Method for implementing abnormal traffic interception based on SDN
A technology of abnormal traffic and traffic, which is applied in the field of network security, can solve problems such as unsatisfactory and suspicious message interception and interception effects, and achieve the effect of flexible interception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
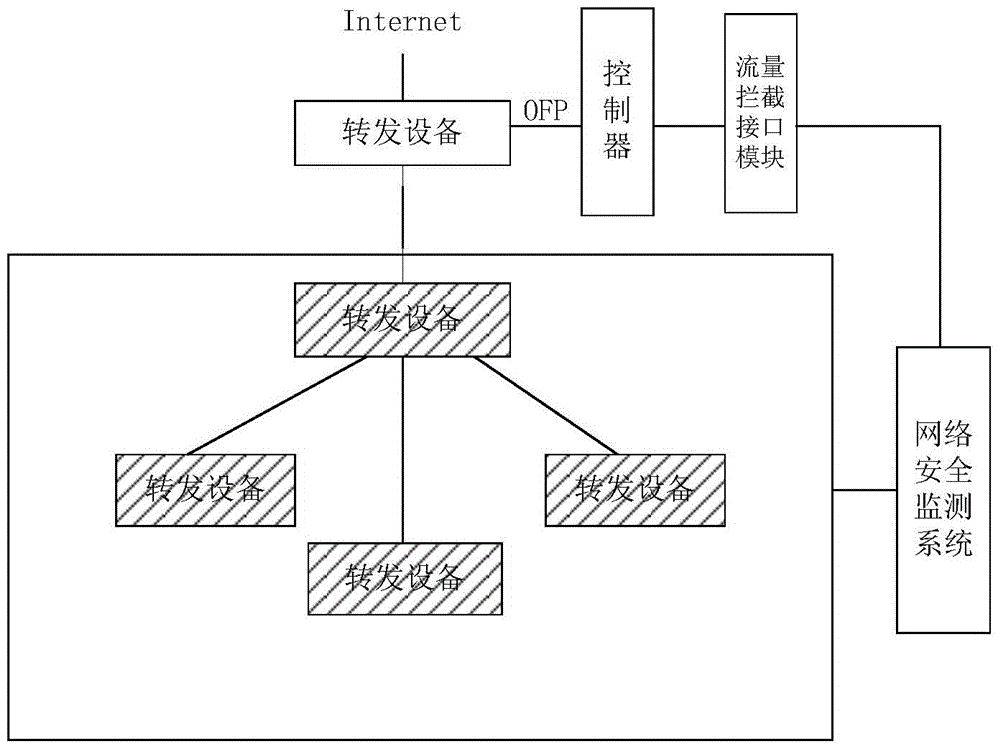
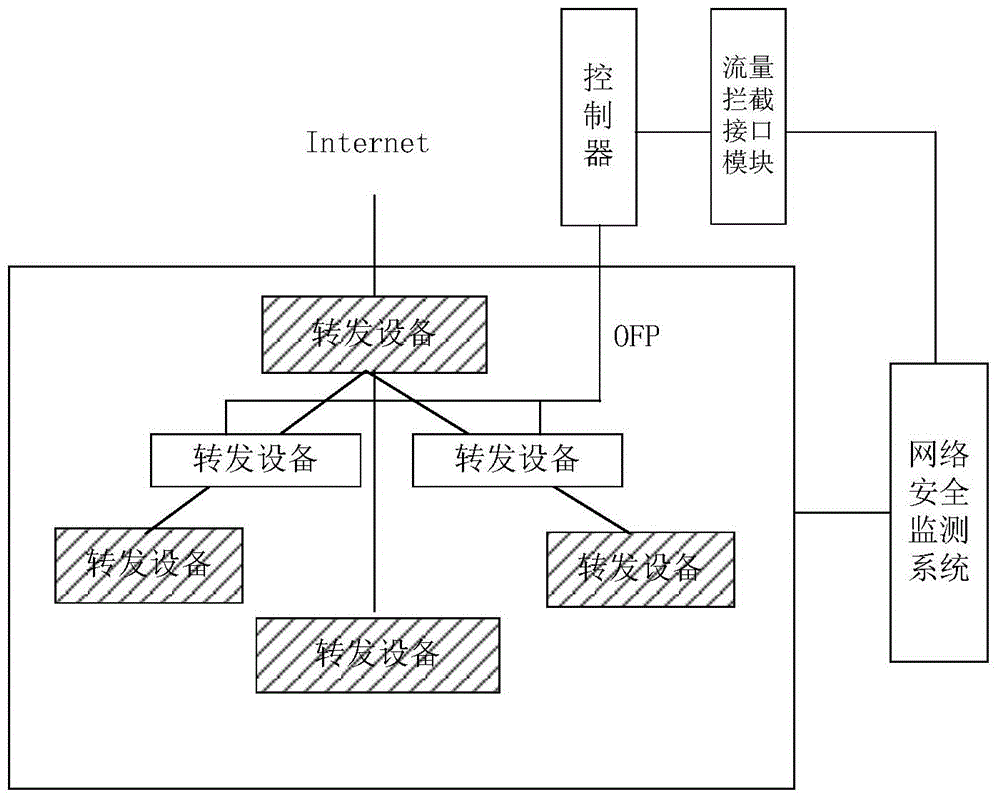
[0054] SDN network is a new type of network innovation architecture, which is a way to realize network virtualization. Its core technology, OpenFlow, separates the control plane and data plane of network equipment, thereby realizing flexible control of network traffic and making the network a pipeline. Get smarter.
