Secret key exchange or public key password encryption optimization method and system based on Meisson number
A key exchange and public key cryptography technology, which is applied in the field of key exchange based on Mersenne number or public key cryptography optimization, can solve problems such as unfavorable hardware implementation, complex circuits, complex algorithms, etc., to reduce time complexity and simplify Effect of circuit design and power consumption reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0115] A kind of key exchange or public key cryptography optimization method based on Mersenne number, this method comprises the combination of following implementation modes:
[0116] In key exchange or public key cryptography-related calculations, the Elgamal algorithm is selected in this embodiment, and the DHM algorithm may also be selected.
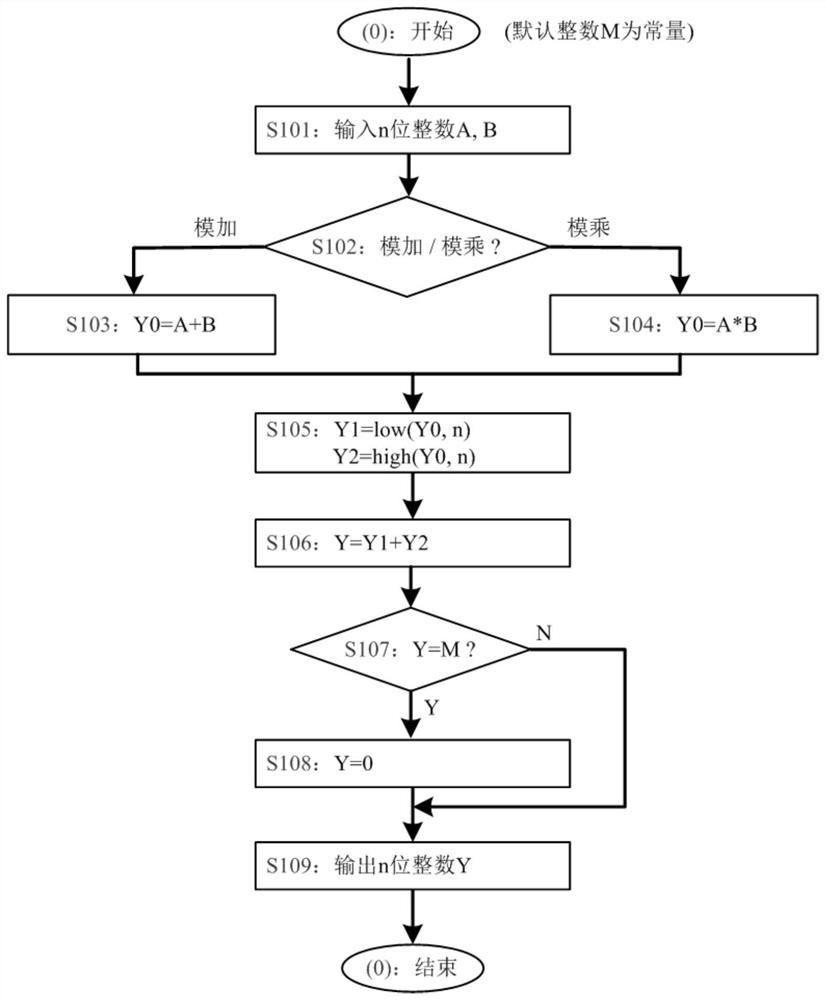
[0117] In the adopted Elgamal algorithm, choose a Mersenne prime M=2 n -1 is used as the modulus of modulo operation mod, wherein n is a positive integer and can make M a prime number, such as n=1279;
[0118] In the process of corresponding modular addition, modular multiplication, and modular exponentiation, the original modulus operation mod is replaced with a specific first modulo operation mod1 without division, wherein the expression of the first modulo operation mod1 is as follows:
[0119] Modular addition: Y=A+B mod1 M=A+B mod(2 n -1),
[0120] Modular multiplication: Y=A*B mod1 M=A*B mod(2 n -1),
[0121] Modular power...
