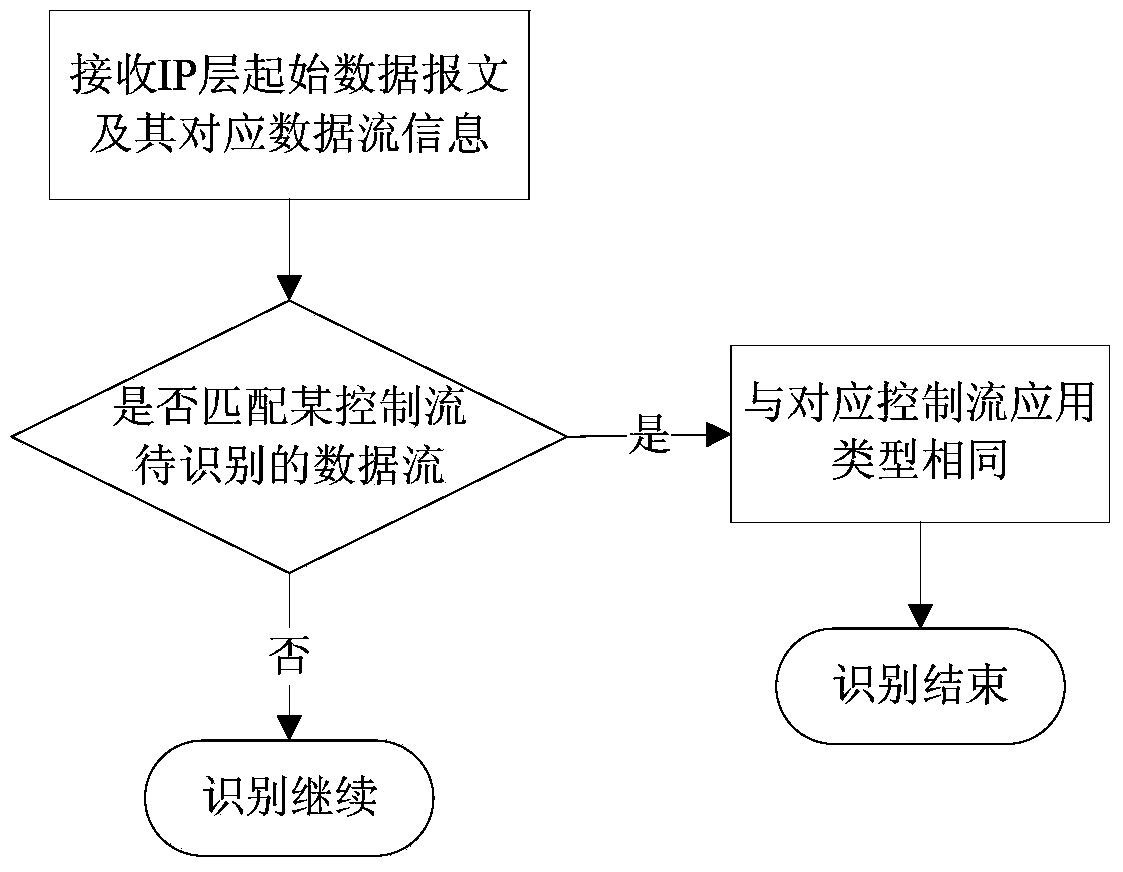
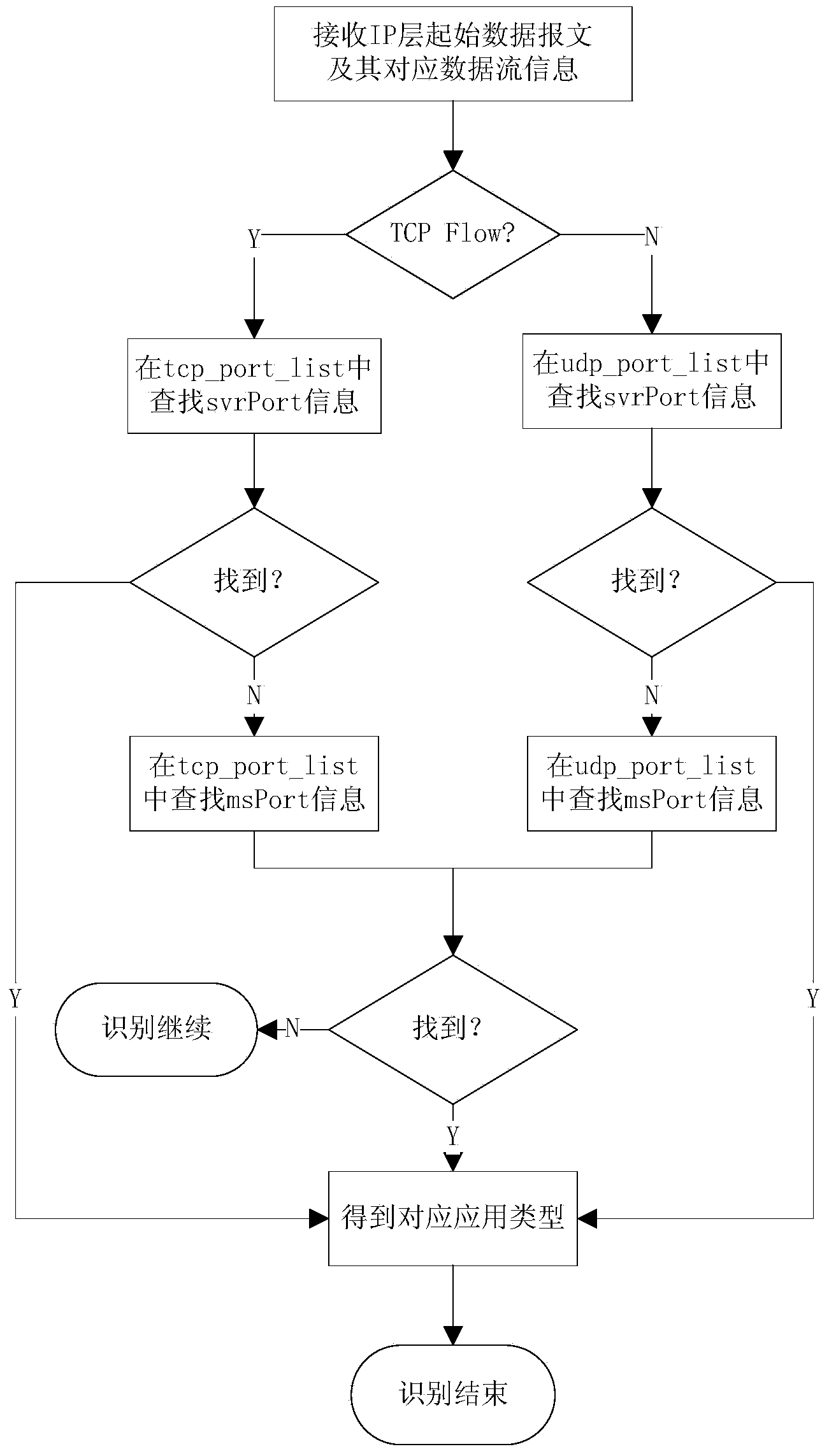
[0047] The basic principle of the embodiment of the present invention is: pay attention to the flow determined by the source IP address, destination IP address, source port, destination port and application layer protocol (TCP / UDP) quintuple, and each data message must belong to and only belong to One stream, and one stream is generated by the same application. According to the layered feature of the network protocol, the embodiment of the present invention naturally uses a layered model. That is, hierarchical processing is performed on the network layer, transport layer, and application layer. After parsing the application layer data, find the flow node to which the service data packet belongs according to the quintuple composed of the obtained source IP address, destination IP address, source port, destination port and application layer protocol (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com