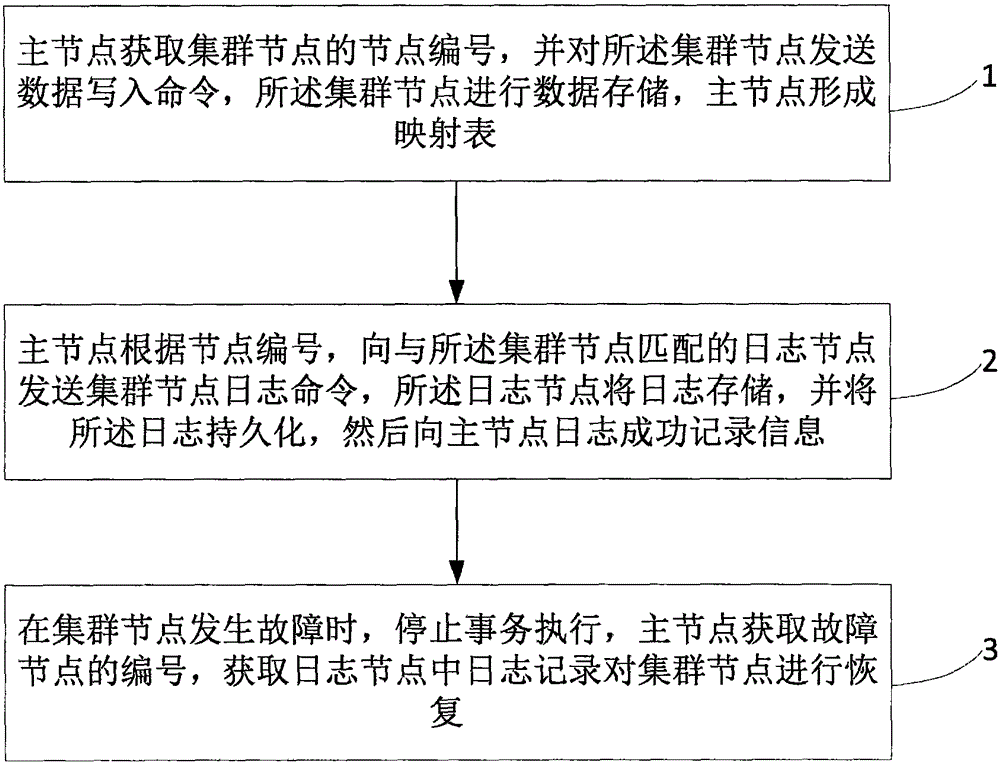
Log recovery method in memory data management and log recovery simulation system in memory data management
A technology of memory data and recovery method, which is applied in the field of data management, can solve the problems of high memory price and inability to be widely used, and achieve the effects of reducing complexity, improving speed and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] The present invention uses "cluster environment" or "multi-machine environment" to represent a distributed concept. In the cluster environment, the main consideration is to divide data into multiple machines for storage. In a cluster environment, each machine node is called a node. Due to the common use of multi-core CPUs in modern computers, some multi-threaded tasks can run on multiple cores in a node, and a core of a CPU is called a site. . Existing in-memory database systems such as VoltDB and SiloR use the advantages of multiprocessors in clusters and cluster nodes to distribute tasks to multiple threads, since each processor core can handle at least one thread (in hyperthreaded CPUs can handle two threads). The system classifies transactions into transactions within a node and transactions across nodes, and tries to put related transaction processes in a node site, so that if a transaction in a site rolls back, it will only affect this node. Also for logs, all s...
Embodiment 2
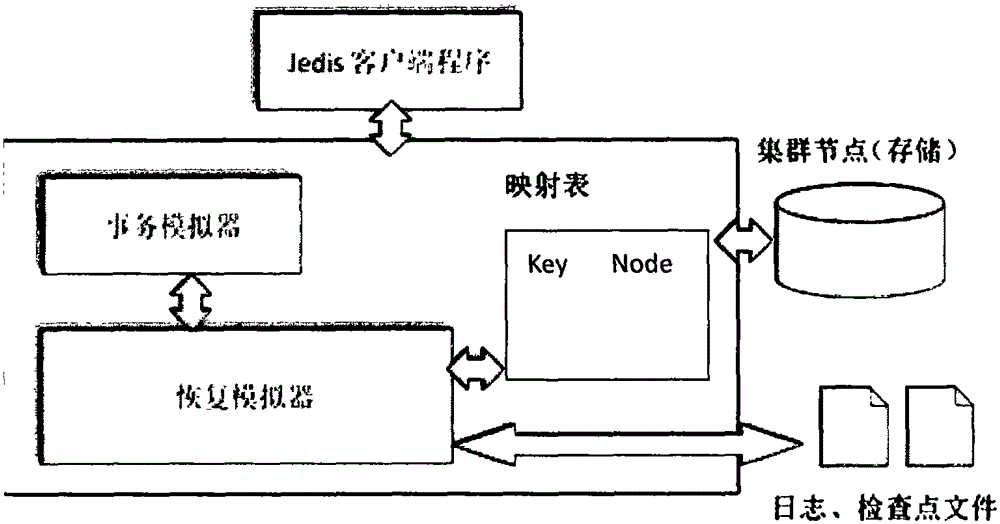
[0101] Such as Figure 4 As shown, a log recovery simulation system in memory data management, including a master node and a Redis instance, wherein;
[0102] The master node includes a mapping list, a transaction simulator, and a recovery simulator; the master node maintains control and obtains the state of the Redis instance through a network connection. The program of the master node runs on a computer with high performance configuration. It is mainly responsible for all functions except data and log storage, including sending read and write commands, simulating the progress of transactions, and controlling the timing of reading and writing logs, etc. . The master node program is written in the Java programming language client Jedis recommended by Redis, and Jedis can call the API to control the operation of the cluster. The main components of the master node see figure 2 .
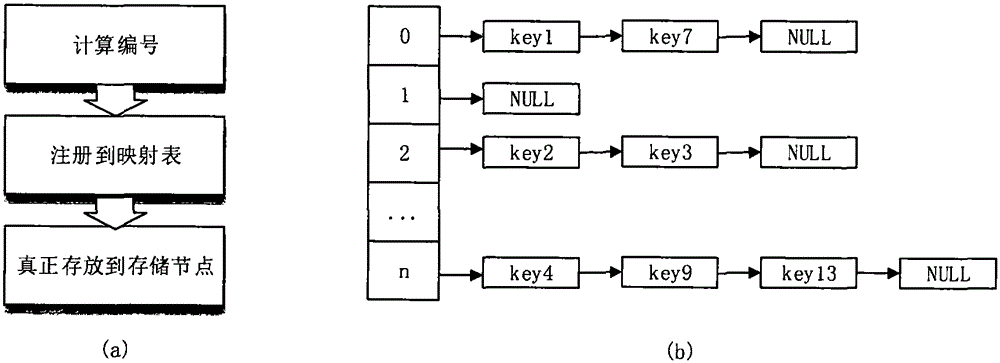
[0103] The mapping list stores the data items and the corresponding specific node numbers in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com