Information security electronic equipment and application architecture
A technology of information security and electronic equipment, applied in the direction of internal/peripheral computer component protection, platform integrity maintenance, etc., can solve the problems of probabilistic random blocking, bottom, and no legitimacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
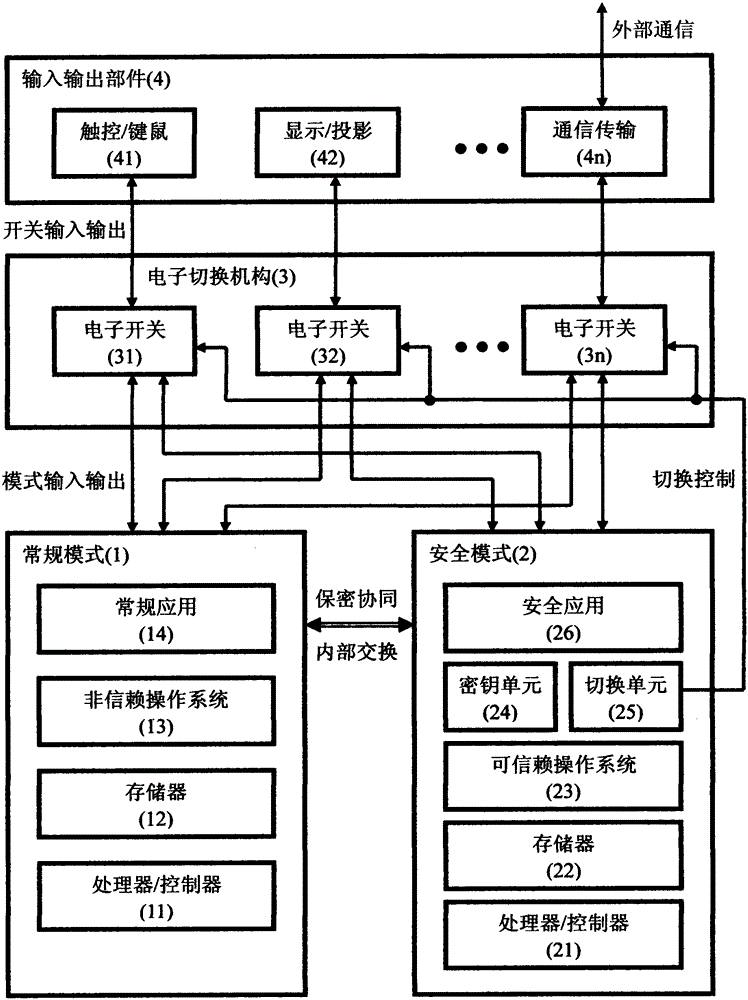
[0049] One of the embodiments of the present invention is information security computer equipment. To improve an existing desktop computer, modify the design of the motherboard in terms of hardware, and develop supporting applications in terms of software, so as to expand and realize.
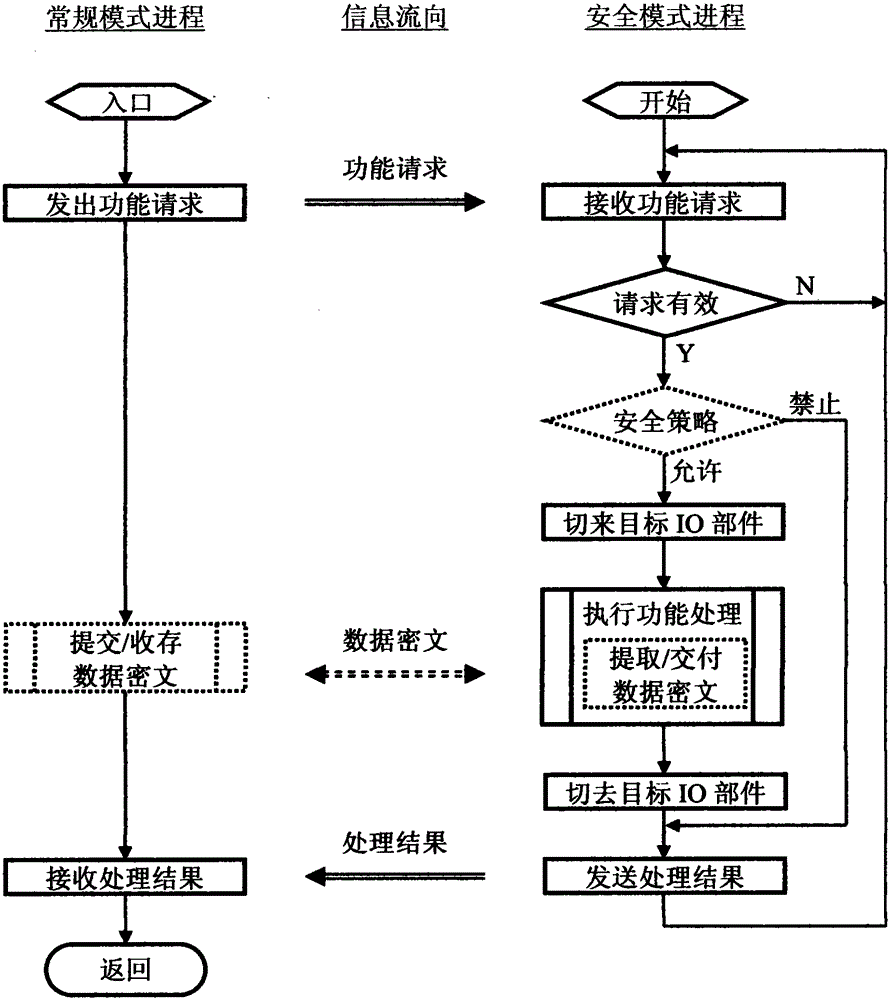
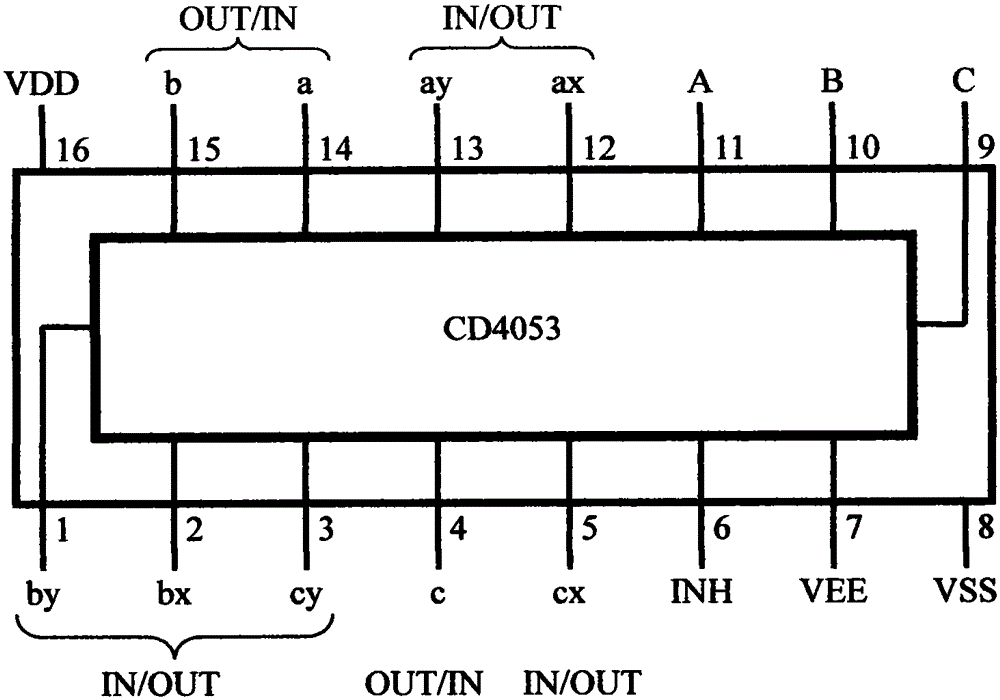
[0050] see figure 1 and its description. Basically adopt the original hardware design as the conventional subsystem, i.e. conventional mode (1), including processor (11) and memory (12); non-trusted operating system (13) adopts WindowsXP, still uses disk storage; conventional application (14 ) Existing software such as the Office series can still be used as usual, but the user must be reminded of security risks. To ensure security, new applications need to be developed in conjunction with the new architecture, and its conventional modules run in conventional mode (see the following embodiments). Equally, basically adopt original hardware design as safety subsystem, i.e. safety mode (2), compr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com