Physical isolation type USB port protection system and method
A USB interface, physical isolation technology, applied in the direction of platform integrity maintenance, electrical digital data processing, internal/peripheral computer component protection, etc. Permission access control strategy, the effect of resisting Trojan theft and preventing internal leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
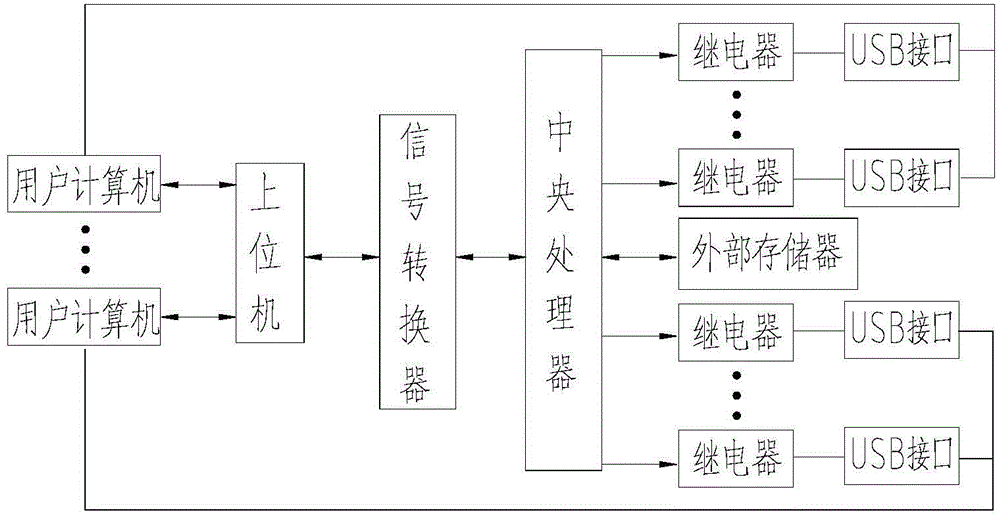
[0026] refer to figure 1 , is a structural schematic diagram of a physically isolated USB interface protection system of the present invention; the protection system includes a central processing unit, a host computer connected to a plurality of user computers, an external memory for storing user names and passwords, and is used for according to the central The switching signal of the processor controls multiple relays of multiple USB interface switches on the user's computer; Connect to the corresponding port of the CPU.
[0027] Wherein, a signal converter for converting the serial port RS232 level signal of the computer into a TTL level signal is arranged between the upper computer and the central processing unit.
[0028] Wherein, an isolator for isolating digital signals from analog signals and preventing interference signals is provided between the central processing unit and the relays.
[0029] Wherein, the protection system also includes a voltage regulator for stab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com