A smart cryptographic key cryptographic algorithm detection system based on a security sandbox mechanism
An intelligent cryptographic key and cryptographic algorithm technology, applied in digital data protection, digital data authentication, platform integrity maintenance, etc., can solve the problems of complex and unclear operation process, cumbersome interaction, difficult to adapt to on-site forensics, on-site analysis, etc. Avoid the effects of loading driver conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described in detail below in conjunction with the accompanying drawings.
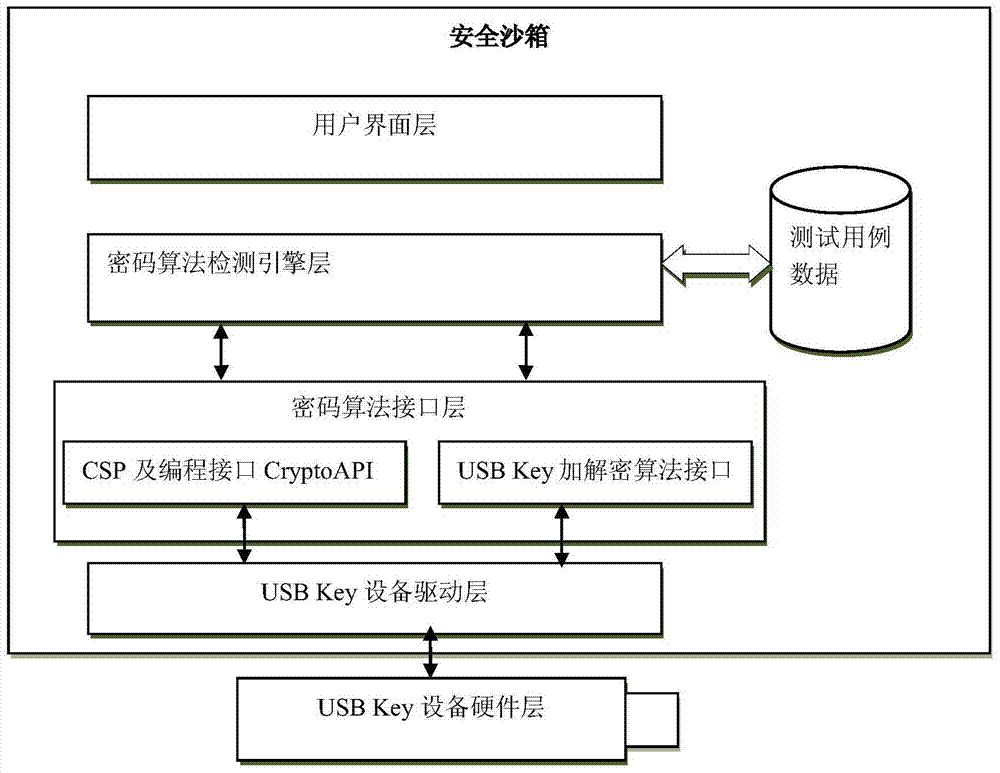
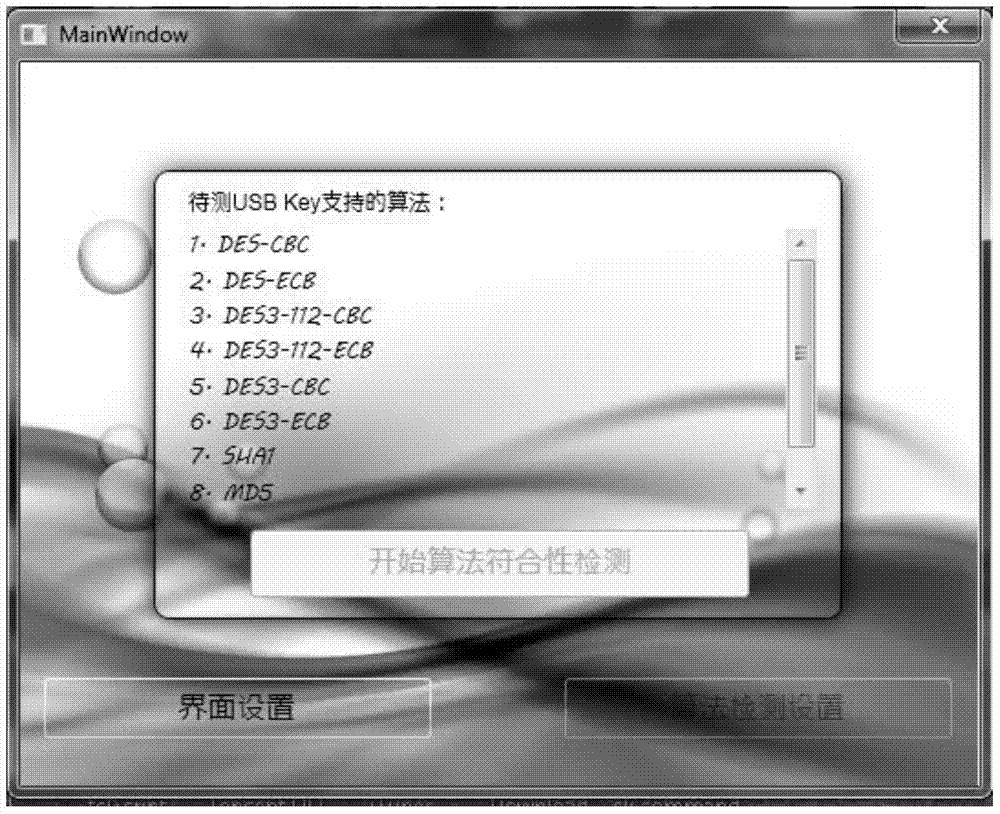
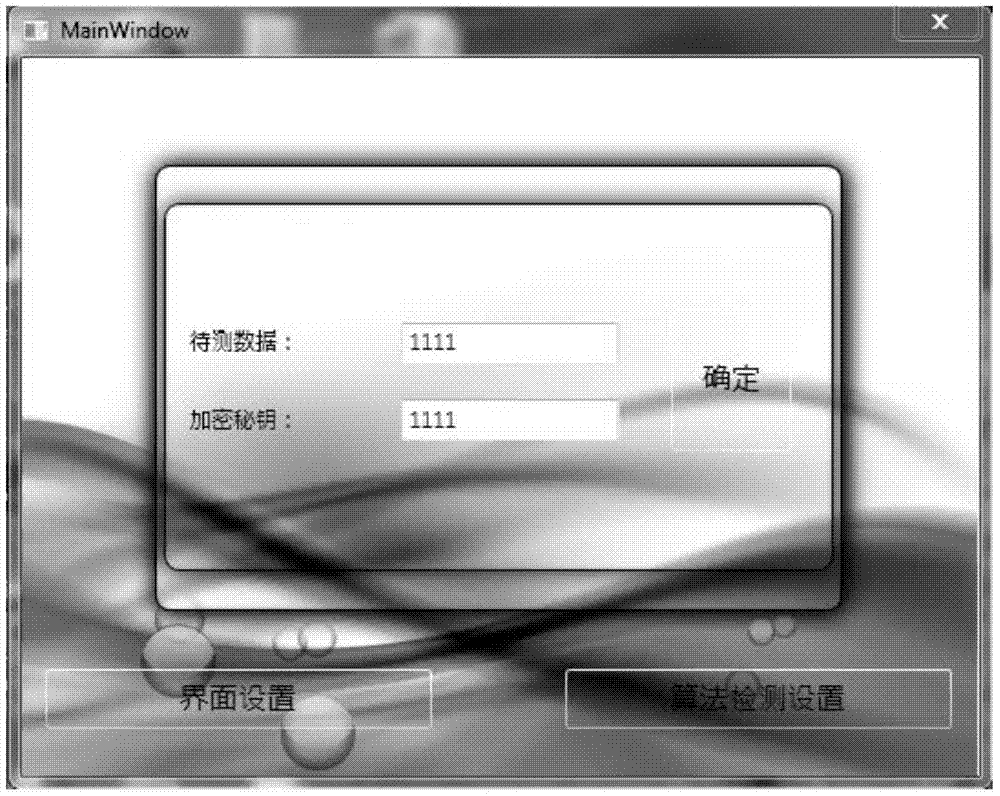
[0038] The present invention adopts a hierarchical module design, which includes: USB Key device hardware layer, USB Key device driver layer, cryptographic algorithm interface layer, cryptographic algorithm detection engine layer and user interface layer from bottom to top. In addition, the present invention also includes some pre-placed test cases for backup in special cases. All other layers except the USB Key device hardware layer are pre-placed in the security sandbox to avoid crashes caused by loading driver conflicts and incomplete uninstallation of drivers.
[0039] The hardware layer of the USB Key device is a USB Key device obtained by the hardware manufacturer after integrating the smart card chip and the storage unit on the integrated circuit board and designing according to the appearance specification of the USB Key device by the State Cryptograp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com