Embodiment 2
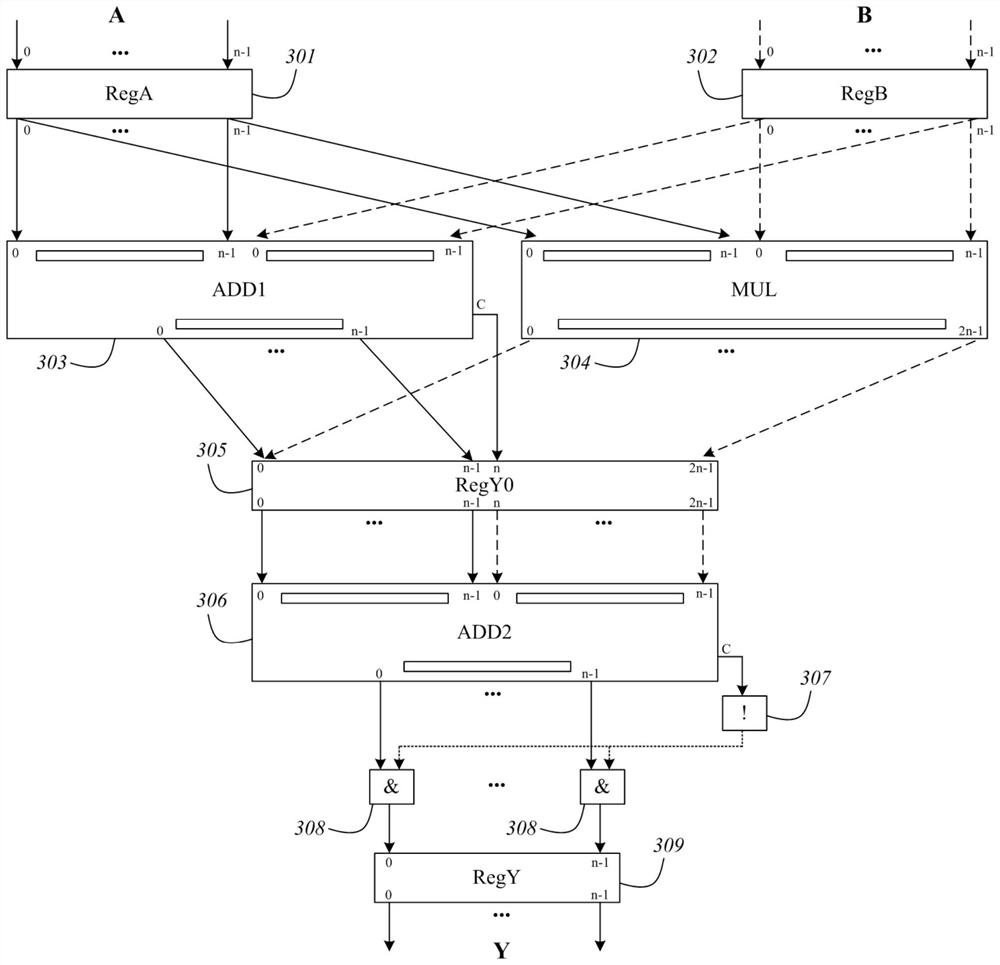
[0133] A system for implementing a Mersenne number-based key exchange or public key encryption optimization method includes one or more fast modulo operation logic circuit components C1, which can support the first modulo operation mod1;
[0134] Logic circuit assembly C1 includes the following devices (as attached image 3 shown):
[0135] n-bit register RegA (301), used for temporarily storing the input number A;
[0136] n-bit register RegB (302), used for temporarily storing the input number B;
[0137] n-bit adder ADD1 (303), used for adding two numbers, outputting an n-bit integer and a carry flag C;
[0138] n-bit multiplier MUL (304), used for multiplying two numbers and outputting 2n-bit integers;
[0139] 2n-bit register RegY0 (305), used for temporary storage of intermediate data;
[0140] N-bit adder ADD2 (306), is used for finishing fast modulus calculation, outputs n-bit integer and carry sign C;
[0141] Logic gate circuit, including n AND gates (308), 1 NO...
