Method and system for authenticating remote user based on camera
An identity verification and remote user technology, applied in the field of computer identity verification, can solve problems such as inability to judge whether the surface information of the ID card image is consistent with the information in the chip, poor customer experience, and inability to distinguish the authenticity of the customer ID card.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
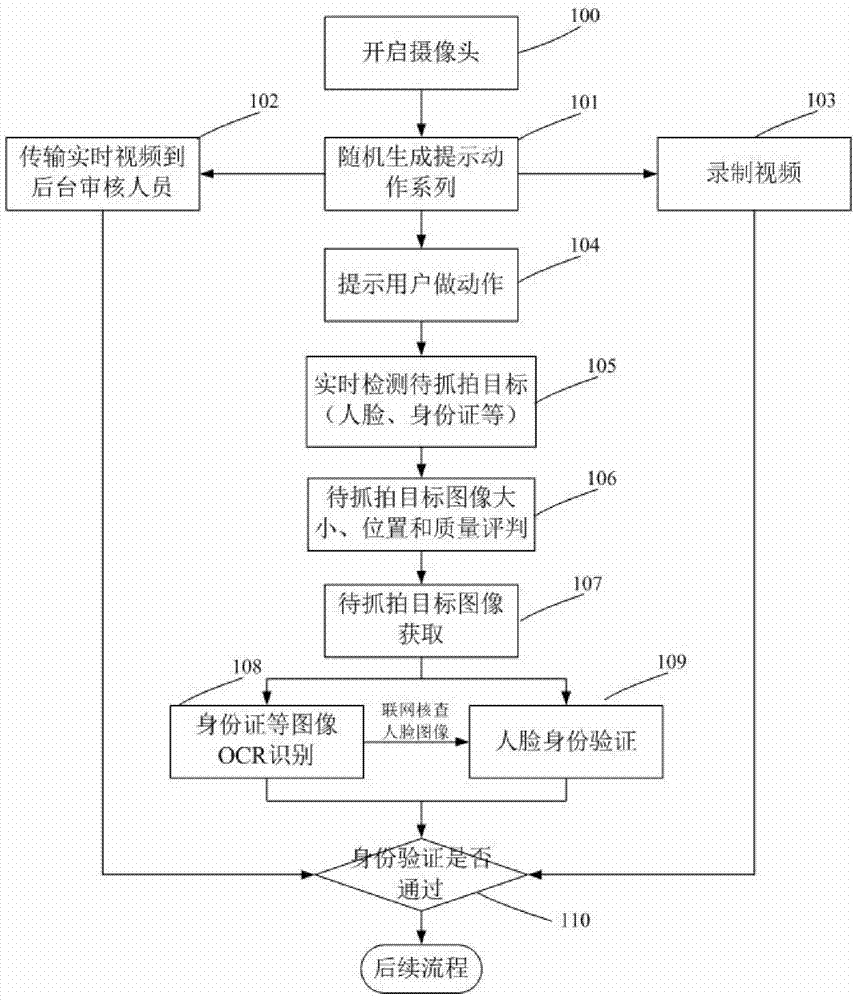
[0055] figure 2 It is a schematic flowchart of a method for realizing remote user identity verification based on a terminal device camera proposed by the present invention. Combine now figure 2 , an example of a method for realizing remote user identity verification based on a terminal device camera proposed by the present invention is given.
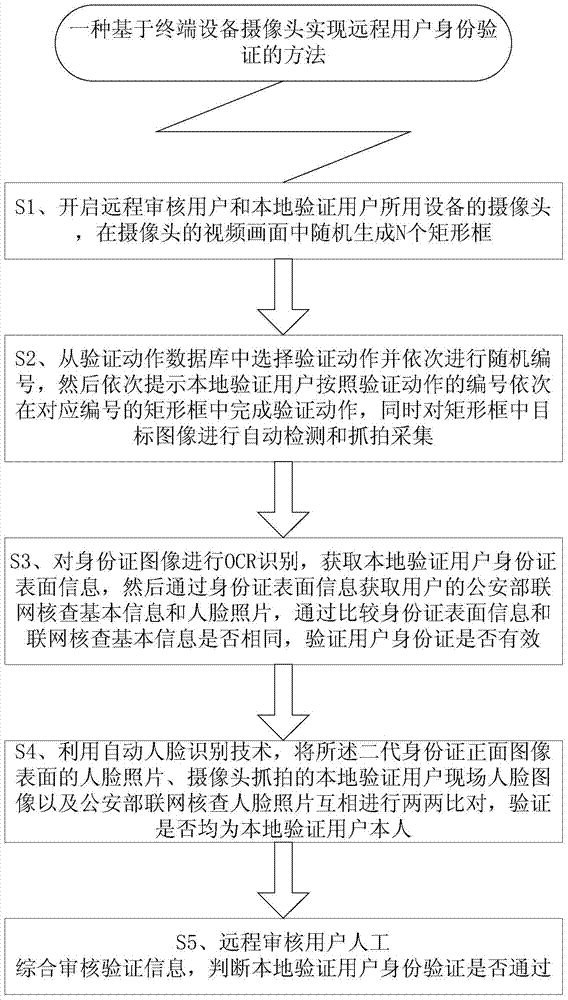
[0056] A method for implementing remote user identity verification based on a terminal device camera proposed in Embodiment 1 includes the following steps:
[0057] Step 100: Turn on the camera;
[0058] Turn on the camera of the device used by the remote authentication user, such as a mobile phone camera. The camera can be various commonly used cameras, such as a USB camera, a built-in camera of a notebook computer, a built-in camera of a mobile phone, and the like.
