Wireless network system and wireless network access method
A wireless network system and wireless network technology, applied in the field of wireless network systems and wireless network access, can solve problems such as security consequences, increase production, increase costs, etc., to ensure legal connections, improve security performance, and avoid security loopholes Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
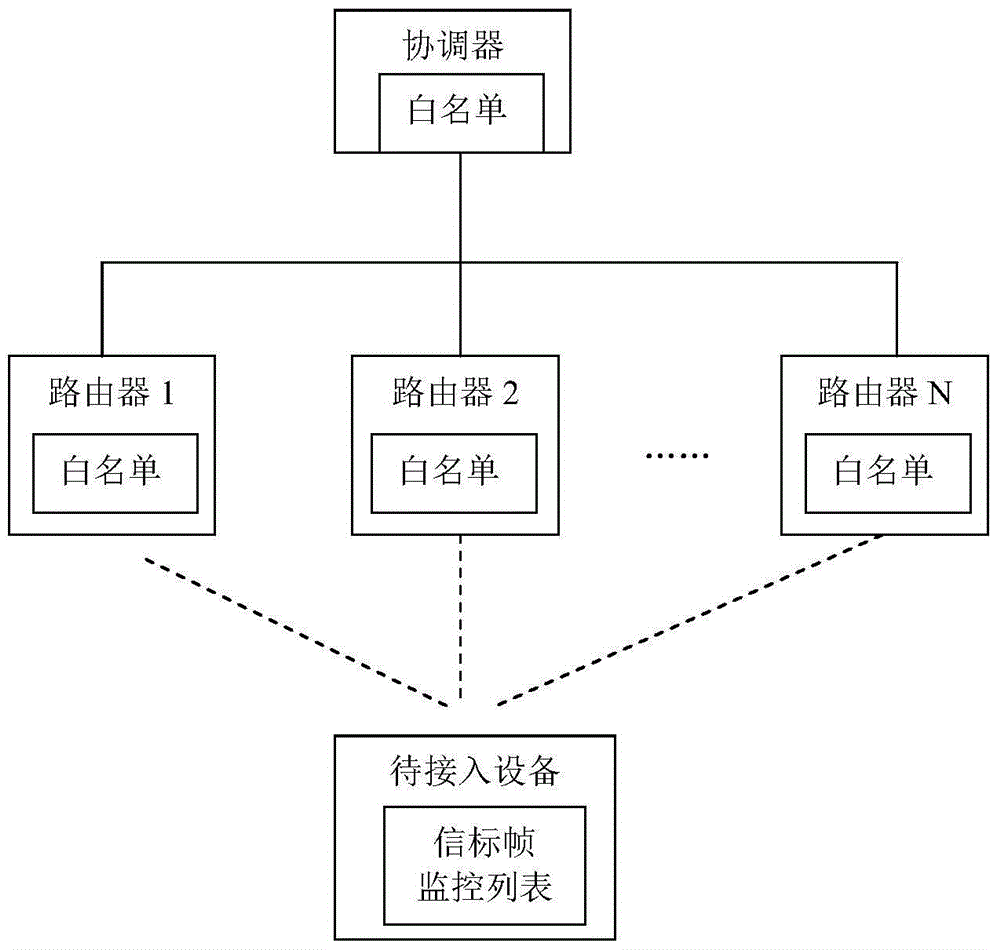
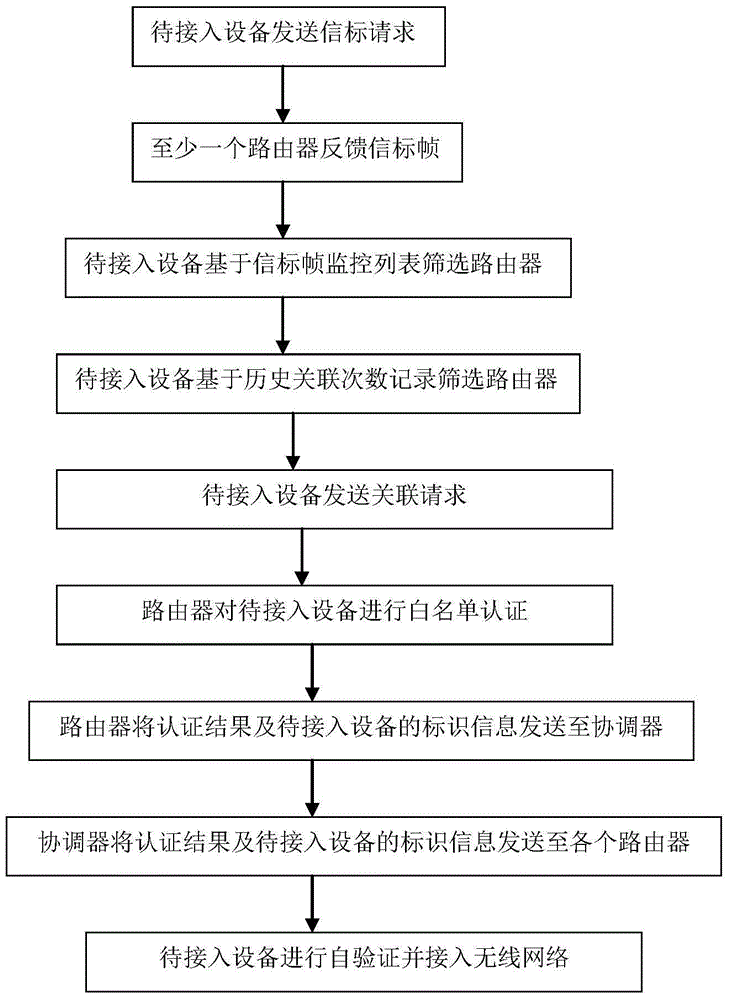
[0077] The device to be connected scans the surrounding routers that support wireless access, and obtains the beacon frames of the surrounding routers. The beacon frame watch list records invalid beacon frames and beacon frames with a bad history. Filter the router according to the beacon frame monitoring list in the device to be connected. Delete and filter out the beacon frames in the beacon frame monitoring list, keep the remaining beacon frames and cache them. Select a beacon frame with the largest signal strength value among the reserved beacon frames. The physical address and service set identification information are extracted from the beacon frame. The beacon frame contains the signal strength value (RSSI value). By parsing and comparing the strength value and selecting the beacon frame with the largest strength value, the largest strength value indicates that the wireless access point of the beacon frame is relatively far from the device to be connected. closer. T...
Embodiment 2
