Authentication method, system and mobile terminal
A mobile terminal and identity verification technology, applied in the field of communication, can solve the problems of poor mobility, the limitation of the number of processing objects cannot meet the actual needs, and the identity verification system cannot be used flexibly, so as to achieve a good user experience and strong data. The effect of processing power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] In the following description, numerous details are provided in order to provide a thorough understanding of the invention. However, it will be appreciated by those skilled in the art that the following description relates only to preferred embodiments of the invention and that the invention may be practiced without one or more of these details. In addition, in order to avoid confusion with the present invention, some technical features known in the art are not described.
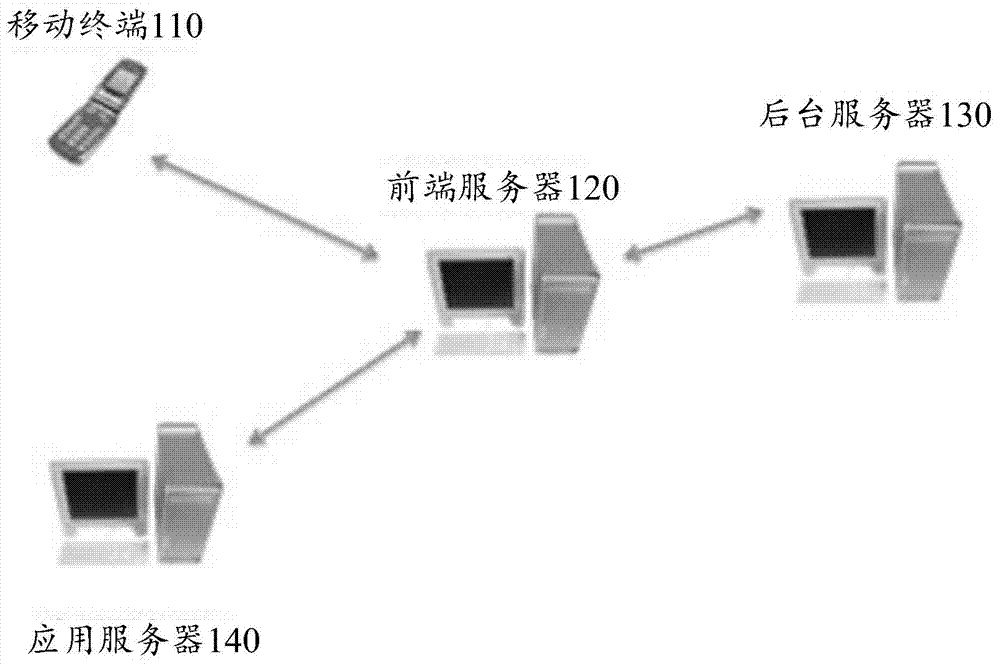
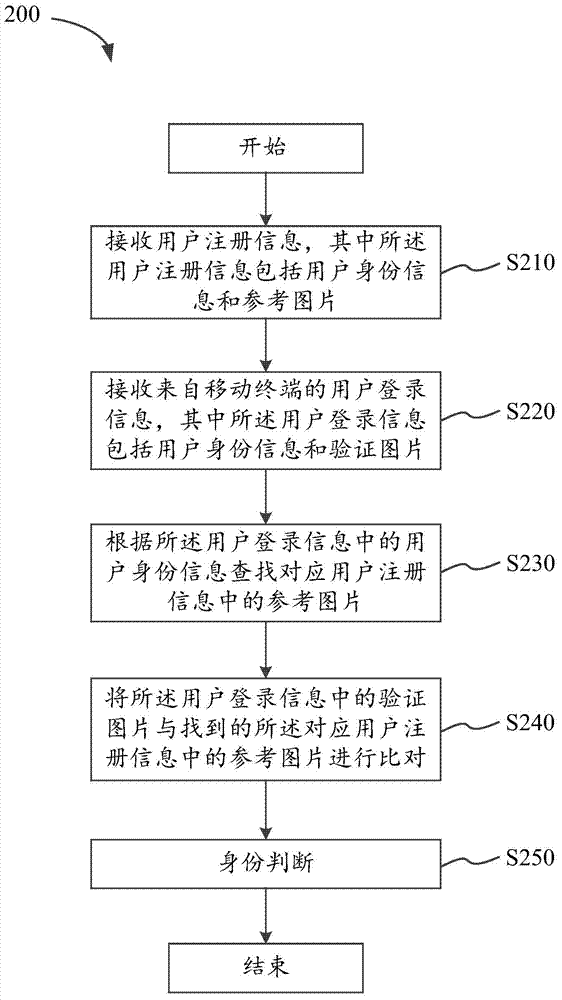
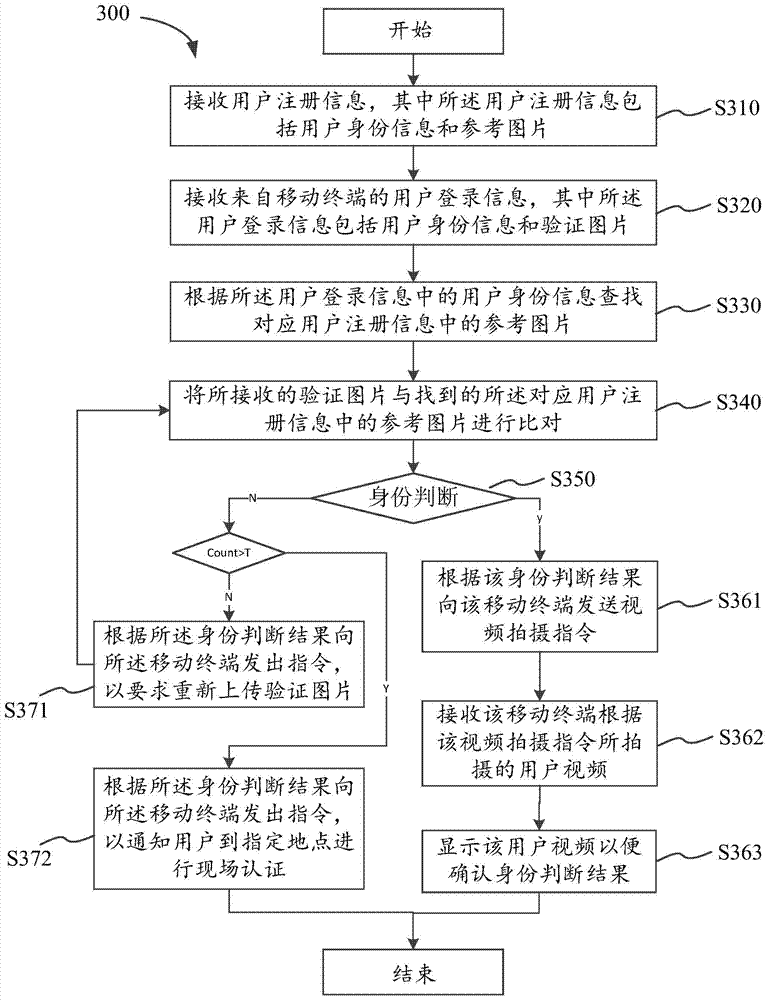
[0058]With the development of smart mobile devices, more and more people have mobile terminals, such as smart phones, Notes and Pads. On the one hand, the portability of mobile devices has brought great convenience to people's lives; on the other hand, mobile devices have been equipped with powerful cameras; on the other hand, communication networks 3G and 4G are also developing rapidly, and the Camera applications have technical support. In addition, with the development of cloud computing, system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com