Method for randomly simulating sensitive information in cloud database
A sensitive information and database technology, applied in the field of information security, can solve problems such as sensitive information leakage, and achieve the effect of overcoming simplicity and directness, increasing the cost of attacks, and increasing the cost of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
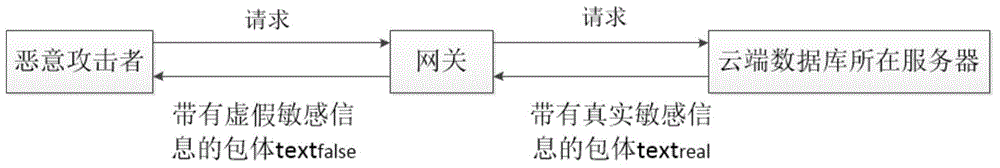
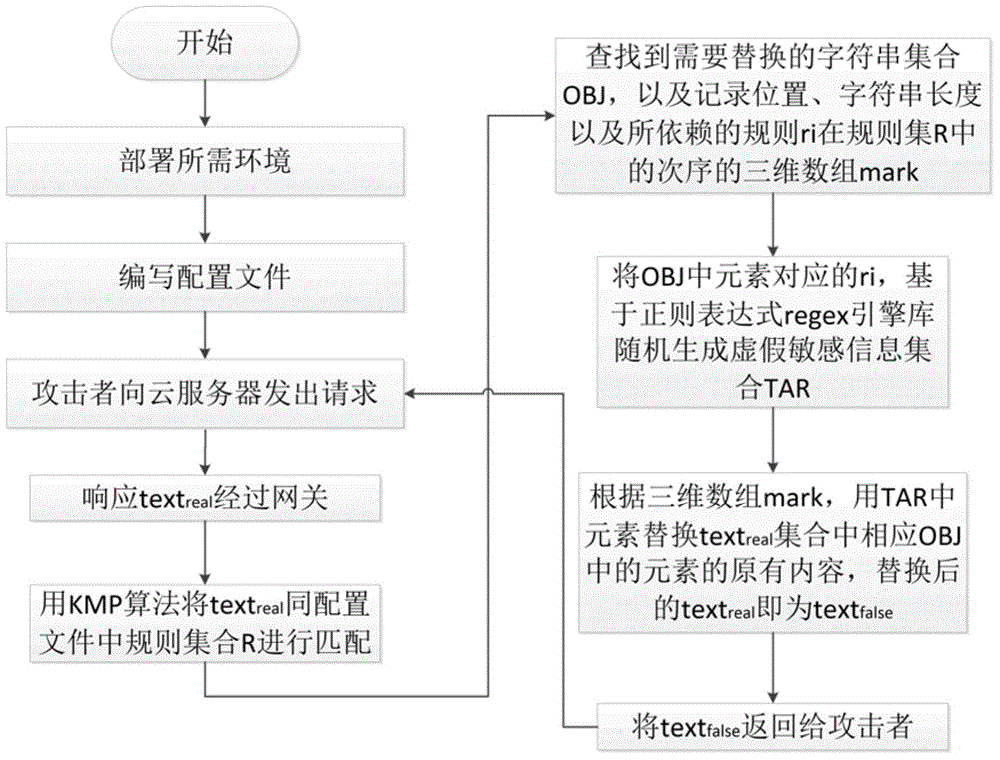
[0017] The following is based on a real attack scenario, combined with figure 1 and figure 2 , the present invention is described in detail through an example of applying the randomized mimicry method.
[0018] like figure 1 As shown, the method of the present invention solidifies or implants the randomized mimetic method into the application layer Nginx gateway corresponding to the server where the cloud database is located. After the attacker sends an HTTP request to the server, the server's HTTP response header and package body will pass through the application layer gateway, randomize the content of the package body, and finally return the fake package body content to the malicious attacker. Specifically include the following steps:
[0019] (1) Provide a configuration interface to the database administrator in the application layer gateway corresponding to the server where the cloud database is located. This interface is used to formulate rules for determining whether...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com