Safety authentication method based on phase retrieval and sparse double random phase encryption
A dual random phase and phase recovery technology, applied in the field of information security, can solve problems to be developed and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
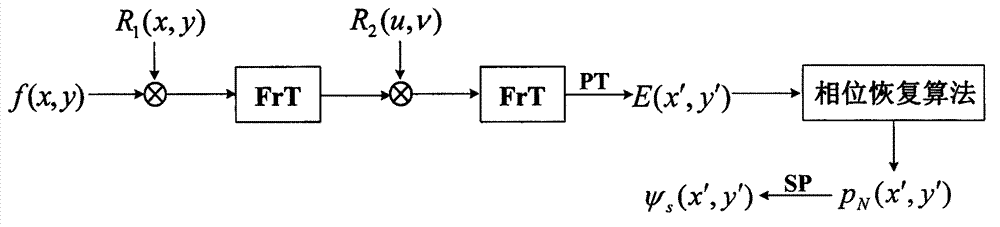
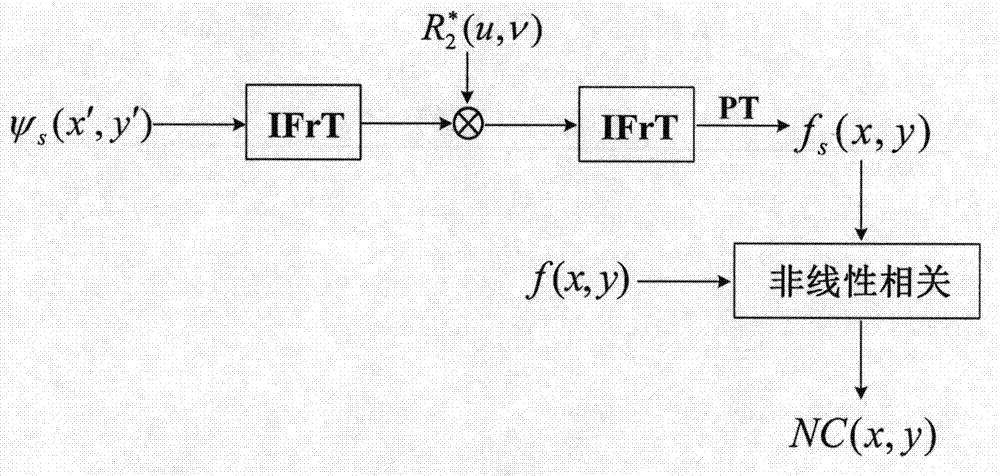
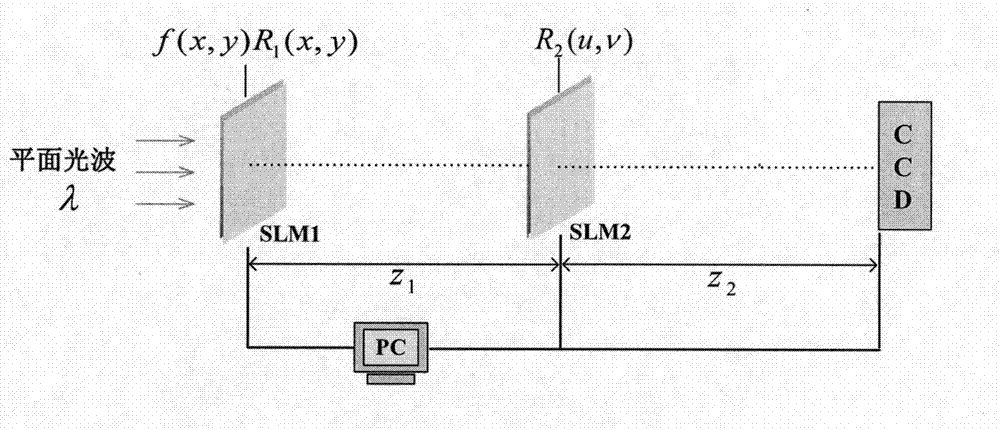
[0046] The present invention is described in detail below in conjunction with embodiment and with reference to accompanying drawing: the encryption process of the method for the present invention can pass through image 3 The optoelectronic hybrid system shown is realized. A spatial light modulator (spatial light modulator, SLM) has the ability to modulate complex amplitude signals. The encryption process is divided into two steps:
[0047] (1) During the encryption process, the computer-controlled SLM1 and SLM2 are used to display the information f(x, y)×R respectively 1 (x, y) and R 2 (u, v), under the illumination of a plane wave of unit amplitude with wavelength λ, f(x, y) and the encryption key R 1 The product of (x, y) is once the distance is z 1 The Fresnel transform, the transformed signal is passed through R 2 After (u, v) modulation, make another distance as z 2 The Fresnel transform of the output signal is recorded by the light intensity detector CCD placed on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com