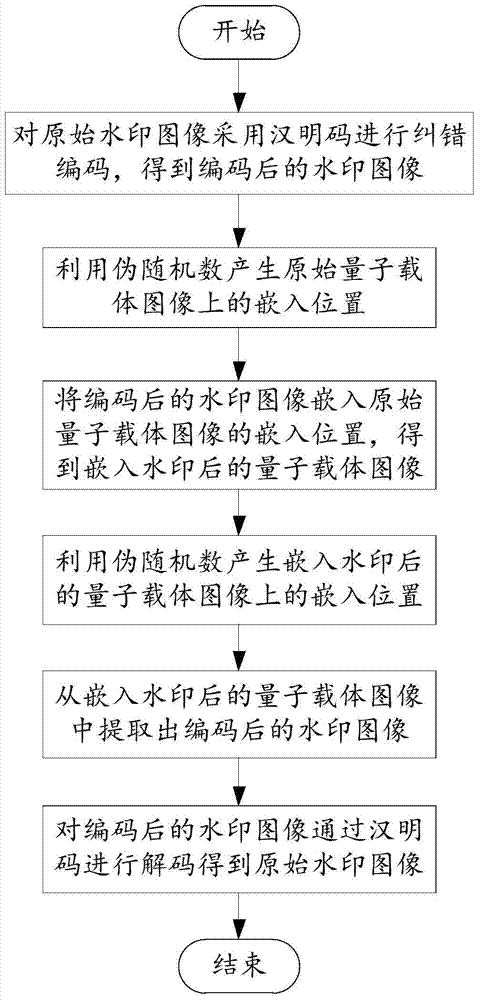
A Quantum Image Watermarking Method Based on Hamming Code
A quantum image and Hamming code technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of large amount of calculation, difficult quantum gate operation, and low computational complexity, and achieve good robustness and complete realization The effect of high performance and accuracy, and low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0100] Please refer to Figure 4 with Figure 5 , Embodiment 1 of the present invention is:
[0101] see Figure 4 , the original watermark image containing "Copyright" font is clear;
[0102] see Figure 5 , the original watermark image containing "Copyright" font is encoded by Hamming code, and the encoded watermark image is blurred, which shows that the error correction encoding of the original watermark image by Hamming code is more effective.
Embodiment 2
[0104] 1. When the original watermark image is encoded with Hamming code for error correction:
[0105] Assuming that the information bit sequence of the original watermark image is a vector A of 1×4, it is divided into one group, and the code length is 4. Use (7,4) Hamming code for error correction coding on vector A, then the code length of Hamming code is 7, and the code length of each group of error correction codes is 3. The bit sequence after encoding the vector A is a 1×7 vector C, and the generator matrix of (7,4) Hamming code is G, then
[0106] A·G=C,
[0107] Among them, "·" represents the matrix multiplication operation, and
[0108]
[0109] 2. When the coded watermark image extracted from the watermark-embedded quantum carrier image is verified and decoded by Hamming code:
[0110] Assuming that the bit sequence of the coded watermark image extracted from the watermarked quantum carrier image is a 1×7 vector D, the vector D and the Hamming check matrix H sh...
Embodiment 3
[0115] Please refer to Figure 6 to Figure 10 , Embodiment three of the present invention is:
[0116] see Image 6 , assuming that the size of the original quantum carrier image is 2 2 ×2 2 , namely m=2, n=2, then
[0117] The horizontal coordinates of the original quantum carrier image are |x>=|x 1 x 0 >
[0118] The vertical coordinate of the original quantum carrier image is |y>=|y 1 the y 0 >
[0119] The original watermark image is a 1×4 vector W, and the encoded watermark image is a 1×7 vector W’;
[0120] If i=2, and x 2 = 1,y 2 = 2, the auxiliary qubit is Z 2 , then at this time
[0121] The corresponding encoded watermark image information is W 2 ';
[0122] The embedding position of the corresponding original quantum carrier image is M 1,2 , namely x 1 =0,x 0 = 1,y 1 = 1,y 0 = 0;
[0123] 1. W in the encoded watermark image information 2 ’ Embedding position M of embedding the original quantum carrier image 1,2
[0124] When the least signifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com