[0055] In the embodiment of the present invention, a network security monitoring system and an abnormal traffic interception system are set in the network. The abnormal traffic interception system includes an abnormal traffic interception interface module, an SDN controller, and an SDN forwarding device. The abnormal traffic interception interface module is connected to the SDN controller, and the SDN Controllers and SDN forwarding devices support the openflow protocol.
[0056] The network connection between the network security monitoring system and the abnormal traffic interception system, and between the abnormal traffic interception interface module and the S...
Embodiment 2
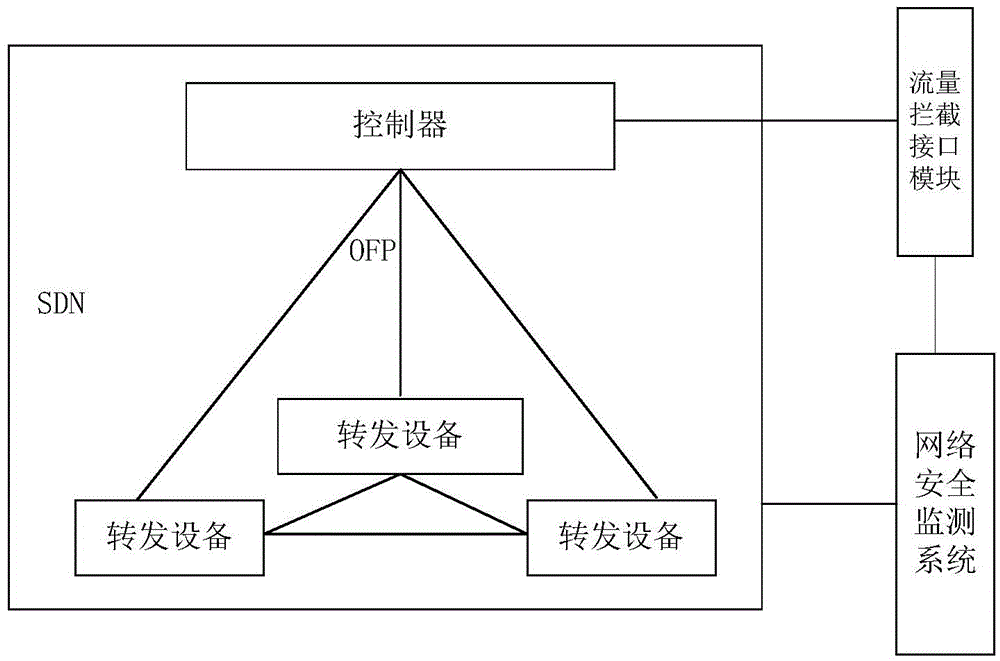
[0089] This embodiment provides a system for realizing abnormal traffic interception based on SDN, and its specific implementation structure is as follows Figure 5 As shown, it may specifically include the following modules: a network security monitoring system 51 and an abnormal traffic interception system 52 , and the abnormal traffic interception system 52 includes: a traffic interception interface module 521 , an SDN controller 522 and an SDN forwarding device 523 .
[0090] The traffic interception interface module 521 is used to extract abnormal traffic characteristic information in the network, formulate a corresponding traffic interception strategy according to the abnormal traffic characteristic information, and send the abnormal traffic characteristic information and traffic interception strategy to the SDN control device;
[0091] The SDN controller 522 is configured to generate a traffic interception matching entry of a forwarding device according to the abnormal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com