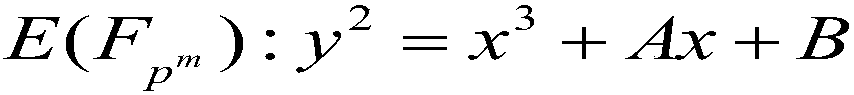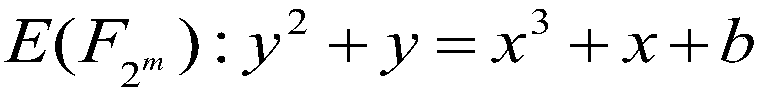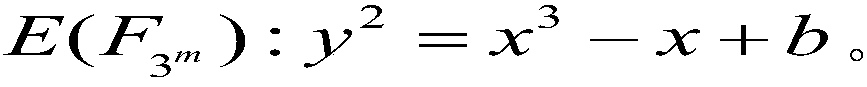A calculation method for tate bilinear pairing against error attack in ternary field
A bilinear pairing and error attack technology, applied in the field of public key cryptography, can solve problems such as low computing efficiency and inability to completely resist error attacks, and achieve the effects of fast and secure computing, less time cost, and resistance to error attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] The following describes the principle of the Tate bilinear pair calculation method against error attacks in the ternary domain. Firstly, the proof of the correctness of the operation results of the Tate bilinear pairing calculation method against error attacks in the ternary field is given when the number of cycles is correct:
[0079] Calculation of Rational Function f by Tate Bilinear Pairs in Primitive Ternary Field P The formula for (ψ(Q)) is as follows:
[0080] f 1 =f P (ψ(Q))=(…(((A 1 ) 3 A 2 ) 3 A 3 ) 3 ...) 3 A m
[0081] Computation of Rational Function f by Tate Bilinear Pairs Against Mistake Attacks in Ternary Domain P The formula for (ψ(Q)) is as follows:
[0082]
[0083] When the number of cycles m has not been changed, after m rounds of operations, we can get Due to finite fields The element R in satisfies the nature of the available thus deduced Therefore after the final modular exponentiation Afterwards, the factor of the ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com