Method for detecting safety of user login interface of Android software
A login interface and security technology, applied in electrical components, transmission systems, etc., can solve problems such as wide coverage of speed and efficiency, large amount of detection tasks, user loss, etc., to achieve the effect of high detection efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in further detail below through specific embodiments and accompanying drawings.
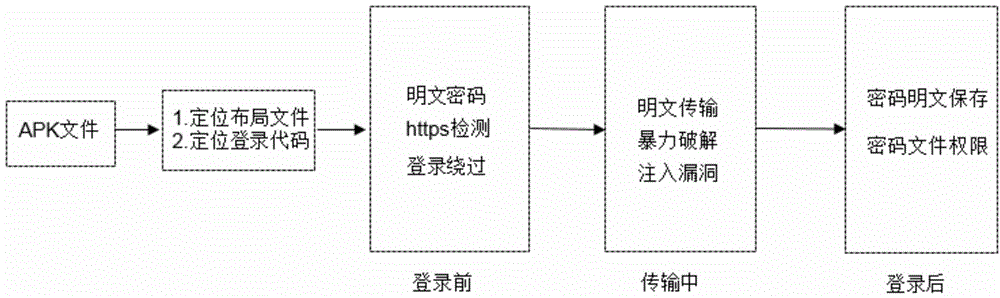
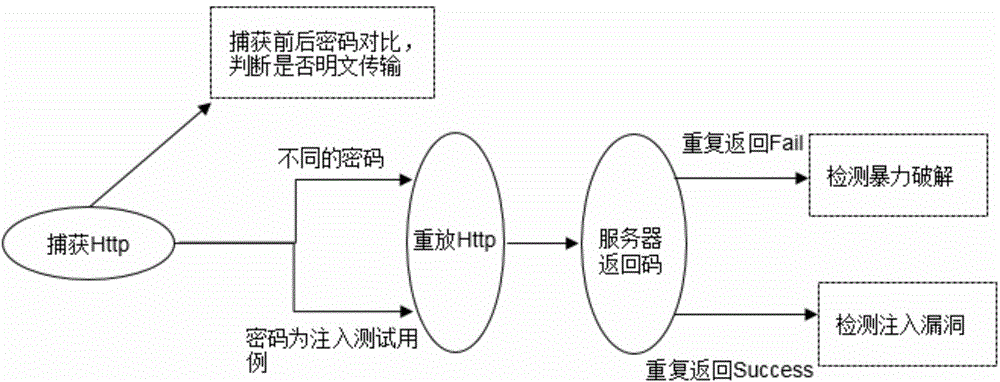
[0021] figure 1 Is the general flowchart of the method of the present invention. First analyze the apk installation package to obtain the layout files and codes related to the login page, then analyze and track the login-related code segments, and divide the entire login detection process into three stages: pre-login detection, data packet transmission detection, and post-login detection. Corresponding vulnerability detection is carried out according to the characteristics of each stage, the result of code execution is recorded, and finally, whether there is a relevant vulnerability is judged according to the execution result of each stage. Each step is described in detail below.
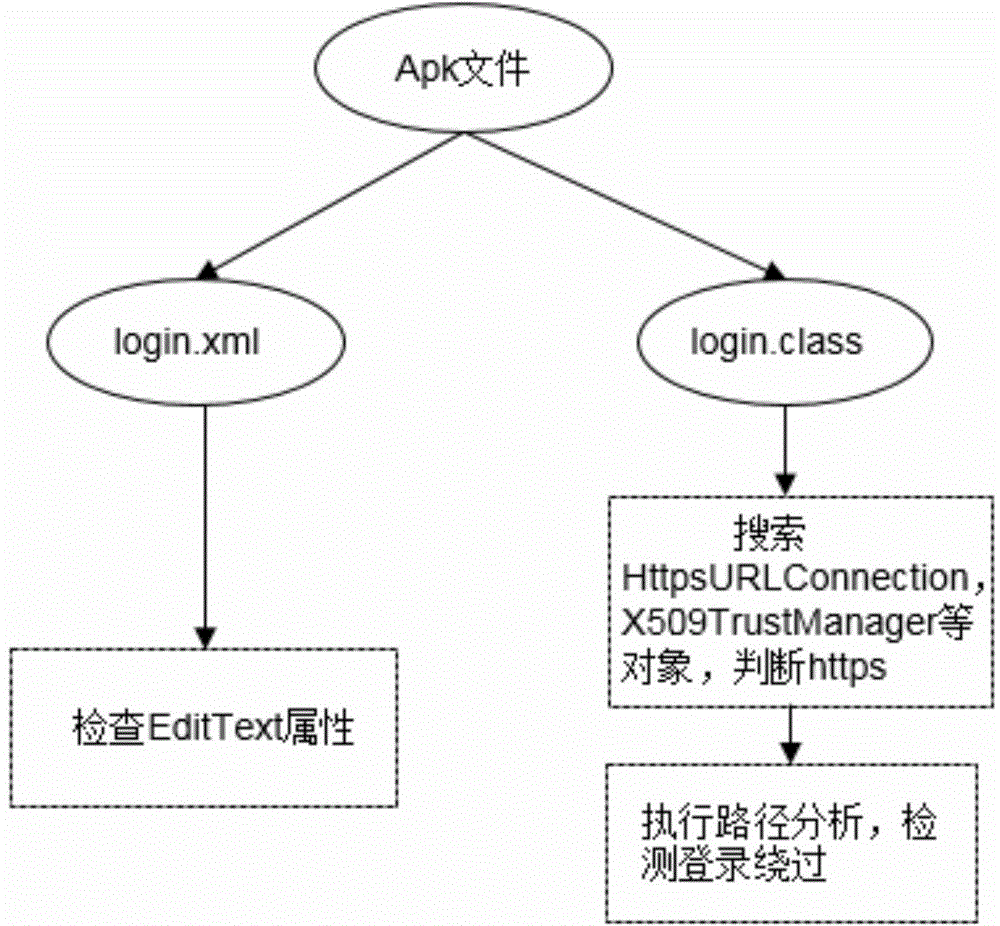
[0022] 1) First decompile the apk file, get all the layout files and smali code, traverse all the layout files, according to some common features of the login interface,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com