[0079]The Zigbee network enables the network access function by default, and there is no need to set it to be enabled at a specific time or manually enable this function. The router receives the network access information of the device to be connected, which includes the verification ID of the device to be connected, and the device to be connected is configured with a unique verification ID before the product leaves the factory. Afterwards, the router will judge whether the verification ID of the device to be connected is in the white list of the router. The white list is stored in the router by default. If the verification ID of the device to be connected is in the white list, the device to be connected is allowed to join the network. At the same time, devices whose authentication IDs are not in the whitelist cannot join the network. That is to say, the network itself can actively refuse the joining of other unapproved devices to be connected, which ensures the security of ...
Embodiment 3
[0089] In this embodiment, a ZigBee network is taken as an example to describe the present invention. Screening of devices to be connected based on the beacon frame monitoring list:
[0090] When the device to be connected sends a beacon request to at least one router and receives several beacon frames fed back by the router, it will filter the received beacon frames through the beacon frame monitoring list. All beacon frames in the beacon frame monitoring list are filtered and deleted, and then the remaining beacon frames are saved in the beacon buffer. This is the first screening performed by the device to be connected to at least one router.
[0091] Filtering based on the number of association history:
[0092] After the device to be accessed sends a beacon request to at least one router, and receives multiple beacon frames. Each beacon frame in the beacon cache has a record of historical association times. The device to be connected will initiate an association reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com