A method and system for uniformly naming malicious code based on file fingerprints
A malicious code and file fingerprinting technology, applied in the field of information security, to improve notification and disposal efficiency and solve uniformity problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] The invention provides a method for uniformly naming malicious codes based on file fingerprints, comprising:
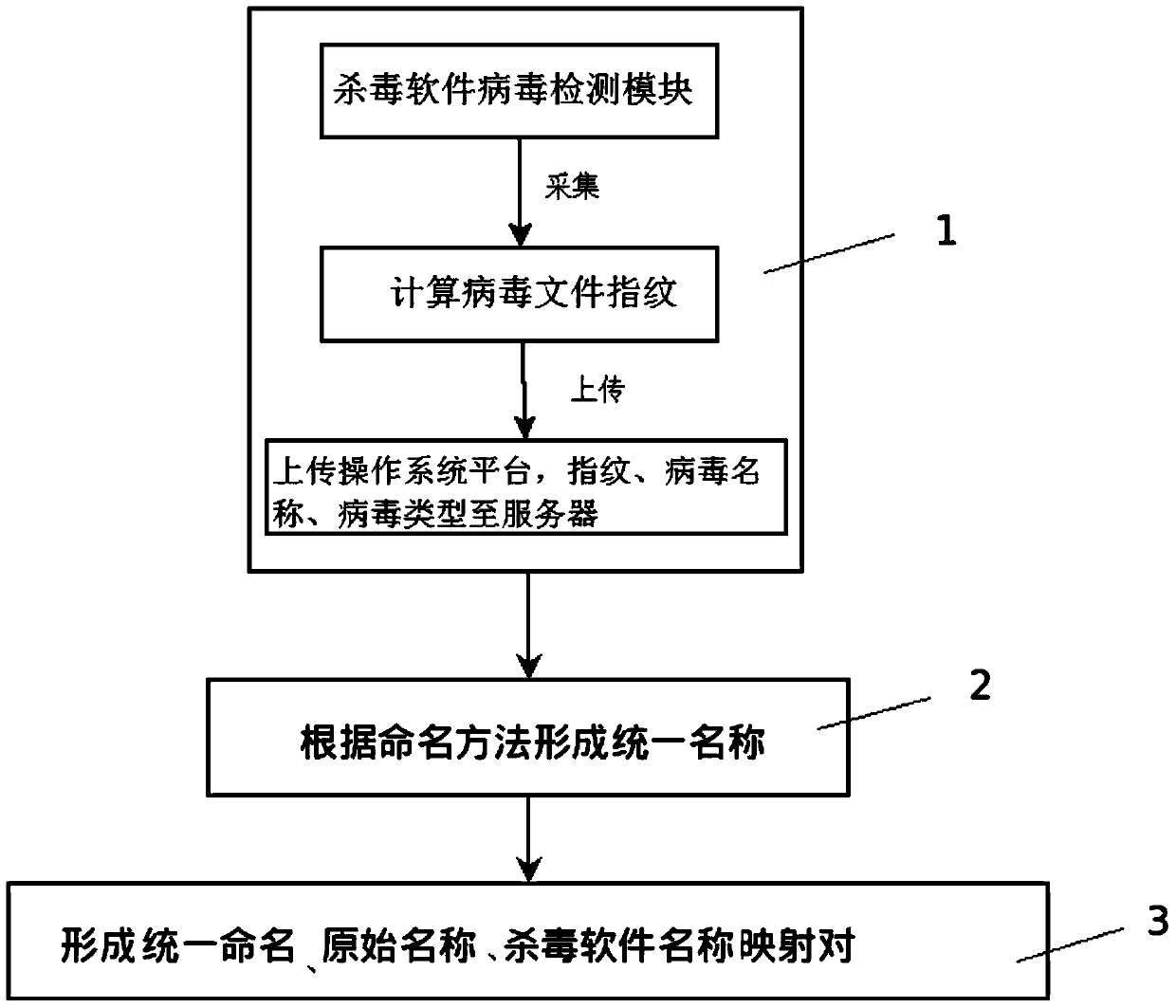
[0034] Step 1: Collecting file fingerprints for anti-virus software, calling when the anti-virus software checks and kills malicious codes, and providing the anti-virus software with the characteristic value of returning malicious codes;
[0035] Step 2: Name the malicious code, receive the malicious code with characteristic values provided in step 1, and generate a unified name for the malicious code named according to the agreed rules:
[0036] Step 3: Establish a mapping relationship between the unified naming of the malicious code described in step 2 and the independent naming of the original factory, receive the preset parameters of the malicious code, and store the mapping relationship as a data row in the database implementing the mapper Above, provide the interface to view the corresponding relationship between the unified naming and the original fact...
