Smart grid malicious data injection attack and detection method
A malicious data, injection attack technology, applied in the field of smart grid data information security, can solve problems such as no detection algorithm proposed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
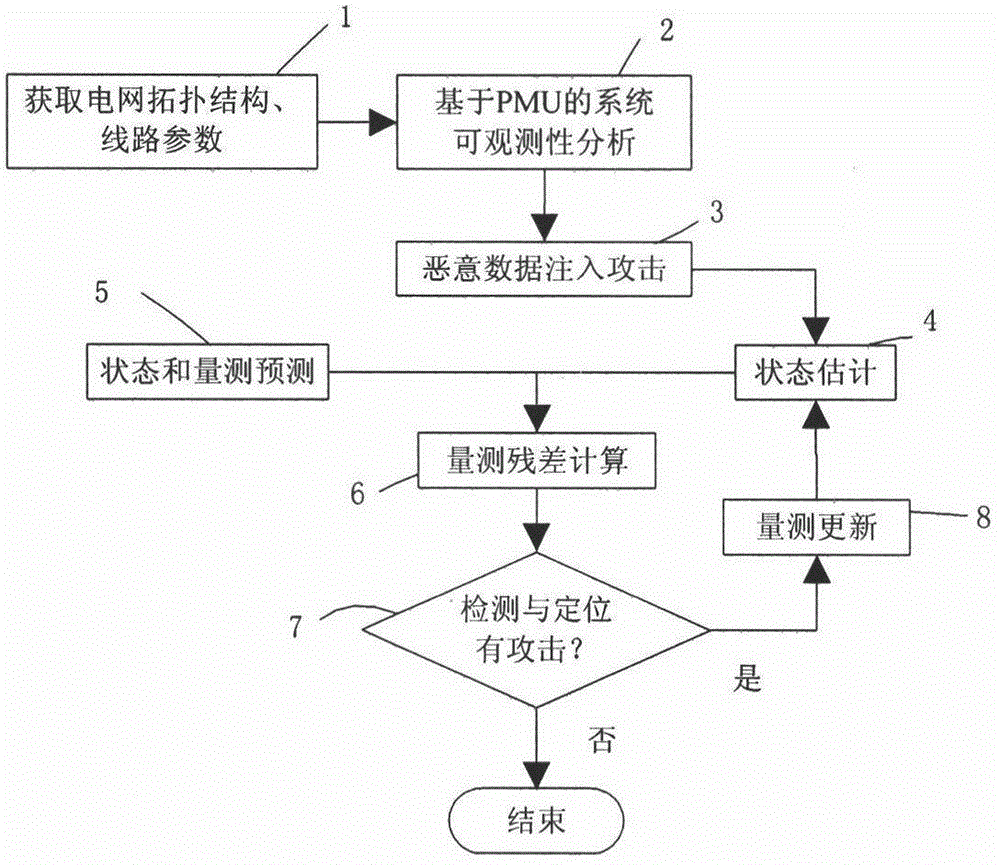
[0055] In order to make the content, effects and key points of the present invention clearer, the present invention will be further elaborated below in conjunction with the accompanying drawings. A smart grid malicious data injection attack and detection method, its technical implementation scheme such as flow figure 1 As shown, it includes the following steps:
[0056] Step 1: Obtain the grid topology and line parameters; the topology of the grid includes the connection status between lines, and the opening and closing of switches; the line parameters include line admittance and ground susceptance.
[0057] Step 2: Based on the PMU system observability analysis, determine the minimum PMU measurement configuration required for system observability through the system observability analysis method of the minimum number of PMU configurations; where, the PMU measurement includes the voltage at the PMU configuration node magnitude and the branch current vectors adjacent to it.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com