A boot authority verification method and system based on an intelligent terminal
A technology of intelligent terminal and verification method, applied in the field of authority verification, can solve the problems of high development cost, high expansion cost, impact control, etc., and achieve the effect of easy expansion and upgrade
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
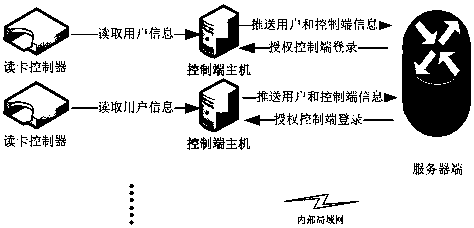
[0033] With the development of science and technology, smart terminal products have become very popular. In the past, the verification method of using scanning equipment to obtain user information for verification and authorization has highlighted problems such as high expansion costs, possible interface conflicts, and radio frequency interference. Therefore, it is the general trend to develop alternative methods that are cheaper and more versatile, and reduce interface interference.
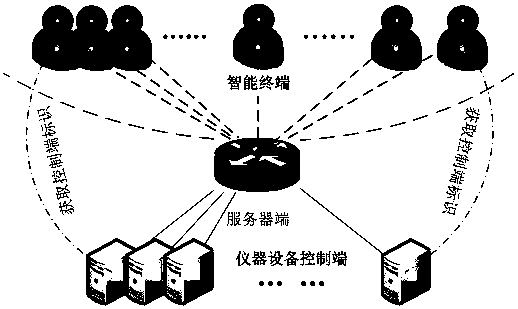
[0034] The smart terminal can easily access the network for signal transmission of various networks. At the same time, by developing the client program of the general operating system, the user can expand the smart terminal. Since the smart terminal has the above advantages, the present invention selects the smart terminal to obtain user identity information to verify the power-on authority.
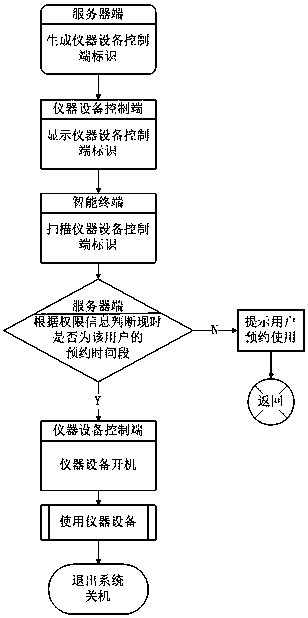
[0035] Such as figure 2 , 3 As shown, the verification method provided by the present invention incl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com