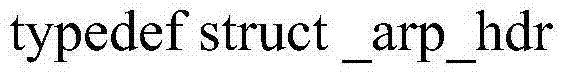Method and system for protecting server IP
A technology for protecting systems and servers, applied in transmission systems, electrical components, etc., can solve problems such as cumbersome, illegal hosts cannot be occupied, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
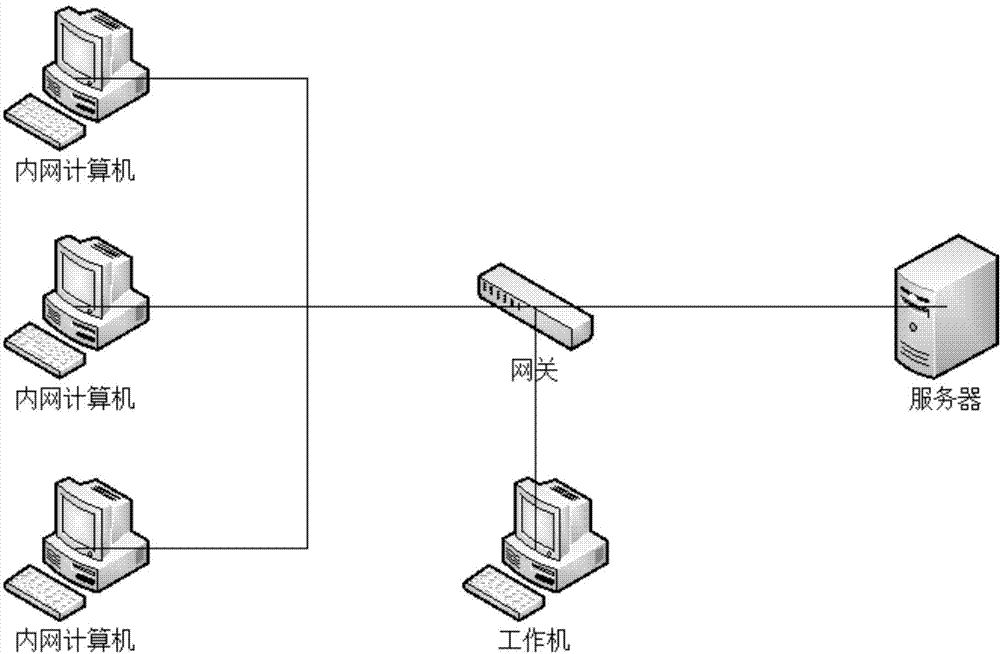
[0040] Such as figure 1 Shown is a schematic diagram of the system topology of the server IP protection method of the present invention, wherein, according to the above topology diagram, a server IP protection method includes:
[0041] Step 1) select a machine in the network segment as a working machine, which maintains a protection list;
[0042] Step 2) the working machine obtains the ARP query packet sent by the host under the same network segment, and the ARP query packet is a MAC address that includes the IP address that the host will obtain and the visitor;
[0043] Step 3) extract IP address and MAC address from described APR inquiry packet, and inquire whether this IP address is in the protection list, wherein, if IP address is in IP protection list and MAC does not correspond, then think it is illegal host, and reply to the host with an ARP packet whose IP is occupied.
[0044] Wherein, before step 1), the protected IP protection list and their legal MAC mapping rec...
Embodiment 2
[0047] It will be described in detail in combination with Embodiment 2.
[0048]Specifically, the implementation method of this scheme is to select a machine in the network segment to do the protection action, called the working machine, and this machine protects the specified IP from being used by illegal MAC through ARP attack. The principle lies in the process of IP acquisition. When a host wants to use a certain IP, it needs to obtain the consent of the intranet. This is the process of ARP negotiation. The normal process is that the host will first send an ARP broadcast to ask whether there is an IP address in the intranet. Use this IP, if yes, tell me (MAC), if this IP is indeed occupied, the ARP protocol defines the behavior of this IP occupant: reply an ARP packet to the inquirer, indicating that the IP is used by me (MAC) , the initiator of the ARP query knows that the IP is occupied, and the IP acquisition fails. Conversely, if there is no reply packet from any host ...
Embodiment 3
[0051] It will be described in conjunction with a specific program design. Specifically, the method includes the following steps in detail:
[0052] 1. Record the policy (protected IP list and their legal MAC mapping) into the memory for backup.
[0053] 2. Use the winpcap library to capture packets in promiscuous mode on all network cards in order to capture ARP query packets.
[0054] 3. To judge each captured ARP query packet, the judgment logic is as follows:
[0055] 1) If it is initiated by the local machine, it will not be processed;
[0056] 2) If sender_ip and target_ip in the ARP structure are consistent, or sender_ip is 0, then it is considered that this is an inquiry packet that wants to obtain an IP address, and only this kind of inquiry packet that wants to obtain an IP address is processed.
[0057] 3) Look for target_ip in the protection list, if found, it means this is a protected IP
[0058] 4) Find the MAC of this IP mapping from the protection list, if i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com