Data processing method based on Huffman sheet
A data processing and data technology, applied in the field of data processing, can solve problems such as high error probability, complex code debugging, and complex code implementation, and achieve the effect of clear data structure, simple coding, and fast execution speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In the following description, numerous specific details are set forth in order to provide a thorough understanding of the present invention. However, the present invention can be implemented in many other ways different from those described here, and those skilled in the art can make similar extensions without violating the connotation of the present invention, so the present invention is not limited by the specific implementations disclosed below.
[0040] Secondly, the present invention is described in detail by means of schematic diagrams. When describing the embodiments of the present invention in detail, for convenience of explanation, the schematic diagrams are only examples, which should not limit the protection scope of the present invention.
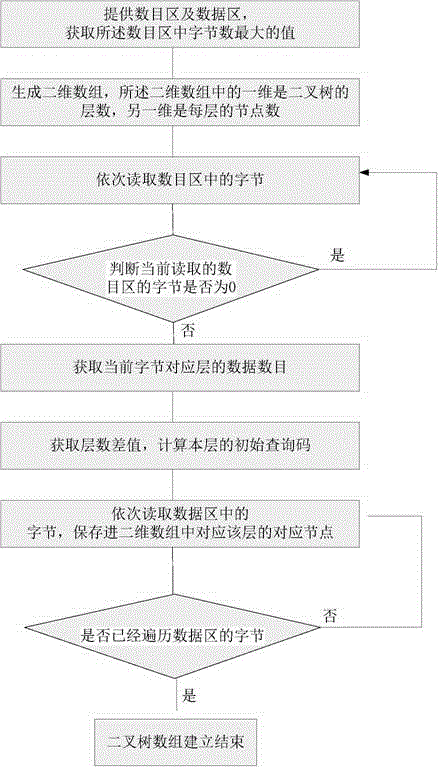
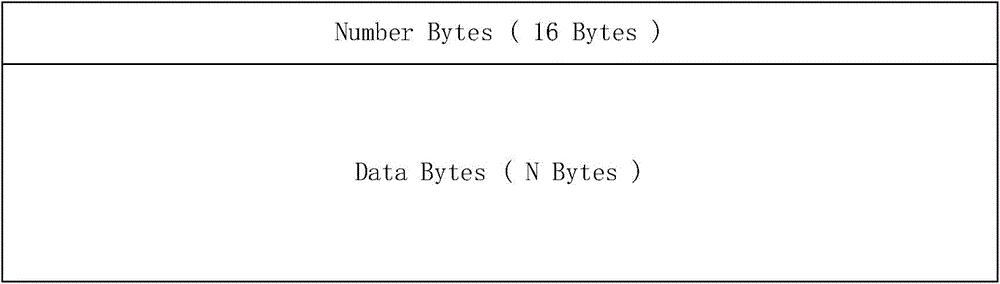
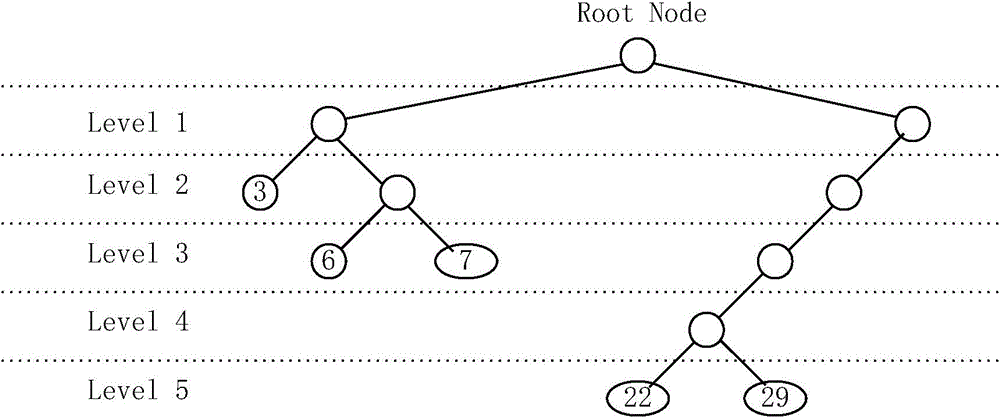
[0041] In the prior art, when JPEG is encoded and decoded, the binary tree is used to encode and decode the Huffman table, the code implementation is complicated, the probability of error is high, and the code debugging is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com