Systems and methods using an origin pattern to verify the authenticity of a host object
A technology of authenticity and pattern, applied in the direction of record carrier, transmission system, digital transmission system used by the machine, can solve the problem of high cost, and achieve the effect of reducing resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
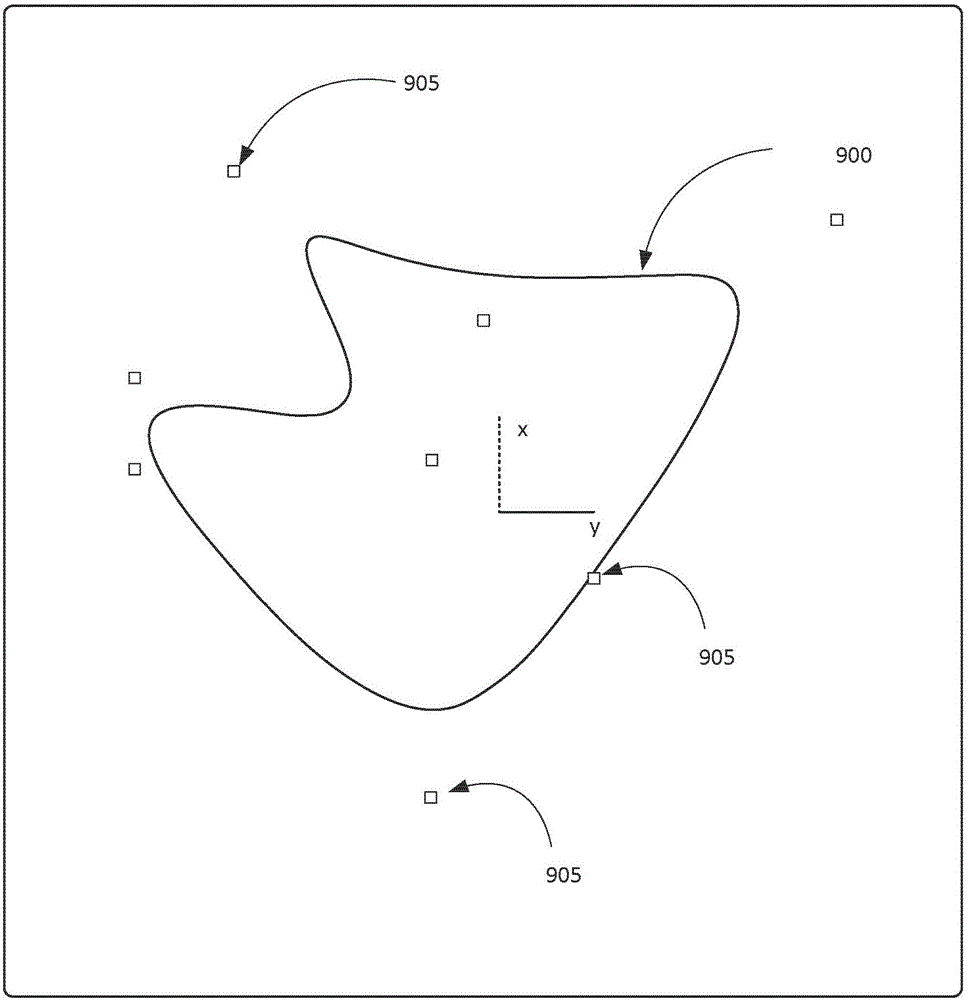
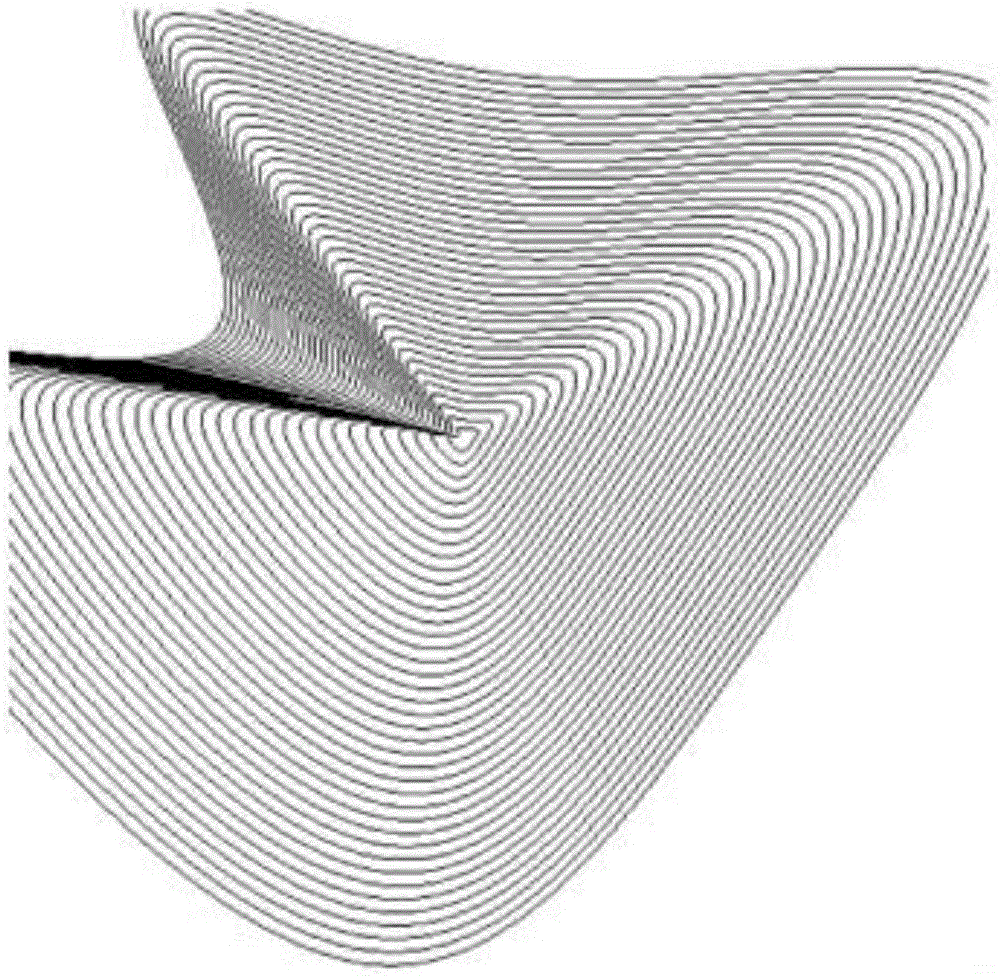
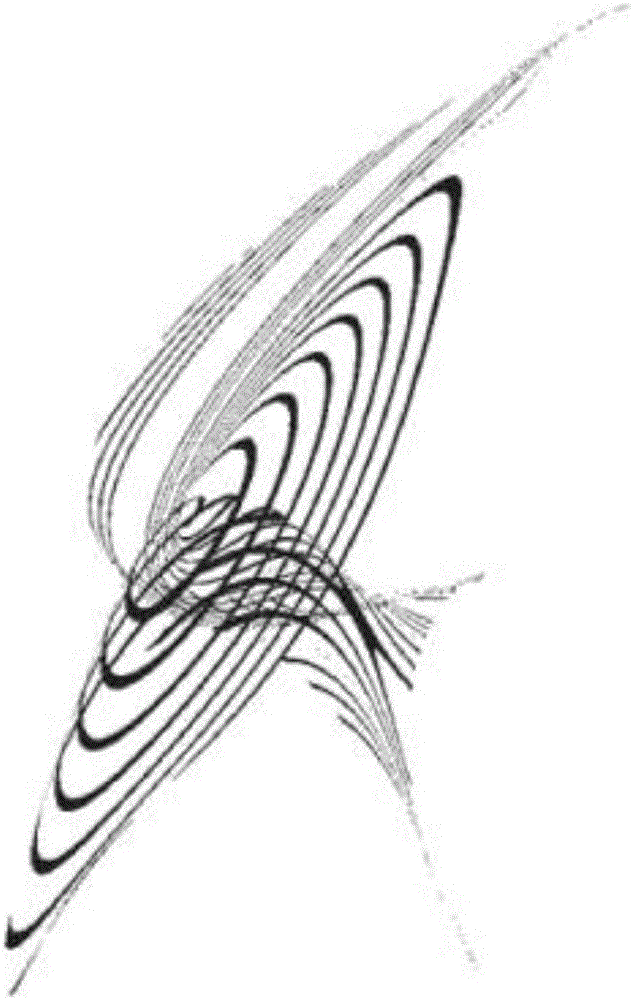
[0027] Implementations include the use of a unique combination of concepts and tools found in differential geometry, encryption, computer-aided design, and smartphone applications to allow manufacturers (e.g., OEMs, design houses, supply chain partners, etc.) to protect their products and assure consumers Systems and methods for product quality. Embodiments achieve protection by generating unique source patterns in the form of computer graphics driven cryptographic challenge pairs or fingerprints for each manufactured part. The source pattern includes a serial number component and a surface texture component. The surface texture component can be 2D or 3D textured, while the serial number component is text or character based, but can appear in the form of a barcode. The source pattern can be verified instantly using an application on the mobile device combined with a central verification processor to provide a semi-distributed verification system. Since the surface texture co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com