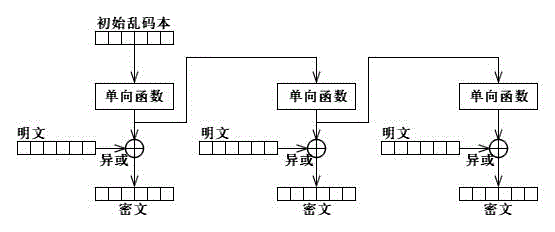
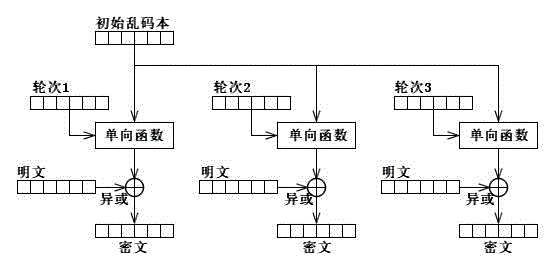
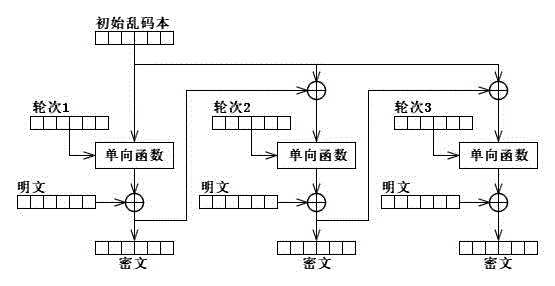
Limited gibberish text one-way conversion method and encryption/decryption application thereof
A one-way transformation and codebook technology, applied to encryption devices with shift registers/memory, key distribution, can solve the problems of encryption and decryption, unable to directly apply stream data, and the encryption overhead is amazing, and achieve the effect of improving the speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0216]The following function EncryptOfGLOWT is the C++ sample code implementation of the GLOWT encryption method with known plaintext and plaintext length. The function EncryptOfGLOWT is defined as follows:
[0217]
[0218]
[0219] The input of the present embodiment is: plaintext szPlain and plaintext length lenPlain, and the buffer size lenGarbled of the buffer szGarbled that is used to output initial garbled book and initial garbled book, the buffer szCipher that is used to output ciphertext and ciphertext buffer Size lenCipher. The output after the function execution is completed is the failed and successful result returned by the function execution, as well as the initial garbled book and the length lenGarbled of the initial garbled book stored in the buffer szGarbled of the initial garbled book when the function is executed successfully, and the buffer szCipher of the ciphertext The length of the ciphertext and the ciphertext in lenCipher. The initial garbled b...
Embodiment 2
[0247] The present embodiment is the decryption method corresponding to the function EncryptOfGLOWT that realizes the garbled book limited one-way transformation encryption method in embodiment 1, and this decryption method is realized by the function DecryptOfGLOWT of C++ code, and example is as follows:
[0248]
[0249]
[0250] The input of this embodiment is: the ciphertext szCipher and the ciphertext length lenCipher, the initial garbled book szGarbled and the size lenGarbled of the initial garbled book, and the buffer szPlain for outputting plaintext and the size lenPlain of the plaintext buffer. The output after the function execution is completed is the failure and success results returned by the function execution, as well as the plaintext and the plaintext length lenPlain stored in the plaintext buffer szPlain when the function execution is successful.
[0251] The above-mentioned process of this embodiment is mainly as follows: first decrypt the initial garble...
Embodiment 3
[0254] In the garbled code book limited one-way transformation encryption method realized by the function EncryptOfGLOWT in the foregoing embodiment 1, the one-way transformation transformation limit value NR and the length lenPlain of the plaintext are fixed, so the length of the required garbled code book can be directly calculated. For stream data encryption, the length of the plaintext is often dynamic, so it is impossible to calculate the length of the required garbled text according to the length of the plaintext. The function StreamGLOWT::EncryptSend disclosed in this embodiment is an embodiment of the present invention in the application of stream data encryption. The function StreamGLOWT::EncryptSend is implemented by C++ code, where StreamGLOWT is a C++ class, and EncryptSend is a method of class StreamGLOWT. The class StreamGLOWT is used for data encrypted communication, and it constructs two data communication channels, namely: m_sockGarbled and m_sockContent. Amo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com