Embodiment 2
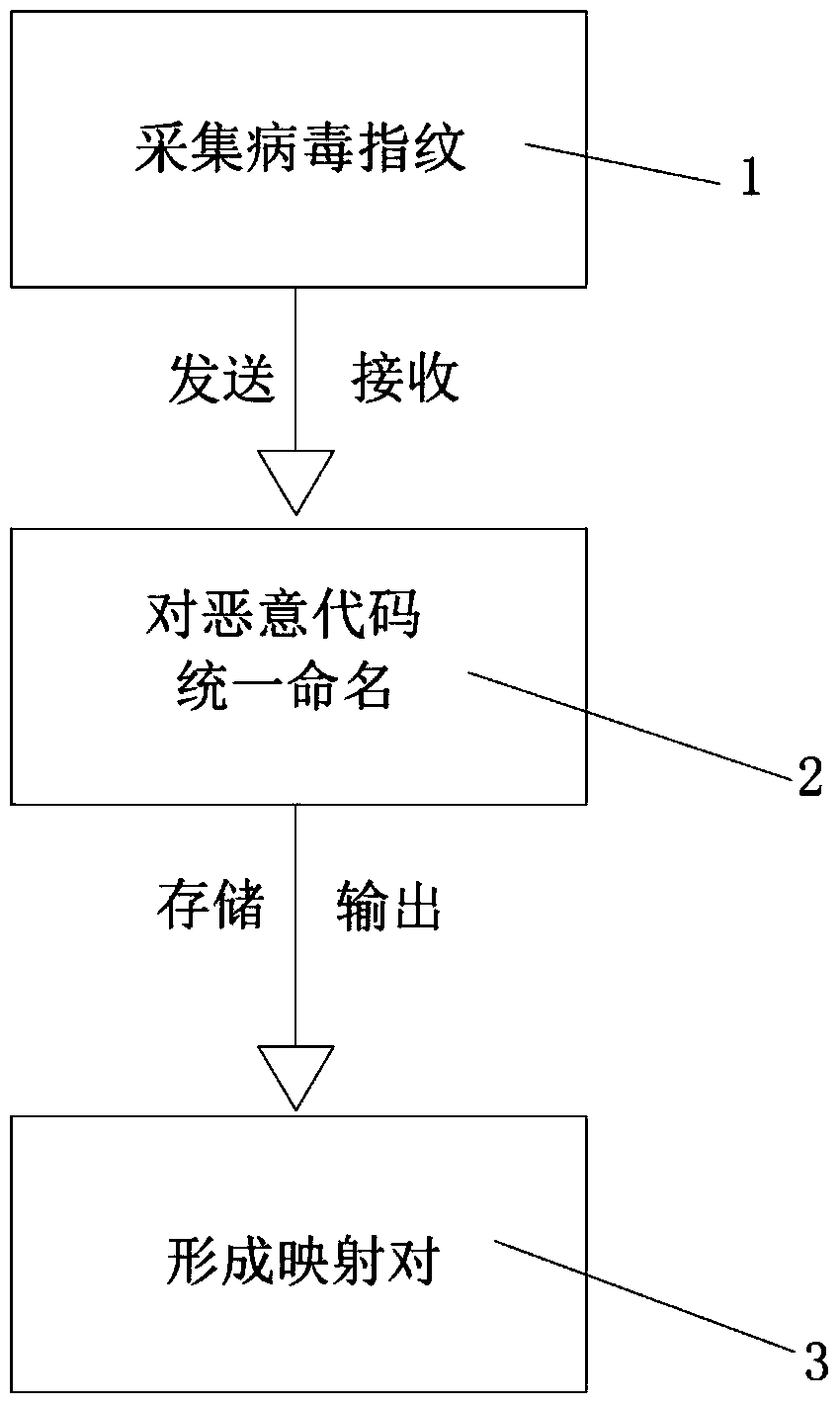
[0038] Such as figure 2As shown, the present invention also provides a system for uniformly naming malicious codes based on file fingerprints. The system includes a file fingerprint collector 1 that collects file fingerprints for antivirus software. , providing the anti-virus software with the characteristic value of returning the malicious code; including a unified malicious code namer 2 receiving the characteristic value of the malicious code, and the unified malicious code namer 2 naming the malicious code according to the agreed rules; Also includes a malicious code unified naming mapper 3, the malicious code unified naming mapper 3 unifies the mapping relationship between naming and the original factory's independent naming, receives the preset parameters of the malicious code, and uses the mapping relationship as data The line is stored on the database implementing the mapper, and the corresponding relationship between the unified naming and the original factory naming ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com