Portable transparent data safety protection terminal oriented to mobile applications
A portable terminal and mobile application technology, applied in the field of information security, can solve problems such as data leakage, and achieve the effect of solving the limitation of computing resources and energy consumption, high-strength data encryption and security protection, and high-speed and high-strength encryption and decryption computing capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the accompanying drawings.
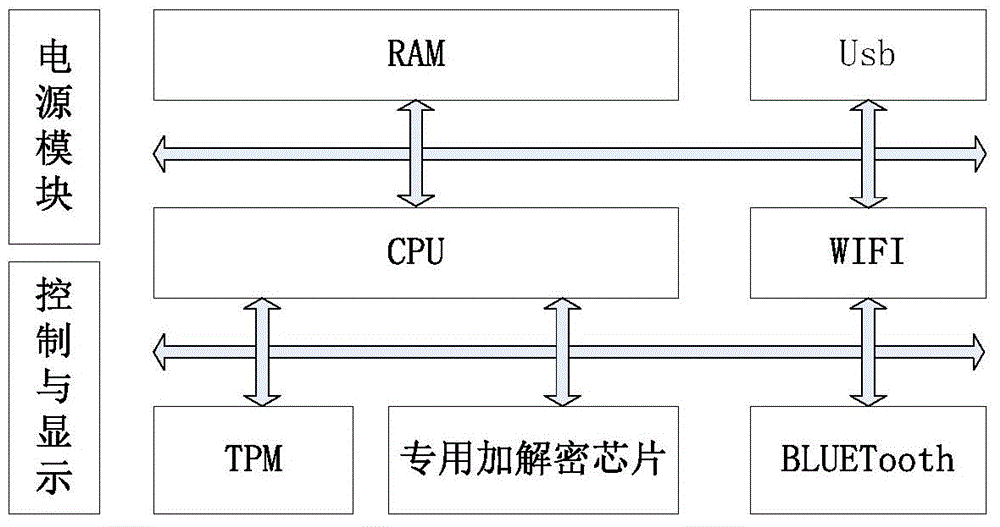
[0050] The specific implementation of the present invention is divided into two parts, one part is hardware equipment, and the other part is software, wherein the hardware architecture of the present invention is as follows: figure 1 shown, including:
