Security analysis method for power system suffering from terror attack
A technology of power systems and analysis methods, applied in system integration technology, information technology support systems, instruments, etc., can solve problems such as only considering active power, ignoring voltage, reactive power, and simple models
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
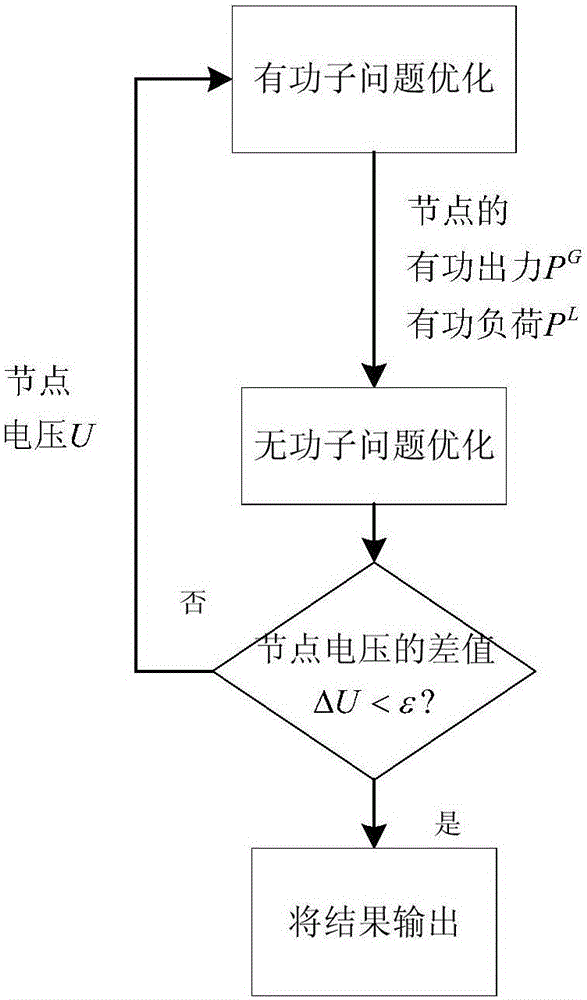
[0198] Such as figure 1 Shown is the optimization flowchart of the terrorist attack problem of the present invention.
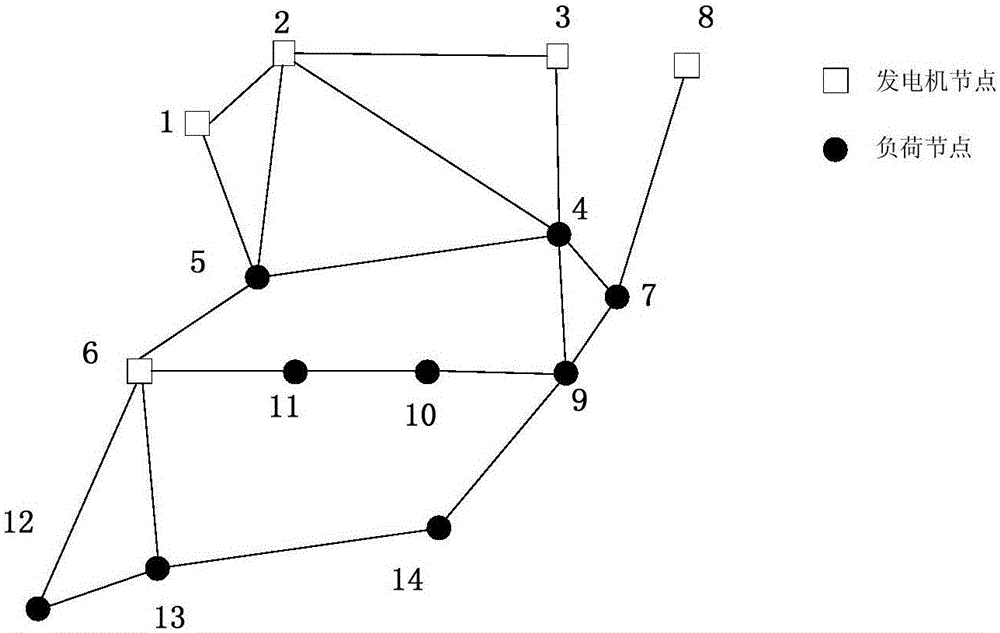
[0199] The graph model of IEEE-14 node systemization is as follows figure 2 As shown, it contains 5 generator nodes, 9 load nodes and 20 edges. The computer used in the experiment is configured with CPU2.0GHz, memory 1G, and optimization software Cplex.
[0200] The IEEE-14 node data is shown in Table 1, and the branch data is shown in Table 2. The total system load is 2.59pu, and each quantity is a unit value. The power flow calculation takes node 1 as the balance node, and the voltage amplitude, angle, line Both the transmitted power and the active power injection of node 1 are the results of power flow calculations.
[0201] Table 1 IEEE-14 node data
[0202]
[0203] Table 2 IEEE-14 tributary data
[0204]
[0205]
[0206] Note: Type 0 means AC line, 1 means transformer winding, 2 means grounding branch; for AC line YK means susceptance to...
Embodiment 2
[0214] IEEE-118 calculation example
[0215] IEEE-118 node system wiring such as Figure 5 , where the black dots represent the load nodes, and the white squares represent the generator nodes. The system contains a total of 19 generating units, with a total output power of 4374.9MW, a total load of 4242MW in the network, and a benchmark capacity of 100MVA.
[0216] Similar to the IEEE-14 node, it is also assumed that the attacker’s attack line cost is 1, that is, = 1, and the threshold of the upper limit of the cut set capacity is set to 18, and then iteratively solves the problem by using the invented idea, and finally obtains the system load shedding and cutting off The line results are shown in Table 4 (the convergence target is reached when active and reactive power is iterated 12 times)
[0217] Table 4 Comparison of IEEE-118 node attack results
[0218]
[0219]
[0220] The change trend of load shedding in each iteration of the 118 system after the attack is as...
Embodiment 3
[0222] IEEE-280 calculation example
[0223] The total output power of IEEE-280 nodes is 4389.56MW, the total load in the network is 4331.69MW, and the reference capacity is 100MVA. Also assume that the attacker’s attack line cost is 1, that is, =1, and the threshold of the upper limit of the cut set capacity is set to 15, and then Utilize the thinking of the present invention to carry out iterative solution, and the system load shedding amount and cut-off circuit result finally obtained are shown in Table 5 (when the active and reactive power alternate iteration is 12 times, the convergence target is reached)
[0224] Table 5 Comparison of IEEE-280 node attack results
[0225]
[0226] The trend of load shedding in each iteration of the 280-node system after the attack is as follows Figure 7 Shown:
[0227] It can be seen from the figure that the amount of load shedding also tends to be stable in the late iteration, which also shows that the fault degree of the terroris...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com