[0059] Step 101: Randomly generate a prompt action series;
[0060] Some actions are pre-designed, including but not limited to: requiring the remote verification ...
Embodiment 2
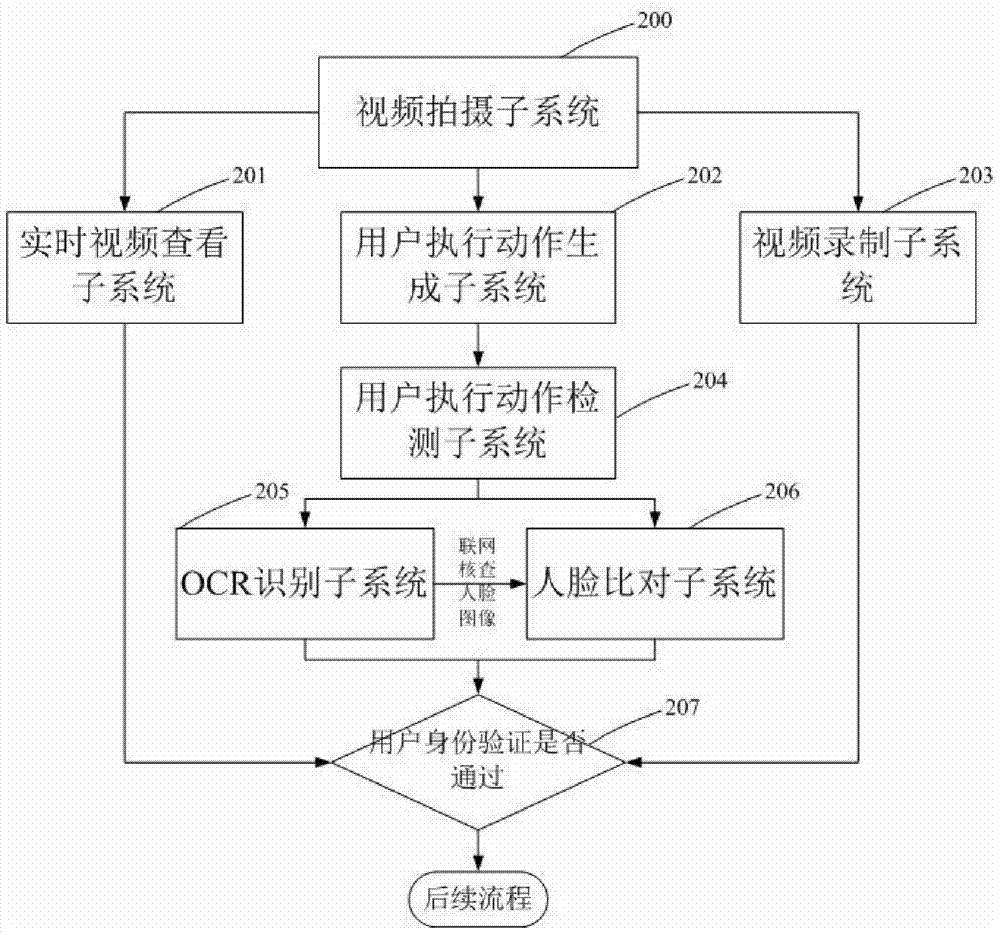
[0083] image 3 It is a block diagram of a system for realizing remote user identity verification based on a terminal device camera proposed by the present invention. Combine now image 3 , an example of a system for realizing remote user identity verification based on a terminal device camera proposed by the present invention is given.
[0084] A system for realizing remote user identity verification based on a terminal device camera proposed by the present invention includes:
[0085] Subsystem 200: video capture subsystem
[0086] Capture user operation video by calling the camera. The camera may be various commonly used cameras, such as a USB camera, a built-in camera of a notebook computer, a built-in camera of a mobile phone, and the like.
[0087] Subsystem 201: Real-time video viewing subsystem
[0088] It allows the review staff to view the user's operation video in real time. Real-time video supports common transmission network transmission, such as wired broad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com