Embodiment 3
[0144] A method for optimizing key exchange or public key cryptography based on Mersenne numbers, comprising a combination of the following implementations:
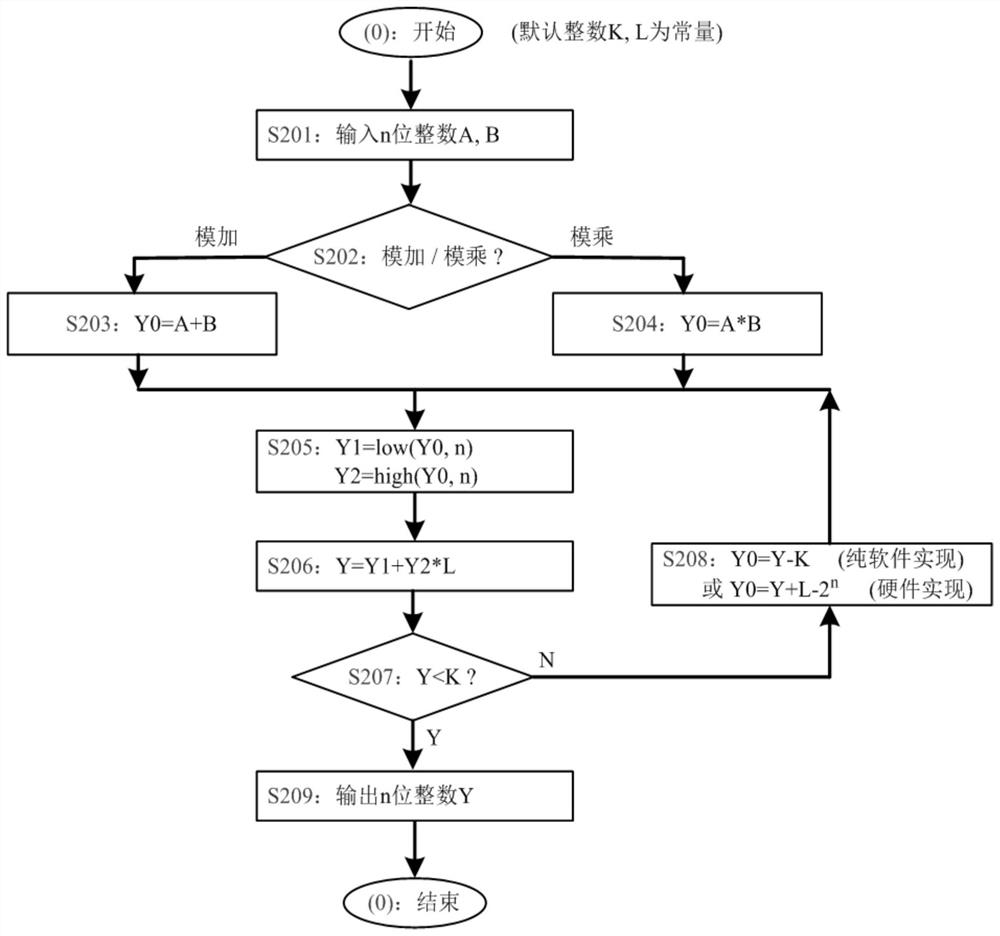
[0145] In the key exchange or public key cryptographic calculation, this embodiment chooses to use the RSA algorithm;
[0146] In the adopted RSA algorithm, the product K of two prime numbers is constructed, and exactly K=2 n -L is used as the modulus of the modulus operation mod, where n is a positive integer, L is a small positive integer, L6 = 64;
[0147] In the process of corresponding modular addition, modular multiplication, and modular exponentiation, the original modulo operation mod is replaced with a specific fast modulo operation without division, the second modulo operation mod2, wherein the second modulo operation mod2 operation The expression is as follows:
[0148] Modular addition: Y=A+B mod2 K=A+B mod(2 n -L),
[0149] Modular multiplication: Y=A*B mod2 K=A*B mod(2 n -L),
[0150] Modular power: Y...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com