[0051] 1. The main control chip is an embedded ARM series chip to meet the needs of the project function for computing power.
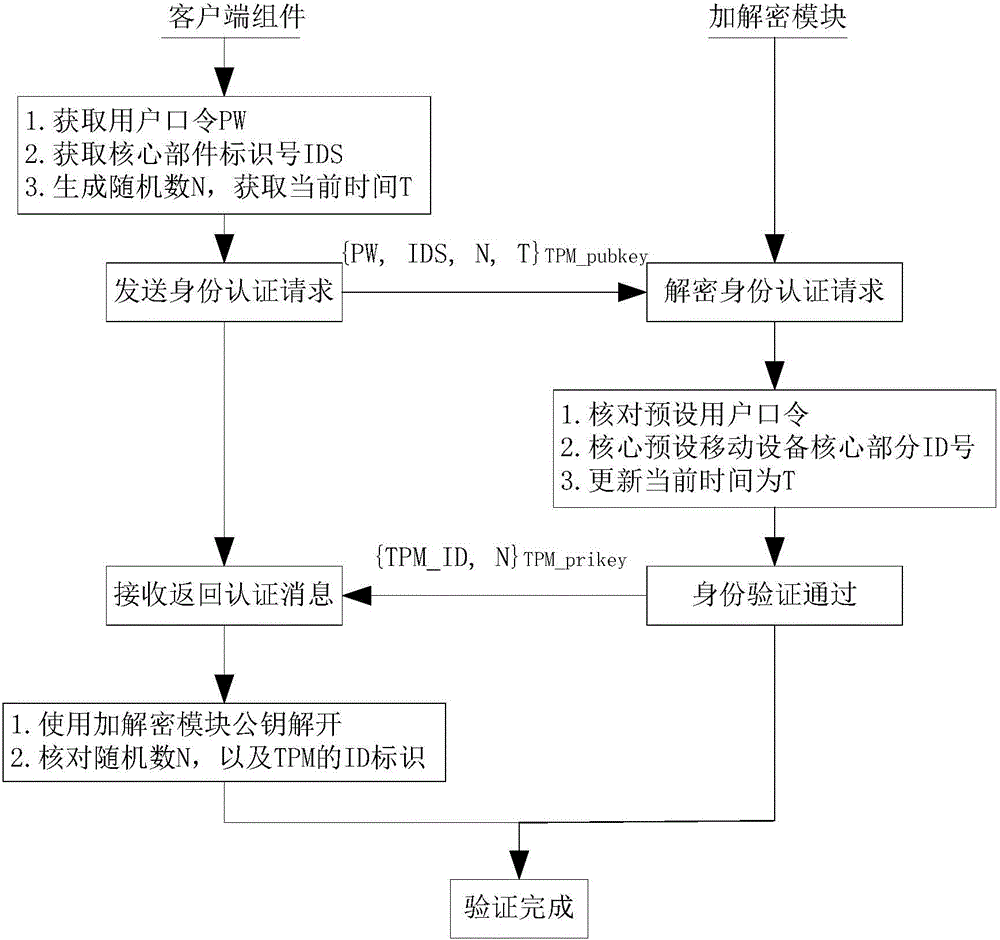
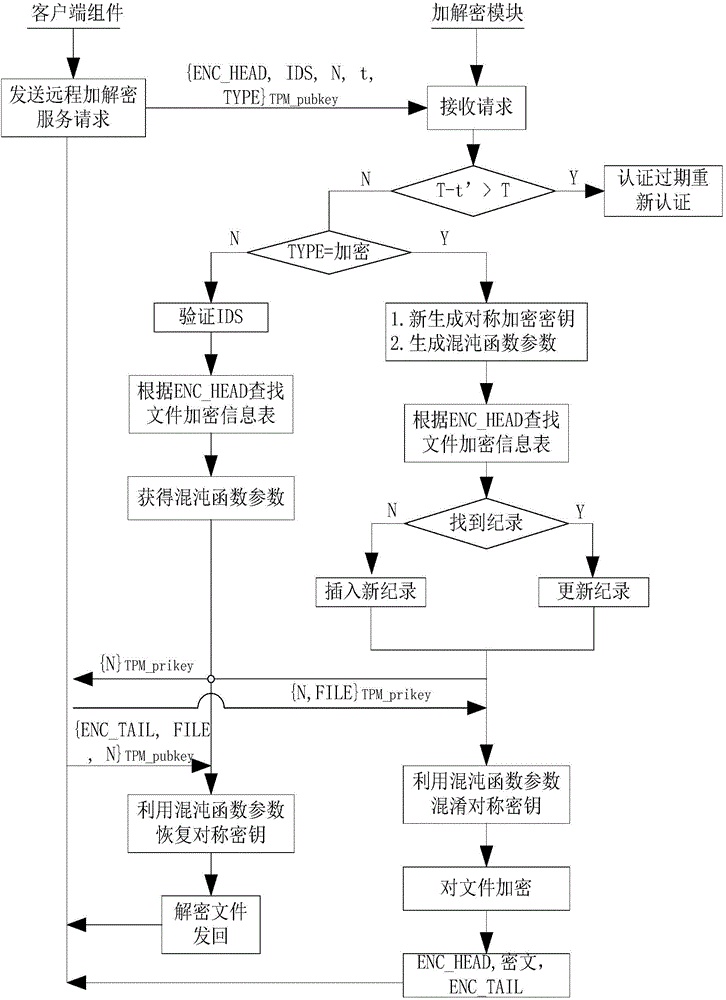
[0052] 2. The trusted chip TPM and the encryption chip Enc, these two parts of the chip realize the trusted reasoning support of the present invention, wherein the TPM uses a dedicated chip, and the memory key includes the corresponding encryption and decryption calculation capabilities, which are controlled by the special chip circuit To protect against illegal theft, the ENC chip is a general-purpose encryption and decryption chip that provides various types of encryption calculation support...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com