Binary oriented hybrid fuzzing method
A fuzzing and binary technology, applied in the computer field, can solve problems such as inability to analyze binary programs, achieve high test coverage, enhance usability, and eliminate blindness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
test Embodiment 400
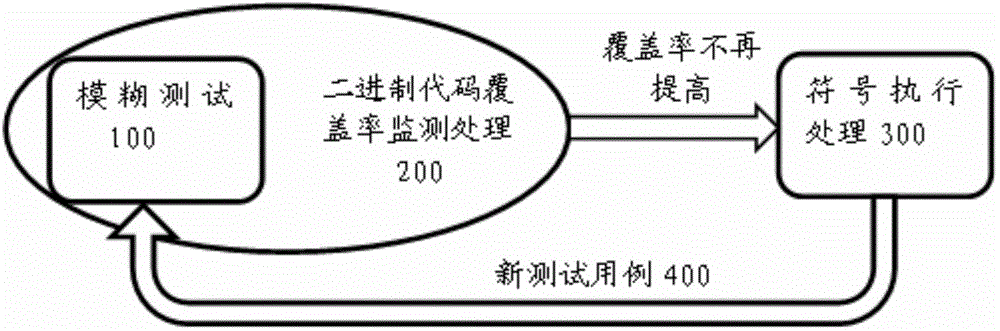
[0033] Adopt fuzz test 100 as front-end processing, wherein utilize test case to drive the execution of the program under test (fuzz test 100 can utilize the test case that the policy generation based on mutation initially drives the execution of the program under test, namely, fuzz test 100 is received Before the new test case 400 fed back from the symbolic execution process 300, use the test case generated based on the mutation strategy to drive the execution of the program under test);
[0034] Using the binary code coverage monitoring process 200 as the middle layer processing, wherein during the execution of the tested program, recording the basic blocks covered by the tested program, thereby calculating the coverage rate of the fuzz test 100;
[0035] When the coverage rate of the calculated fuzz test 100 no longer improves, execute the symbolic execution process 300 as the backend process, wherein the symbolic execution process 300 generates a new test case 400 covering ...
specific example
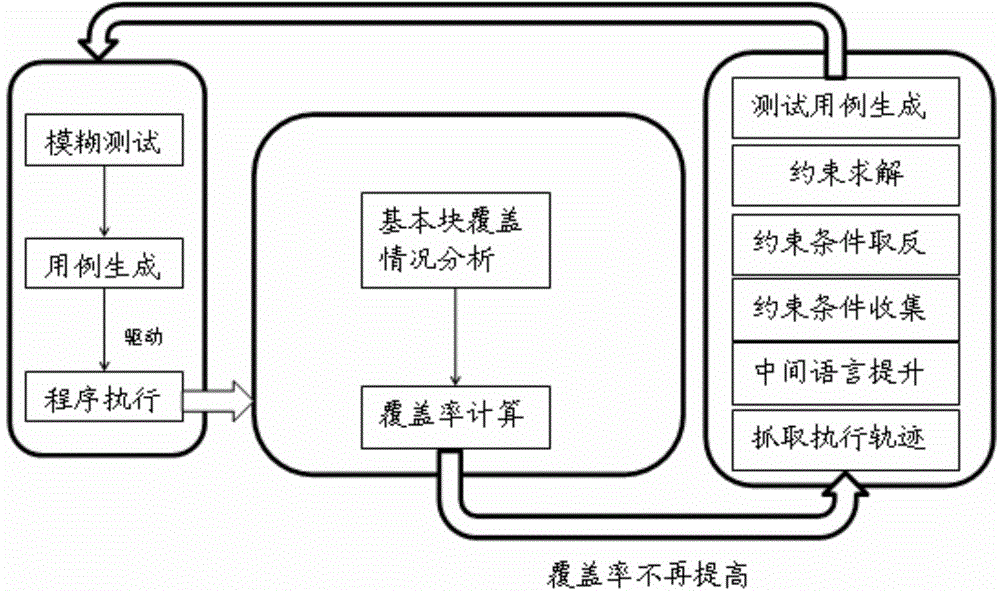
[0045] Perform security analysis on the commonly used binary program ls (display directory content in list form) under Linux system. The external input of the target program ls is composed of a series of option parameters and the target path, and the test cases are randomly generated by the mutation-based test case generation strategy. Use the generated test cases to drive the target program ls to run.
[0046] The ls program starts to run, and at the same time starts the binary code coverage monitoring module. After each test case is executed, analyze the basic blocks covered by the use case, add the test case to all previously executed test cases to form a new test case set, and then calculate the code coverage of the entire test case set ( It is also possible to count the number of distinct basic blocks covered by the set of use cases).
[0047] When the binary code coverage monitoring module detects that the newly executed test cases cannot improve the coverage of the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com